Похожие презентации:
Web parameter poisoning using burp suite
1.
Week 7 PracticeWeb parameter poisoning using burp suite
(Assignment Week 7: Change the price of all item to 1 USD on ecommerce shopping cart)
2.
Intercept WebTraffic using Burp
proxy
3.
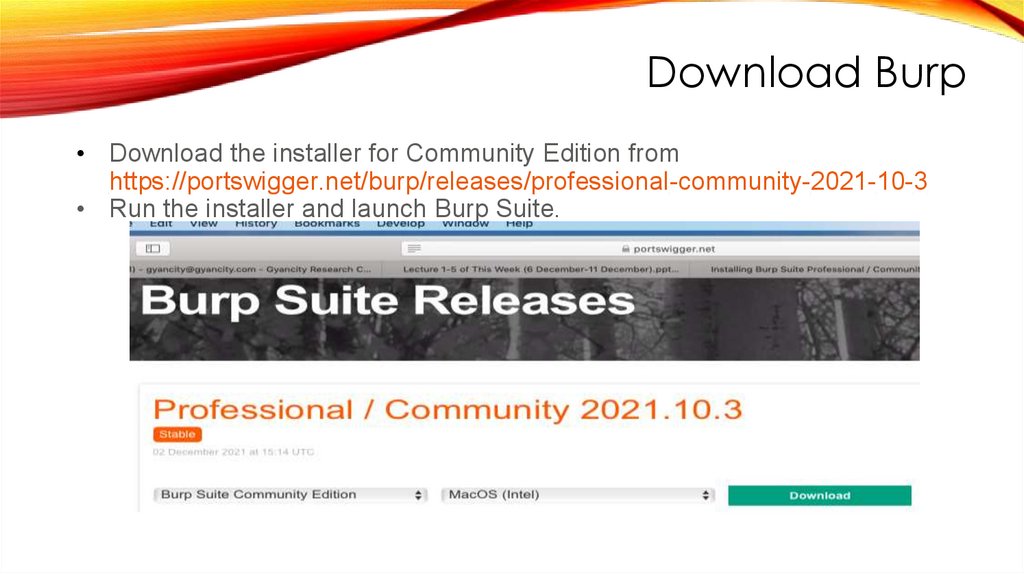
Download Burp• Download the installer for Community Edition from
https://portswigger.net/burp/releases/professional-community-2021-10-3
• Run the installer and launch Burp Suite.
4.
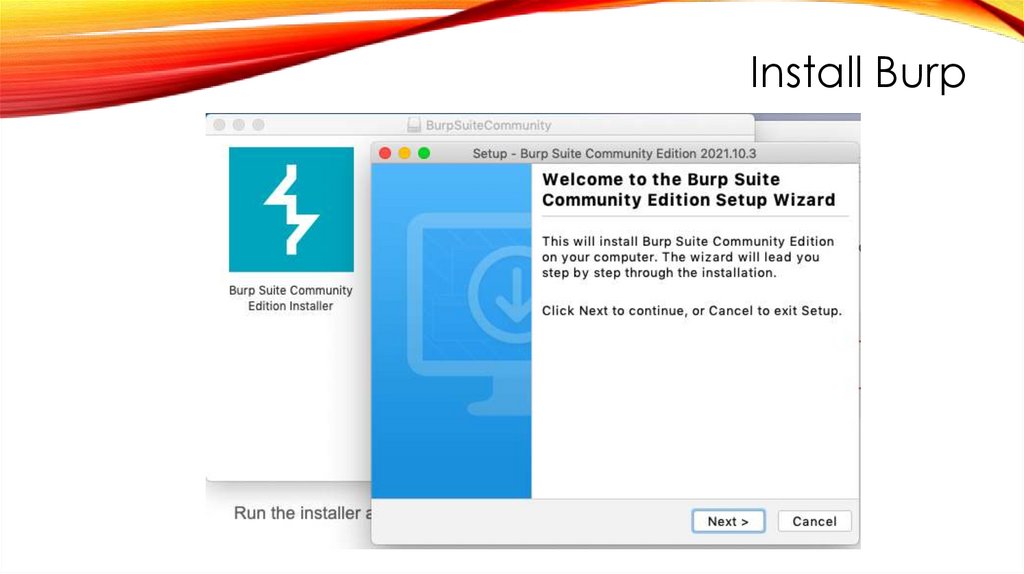
Install Burp5.
Install Burp6.
Install Burp7.
Intercept HTTP traffic with Burp Proxy• Burp Proxy allows us to intercept HTTP
requests and responses sent between our
browser
and
the
target
server.
• This enables us to study how the website
behaves when we perform different
actions.
8.
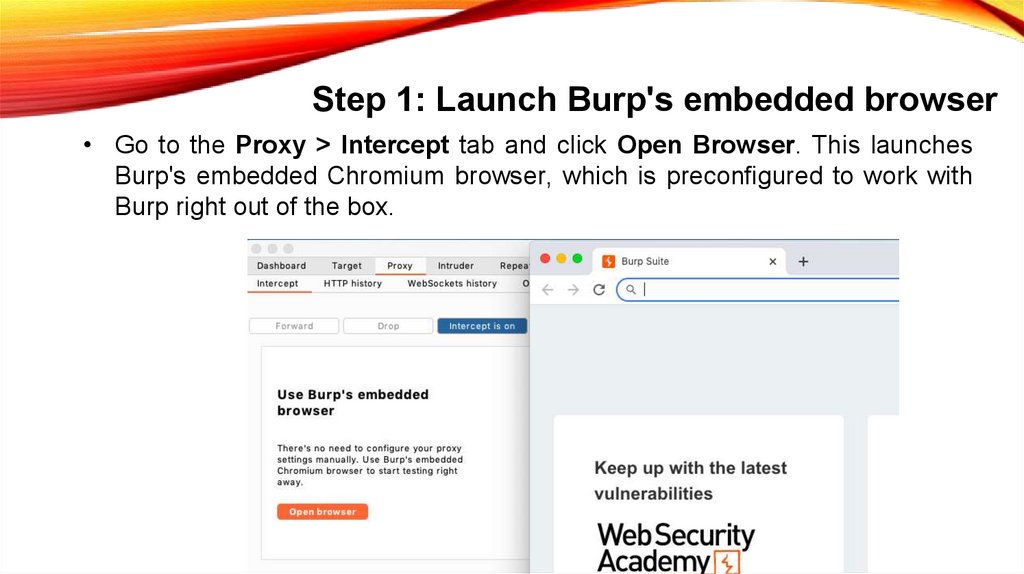
Step 1: Launch Burp's embedded browser• Go to the Proxy > Intercept tab and click Open Browser. This launches
Burp's embedded Chromium browser, which is preconfigured to work with
Burp right out of the box.
9.
Step 2: Intercept a request• In Burp, notice that the Intercept is on button is selected.
10.
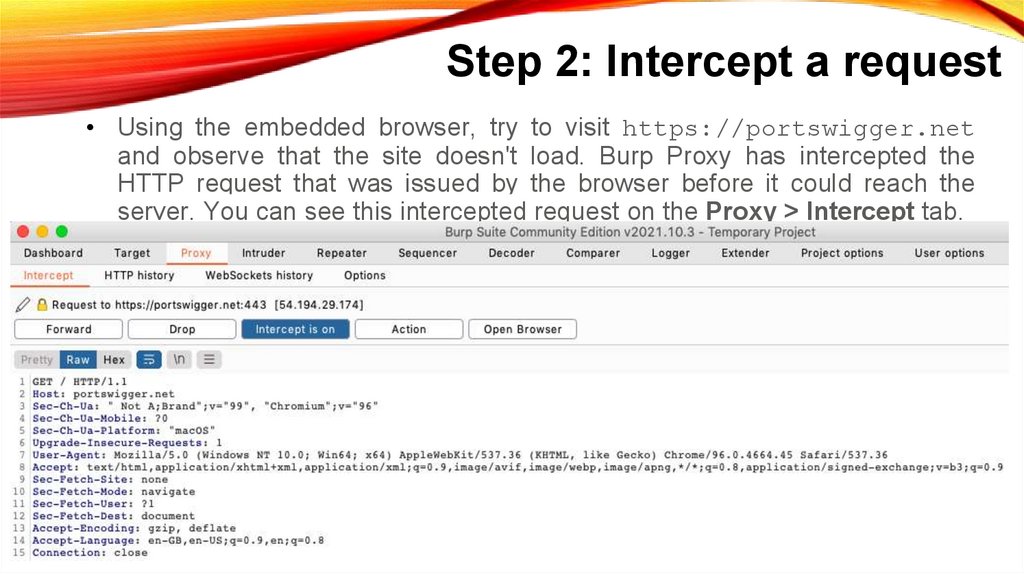
Step 2: Intercept a request• Using the embedded browser, try to visit https://portswigger.net
and observe that the site doesn't load. Burp Proxy has intercepted the
HTTP request that was issued by the browser before it could reach the
server. You can see this intercepted request on the Proxy > Intercept tab.
11.
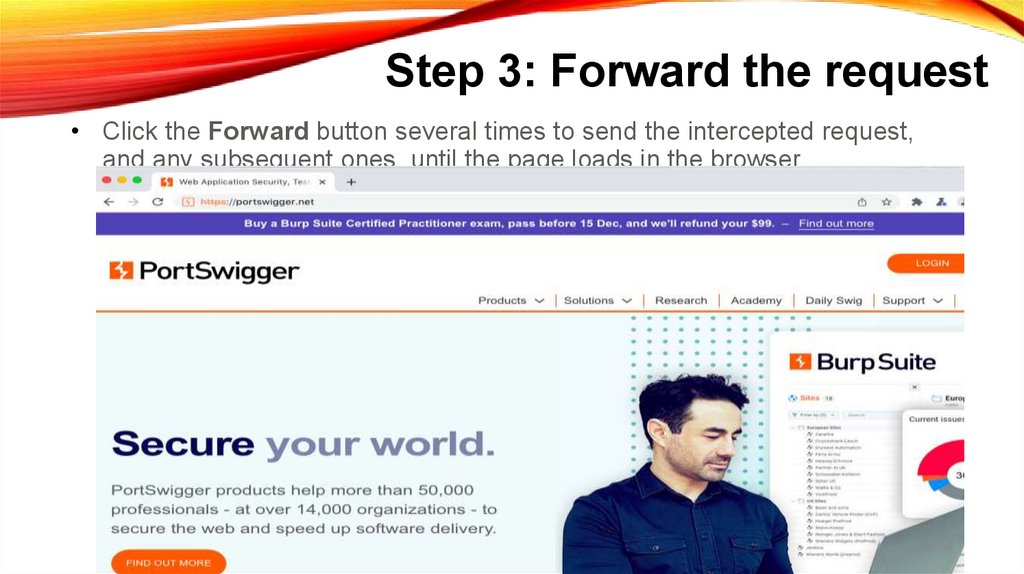
Step 3: Forward the request• Click the Forward button several times to send the intercepted request,
and any subsequent ones, until the page loads in the browser.
12.
Step 4: Switch off interception• Due to the number of requests browsers typically send, you often won't
want to intercept every single one of them. Click the Intercept is on button
so that it now says Intercept is off.
• Go back to the embedded browser and confirm that you can now interact
with the site as normal.
13.
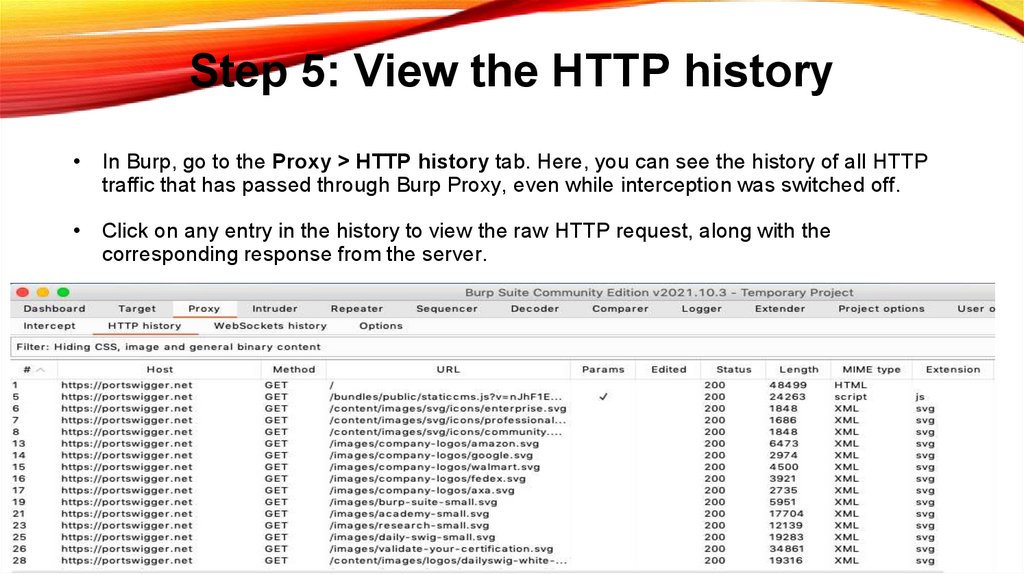
Step 5: View the HTTP historyIn Burp, go to the Proxy > HTTP history tab. Here, you can see the history of all HTTP
traffic that has passed through Burp Proxy, even while interception was switched off.
Click on any entry in the history to view the raw HTTP request, along with the
corresponding response from the server.
14.
Web Forensics:Web Parameter Poisoning using Burp Suite (Change
the Item Name in Shopping Cart on E-Commerce Website before
checkout)
15.
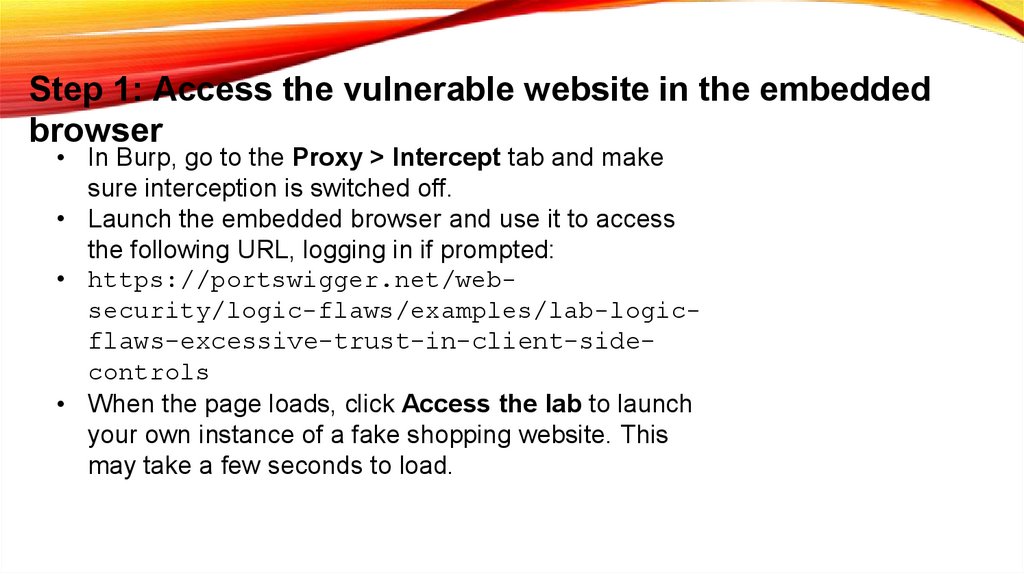
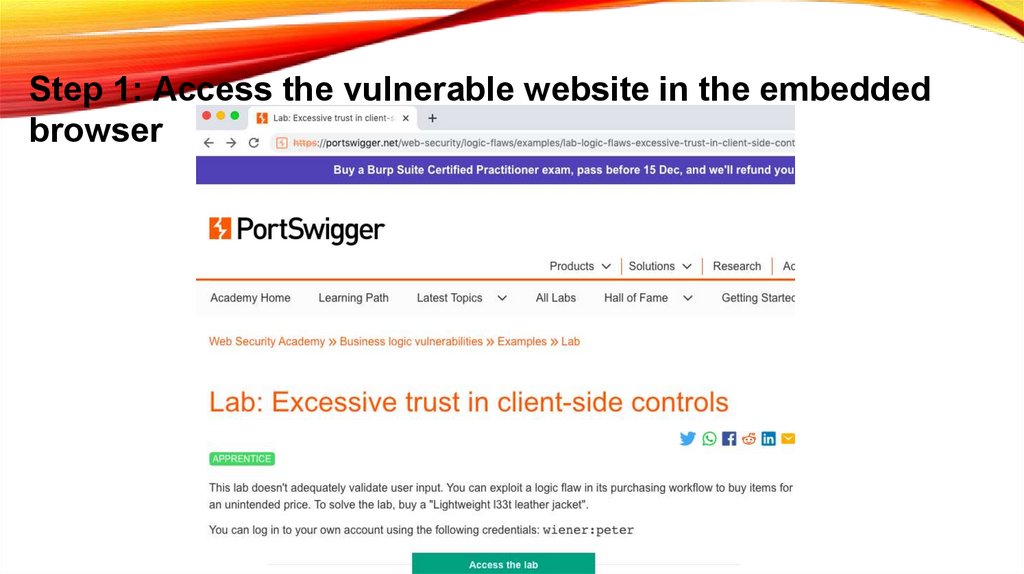
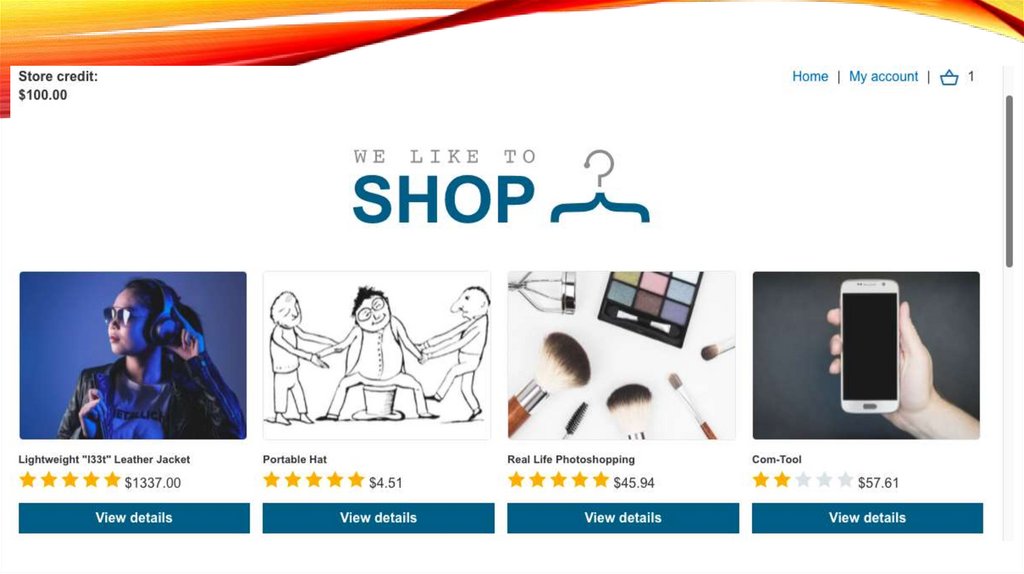
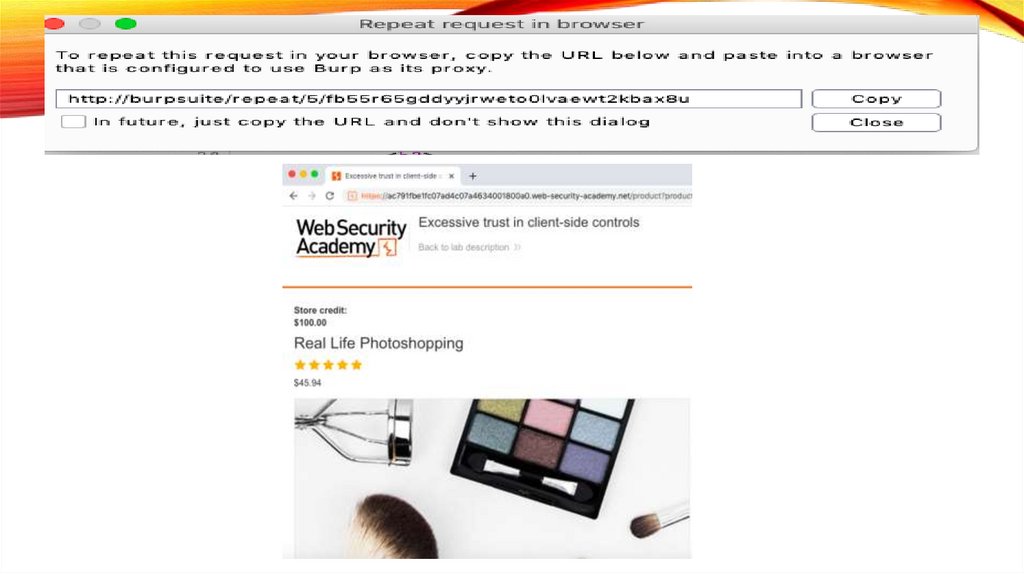
Step 1: Access the vulnerable website in the embeddedbrowser
• In Burp, go to the Proxy > Intercept tab and make
sure interception is switched off.
• Launch the embedded browser and use it to access
the following URL, logging in if prompted:
• https://portswigger.net/websecurity/logic-flaws/examples/lab-logicflaws-excessive-trust-in-client-sidecontrols
• When the page loads, click Access the lab to launch
your own instance of a fake shopping website. This
may take a few seconds to load.
16.
Step 1: Access the vulnerable website in the embeddedbrowser
17.
Step 1: Access the vulnerable website in the embeddedbrowser
[email protected]
3Sk\(AAK}%tX~aF6MnQPf3p4Ag4Gs(9@
18.
19.
20.
21.
22.
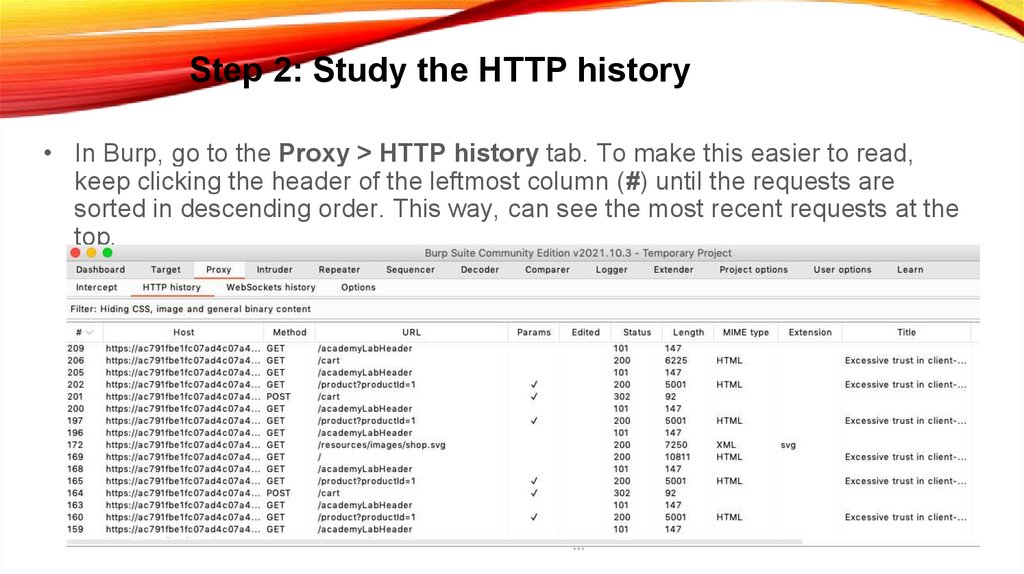
Step 2: Study the HTTP history• In Burp, go to the Proxy > HTTP history tab. To make this easier to read,
keep clicking the header of the leftmost column (#) until the requests are
sorted in descending order. This way, can see the most recent requests at the
top.
23.
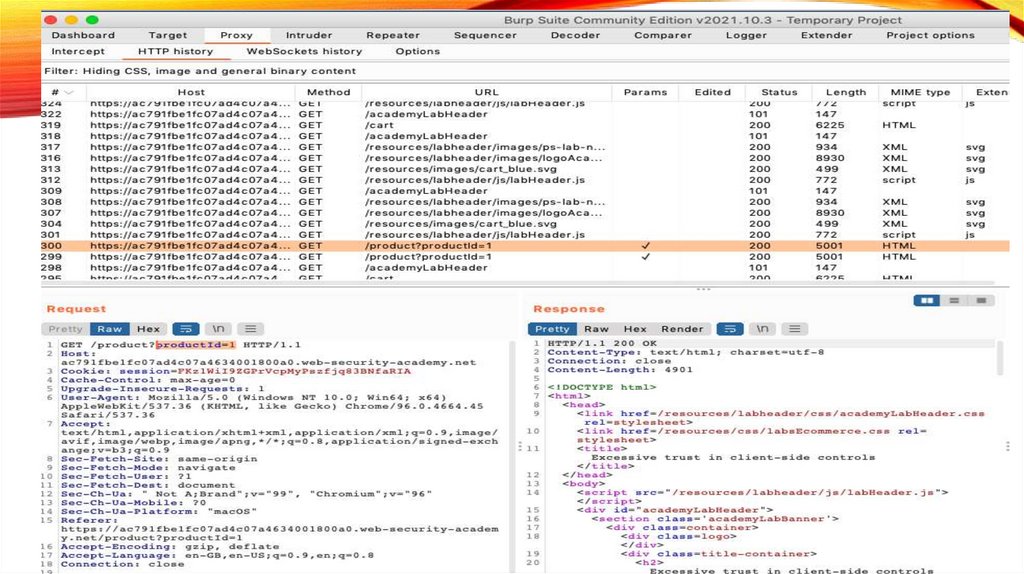
Step 3: Identify an interestingrequest
• Notice that each time you access a product page, the browser sends a GET
/product request with a productId query parameter.
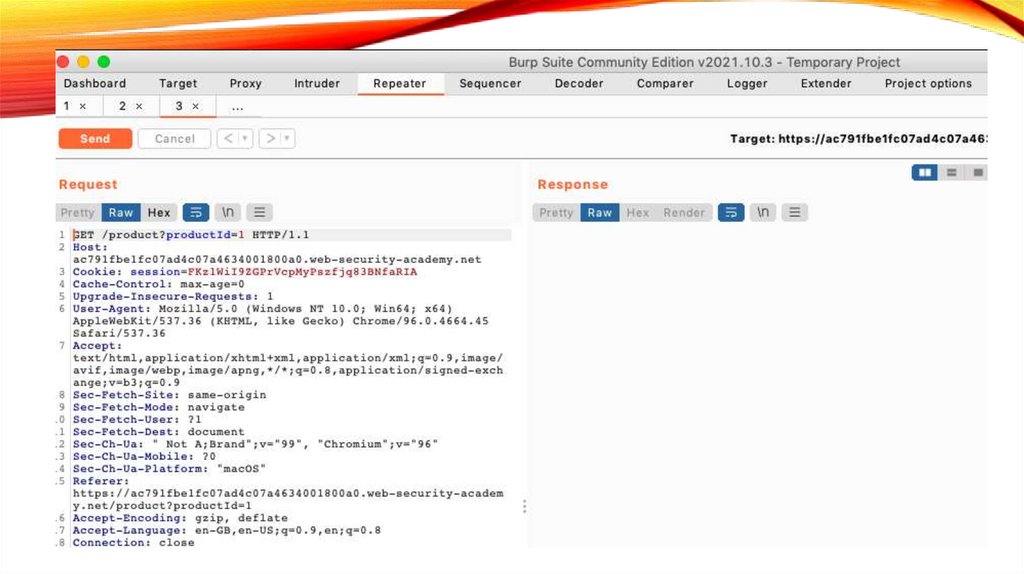
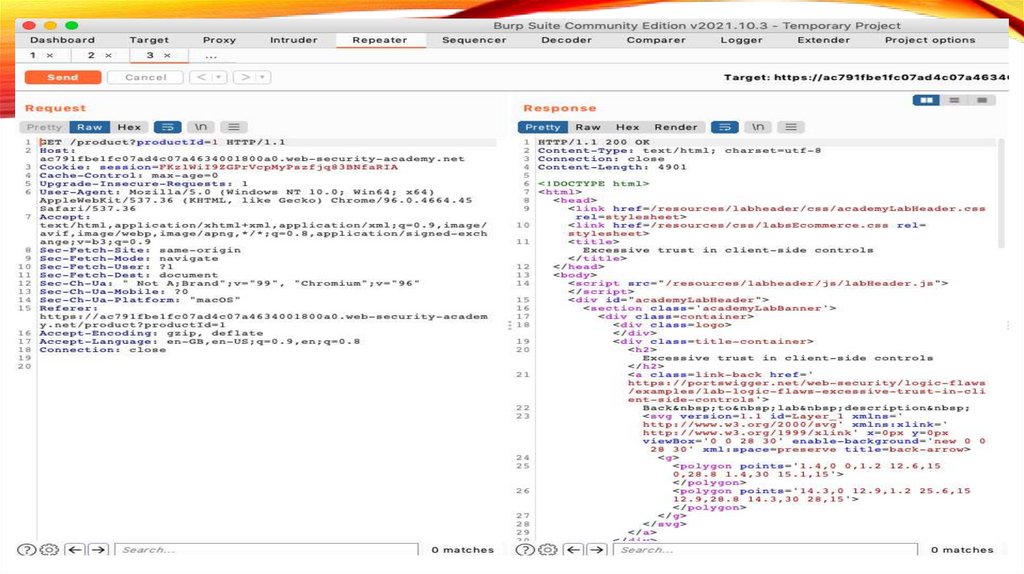
24.
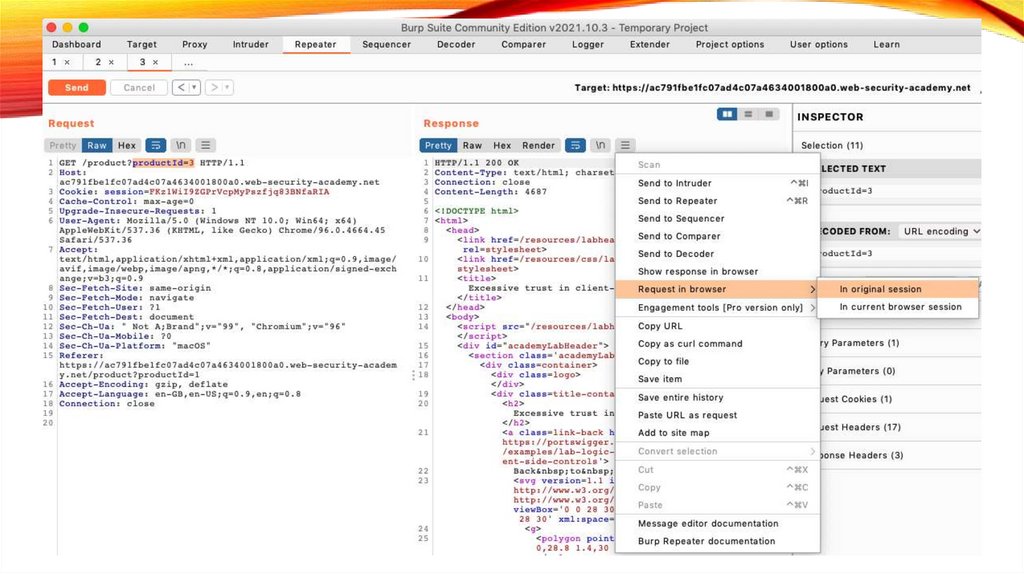
Step 4: Send the request toBurp Repeater
• Right-click on any of the GET /product?productId=[...] requests
and select Send to Repeater.
25.
26.
27.
28.
29.
30.
31.
Web Forensics:Web Parameter Poisoning using Burp Suite (Change
the Item Number in Shopping Cart on E-Commerce Website before
checkout)
32.
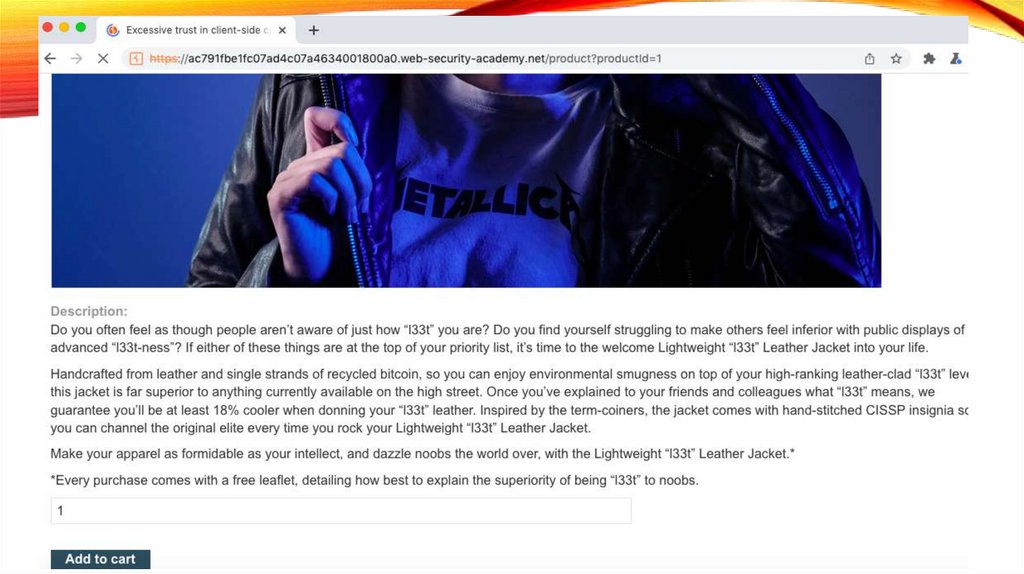
Open Leather Jacket33.
Add To CartClick on Cart Symbol
34.
Add To Cart35.
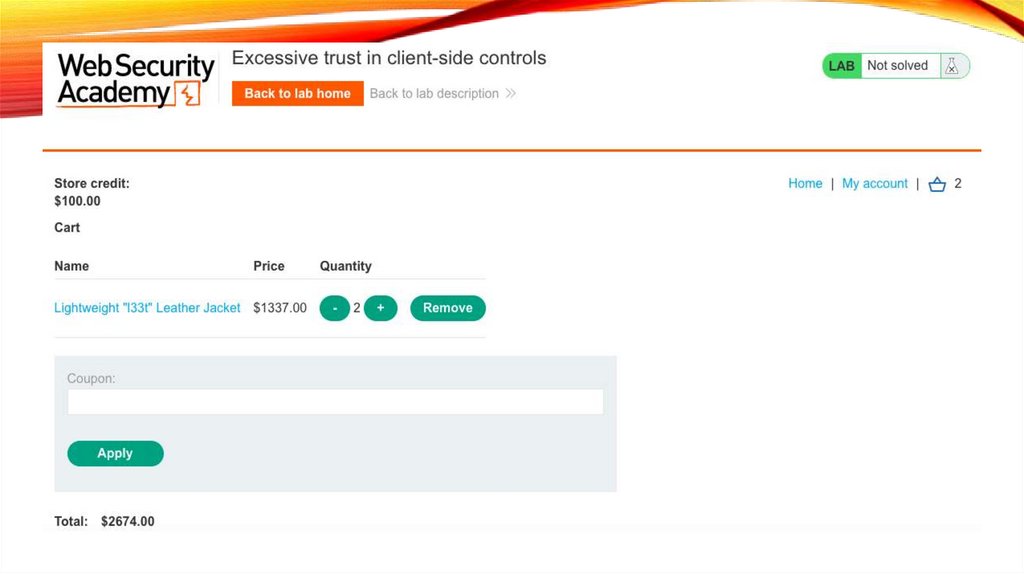
We Make Intercept is On36.
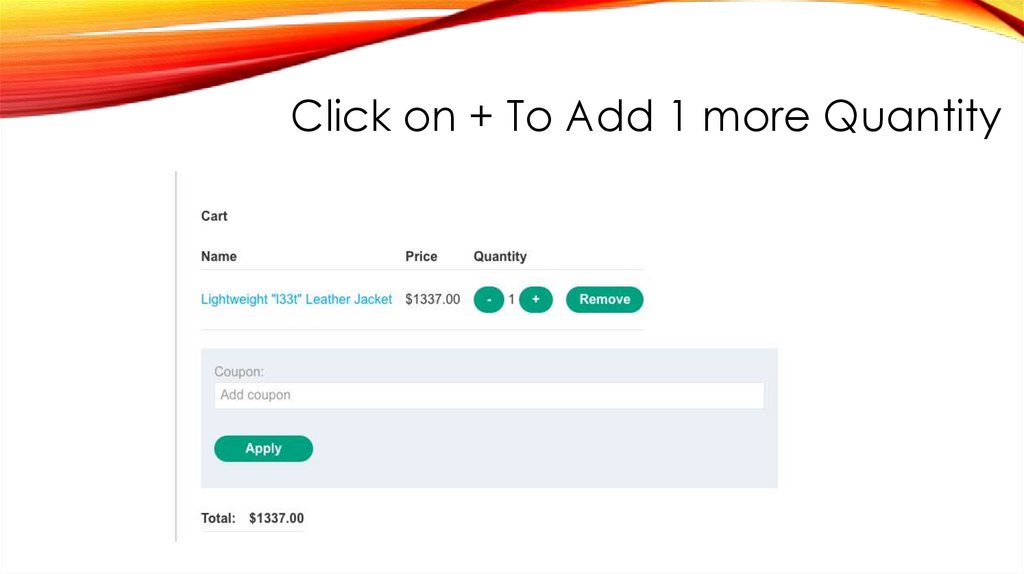
Click on + To Add 1 more Quantity37.
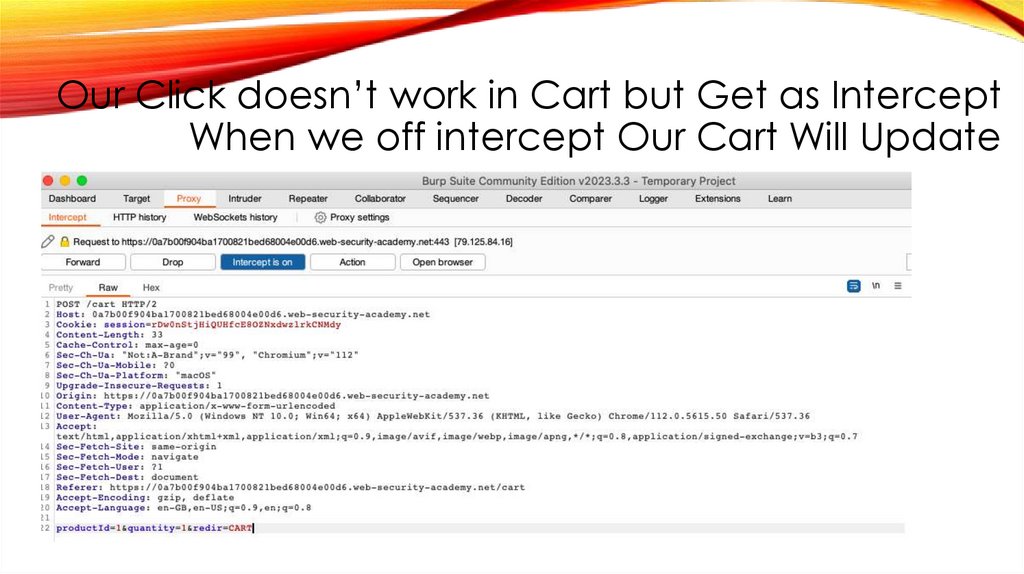
Our Click doesn’t work in Cart but Get as InterceptWhen we off intercept Our Cart Will Update
38.
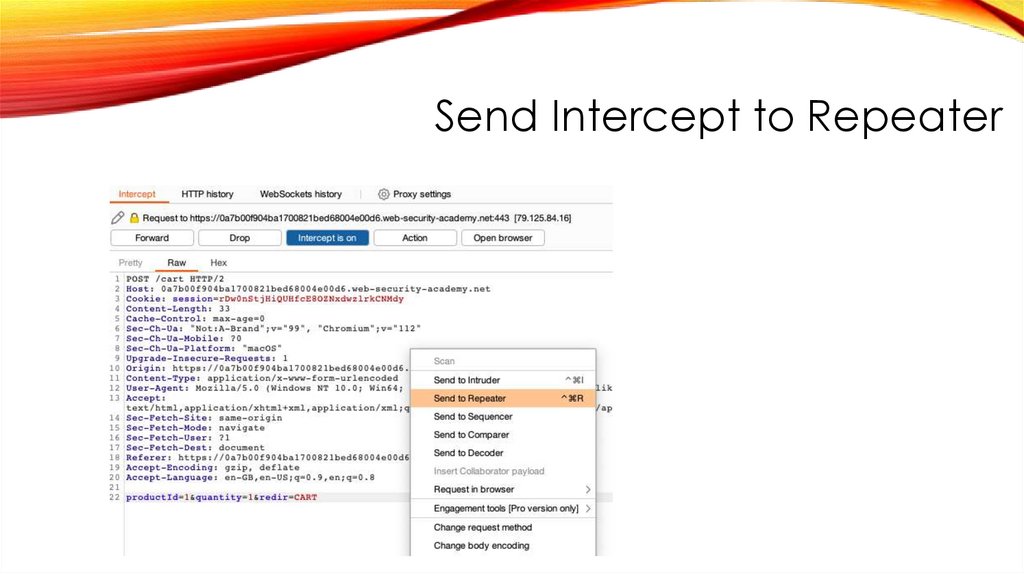
Send Intercept to Repeater39.
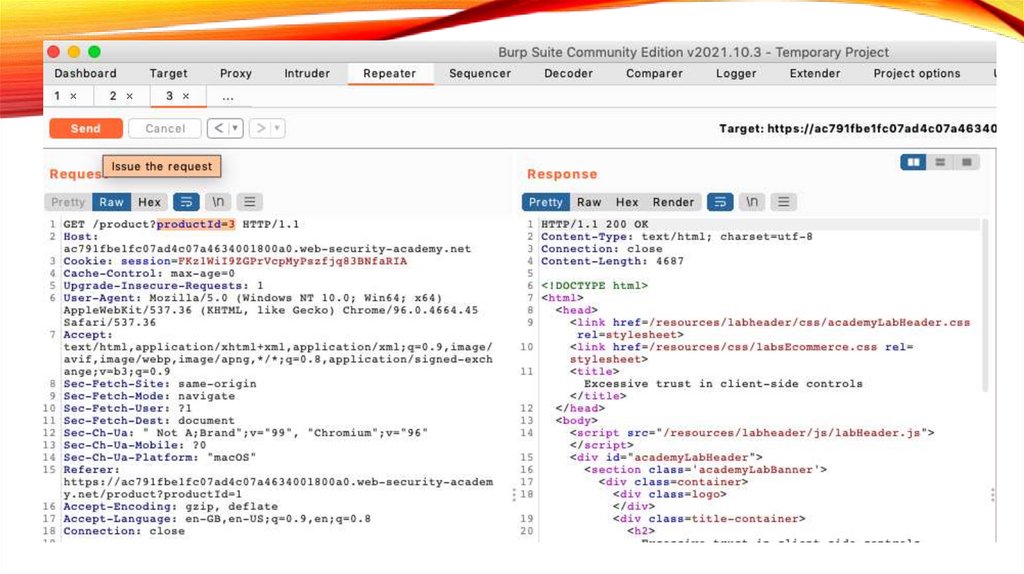
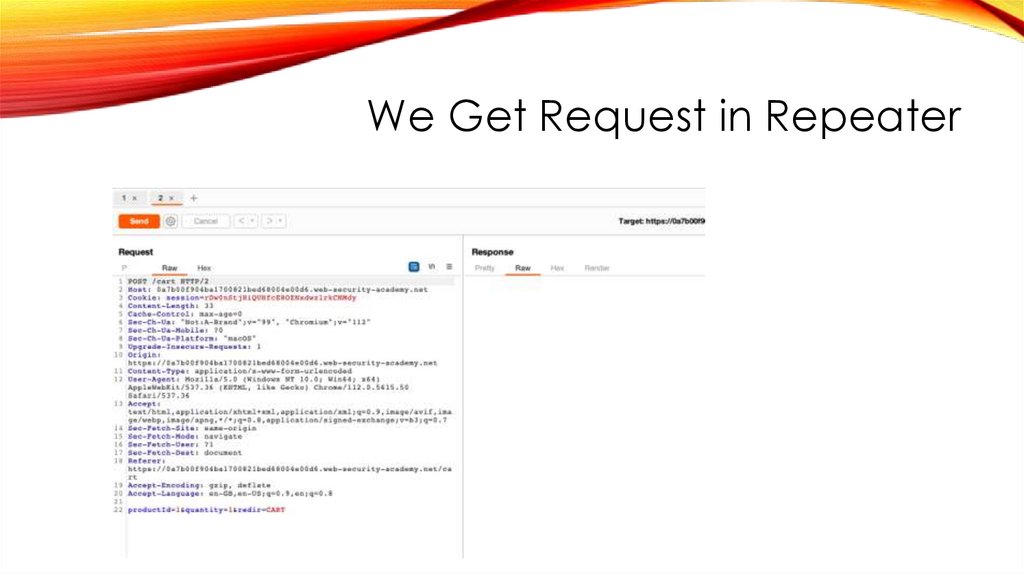
We Get Request in Repeater40.
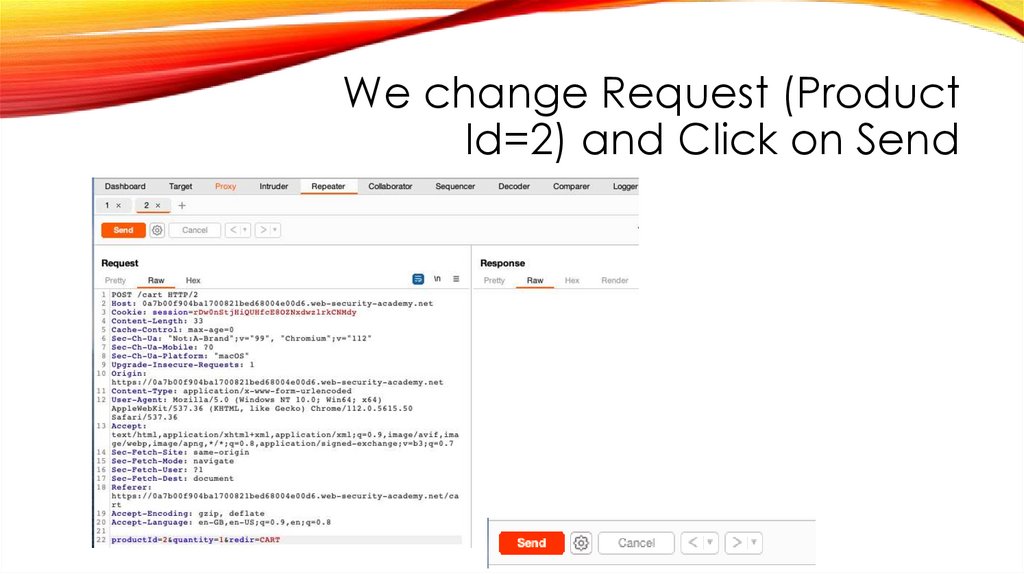
We change Request (ProductId=2) and Click on Send
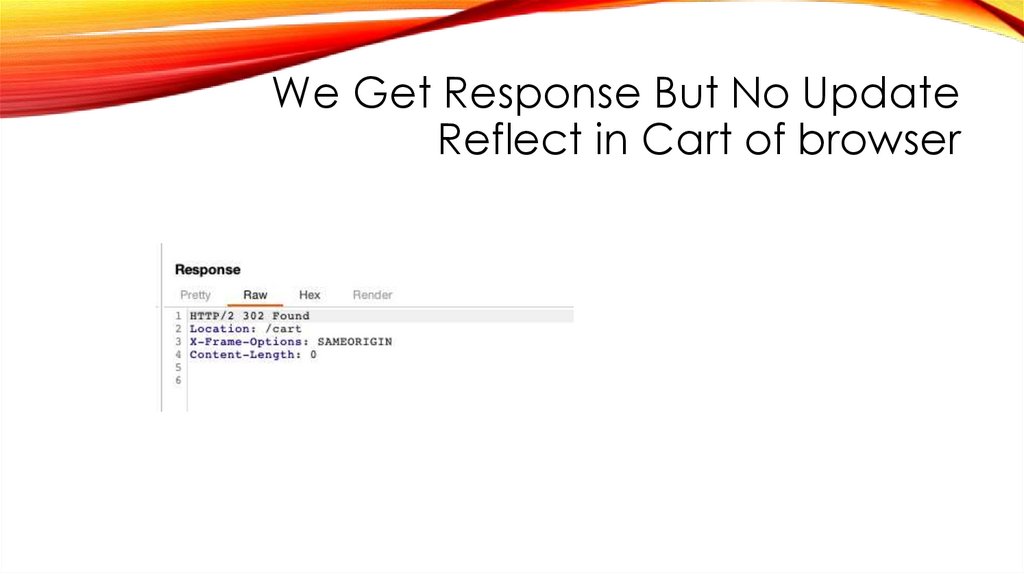
41.
We Get Response But No UpdateReflect in Cart of browser
42.
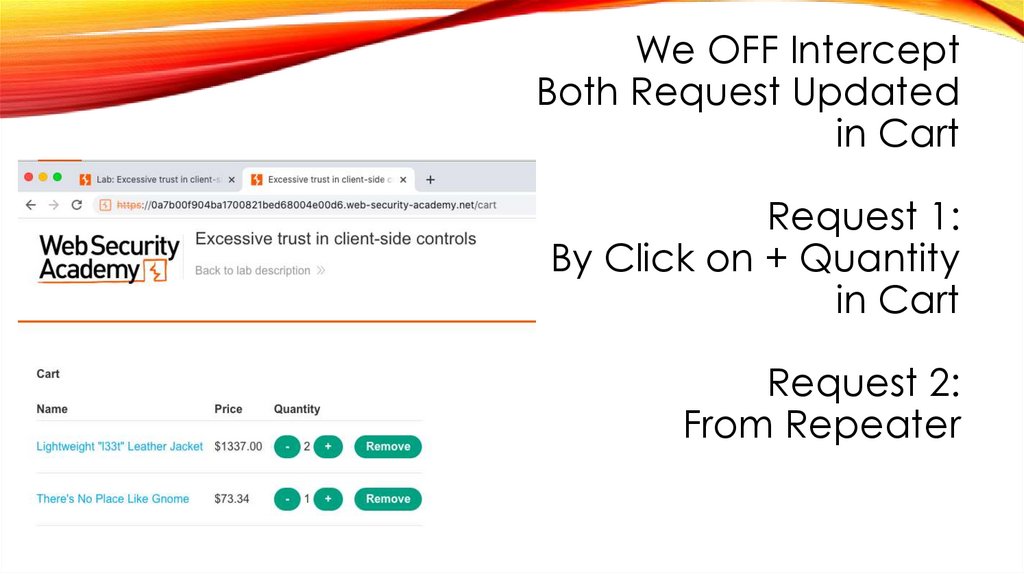
We OFF Intercept43.
We OFF InterceptBoth Request Updated
in Cart
Request 1:
By Click on + Quantity
in Cart
Request 2:
From Repeater
44.
We ON InterceptRequest 2:
From Repeater
By Changing Product
Id=3
And Click Send 2 Time
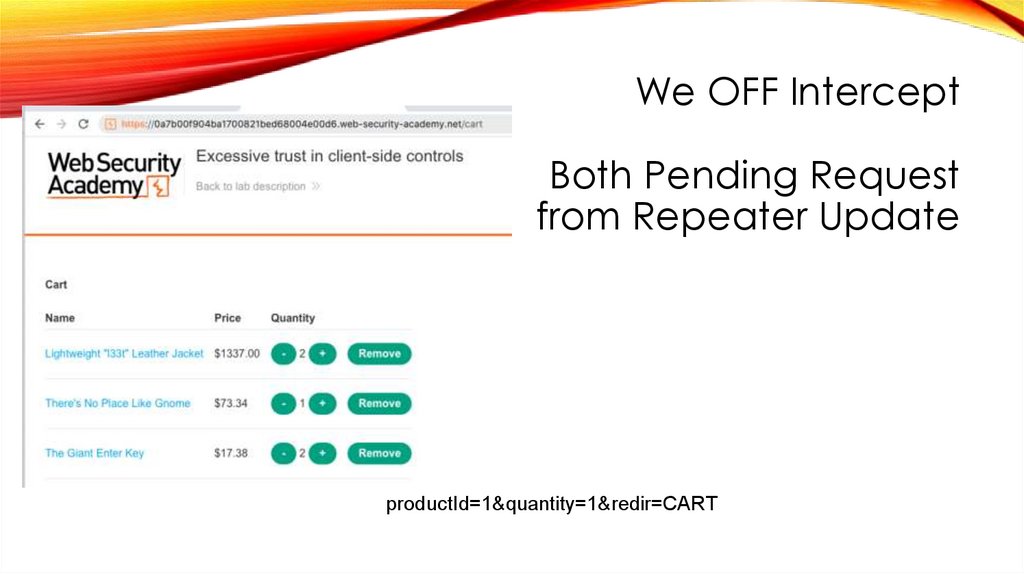
45.
We OFF InterceptBoth Pending Request
from Repeater Update
productId=1&quantity=1&redir=CART
46.
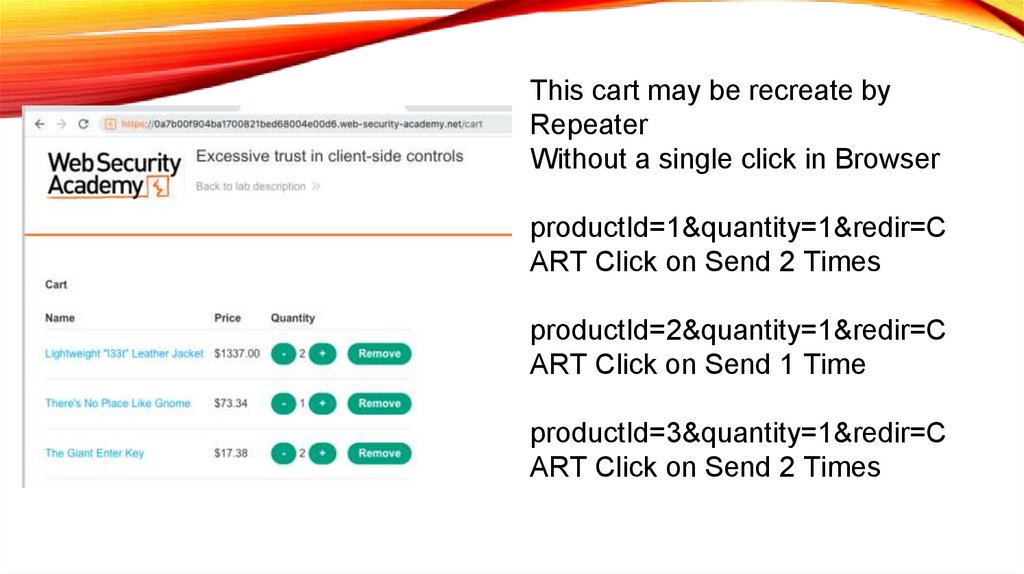
This cart may be recreate byRepeater
Without a single click in Browser
productId=1&quantity=1&redir=C
ART Click on Send 2 Times
productId=2&quantity=1&redir=C
ART Click on Send 1 Time
productId=3&quantity=1&redir=C
ART Click on Send 2 Times
47.
Web Forensics:Web Parameter Poisoning using Burp Suite (Change
the Price in Shopping Cart on E-Commerce Website before checkout)
48.
IN REPEATER&price=100 in same line and it
will set price of jacket to 1 USD
(100 cent)
productId=1&quantity=1&price=1
00&redir=CART Click on Send
49.
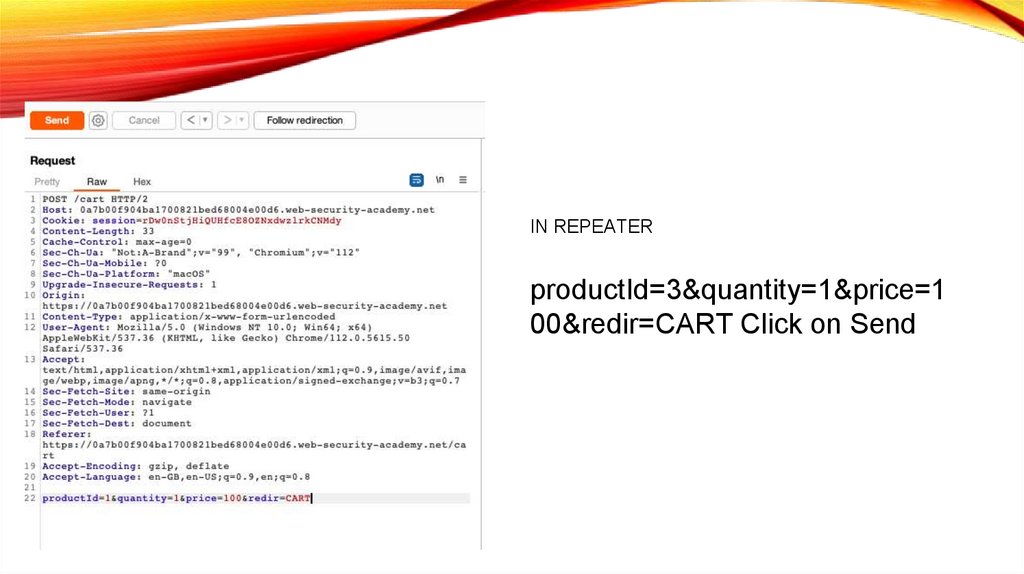
IN REPEATERproductId=3&quantity=1&price=1
00&redir=CART Click on Send
50.
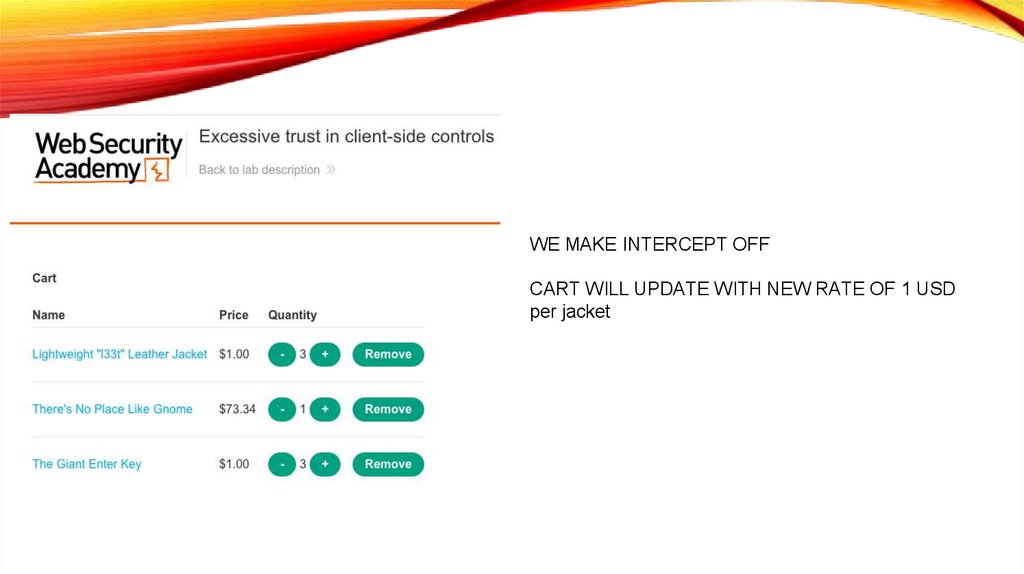
WE MAKE INTERCEPT OFFCART WILL UPDATE WITH NEW RATE OF 1 USD
per jacket




















 Интернет
Интернет








