Похожие презентации:
Requirements Development and Management
1.
RequirementsDevelopment and
Management.
Overview.
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
2.
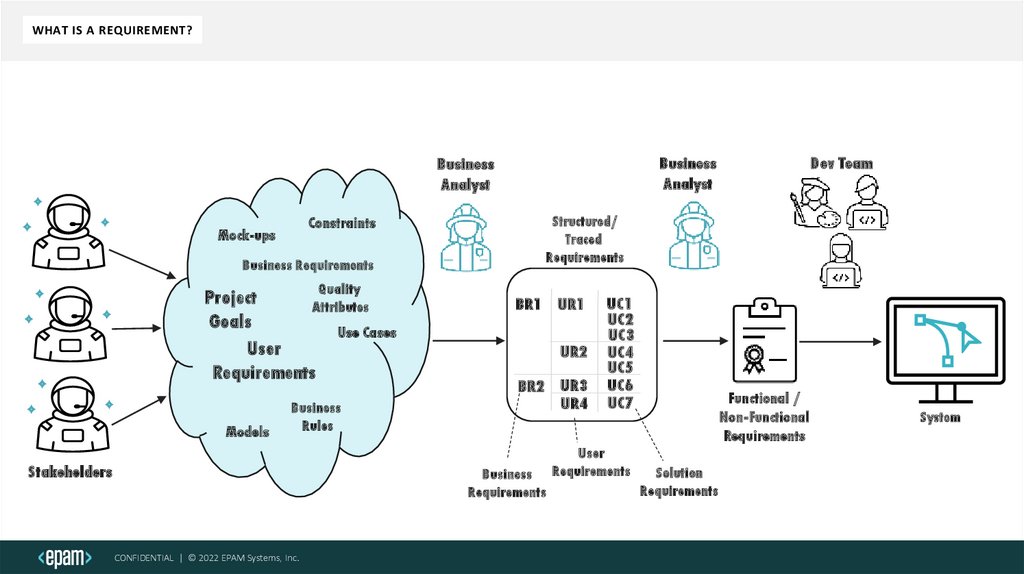
WHAT IS A REQUIREMENT?Constraints
Mock-ups
Business Requirements
Quality
Project
Attributes
Goals
Use Cases
User
Requirements
Models
Business
Rules
Stakeholders
Structured/
Traced
Requirements
BR1 UR1
UR2
BR2 UR3
UR4
Business
Requirements
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Dev Team
Business
Analyst
Business
Analyst
UC1
UC2
UC3
UC4
UC5
UC6
UC7
User
Requirements
Functional /
Non-Functional
Requirements
Solution
Requirements
System
3.
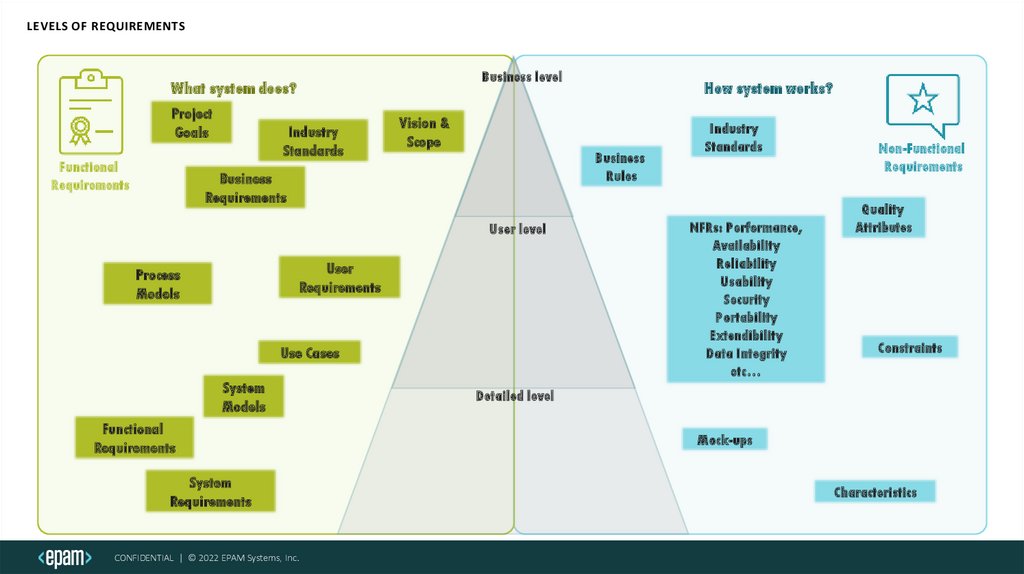
LEVELS OF REQUIREMENTSBusiness level
What system does?
Project
Goals
Functional
Requirements
Industry
Standards
Vision &
Scope
Business
Rules
Business
Requirements
User level
User
Requirements
Process
Models
Use Cases
System
Models
Functional
Requirements
System
Requirements
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
How system works?
Industry
Standards
NFRs: Performance,
Availability
Reliability
Usability
Security
Portability
Extendibility
Data Integrity
etc…
Non-Functional
Requirements
Quality
Attributes
Constraints
Detailed level
Mock-ups
Characteristics
4.
EXAMPLES OF REQUIREMENTSIdea behind
Business Requirements
Why the organization needs this
system?
User Requirements
What user should be able to do
within the system?
User Story
What user should be able to do
within the system to achieve the
goal?
Functional Requirements
What functions the system should
perform?
Non-Functional
Requirements
How should the system behave?
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Example
We as an airline want to reduce the cost of check-in
counter employees by 25%
Passenger shall be able to quickly check in for the flight
As a passenger I want to be able to check in quickly to get
to the plane in time
FR1 System shall allow the user with “Customer” role to
select the Flight from the dropdown list
FR1.1 The list of Flights shall include Flights labelled as
“Outbound” only
System shall support 10 000 CCU
5.
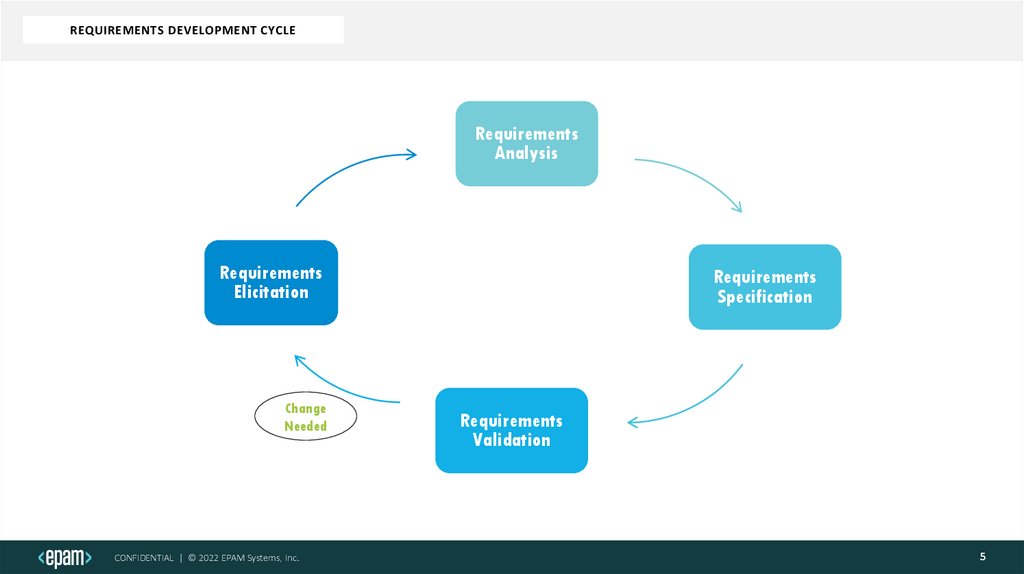
REQUIREMENTS DEVELOPMENT CYCLERequirements
Analysis
Requirements
Elicitation
Change
Needed
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Requirements
Specification
Requirements
Validation
5
6.
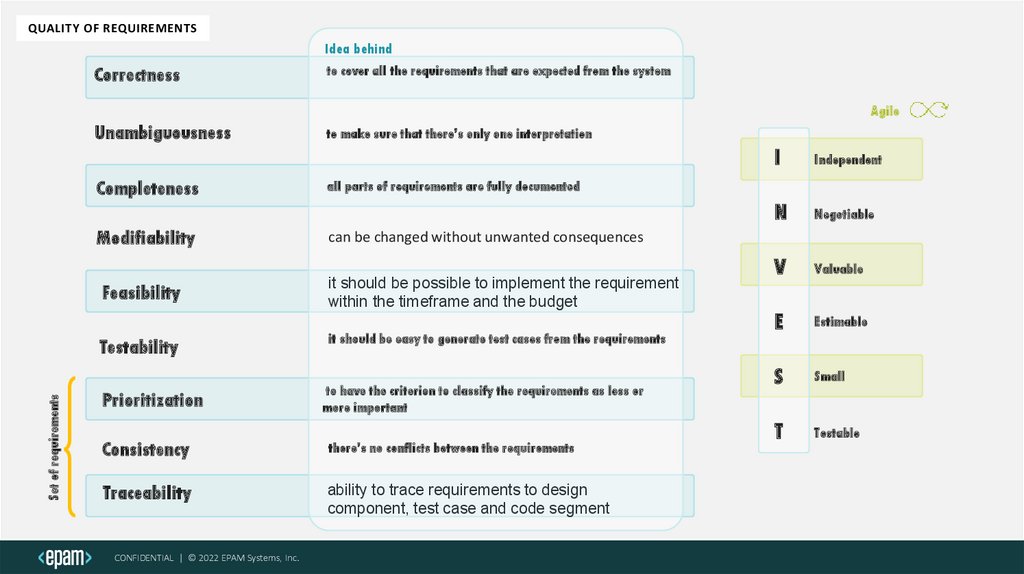
QUALITY OF REQUIREMENTSIdea behind
Correctness
to cover all the requirements that are expected from the system
Agile
Unambiguousness
Completeness
Set of requirements
Modifiability
to make sure that there’s only one interpretation
N
Negotiable
V
Valuable
E
Estimable
S
Small
T
Testable
can be changed without unwanted consequences
Feasibility
Testability
it should be easy to generate test cases from the requirements
to have the criterion to classify the requirements as less or
more important
Consistency
there’s no conflicts between the requirements
Traceability
ability to trace requirements to design
component, test case and code segment
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Independent
all parts of requirements are fully documented
it should be possible to implement the requirement
within the timeframe and the budget
Prioritization
I
7.
REQUIREMENT LIFECYCLEElicitation
Analysis
Documentation
Documented
Cancelled
Reviewed
Validation
Approved
Baseline. Its version can be updated via
Change Management process
Development
Implemented
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
8.
REQUIREMENTS MANAGEMENTRequirements management knowledge area describes the tasks that business analysts perform in
order to maintain the integrity, accuracy, and currency of requirements:
• Maintaining Requirements
• Tracing Requirements
• Prioritizing Requirements
• Requirements Change Management
• Approving Requirements
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
9.
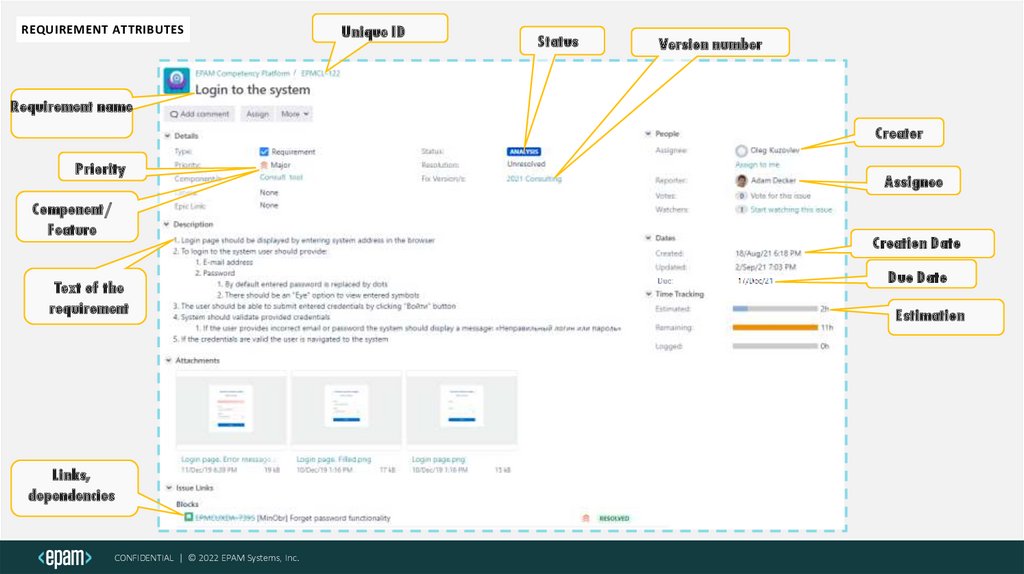
REQUIREMENT ATTRIBUTESUnique ID
Status
Version number
Requirement name
Creator
Priority
Component/
Feature
Assignee
Creation Date
Text of the
requirement
Links,
dependencies
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Due Date
Estimation
10.
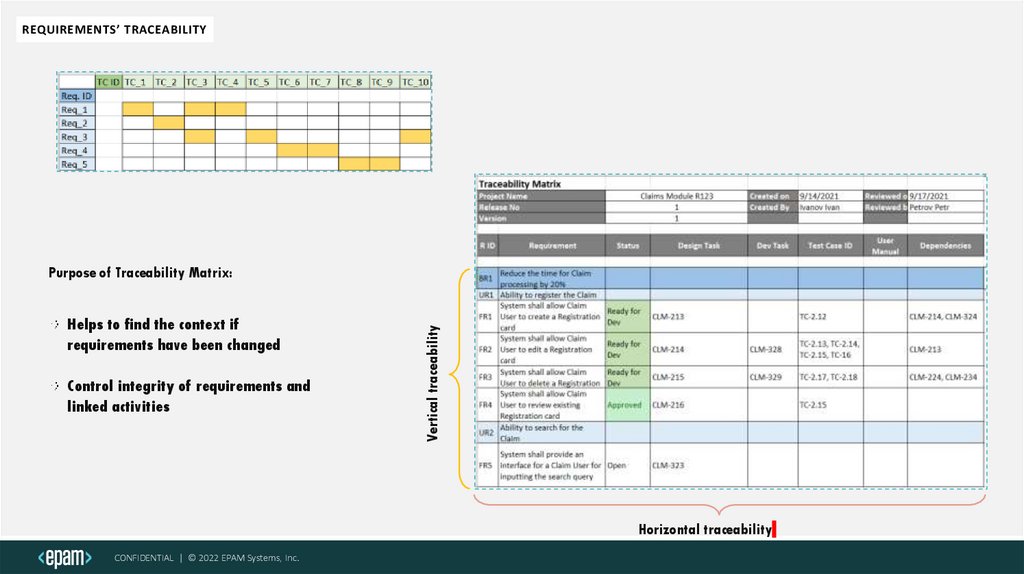
REQUIREMENTS’ TRACEABILITYHelps to find the context if
requirements have been changed
Control integrity of requirements and
linked activities
Vertical traceability
Purpose of Traceability Matrix:
Horizontal traceability
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
11.
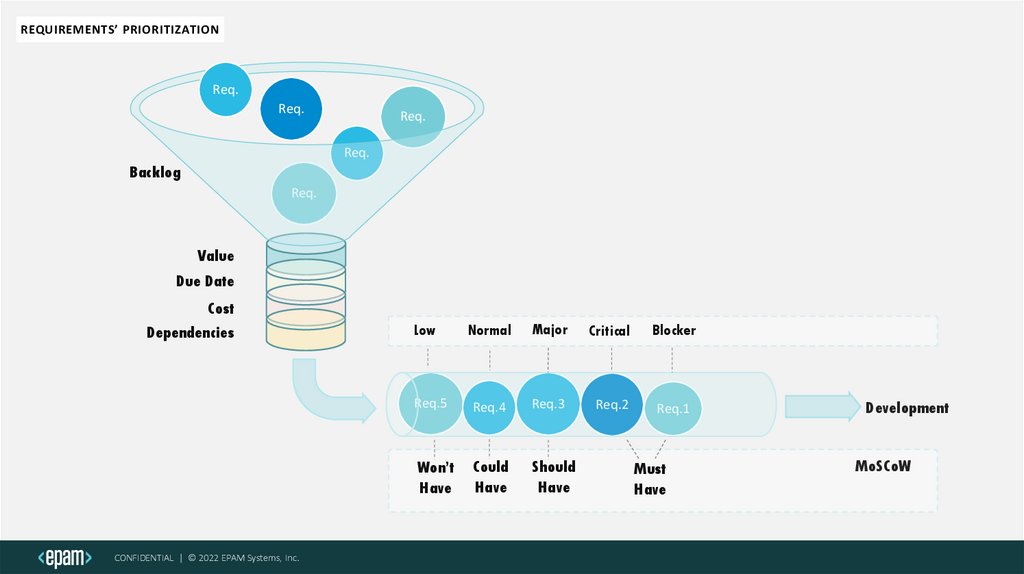
REQUIREMENTS’ PRIORITIZATIONReq.
Req.
Req.
Req.
Backlog
Req.
Value
Due Date
Cost
Dependencies
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Normal
Major
Critical
Blocker
Req.5
Req.4
Req.3
Req.2
Req.1
Won’t
Have
Could
Have
Should
Have
Low
Must
Have
Development
MoSCoW
12.
REQUIREMENTS CHANGE MANAGEMENTExisting Product
New Product
Change
Request 1
Change
Request 2
Change
Request 3
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Change
Request n
13.
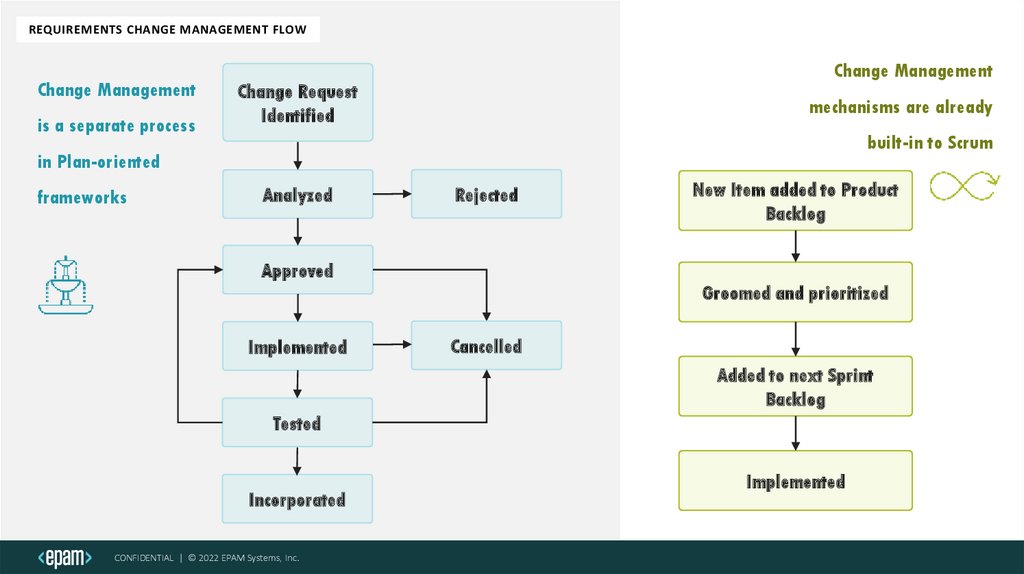
REQUIREMENTS CHANGE MANAGEMENT FLOWChange Management
is a separate process
Change Management
Change Request
Identified
mechanisms are already
built-in to Scrum
in Plan-oriented
frameworks
Analyzed
Rejected
New Item added to Product
Backlog
Approved
Groomed and prioritized
Implemented
Cancelled
Added to next Sprint
Backlog
Tested
Incorporated
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Implemented
14.
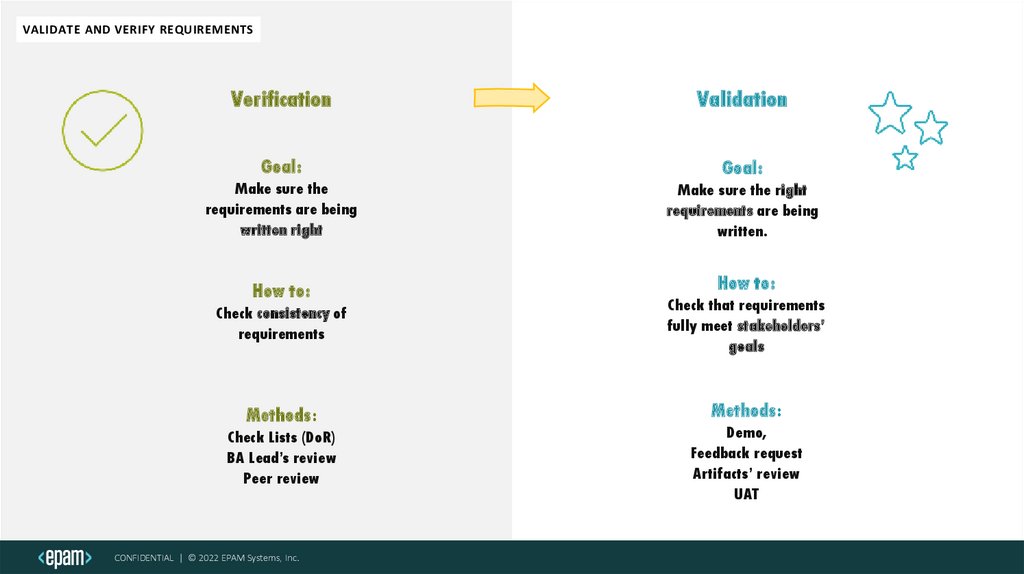
VALIDATE AND VERIFY REQUIREMENTSVerification
Validation
Goal:
Goal:
Make sure the
requirements are being
written right
Make sure the right
requirements are being
written.
How to:
How to:
Check consistency of
requirements
Check that requirements
fully meet stakeholders’
goals
Methods:
Methods:
Check Lists (DoR)
BA Lead’s review
Peer review
CONFIDENTIAL | © 2022 EPAM Systems, Inc.
Demo,
Feedback request
Artifacts’ review
UAT




 Менеджмент
Менеджмент








