Похожие презентации:
Basis оf Operating Systems (Windows, Linux, Mac Osx)
1.
Lection 5● BASIS OF OPERATING SYSTEMS (WINDOWS, LINUX, MAC OSX)
● PROTECTION OF INFORMATION WHEN USING INFORMATION
TECHNOLOGIES
2.
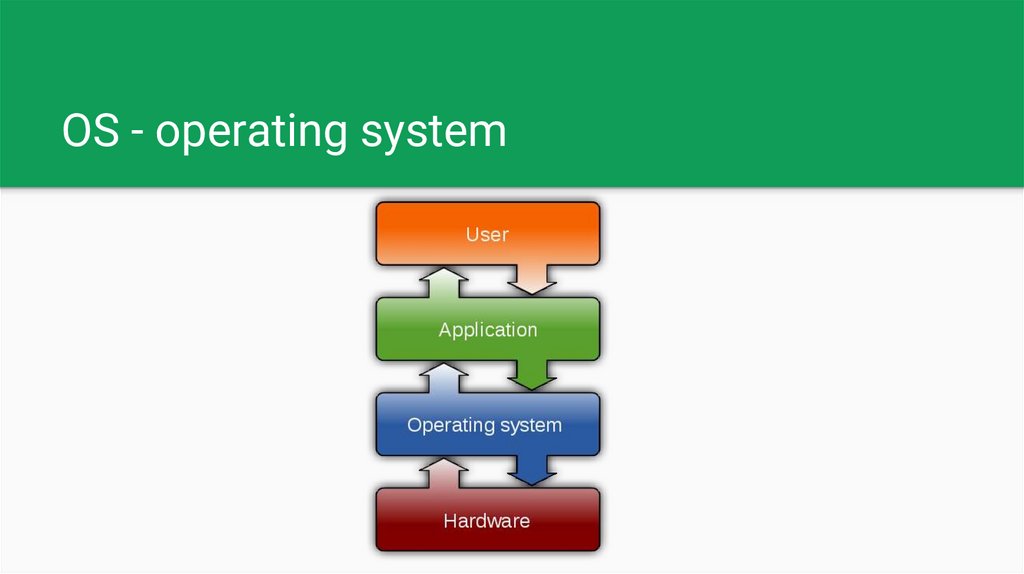
OS - operating systemOS is system software that manages computer hardware,
software resources, and provides common services for
computer programs.
3.
OS - operating system4.
5.
6.
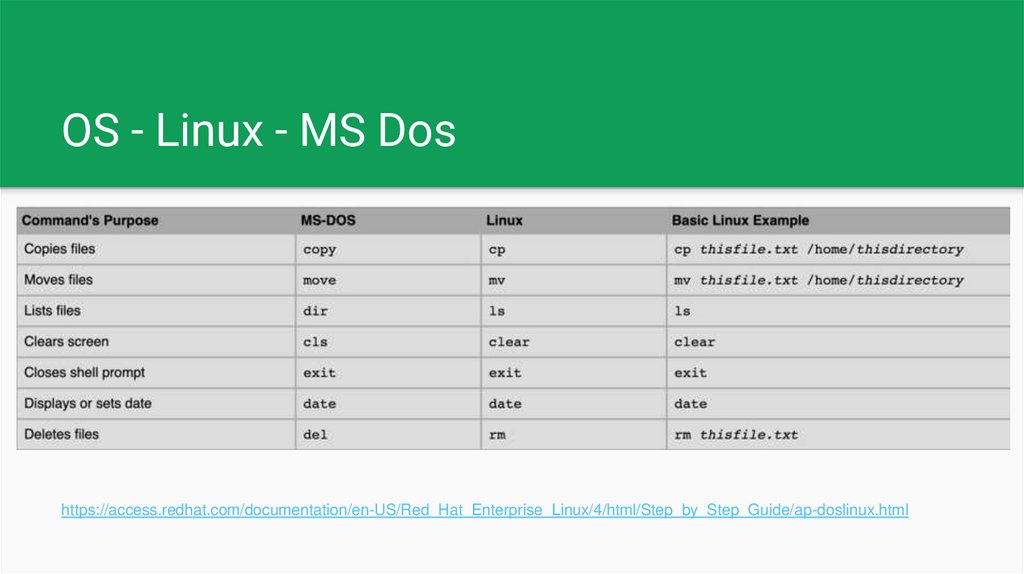
OS - Linux - MS Doshttps://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/4/html/Step_by_Step_Guide/ap-doslinux.html
7.
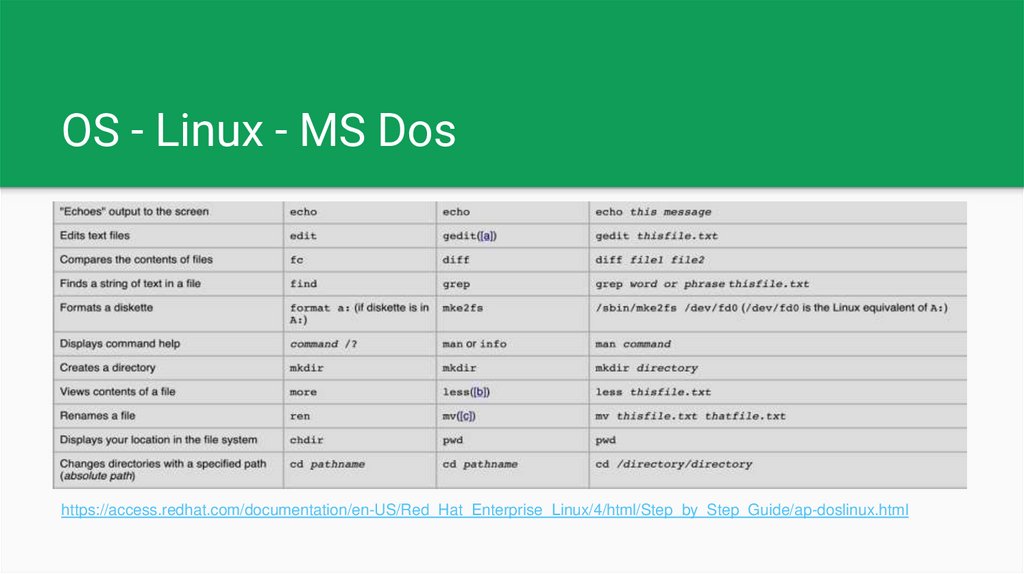
OS - Linux - MS Doshttps://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/4/html/Step_by_Step_Guide/ap-doslinux.html
8.
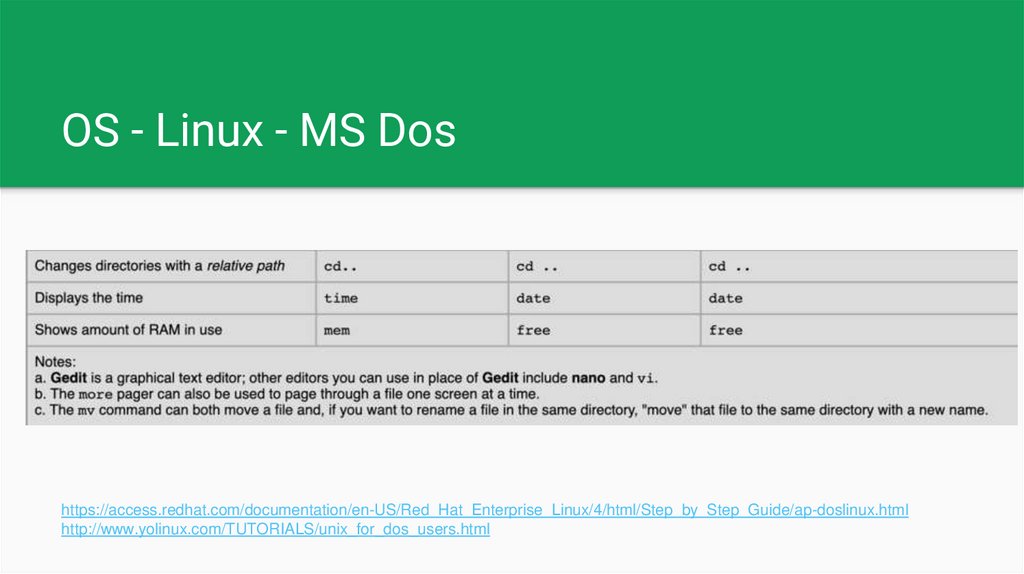
OS - Linux - MS Doshttps://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/4/html/Step_by_Step_Guide/ap-doslinux.html
http://www.yolinux.com/TUTORIALS/unix_for_dos_users.html
9.
OS - LinuxTry some commands
https://bellard.org/jslinux/
10.
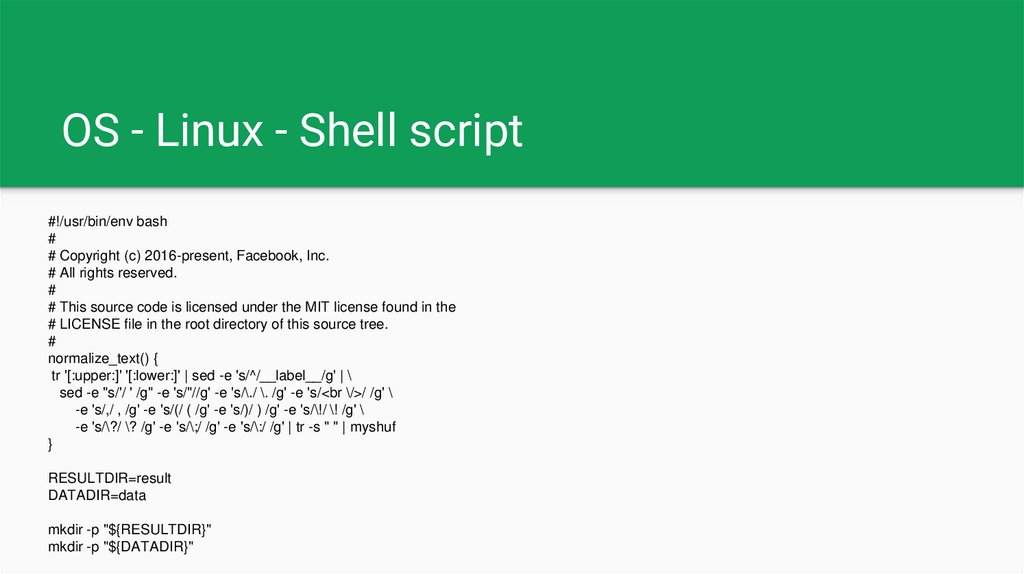
OS - Linux - Shell script#!/usr/bin/env bash
#
# Copyright (c) 2016-present, Facebook, Inc.
# All rights reserved.
#
# This source code is licensed under the MIT license found in the
# LICENSE file in the root directory of this source tree.
#
normalize_text() {
tr '[:upper:]' '[:lower:]' | sed -e 's/^/__label__/g' | \
sed -e "s/'/ ' /g" -e 's/"//g' -e 's/\./ \. /g' -e 's/<br \/>/ /g' \
-e 's/,/ , /g' -e 's/(/ ( /g' -e 's/)/ ) /g' -e 's/\!/ \! /g' \
-e 's/\?/ \? /g' -e 's/\;/ /g' -e 's/\:/ /g' | tr -s " " | myshuf
}
RESULTDIR=result
DATADIR=data
mkdir -p "${RESULTDIR}"
mkdir -p "${DATADIR}"
11.
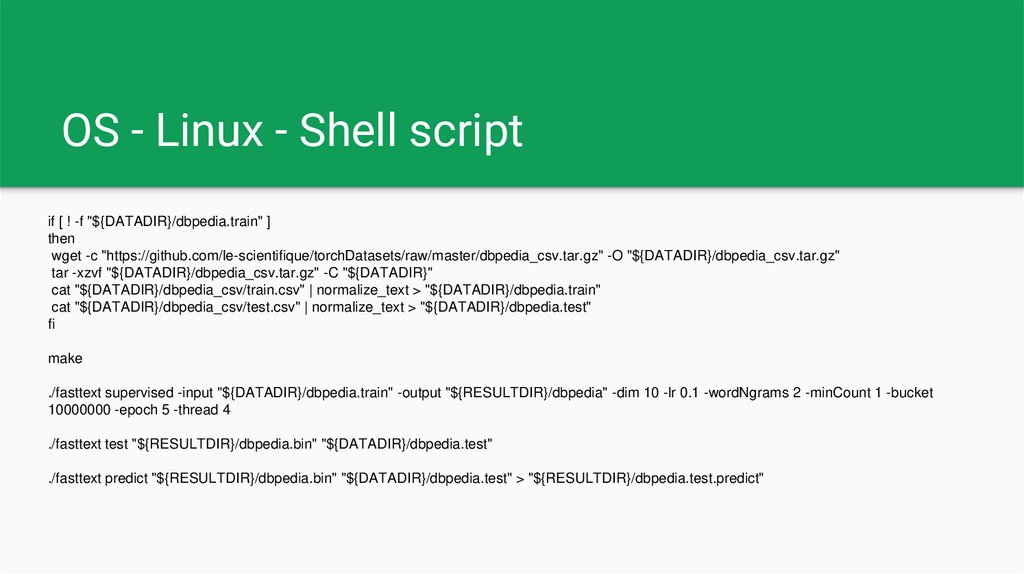
OS - Linux - Shell scriptif [ ! -f "${DATADIR}/dbpedia.train" ]
then
wget -c "https://github.com/le-scientifique/torchDatasets/raw/master/dbpedia_csv.tar.gz" -O "${DATADIR}/dbpedia_csv.tar.gz"
tar -xzvf "${DATADIR}/dbpedia_csv.tar.gz" -C "${DATADIR}"
cat "${DATADIR}/dbpedia_csv/train.csv" | normalize_text > "${DATADIR}/dbpedia.train"
cat "${DATADIR}/dbpedia_csv/test.csv" | normalize_text > "${DATADIR}/dbpedia.test"
fi
make
./fasttext supervised -input "${DATADIR}/dbpedia.train" -output "${RESULTDIR}/dbpedia" -dim 10 -lr 0.1 -wordNgrams 2 -minCount 1 -bucket
10000000 -epoch 5 -thread 4
./fasttext test "${RESULTDIR}/dbpedia.bin" "${DATADIR}/dbpedia.test"
./fasttext predict "${RESULTDIR}/dbpedia.bin" "${DATADIR}/dbpedia.test" > "${RESULTDIR}/dbpedia.test.predict"
12.
Эндрю Стюарт Таненбаум — профессор Амстердамского свободного университета,где возглавляет группу разработчиков компьютерных систем; защитил докторскую
диссертацию по физике в Калифорнийском университете в Беркли. Известен как автор
Minix (свободная Unix-подобная операционная система для студенческих
лабораторий), книг по компьютерным наукам и RFID-вируса.
13.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#1 - You are a target to hackers
Don't ever say "It won't happen to me". We are all at risk and the stakes are high - to your personal and
financial well-being, and to the University's standing and reputation.
14.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#2 - Keep software up to date
Installing software updates for your operating system and programs is critical. Always install the latest
security updates for your devices
15.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
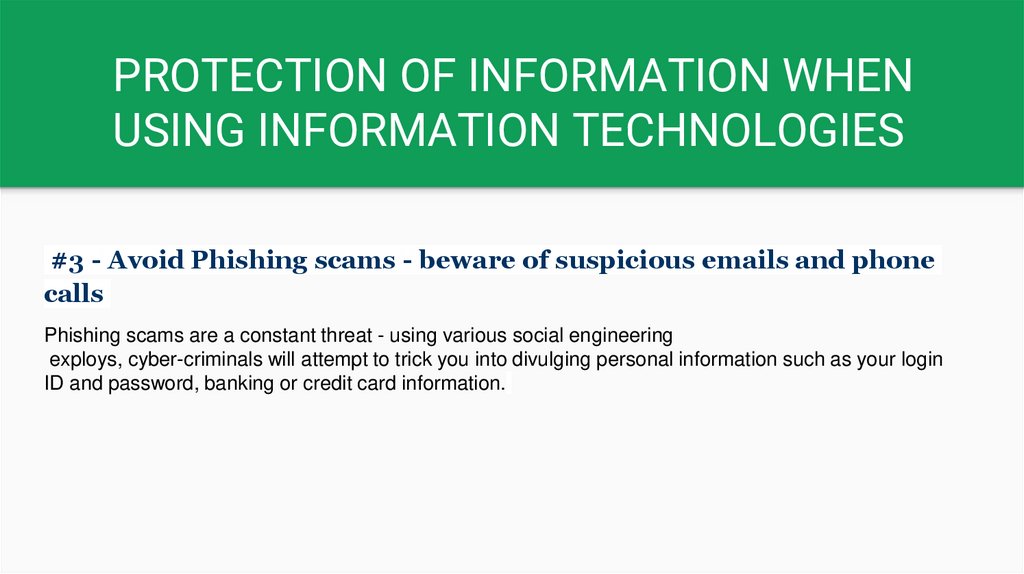
#3 - Avoid Phishing scams - beware of suspicious emails and phone
calls
Phishing scams are a constant threat - using various social engineering
exploys, cyber-criminals will attempt to trick you into divulging personal information such as your login
ID and password, banking or credit card information.
16.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#4 - Practice good password management
We all have too many passwords to manage - and it's easy to take short-cuts, like reusing the same
password. A password management program can help you to maintain strong unique passwords for all
of your accounts. These programs can generate strong passwords for you, enter credentials
automatically, and remind you to update your passwords periodically.
17.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#5 - Be careful what you click
Avoid visiting unknown websites or downloading software from untrusted sources. These sites often
host malware that will automatically, and often silently, compromise your computer.
If attachments or links in the email are unexpected or suspicious for any reason, don't click on it.
18.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#6 - Never leave devices unattended
The physical security of your devices is just as important as their technical security.
● If you need to leave your laptop, phone, or tablet for any length of time - lock it up so no one else
can use it.
● If you keep sensitive information on a flash drive or external hard drive, make sure to keep these
locked as well.
● For desktop computers, shut-down the system when not in use - or lock your screen.
19.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#6 - Never leave devices unattended
The physical security of your devices is just as important as their technical security.
● If you need to leave your laptop, phone, or tablet for any length of time - lock it up so no one else
can use it.
● If you keep sensitive information on a flash drive or external hard drive, make sure to keep these
locked as well.
● For desktop computers, shut-down the system when not in use - or lock your screen.
20.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#7 - Protect sensitive data
The physical security of your devices is just as important as their technical security.
● If you need to leave your laptop, phone, or tablet for any length of time - lock it up so no one else
can use it.
● If you keep sensitive information on a flash drive or external hard drive, make sure to keep these
locked as well.
● For desktop computers, shut-down the system when not in use - or lock your screen.
21.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#8 - Use mobile devices safely
The physical security of your devices is just as important as their technical security.
● If you need to leave your laptop, phone, or tablet for any length of time - lock it up so no one else
can use it.
● If you keep sensitive information on a flash drive or external hard drive, make sure to keep these
locked as well.
● For desktop computers, shut-down the system when not in use - or lock your screen.
22.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#9 - Install anti-virus protection
Only install an anti-virus program from a known and trusted source. Keep virus definitions,
engines and software up to date to ensure your anti-virus program remains effective.
23.
PROTECTION OF INFORMATION WHENUSING INFORMATION TECHNOLOGIES
#10 - Back up your data
Back up regularly - if you are a victim of a security incident, the only guaranteed way to repair your
computer is to erase and re-install the system.













 Программное обеспечение
Программное обеспечение








