Похожие презентации:
Digital Certificates
1. Digital Certificates
Presented bySunit Chauhan
Copyright, 1996 © Dale Carnegie & Associates, Inc.
2. Basic Terms
• Public Key Cryptographic Standards, PKCSA collection of 12 papers PKCS #1 to PKCS #12
developed by RSA Labs and representatives from
the academia and industry.
PKCS #1
RSA Algorithm
PKCS #3
Diffie-Hellman Algorithm
PKCS #7
Cryptographic Message Syntax Std
PKCS #10
Key Certification Request
PKCS #11
Standard API for developers
PKCS #12
Certificate Interchange Format
PKCS #13
Elliptic Curves Algorithm
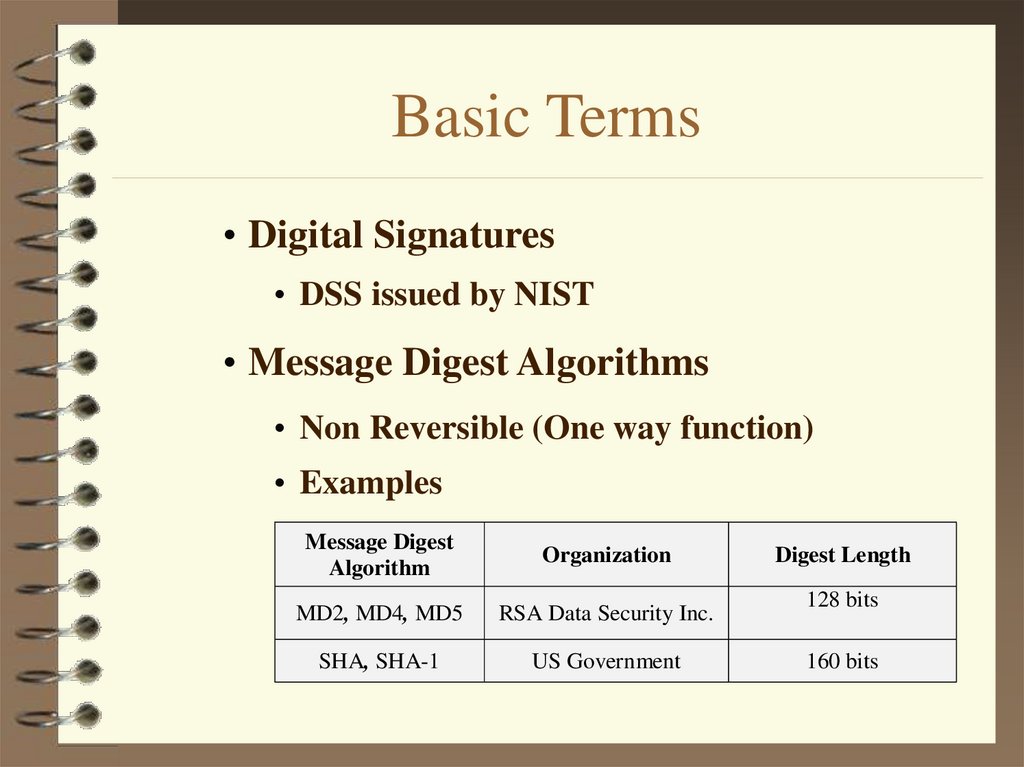
3. Basic Terms
• Digital Signatures• DSS issued by NIST
• Message Digest Algorithms
• Non Reversible (One way function)
• Examples
Message Digest
Algorithm
Organization
MD2, MD4, MD5
RSA Data Security Inc.
SHA, SHA-1
US Government
Digest Length
128 bits
160 bits
4. Digital Certificates
Certificates are the framework foridentification information, and bind
identities with public keys.
They provide a foundation for
• identification ,
• authentication and
• non-repudiation.
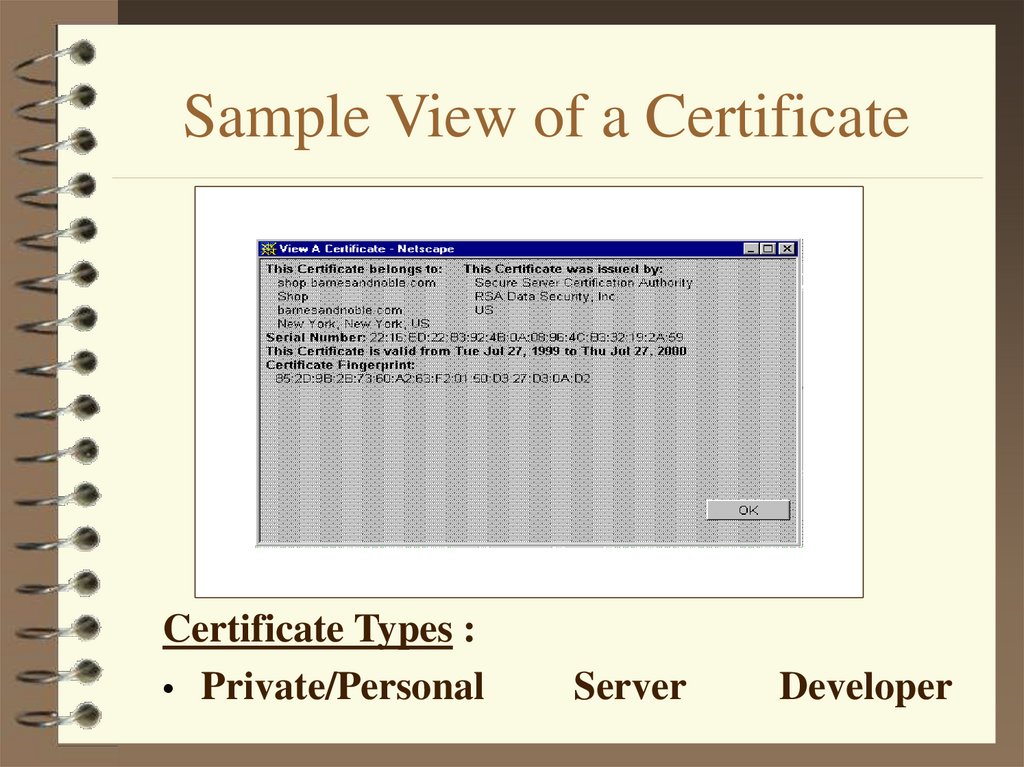
5. Sample View of a Certificate
Certificate Types :• Private/Personal
Server
Developer
6.
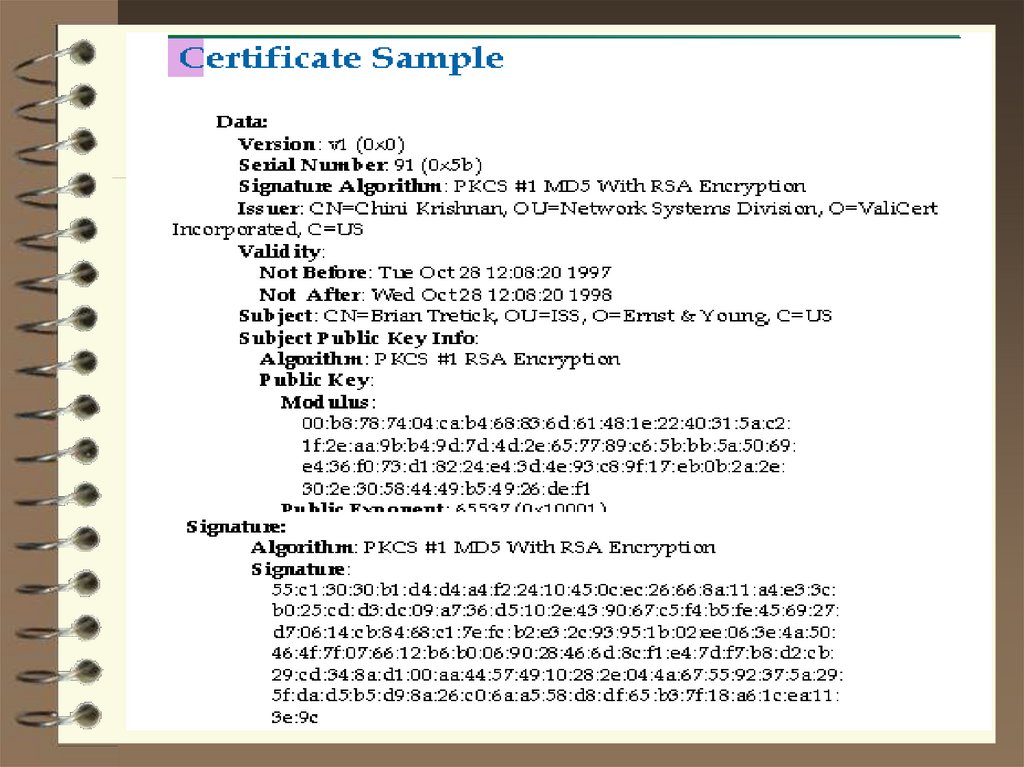
7. X.509 v3 Certificate Format
• Version• Certificate Serial Number
• Signature Algorithm Identifier
• Issuer Name
• Validity Period
• Subject Name
• Subject Public Key Information
• Optional Fields
8. X.509 v3 Extension Fields
• Associate additional information forsubjects ,public keys ,managing
certification hierarchy and certificate
revocation lists.
• Extension type
• Extension value
• Criticality indicator
9. X.509 Profiles
Tailor the authentication model of X.509 tospecific environments based on Risk perception.
• IETF Public Key Infrastructure (PKIX -1) :
Application-independent certificate based key
distribution mechanism.
• SET Standard :
Secure messaging for payment-service transactions
over open-networks.
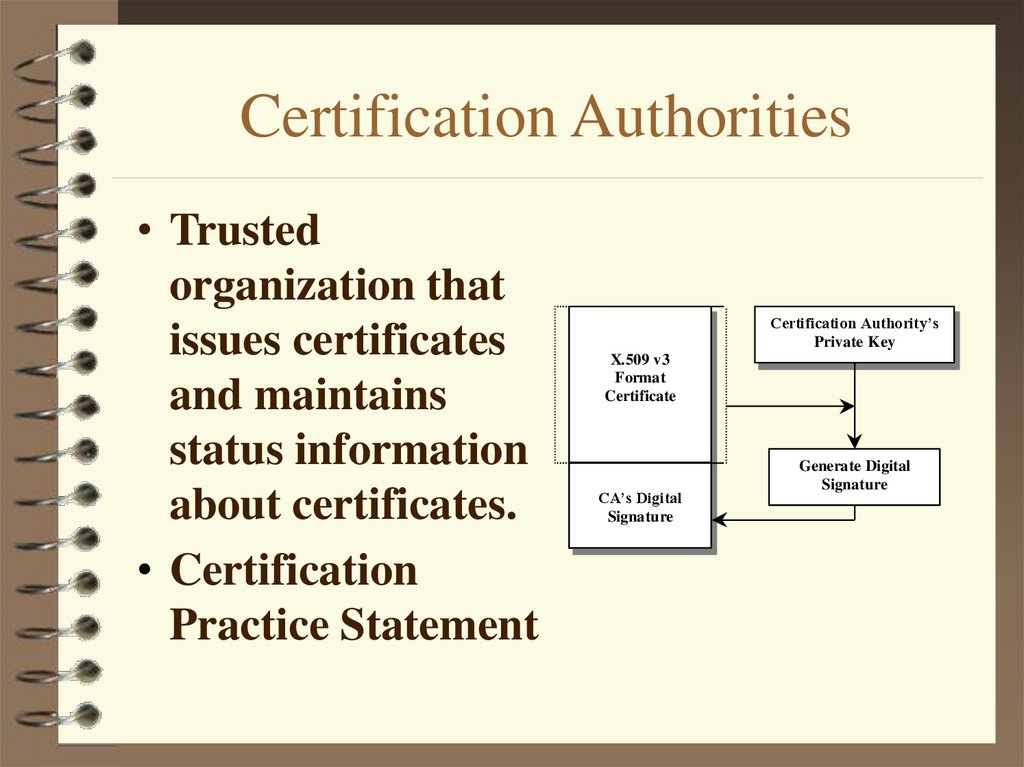
10. Certification Authorities
• Trustedorganization that
issues certificates
and maintains
status information
about certificates.
• Certification
Practice Statement
Certification Authority’s
Private Key
X.509 v3
Format
Certificate
CA’s Digital
Signature
Generate Digital
Signature
11. How Digital Certificates work?
• Generate Public and Private Keys.• Get Certificate from the CA
• Sign the document/page using the private
key.
• Send signed document over open
networks along with the CA’s certificate.
• Recipient verifies using the signing CA’s
public key
• Trust Chain and Fingerprints
12. Web Server Security
• Server Authentication using SSL• Information to/from the correct Web Site
• Information in encrypted form
• Setting up SSL on a Web Site
• Create a Server Certificate Request
• Obtain the Server Certificate from a CA/locally
• Install it on the Web Server
• Establishing an SSL connection
• Need root certificate of the issuing CA
13. Client Authentication
• Anonymous• Basic
• Challenge Response (NT)
• SSL Client Authentication
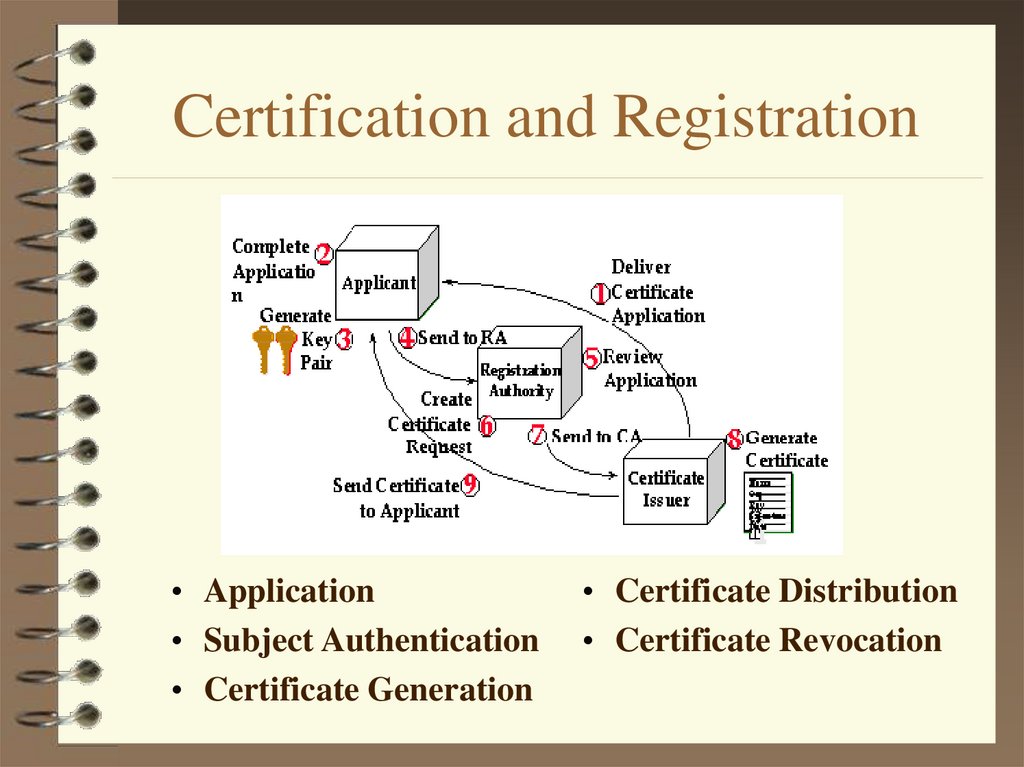
14. Certification and Registration
• Application• Subject Authentication
• Certificate Generation
• Certificate Distribution
• Certificate Revocation
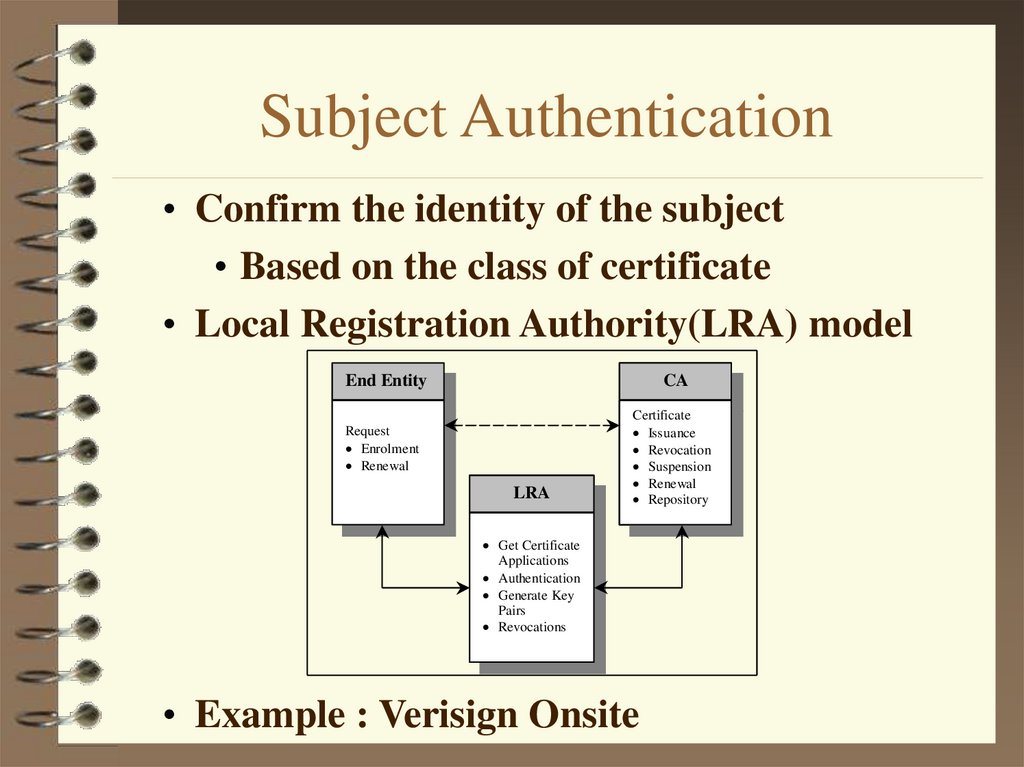
15. Subject Authentication
• Confirm the identity of the subject• Based on the class of certificate
• Local Registration Authority(LRA) model
End Entity
CA
Request
Enrolment
Renewal
LRA
Certificate
Issuance
Revocation
Suspension
Renewal
Repository
Get Certificate
Applications
Authentication
Generate Key
Pairs
Revocations
• Example : Verisign Onsite
16. Importing a Certificate
To send an encrypted message or document toa person who has a certificate.
• From a Certification Authority
• From a Directory Service (LDAP)
• From a signed message
• From a local file (encoded Binary PKCS #7)
17. Certificate Revocation Lists
• A data structure that has the list of all theserial numbers of the revoked certificates.
• Standard X.509 CRL format (ISO/ITU)
• Propagation
• Polling for CRLs
• Pushing CRLs
• Online status checking
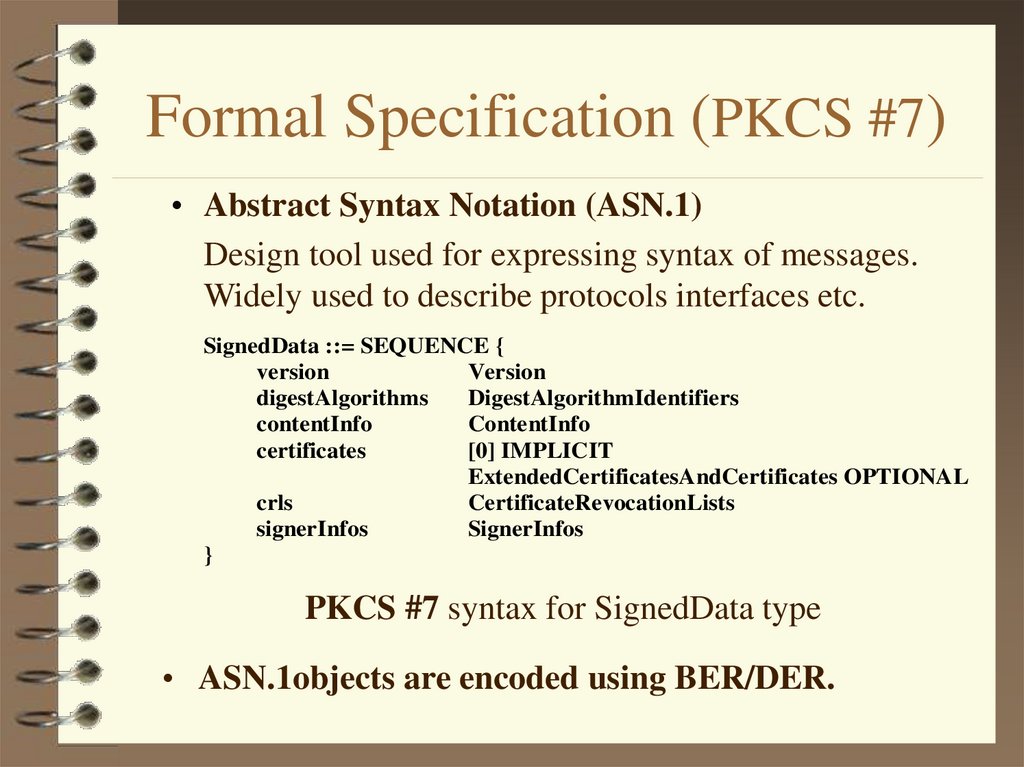
18. Formal Specification (PKCS #7)
• Abstract Syntax Notation (ASN.1)Design tool used for expressing syntax of messages.
Widely used to describe protocols interfaces etc.
SignedData ::= SEQUENCE {
version
Version
digestAlgorithms
DigestAlgorithmIdentifiers
contentInfo
ContentInfo
certificates
[0] IMPLICIT
ExtendedCertificatesAndCertificates OPTIONAL
crls
CertificateRevocationLists
signerInfos
SignerInfos
}
PKCS #7 syntax for SignedData type
• ASN.1objects are encoded using BER/DER.
19. Key Certification Request
CertificationRequest ::= SEQUENCE {certificationRequestInfo
CertificationRequestInfo
signatureAlgorithms
SignatureAlgorithmIdentifiers
signature
Signature
}
CertificationRequestInfo ::= SEQUENCE {
version
Version
subject
Name
subjectpublickeyInfo
SubjectPublicKeyInfo
attributes
[0] IMPLICIT Attributes
}
Version ::= INTEGER
Attributes ::= Set (Name = Value pair)
SignatureAlgorithmIdentifier ::= AlgorithmIdentifier
Signature ::= BIT STRING
PKCS #10 syntax using ASN.1 notation
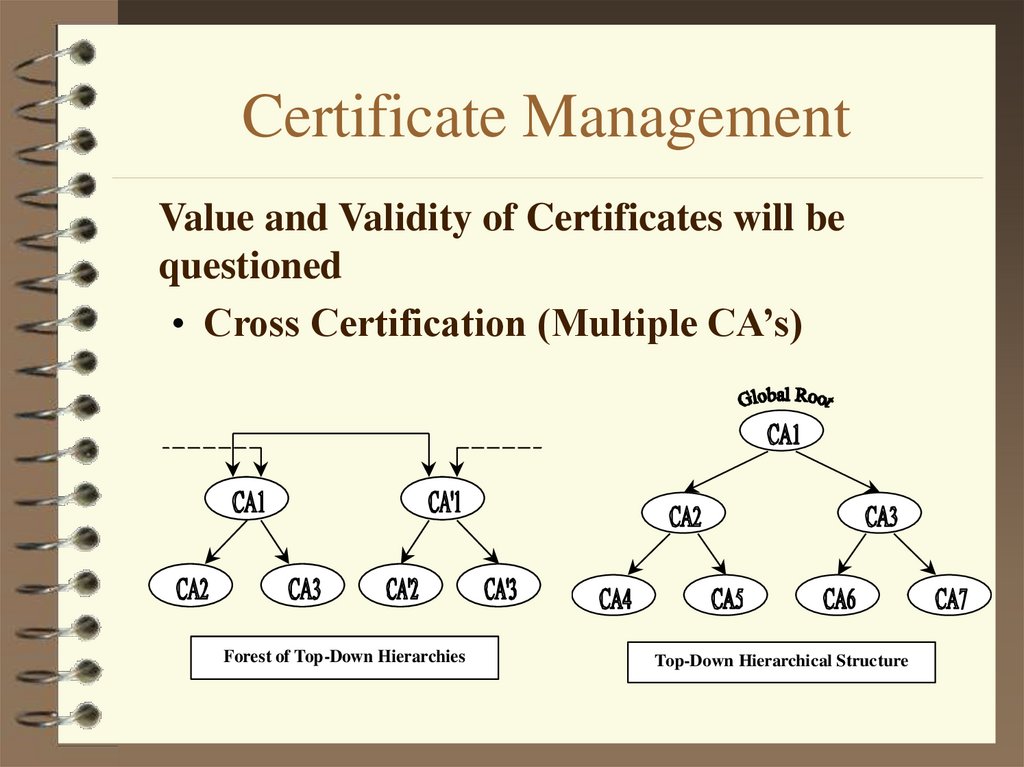
20. Certificate Management
Value and Validity of Certificates will bequestioned
• Cross Certification (Multiple CA’s)
Forest of Top-Down Hierarchies
Top-Down Hierarchical Structure
21. Applications of Certificates
• Sandbox• Code Signing Vs Shrink-Wrapped Software
• Accountability and Authenticity
• Microsoft Authenticode 1.0
• based on X.503 v3 and PKCS #7
• Commercial Vs Individual Publishers
• Object Signing
• Netscape’s technology
• Signs any kind of Files
22. Applications (continued)
• Secure Messaging & S/MIME• Web Server Security
• Microsoft ASP for Access Control













 Программирование
Программирование








