Похожие презентации:
история шифров
1.
A Journey Through Secrecy:The History of Ciphers
Embark on a fascinating journey through the ages, exploring the
evolution of ciphers and the enduring human quest for secure
communication.
2.
Ancient Secrets: Early Forms of EncryptionThe Caesar Cipher
Scytale: Sparta's Secret Baton
One of the earliest and simplest forms of encryption,
An ancient Greek method used by the Spartans for
attributed to Julius Caesar. It involves shifting letters
military communications. A strip of parchment was
a certain number of places down the alphabet.
wound around a cylinder, and the message was
written along its length.
3.
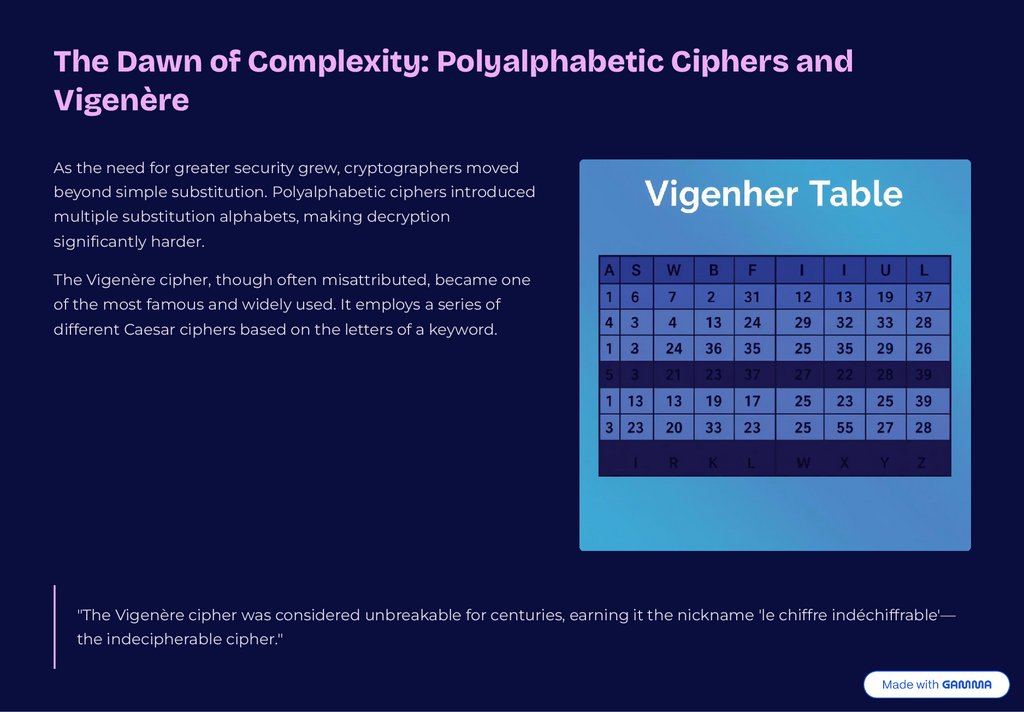
The Dawn of Complexity: Polyalphabetic Ciphers andVigenère
As the need for greater security grew, cryptographers moved
beyond simple substitution. Polyalphabetic ciphers introduced
multiple substitution alphabets, making decryption
significantly harder.
The Vigenère cipher, though often misattributed, became one
of the most famous and widely used. It employs a series of
different Caesar ciphers based on the letters of a keyword.
"The Vigenère cipher was considered unbreakable for centuries, earning it the nickname 'le chiffre indéchiffrable'4
the indecipherable cipher."
4.
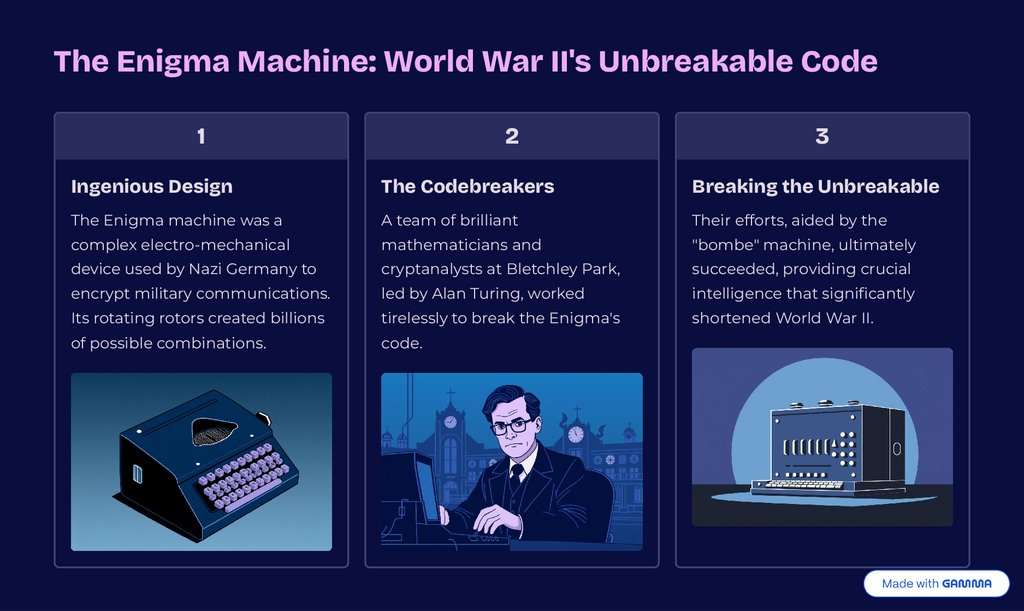
The Enigma Machine: World War II's Unbreakable Code1
2
3
Ingenious Design
The Codebreakers
Breaking the Unbreakable
The Enigma machine was a
A team of brilliant
Their efforts, aided by the
complex electro-mechanical
mathematicians and
"bombe" machine, ultimately
device used by Nazi Germany to
cryptanalysts at Bletchley Park,
succeeded, providing crucial
encrypt military communications.
led by Alan Turing, worked
intelligence that significantly
Its rotating rotors created billions
tirelessly to break the Enigma's
shortened World War II.
of possible combinations.
code.
5.
The Rise of Modern Cryptography: From DES to AESThe digital age demanded new, more robust encryption
standards. The Data Encryption Standard (DES) emerged
in the 1970s, becoming a cornerstone for data security.
However, as computing power advanced, DES eventually
proved vulnerable. This led to the development of the
Advanced Encryption Standard (AES) in the early 2000s,
which remains a global standard for strong encryption.
DES: Pioneering symmetric-key algorithm.
AES: Current gold standard, highly secure and
efficient.
6.
Public-Key Cryptography: Sharing Secrets SecurelyAsymmetric Keys
RSA Explained
Digital Signatures
Public-key cryptography uses a pair of
The RSA algorithm, named after
Beyond encryption, public-key
keys: a public key for encryption and a
Rivest, Shamir, and Adleman, is a
cryptography enables digital
private key for decryption. This
prominent example. It relies on the
signatures, verifying the authenticity
revolutionary concept allowed secure
computational difficulty of factoring
and integrity of digital messages and
communication without a shared
large prime numbers.
documents.
secret beforehand.
7.
The Digital Frontier: Cryptography in the Internet AgeThe internet's rapid expansion brought an unprecedented need for secure communication on a global scale.
Cryptography became fundamental to almost every online interaction.
SSL/TLS
VPNs
Blockchain
Secure Sockets Layer (SSL) and
Virtual Private Networks (VPNs)
Blockchain technology
its successor Transport Layer
use encryption to create secure
leverages cryptographic
Security (TLS) encrypt internet
tunnels over public networks,
principles to create immutable
traffic, protecting data
ensuring privacy and data
and decentralized ledgers,
exchanged between web
protection for remote access.
forming the backbone of
browsers and servers.
cryptocurrencies and other
distributed applications.
8.
Quantum Computing's Threat: The Future of EncryptionThe advent of quantum computing poses a significant
challenge to current cryptographic standards. Quantum
algorithms, such as Shor's algorithm, could theoretically
break many widely used public-key encryption schemes.
This potential threat has spurred the development of
"post-quantum cryptography"4new cryptographic
algorithms designed to be resistant to attacks from
quantum computers.
Researchers worldwide are working to develop and standardize quantum-resistant cryptographic solutions
before powerful quantum computers become a reality.
9.
Cryptography Today:Protecting Your Data in a
Connected World
In an increasingly interconnected world, cryptography is no longer
just for spies and militaries. It is an essential tool for protecting
personal privacy, financial transactions, and national security.
From secure messaging apps to online banking, encryption
underpins the trust and functionality of our digital lives.
10.
Q&A and Key Takeaways: The Enduring Art ofSecrecy
A Long History
Future Challenges
Cryptography has evolved from
Foundation of
Security
simple shifts to complex
Modern encryption is the
computing presents new
algorithms, driven by the
constant battle between code
makers and code breakers.
Thank you! Any questions?
bedrock of digital security,
protecting data, privacy, and
trust across the internet.
The rise of quantum
threats, demanding
continuous innovation in
cryptographic research and
development.





 Информатика
Информатика








