Похожие презентации:
Computer viruses and antivirus programs
1.
Computer viruses and antivirus programs2.
Computer viruses and anti-virusprograms
The personal computer plays lives of the modern person
an important role as it helps it almost with all areas of its
activity. The modern society is more and more involved
in the virtual world of the Internet. But with active
development of global networks the information security
question as their getting networks viruses can break
integrity and safety of your information is actual.
Protection of the computer against viruses is that
problem, to solve which it is necessary all users, and
especially as that who actively uses the Internet or works
in a local network.
3.
HISTORY OF COMPUTERVIRUSES
First "epidemic" of a computer virus has occurred in
1986 when a virus by name of Brain (English "brain")
"infected" diskettes of personal computers. Now
some tens thousand the viruses infecting computers
and extending on computer networks are known.
4.
What is the virus? And than the biologicalvirus differs from the computer? Extending on
computer networks.
Let's address to the virus encyclopedia
«Kaspersky's Laboratory», Cyril's electronic
encyclopedia and Mefodija and to the
explanatory dictionary of Russian of
S.I.Ozhegova and N.J.Shvedovoj
5.
Computer virus – speciallycreated small program capable to
self-reproduction, a
contamination of the computer
and to performance of other
undesirable actions.
The encyclopedia of viruses
«Kaspersky's laboratories
http://
www.viruslist.com/ru/viruses/encyclopedia
6.
What the general between biologicaland computer viruses?
1. Ability to reproduction.
2. Harm for health of the person and
undesirable actions for the computer.
3. Reserve since viruses have the
incubatory period.
7.
THAN THE COMPUTER VIRUS ISDANGEROUS?
After infection of the computer the virus can become
more active and start to carry out harmful actions on
destruction of programs and the data.
Virus activization can be connected with various
events:
Approach of certain date or day of week
Program start
Document opening …
8.
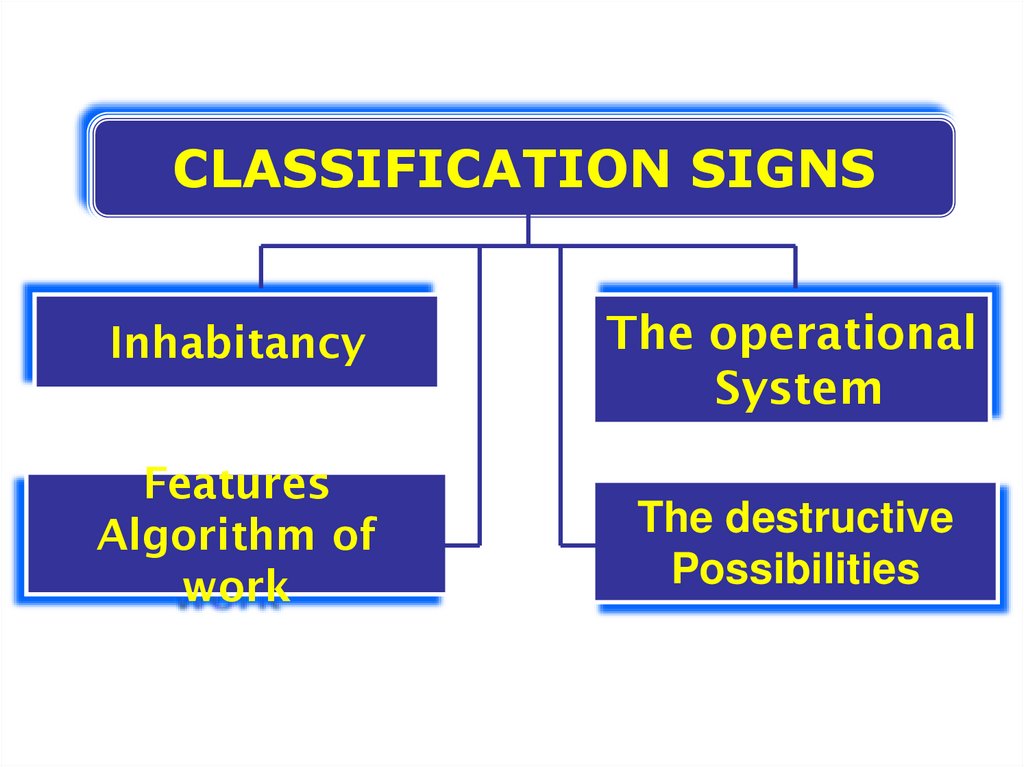
CLASSIFICATION SIGNSInhabitancy
The operational
System
Features
Algorithm of
work
The destructive
Possibilities
9.
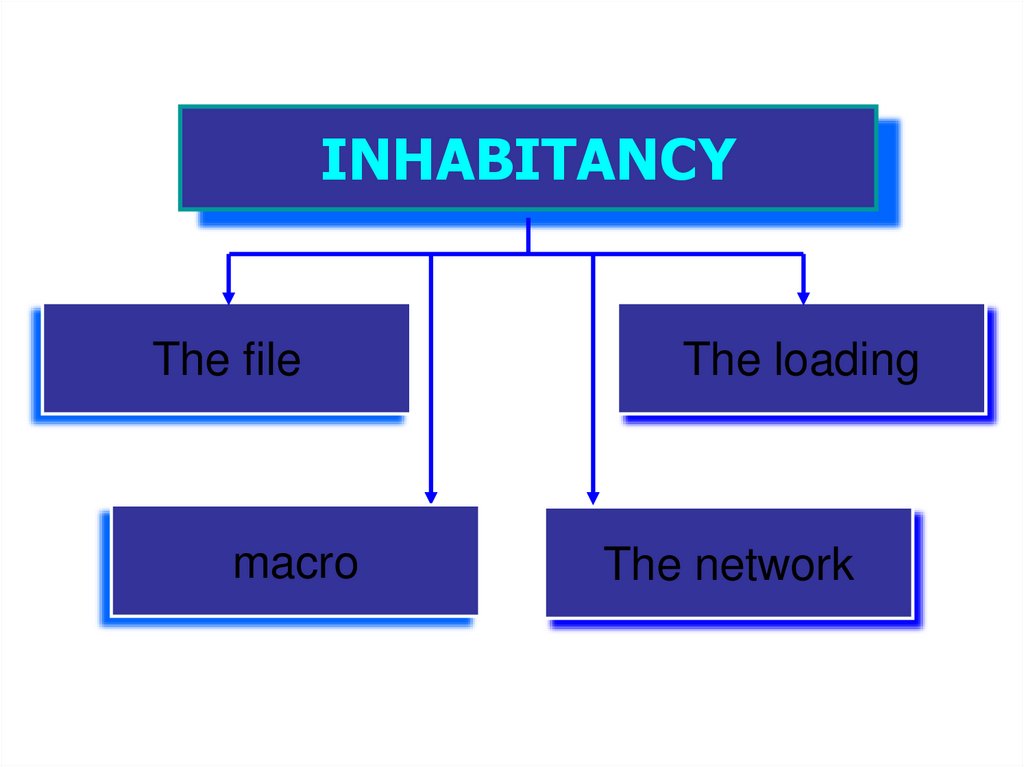
INHABITANCYThe file
macro
The loading
The network
10.
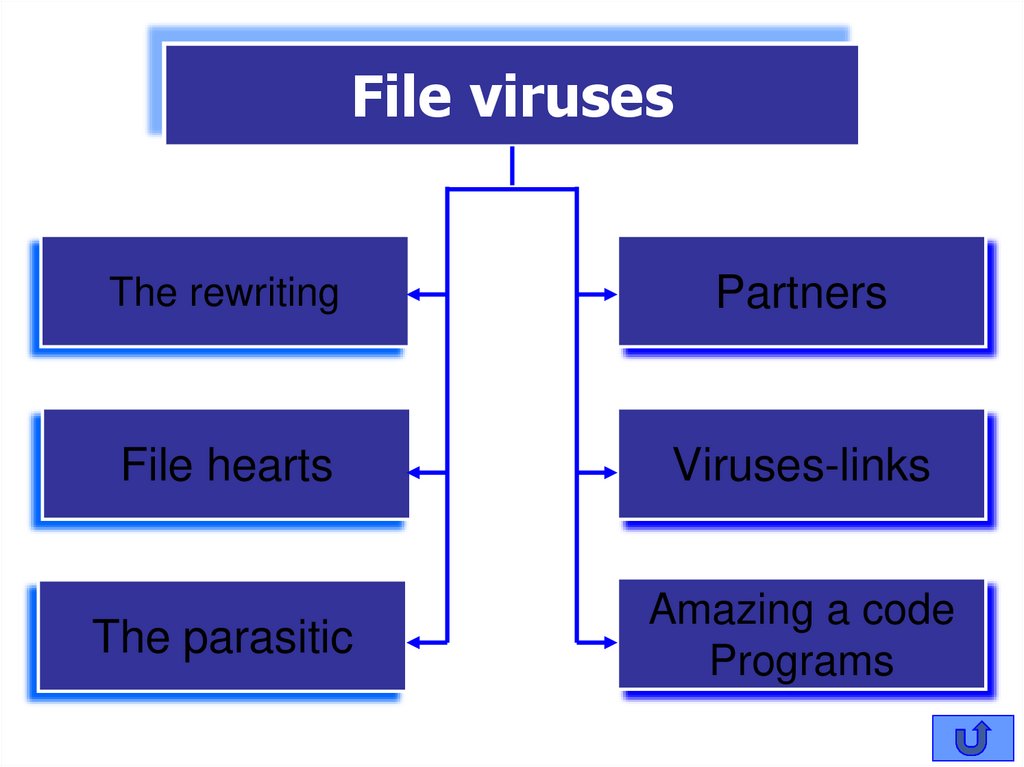
File virusesThe rewriting
Partners
File hearts
Viruses-links
The parasitic
Amazing a code
Programs
11.
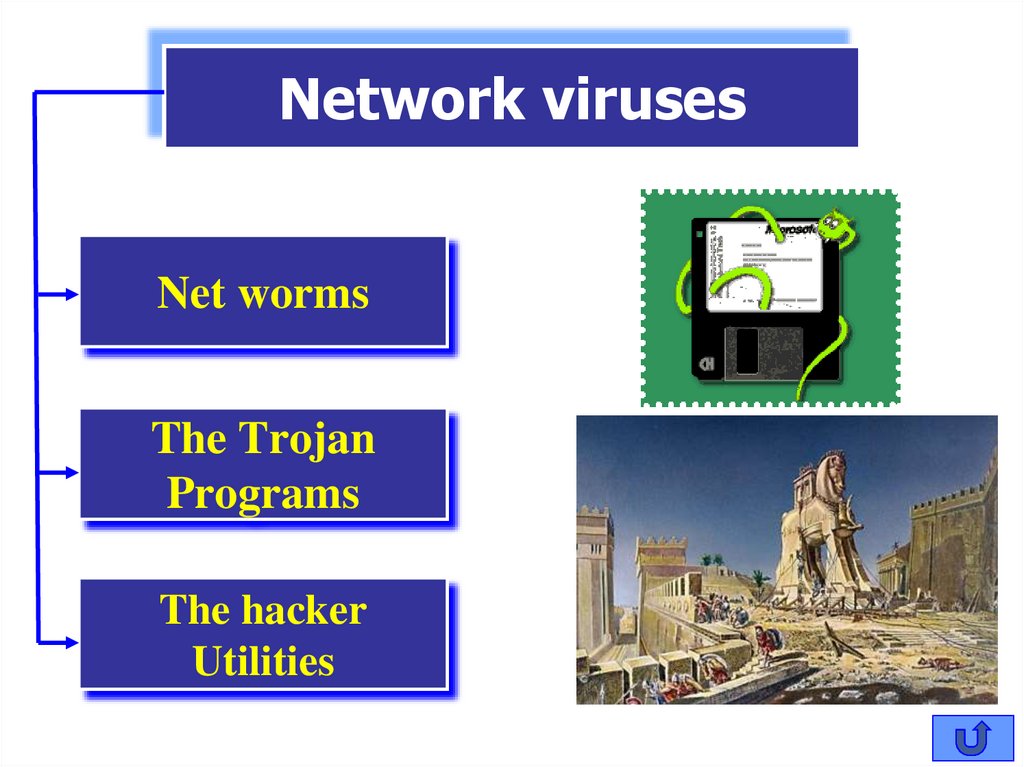
Network virusesNet worms
The Trojan
Programs
The hacker
Utilities
12.
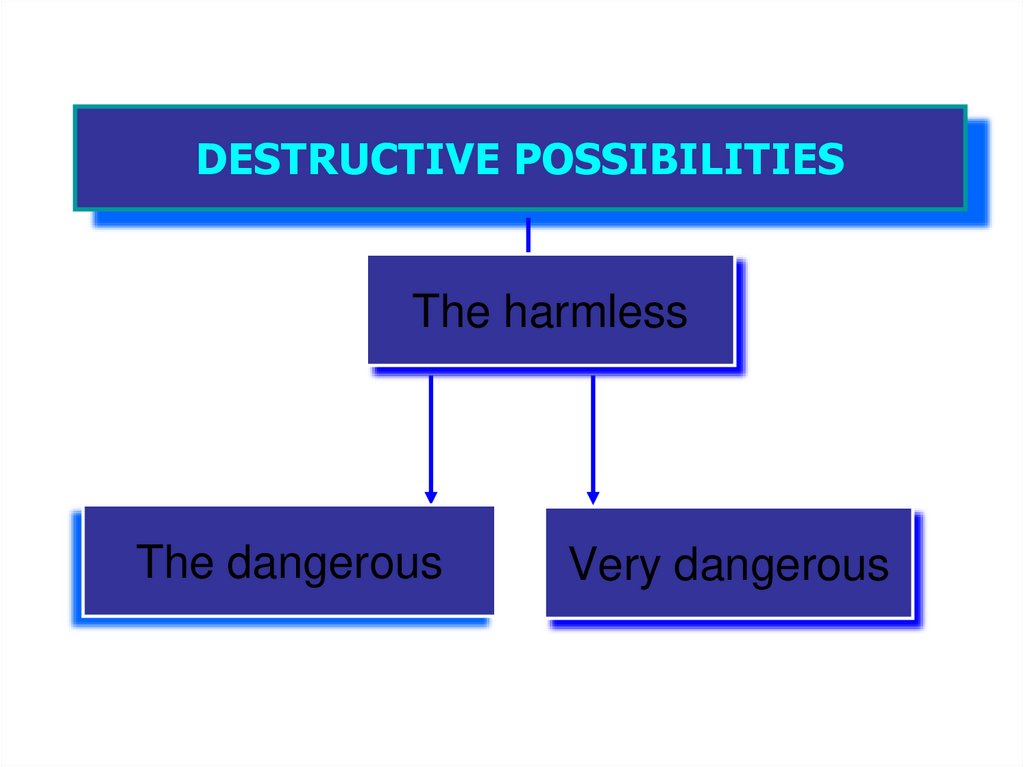
DESTRUCTIVE POSSIBILITIESThe harmless
The dangerous
Very dangerous
13.
On destructive features viruses canbe divided on:
• Harmless, i.e. not influencing in any way for computer work
(except reduction of free memory by a disk as a result of the
distribution);
• Harmless which influence is limited to reduction of free
memory by a disk and graphic, sound and so forth effects;
• Dangerous viruses which can lead to serious failures in
computer work;
• Very dangerous in which algorithms of work procedures which
can lead to loss of programs are obviously put destroy the
data, erase necessary for work of the computer the information
which has been written down in system areas of memory, and
even as one of unchecked computer legends says, to promote
fast deterioration of moving parts of mechanisms - to enter into
a resonance and to destroy heads of some types of
winchesters.
14.
Protectionmethods
15.
• Protection of local networks• Use distributive ON
• Reserve copying of the information
• Use of the anti-virus
• Programs
• Not to start nepro • веренные files
16.
Anti-virus programs17.
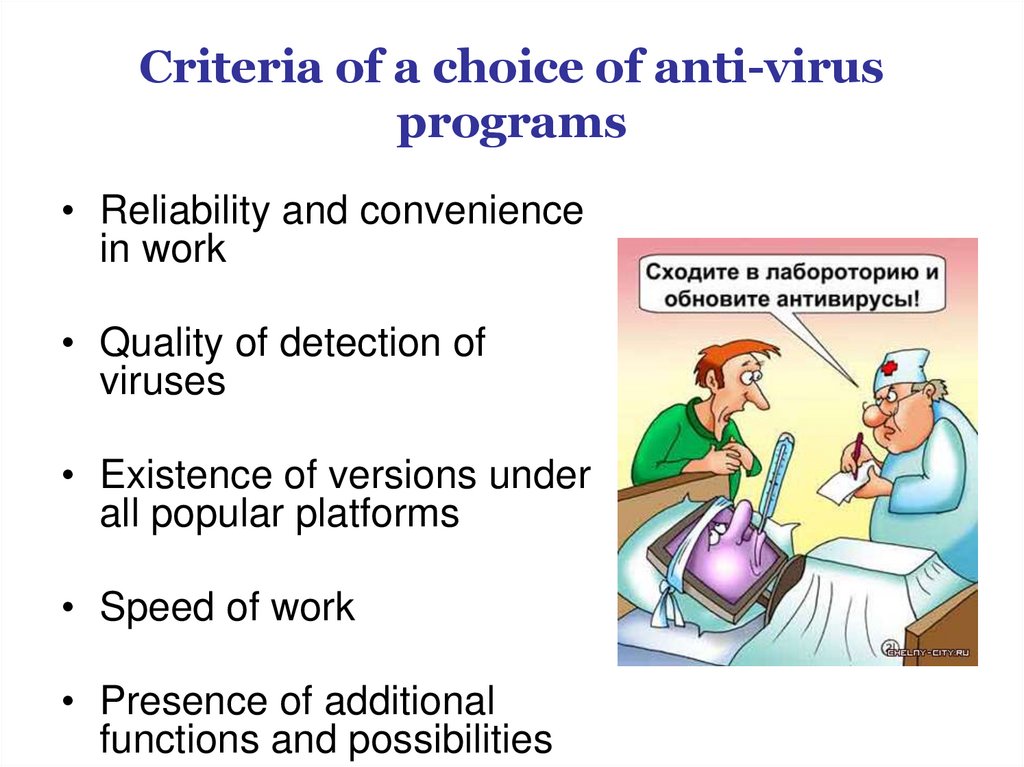
Criteria of a choice of anti-virusprograms
• Reliability and convenience
in work
• Quality of detection of
viruses
• Existence of versions under
all popular platforms
• Speed of work
• Presence of additional
functions and possibilities
18.
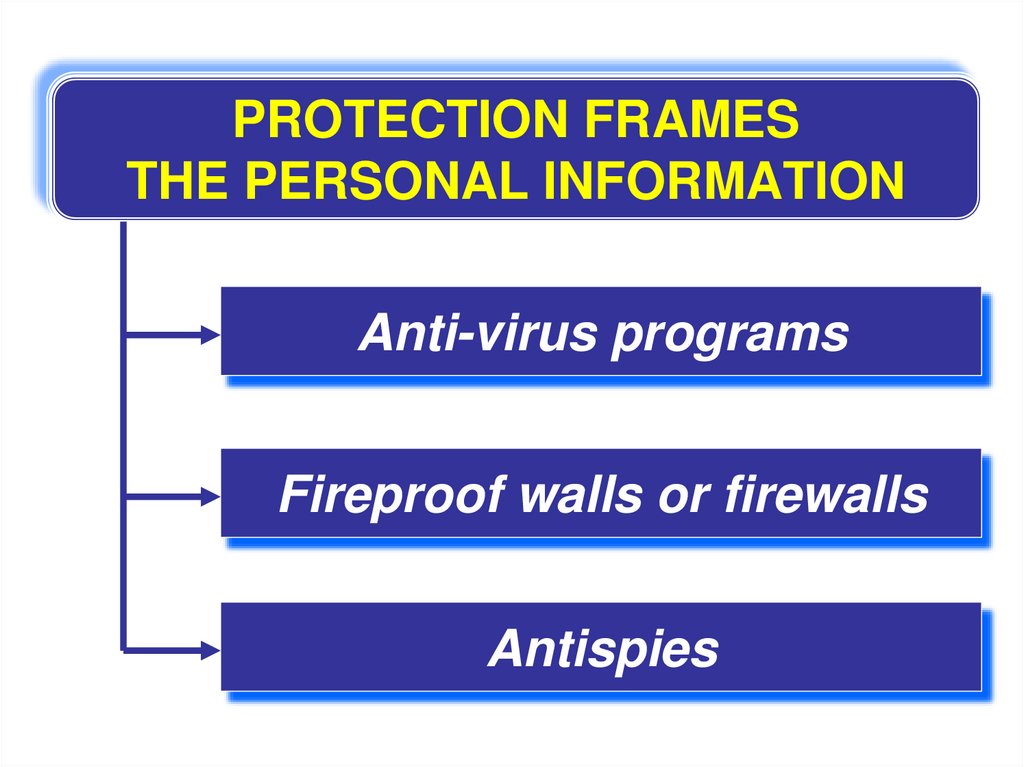
PROTECTION FRAMESTHE PERSONAL INFORMATION
Anti-virus programs
Fireproof walls or firewalls
Antispies
19.
List of references• 1. Шапиро В.Д. Управление проектами / В.Д. Шапиро. – СПб:
Два Три, 2017. -610 с.
• 2. Ястремская Е.Н. Стратегическое инвестирование
предприятий: Монография / Е.Н. Ястремская, А.В. Строкович. –
Харьков: РИО ХГАДТУ, 2010-2017. – 182 с.
• 3. Kezsner Harold. Project Management. 6th edition. John Wiley &
Sons. Jnc, 201.
• 4. Fleming Q.W. Earned value project management / Q. W
Fleming,J.M. Hoppelman, PMI, 2017.
• 5. A Guide to the Project Management Body of Knowledge. PMI,
2016.
• Ресурсы Интернет.
• 6. www.pmi.ore .
• 7. www.pmi.org/publictn/ pmboktoc.htm.
• 8. www. Project.km.ru












 Информатика
Информатика Программное обеспечение
Программное обеспечение








