Похожие презентации:
Hacking LAB
1.
Hacking LABDr Bishwajeet Pandey, SMIEEE
Professor- Dept of IS& CS, Astana IT University, Kazakhstan
PhD (Gran Sasso Science Institute, L'Aquila, Italy)
Visiting Professor at
L.N. Gumilyov Eurasian National University, Kazakhstan
UCSI UNIVERSITY-Malaysia
2.
ABOUT COURSE TEACHERPhD from Gran Sasso Science Institute, Italy
PhD Supervisor Prof Paolo Prinetto from Politecnico Di Torino, Italy
MTech from Indian Institute of Information Technology, Gwalior, India
Visited 47 Countries Across The Globe
Written 200+ Research paper with 212 Researcher from 93 Universities
Scopus Profile: https://www.scopus.com/authid/detail.uri?authorId=57203239026
Google Scholar: https://scholar.google.com/citations?user=UZ_8yAMAAAAJ&hl=hi
IBM Certified Solution Designer
EC-Council Certified Ethical Hacker
AWS Certified Cloud Practitioner
Email: [email protected], [email protected], [email protected]
3.
Hacking LAB: Practices1.
Working with network commands in Windows and Linux (Assignment Week 1: Make a list of 50 Commands with syntax and
usage)
2. Capturing and Analyzing Network Traffic using Wireshark (Assignment Week 2: Case study of TCP 3-way handshake) or
(Assignment Week 2: Capture HTTP packet and extract username and Password using Ettercap and Wireshark)
3. Website technical information gathering using maltego, httrack, whois. (Assignment Week 3: Chose any two tools from
OSINTFramework.com and discuss the steps to use it)
4. Full Scan, Half Open Scan, Stealth Scan and XMAS Scan using NMAP (Assignment Week 4: Run Any 10 NSE Scripts )
5. Perform Host Discovery, Service Discovery(FTP, Telnet, SSH, Java RMI Server, SMB), Port Scanning using Metasploit or
(Assignment Week 5: Demonstrate Eternal Blue, VSFTPD, OpenSSH exploit using Metasploit)
6. Social engineering using SEToolkit (Assignment Week 6: Create a Clone of GMAIL using SEToolkit)
7. Web parameter poisoning using burp suite (Assignment Week 7: Change the price of all item to 1 USD on e-commerce shopping
cart)
8. Create Fake Harmless Virus using Notepad (Assignment Week 8: Create a MAC/Window and Android Spyware
with MSFVenom)
9. Malware Classification using Convolutional Neural Networks using Google Colab (Assignment Week 9: Malware Classification
using Convolutional Neural Networks using Jupyter Notebook)
10. Perform session hijacking using Zed Attack Proxy (ZAP) (Assignment Week 10: Perform Session Hijacking using Wireshark)
4.
Week 4 PracticeFull Scan, Half Open Scan, Stealth Scan and XMAS Scan using
NMAP
(Assignment Week 4: Run Any 10 NSE Scripts )
5.
Syntax of NMAP Command• #nmap [Scan Type] [Options] {Target Specification}
• Target Specification:can pass host name or IP Address e. g.
scanme.nmap.org, microsoft.com, 192.168.0.1, 10.10.10.136
• Scan Techniques
• -sS//sT/sA/sW: TCP SYN/CONNECT()/ACK/Window
• -sU: UDP Scan
• -sO: IP Protocol Scan
• Host Discovery
• -sL: small List target to Scan
• -sn: Disable Port Scan
• -PS/PA: TCP Syn/ACK discovery to given ports
• -PU: UDP discovery to given ports
• -PE: ICMP Echo request discovery probe
• -PO: IP Protocol Ping
• -PN: No Ping
6.
Syntax of NMAP Command• MISC
• -6 Enable IPv6 Scaning
• -A Enable OS detection, version detection,
• -O Enable OS detection
• -p <port ranges>: Only scan specified ports
7.
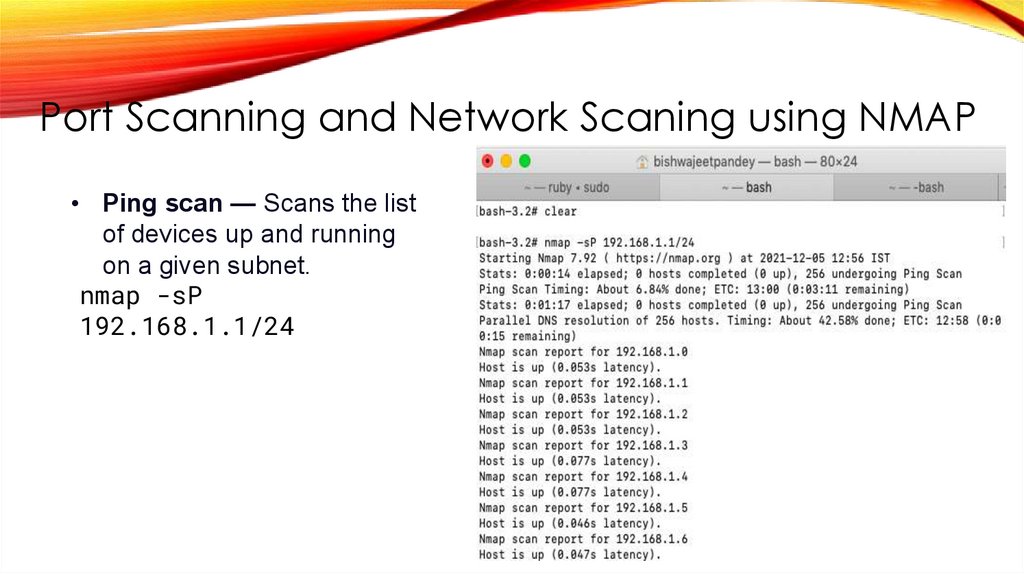
Port Scanning and Network Scaning using NMAP• Ping scan — Scans the list
of devices up and running
on a given subnet.
nmap -sP
192.168.1.1/24
8.
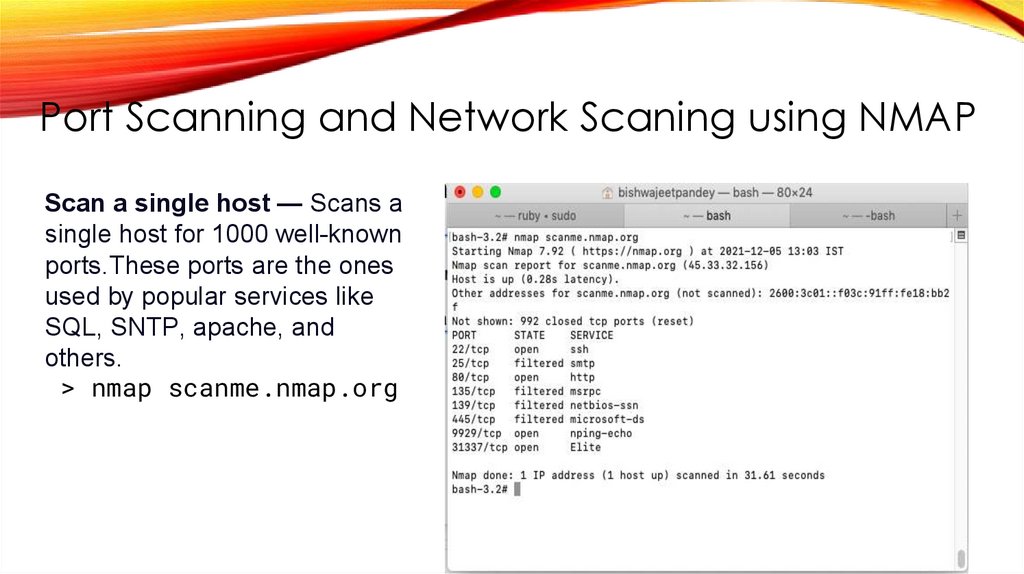
Port Scanning and Network Scaning using NMAPScan a single host — Scans a
single host for 1000 well-known
ports.These ports are the ones
used by popular services like
SQL, SNTP, apache, and
others.
> nmap scanme.nmap.org
9.
Port Scanning and Network Scaning using NMAP● Port scanning is one of the most fundamental features of
Nmap. We can scan for ports in several ways.
● Using the -p param to scan for a single port (here 973)
> nmap -p 973 192.164.0.1
● If you donot want specify the type of port, you can scan
for all port.
> nmap –p- 192.164.0.1
10.
Port Scanning and Network Scaning using NMAP● A range of ports can be scanned by separating them with
a hyphen.
> nmap -p 76–973 192.164.0.1
● We can also use the -top-ports flag to specify the top n
ports to scan.
> nmap --top-ports 10 scanme.nmap.org
11.
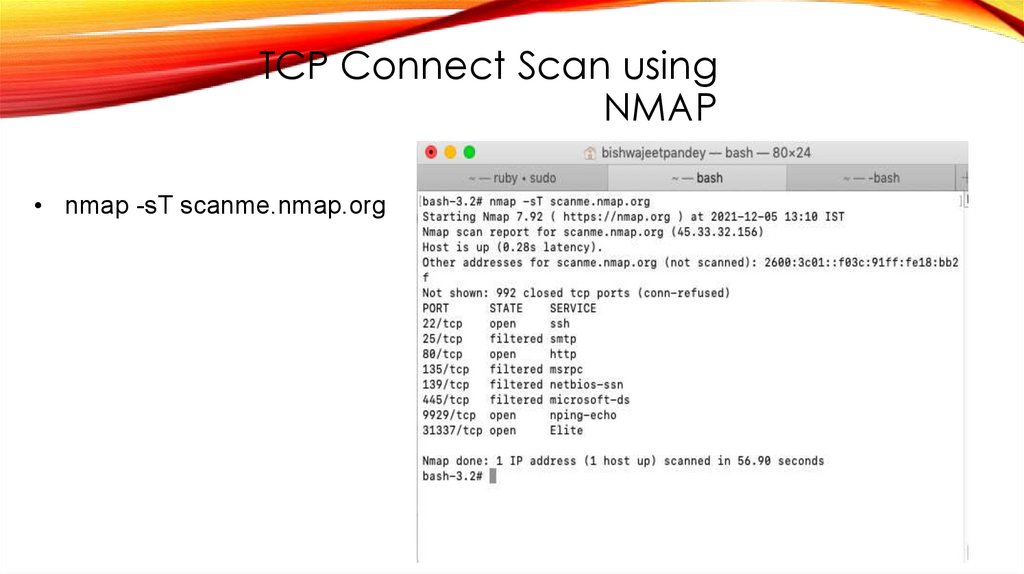
TCP Connect Scan usingNMAP
• nmap -sT scanme.nmap.org
12.
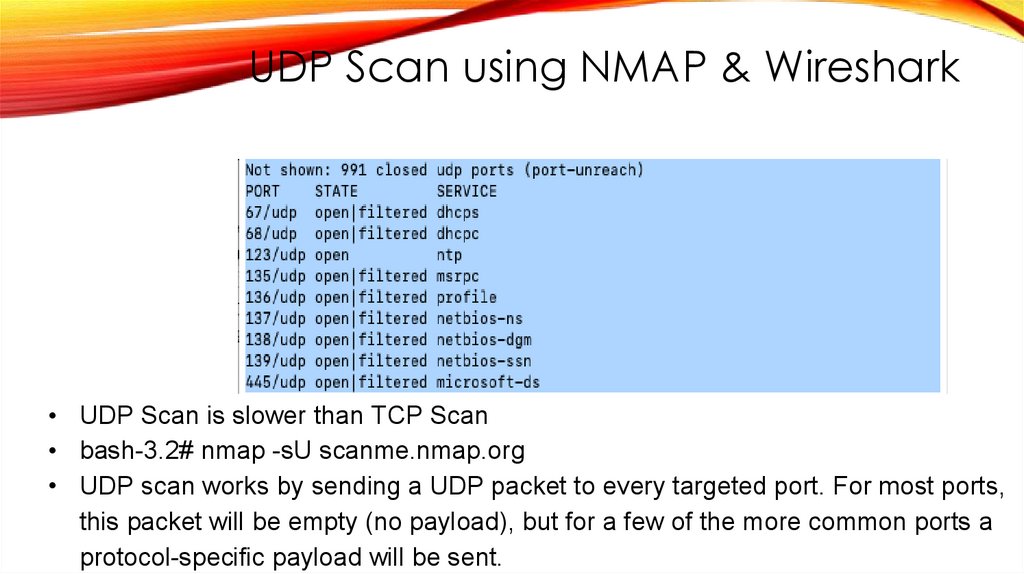
UDP Scan using NMAP & Wireshark• UDP Scan is slower than TCP Scan
• bash-3.2# nmap -sU scanme.nmap.org
• UDP scan works by sending a UDP packet to every targeted port. For most ports,
this packet will be empty (no payload), but for a few of the more common ports a
protocol-specific payload will be sent.
13.
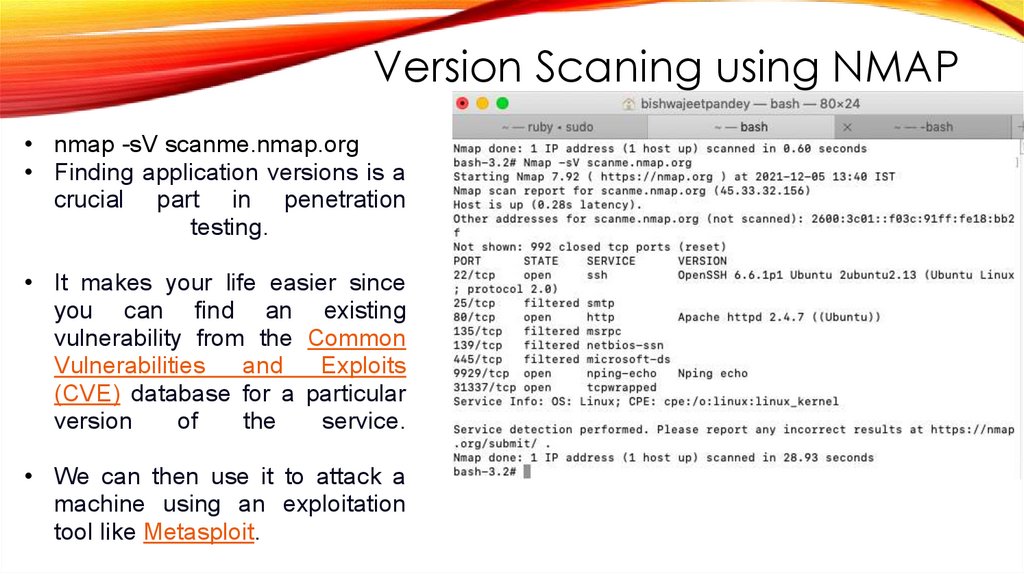
Version Scaning using NMAP• nmap -sV scanme.nmap.org
• Finding application versions is a
crucial part in penetration
testing.
• It makes your life easier since
you can find an existing
vulnerability from the Common
Vulnerabilities
and
Exploits
(CVE) database for a particular
version
of
the
service.
• We can then use it to attack a
machine using an exploitation
tool like Metasploit.
14.
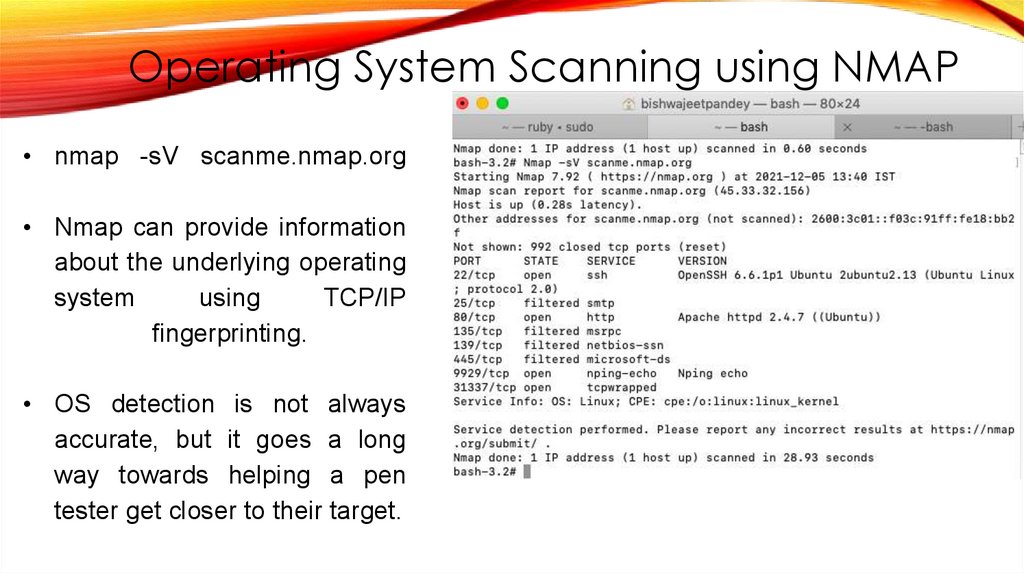
Operating System Scanning using NMAP• nmap -sV scanme.nmap.org
• Nmap can provide information
about the underlying operating
system
using
TCP/IP
fingerprinting.
• OS detection is not always
accurate, but it goes a long
way towards helping a pen
tester get closer to their target.
15.
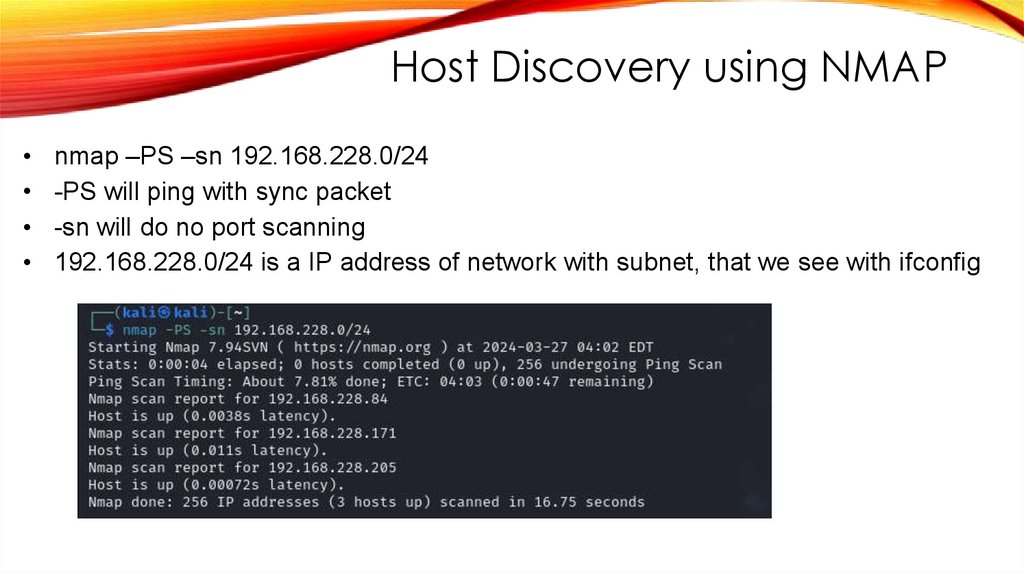
Host Discovery using NMAPnmap –PS –sn 192.168.228.0/24
-PS will ping with sync packet
-sn will do no port scanning
192.168.228.0/24 is a IP address of network with subnet, that we see with ifconfig
16.
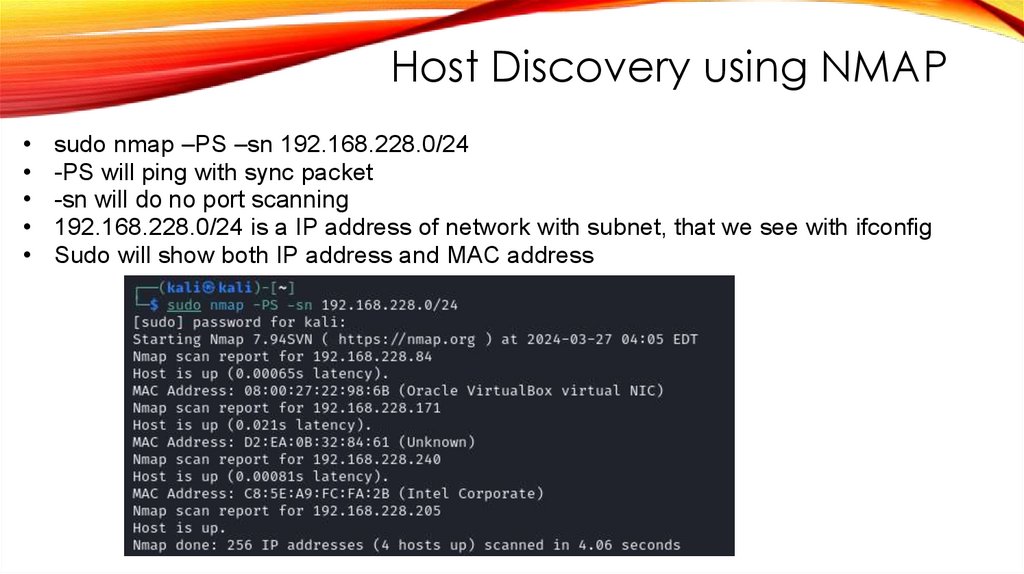
Host Discovery using NMAPsudo nmap –PS –sn 192.168.228.0/24
-PS will ping with sync packet
-sn will do no port scanning
192.168.228.0/24 is a IP address of network with subnet, that we see with ifconfig
Sudo will show both IP address and MAC address
17.
Normal Output• Nmap scans can also be exported to a text file.
• It will be slightly different from the original command
line output, but it will capture all the essential scan
results.
• > nmap -oN output.txt scanme.nmap.org
18.
XML Output• Nmap scans can also be exported to XML.
• It is also the preferred file format of most pen-testing
tools, making it easily parsable when importing scan
results.
• > nmap -oX output.xml scanme.nmap.org
19.
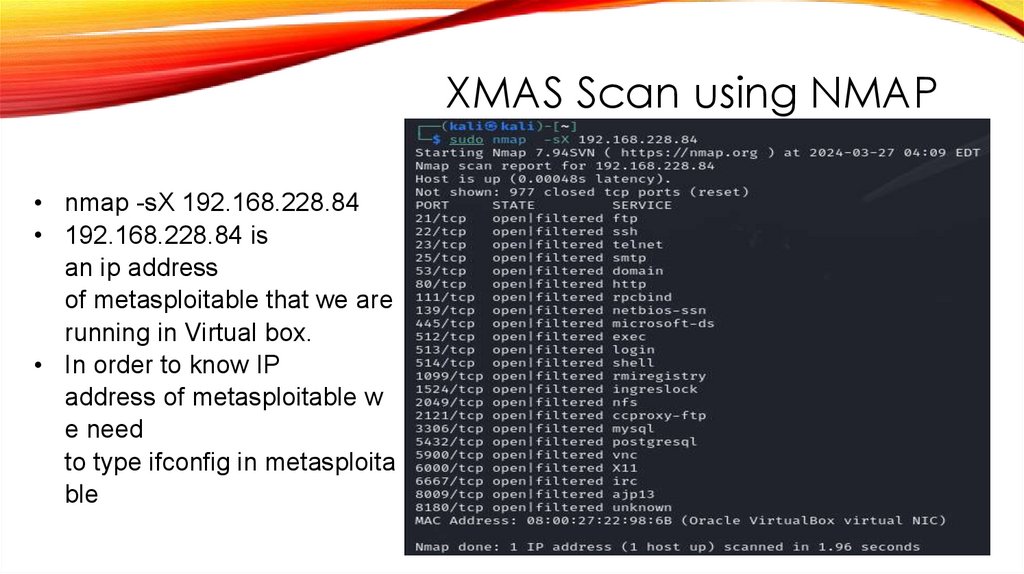
XMAS Scan using NMAP• nmap -sX 192.168.228.84
• 192.168.228.84 is
an ip address
of metasploitable that we are
running in Virtual box.
• In order to know IP
address of metasploitable w
e need
to type ifconfig in metasploita
ble
20.
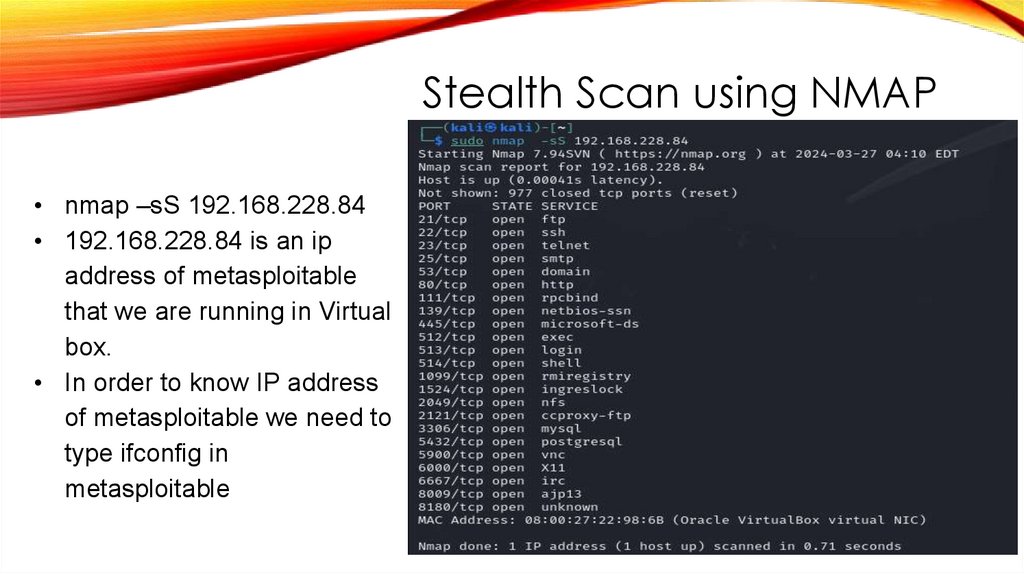
Stealth Scan using NMAP• nmap –sS 192.168.228.84
• 192.168.228.84 is an ip
address of metasploitable
that we are running in Virtual
box.
• In order to know IP address
of metasploitable we need to
type ifconfig in
metasploitable
21.
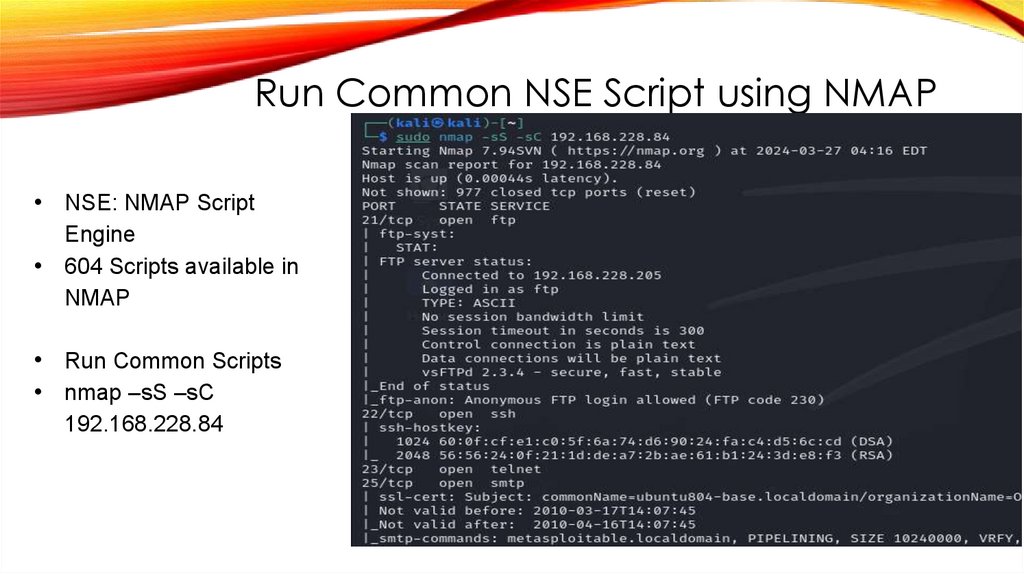
Run Common NSE Script using NMAP• NSE: NMAP Script
Engine
• 604 Scripts available in
NMAP
• Run Common Scripts
• nmap –sS –sC
192.168.228.84
22.
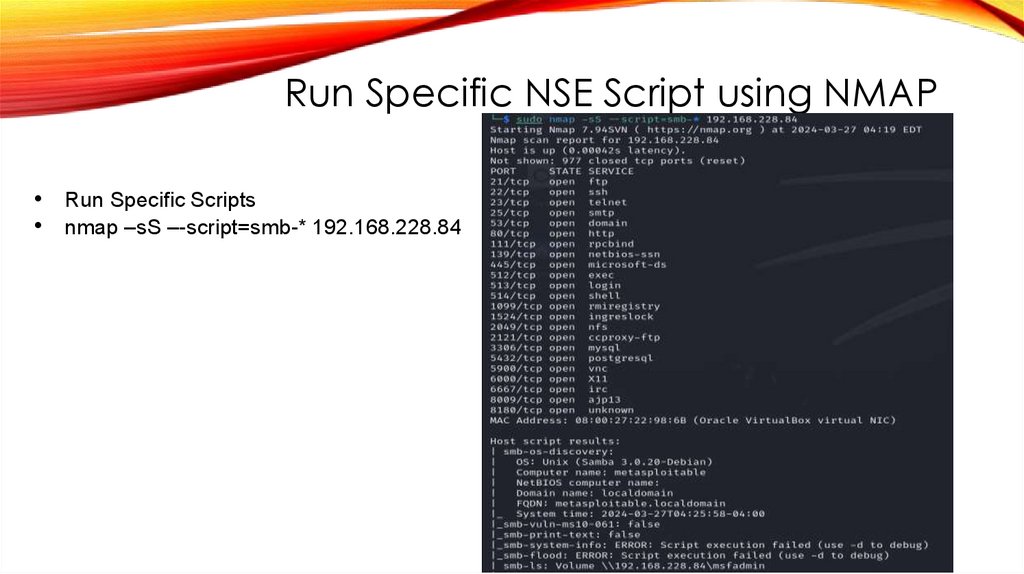
Run Specific NSE Script using NMAP• Run Specific Scripts
• nmap –sS –-script=smb-* 192.168.228.84
23.
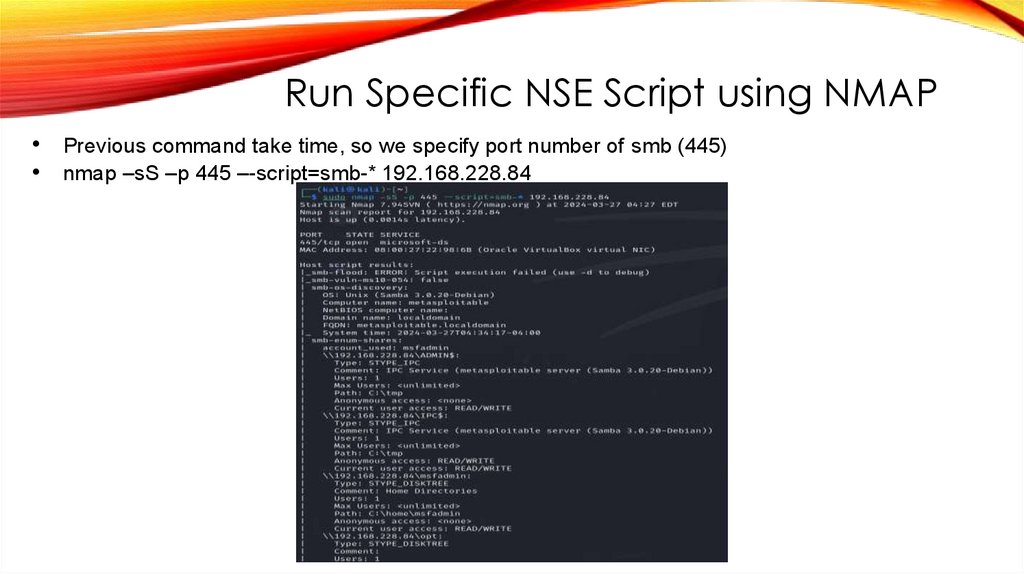
Run Specific NSE Script using NMAP• Previous command take time, so we specify port number of smb (445)
• nmap –sS –p 445 –-script=smb-* 192.168.228.84
24.
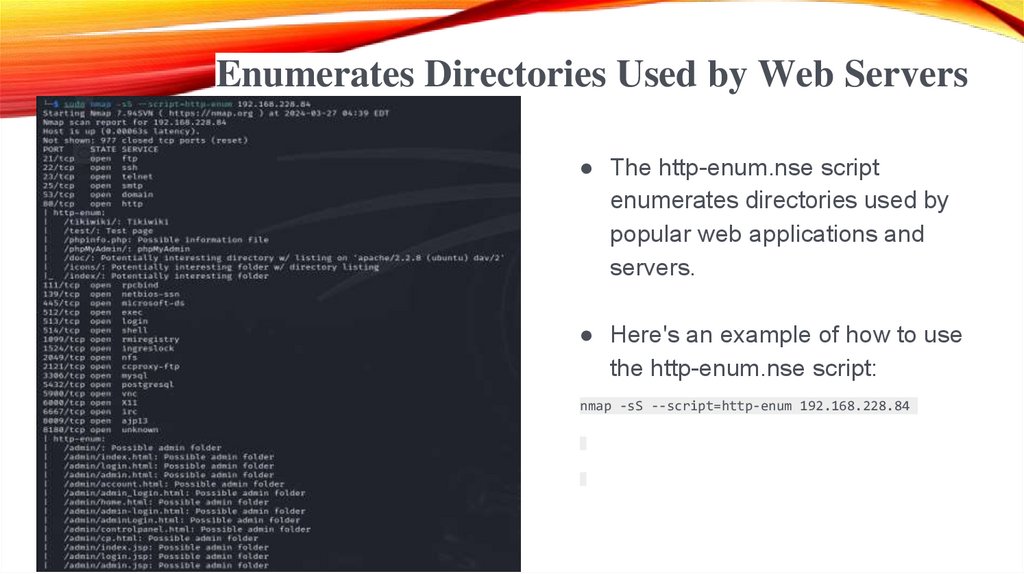
Enumerates Directories Used by Web Servers● The http-enum.nse script
enumerates directories used by
popular web applications and
servers.
● Here's an example of how to use
the http-enum.nse script:
nmap -sS --script=http-enum 192.168.228.84
25.
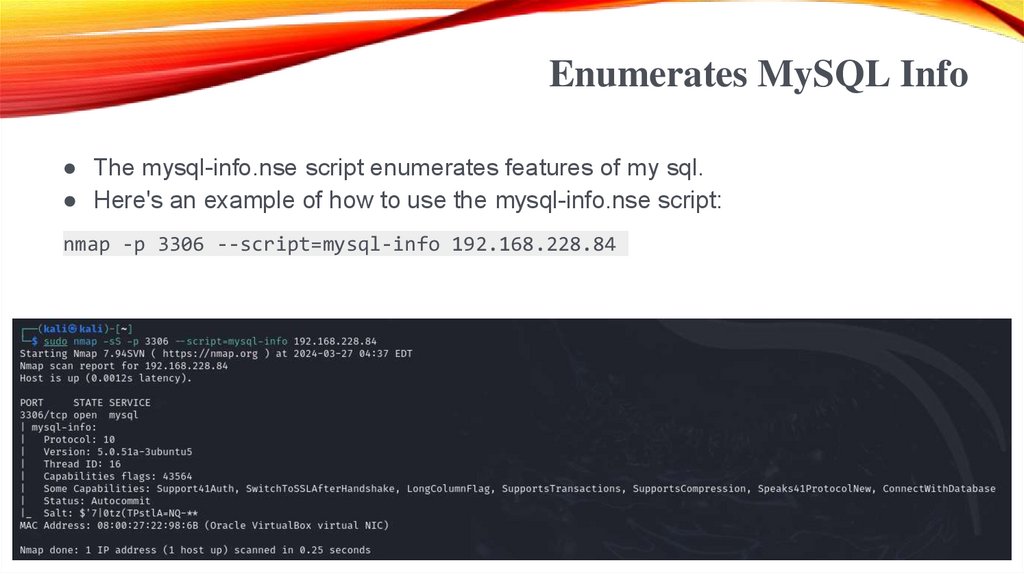
Enumerates MySQL Info● The mysql-info.nse script enumerates features of my sql.
● Here's an example of how to use the mysql-info.nse script:
nmap -p 3306 --script=mysql-info 192.168.228.84
26.
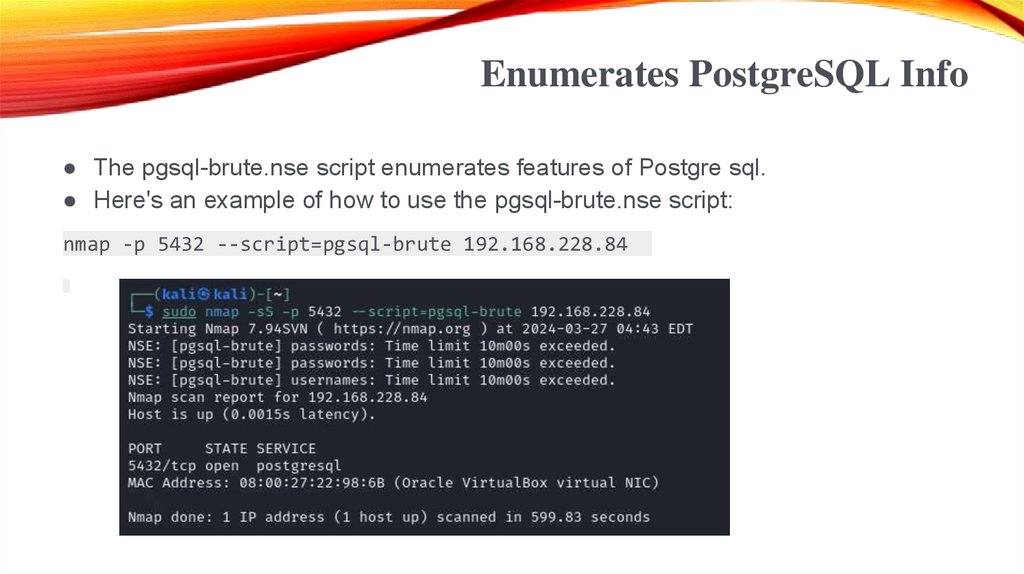
Enumerates PostgreSQL Info● The pgsql-brute.nse script enumerates features of Postgre sql.
● Here's an example of how to use the pgsql-brute.nse script:
nmap -p 5432 --script=pgsql-brute 192.168.228.84
27.
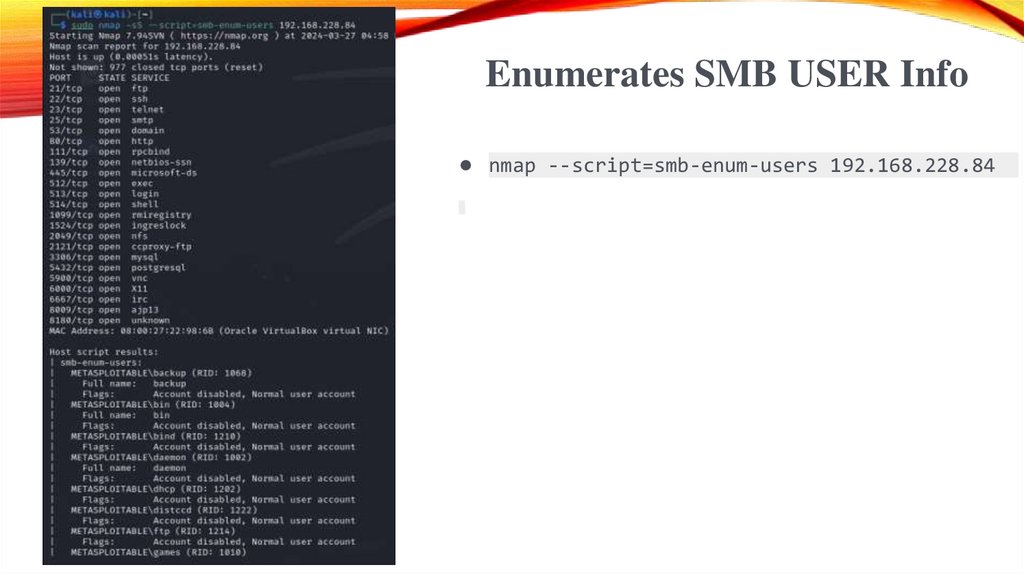
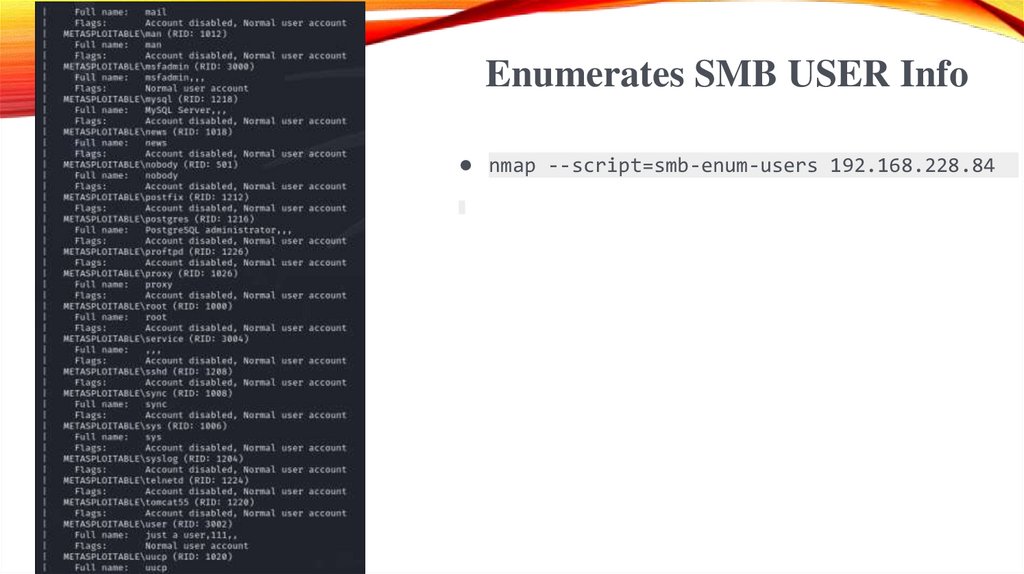
Enumerates SMB USER Info● nmap --script=smb-enum-users 192.168.228.84
28.
Enumerates SMB USER Info● nmap --script=smb-enum-users 192.168.228.84
29.
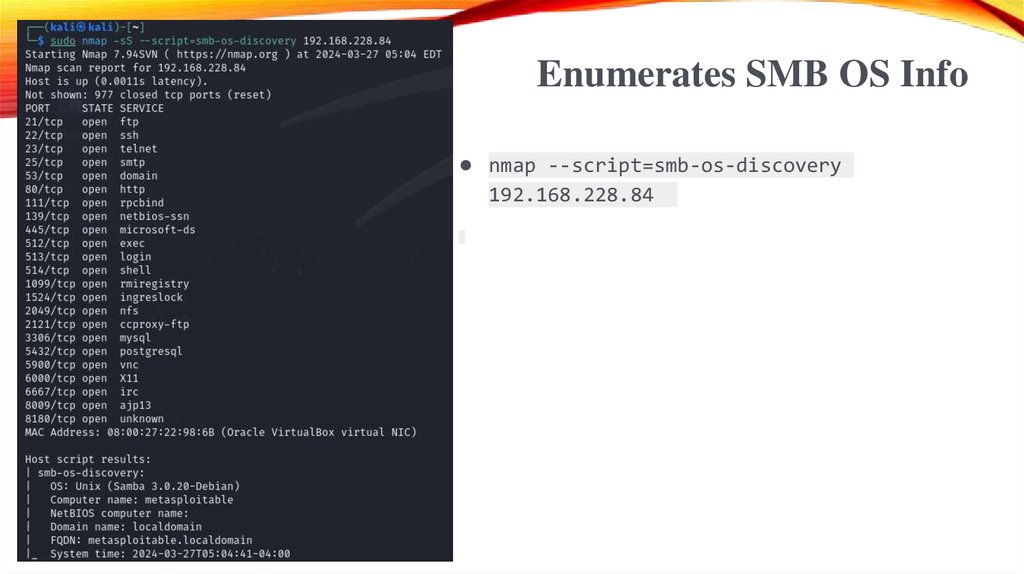
Enumerates SMB OS Info● nmap --script=smb-os-discovery
192.168.228.84







 Информатика
Информатика








