Похожие презентации:
Hacking Lab Practice
1.
Hacking LAB: Practices1.
Working with network commands in Windows and Linux (Assignment Week 1: Make a list of 50 Commands with syntax and
usage)
2. Capturing and Analyzing Network Traffic using Wireshark (Assignment Week 2: Case study of TCP 3-way handshake) or
(Assignment Week 2: Capture HTTP packet and extract username and Password using Ettercap and Wireshark)
3. Website technical information gathering using maltego, httrack, whois. (Assignment Week 3: Chose any two tools from
OSINTFramework.com and discuss the steps to use it)
4. Full Scan, Half Open Scan, Stealth Scan and XMAS Scan using NMAP (Assignment Week 4: Run Any 10 NSE Scripts )
5. Perform Host Discovery, Service Discovery(FTP, Telnet, SSH, Java RMI Server, SMB), Port Scanning using Metasploit or
(Assignment Week 5: Demonstrate Eternal Blue, VSFTPD, OpenSSH exploit using Metasploit)
6. Social engineering using SEToolkit (Assignment Week 6: Create a Clone of GMAIL using SEToolkit)
7. Web parameter poisoning using burp suite (Assignment Week 7: Change the price of all item to 1 USD on e-commerce shopping
cart)
8. Create Fake Harmless Virus using Notepad (Assignment Week 8: Create a MAC/Window and Android Spyware
with MSFVenom)
9. Malware Classification using Convolutional Neural Networks using Google Colab (Assignment Week 9: Malware Classification
using Convolutional Neural Networks using Jupyter Notebook)
10. Perform session hijacking using Zed Attack Proxy (ZAP) (Assignment Week 10: Perform Session Hijacking using Wireshark)
2.
Week 2 PracticeCapturing and Analyzing Network Traffic using
Wireshark
(Assignment Week 2: Case study of TCP 3-way
handshake)
or
(Assignment Week 2: Capture HTTP packet and extract
username and Password using Wireshark & Ettercap)
3.
WIRESHARK• Wireshark is a network packet analyzer. A network packet
analyzer presents captured packet data in as much detail as
possible.
• You could think of a network packet analyzer as a measuring
device for examining what’s happening inside a network cable,
just like an electrician uses a voltmeter for examining what’s
happening inside an electric cable (but at a higher level, of
course).
• Wireshark is available for free, is open source, and is one of the
best packet analyzers available today.
4.
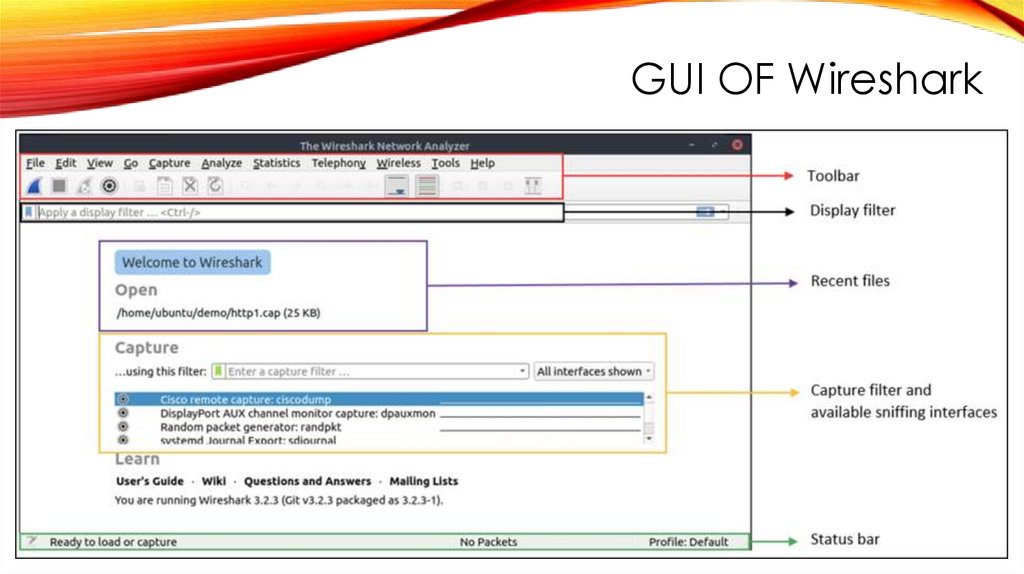
GUI OF Wireshark5.
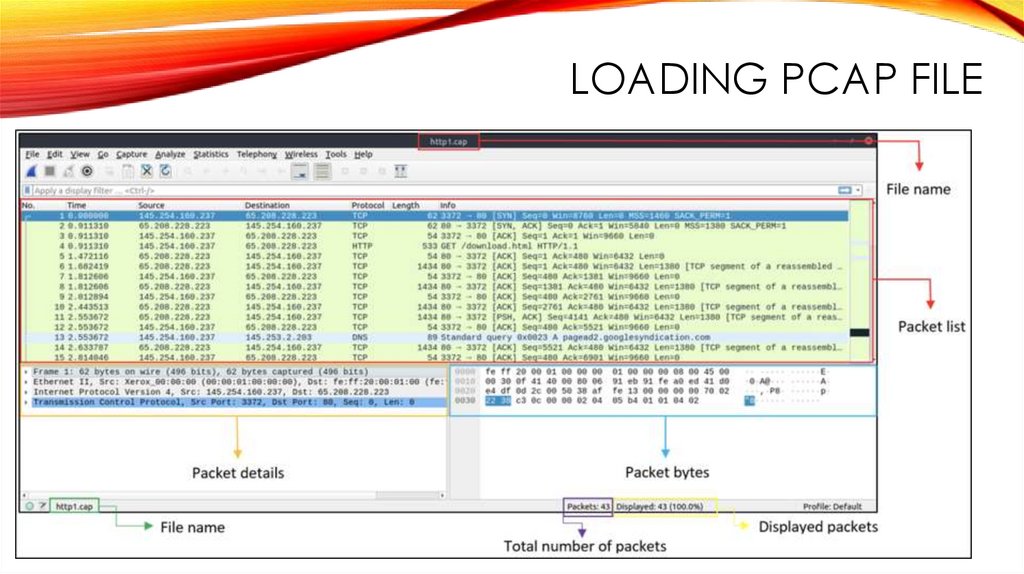
LOADING PCAP FILE6.
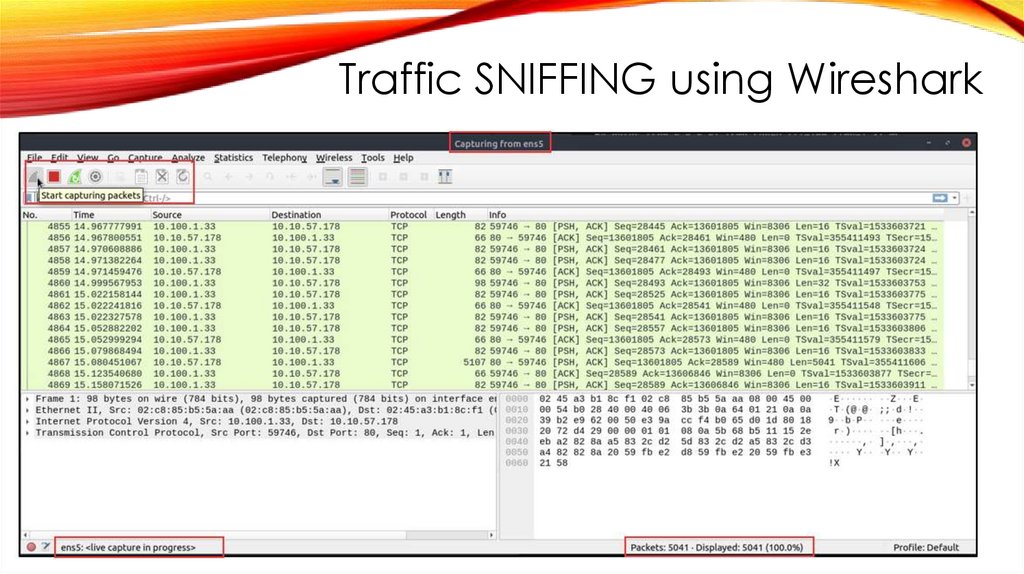
Traffic SNIFFING using Wireshark7.
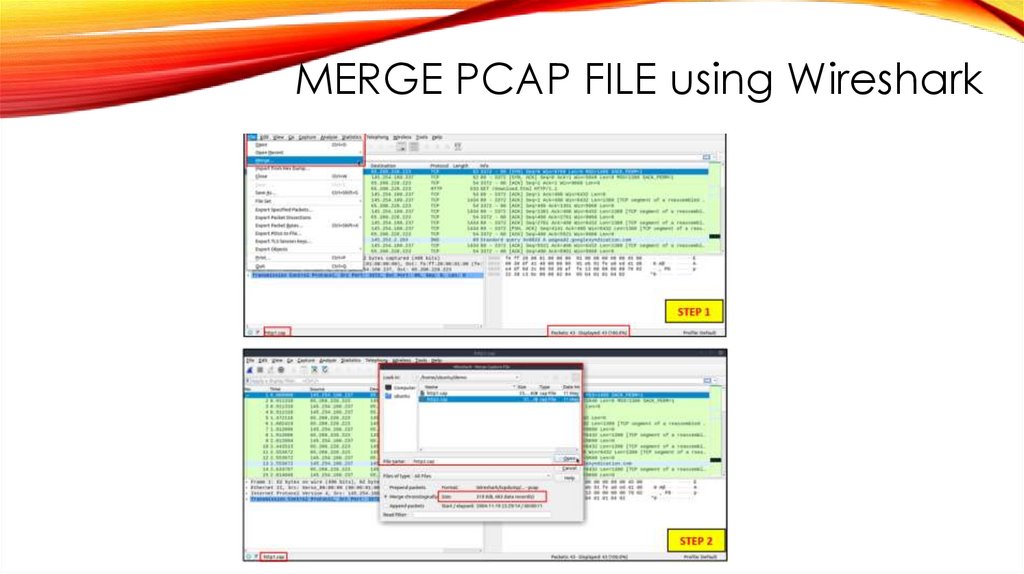
MERGE PCAP FILE using Wireshark8.
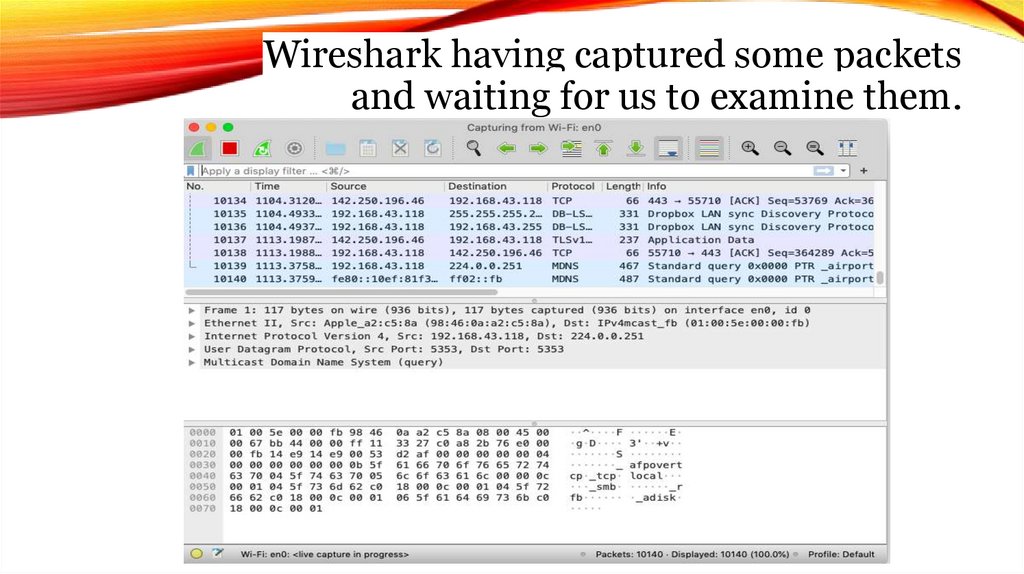
Wireshark having captured some packetsand waiting for us to examine them.
9.
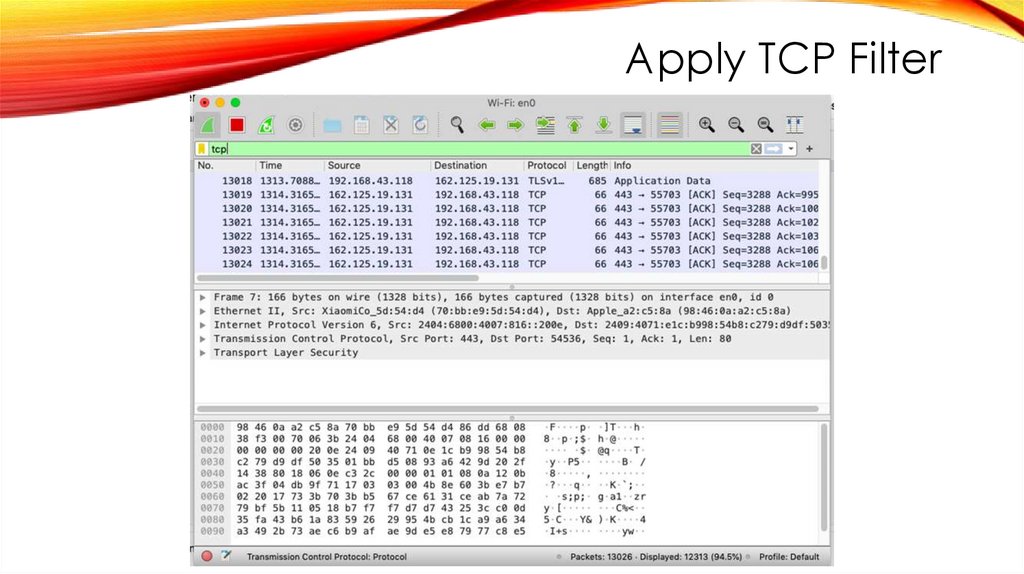
Apply TCP Filter10.
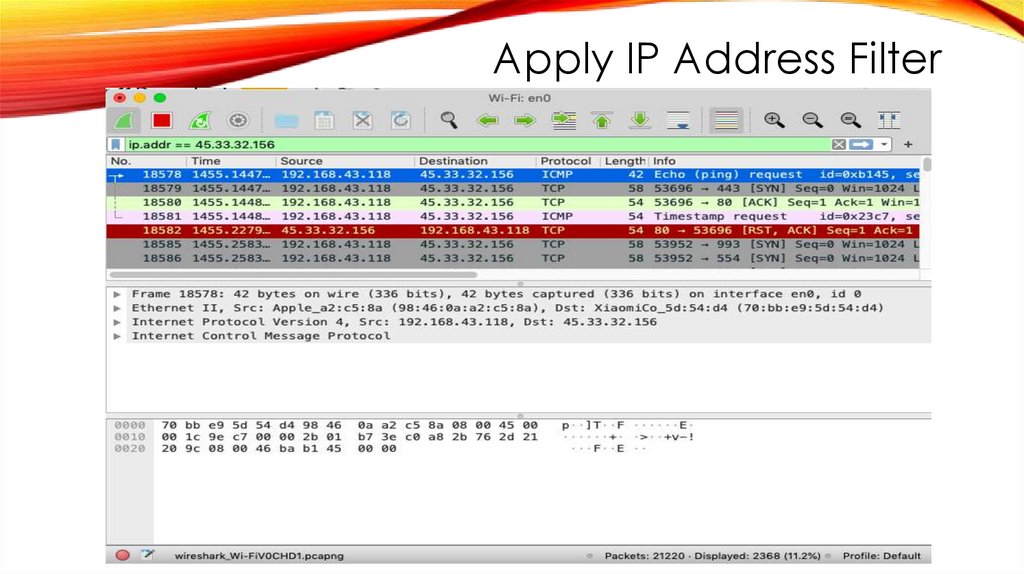
Apply IP Address Filter11.
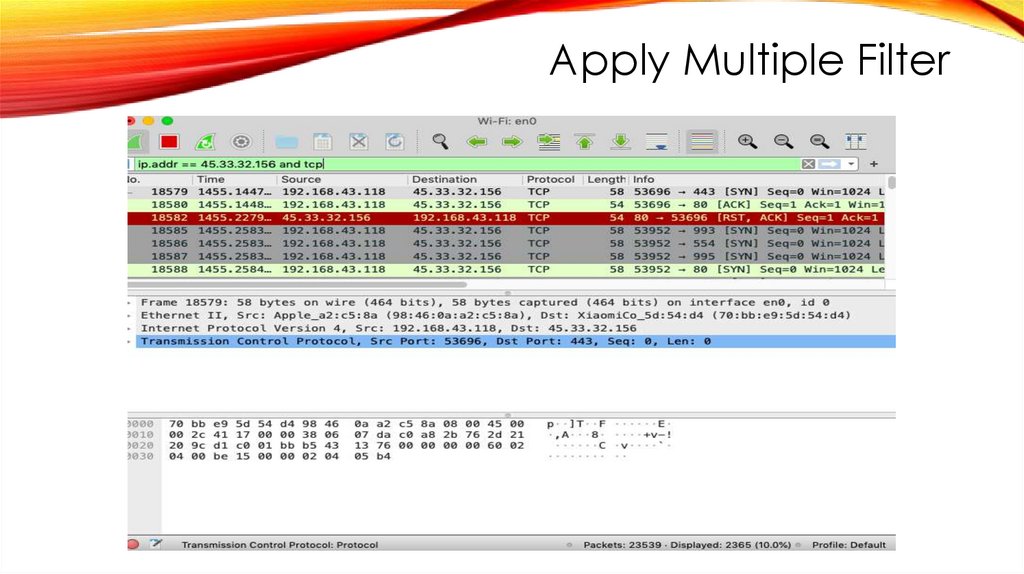
Apply Multiple Filter12.
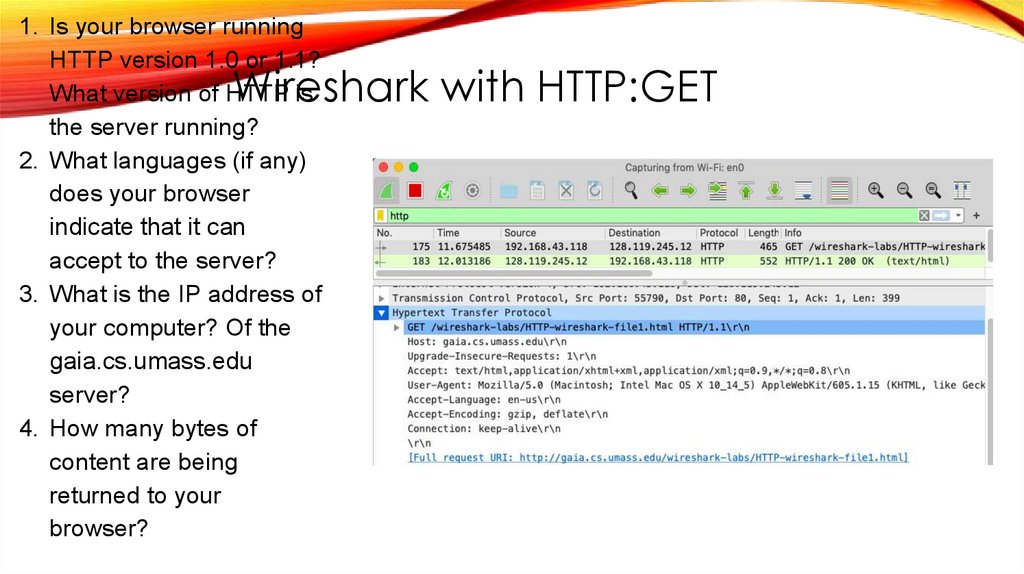
Wireshark with HTTP:GETLet’s begin our exploration of HTTP by downloading a very simple HTML file one that is very short, and contains no embedded objects. Do the following:
1. Start up your web browser.
2. Start up the Wireshark packet sniffer,Enter “http” (just the letters, not the
quotation marks) in the display-filter-specification window,
3. Wait a bit more than one minute, and then begin Wireshark packet capture.
4. Enter the following to your browser
http://gaia.cs.umass.edu/wireshark-labs/HTTP-wireshark-file1.html
5. Stop Wireshark packet capture.
13.
1. Is your browser runningHTTP version 1.0 or 1.1?
What version of HTTP is
the server running?
2. What languages (if any)
does your browser
indicate that it can
accept to the server?
3. What is the IP address of
your computer? Of the
gaia.cs.umass.edu
server?
4. How many bytes of
content are being
returned to your
browser?
Wireshark with HTTP:GET
14.
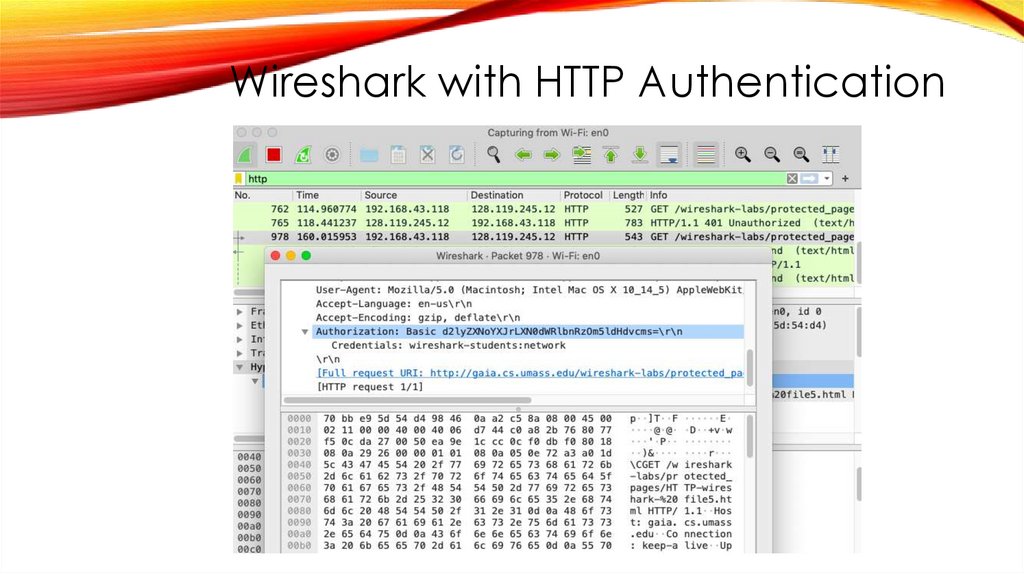
Wireshark with HTTP Authentication1. Finally, let’s try visiting a web site that is password-protected and
examine the sequence of HTTP message exchanged for such a
site.
2. The URL http://gaia.cs.umass.edu/wiresharklabs/protected_pages/HTTP-wireshark-file5.html is password
protected.
3. The username is “wireshark-students” (without the quotes), and
the password is “network” (again, without the quotes).
15.
Wireshark with HTTP Authentication● Start up the Wireshark packet sniffer
● Enter the following URL into your browser
http://gaia.cs.umass.edu/wireshark-labs/protected_pages/HTTPwireshark- file5.html
Type the requested username and password into the pop up box.
● Stop Wireshark packet capture, and enter “http” in the display-filterspecification window, so that only captured HTTP messages will be
displayed later in the packet-listing window.
16.
Wireshark with HTTP Authentication17.
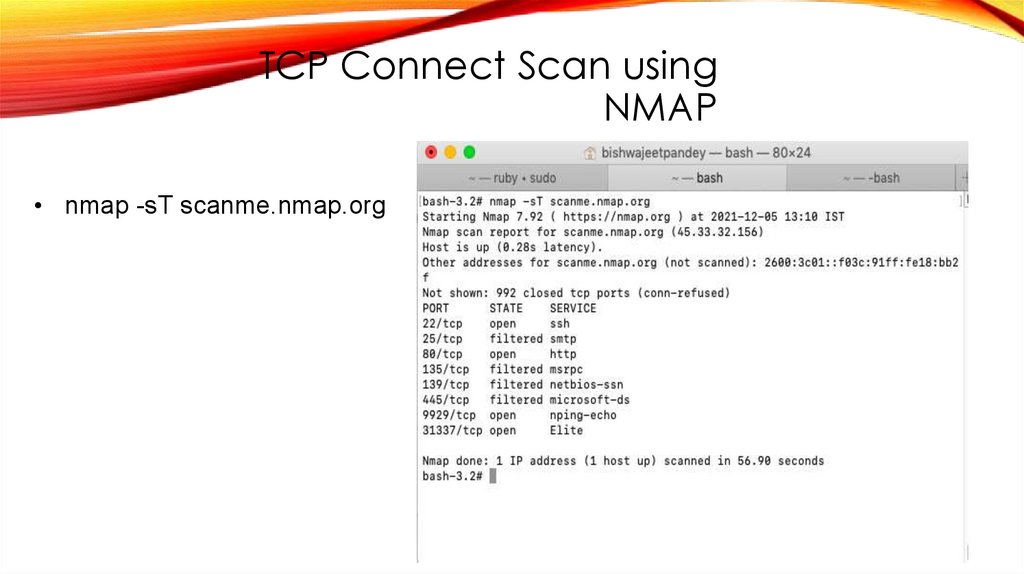
TCP Connect Scan usingNMAP
• nmap -sT scanme.nmap.org
18.
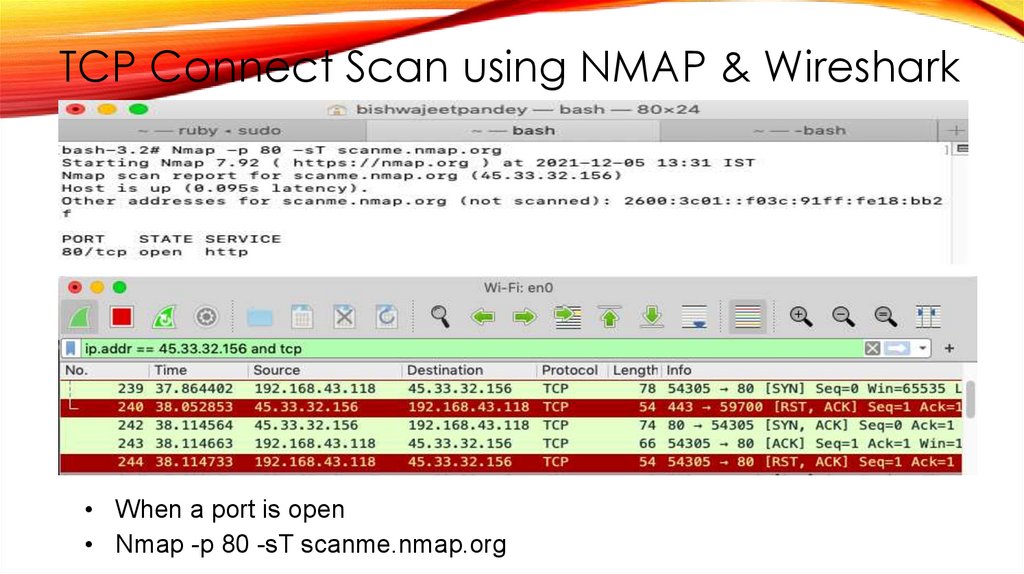
TCP Connect Scan using NMAP & Wireshark• When a port is open
• Nmap -p 80 -sT scanme.nmap.org
19.
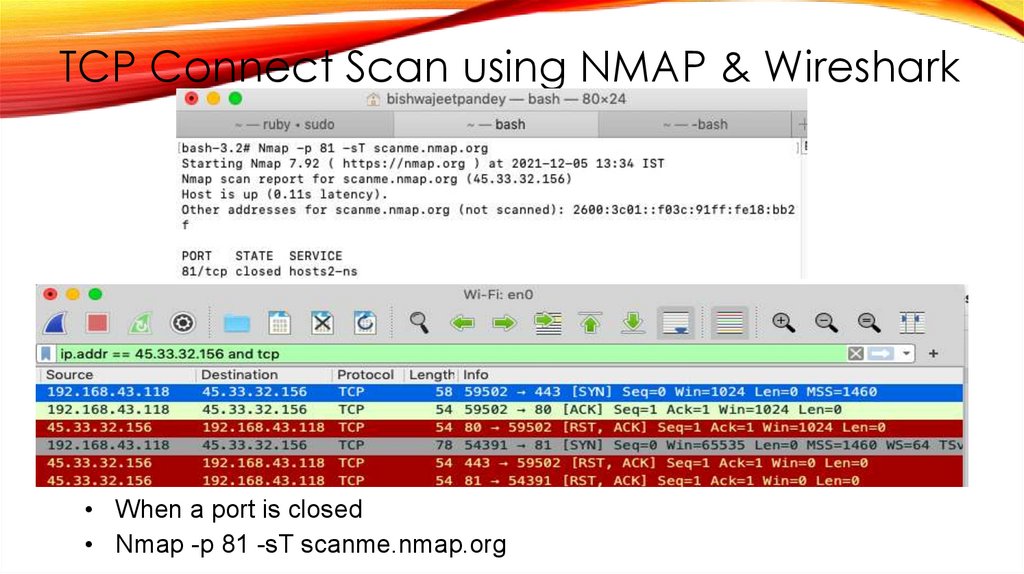
TCP Connect Scan using NMAP & Wireshark• When a port is closed
• Nmap -p 81 -sT scanme.nmap.org
20.
Capturing and Analyzing Network Traffic usingEttercap on MAC
21.
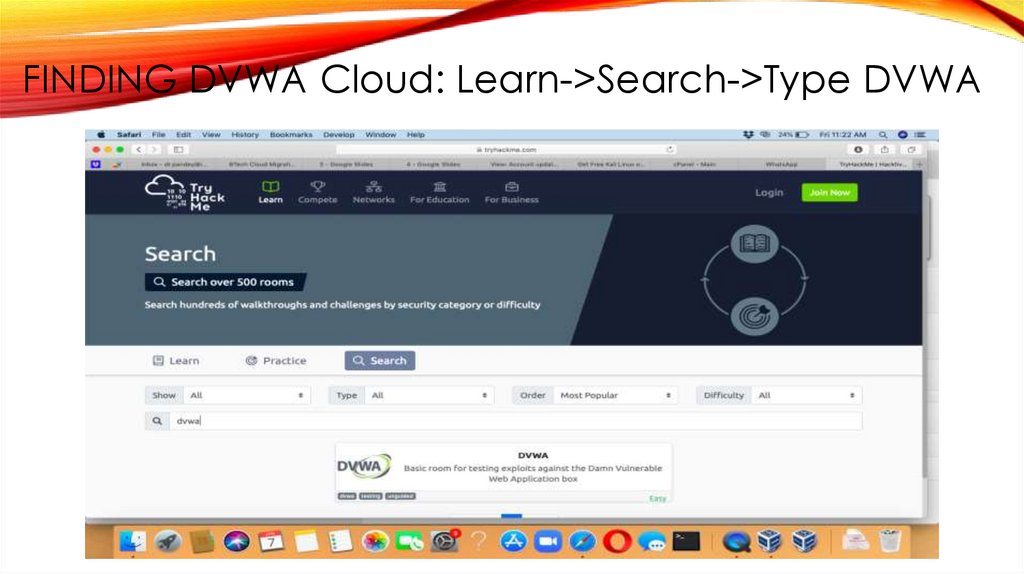
FINDING DVWA Cloud: Learn->Search->Type DVWA22.
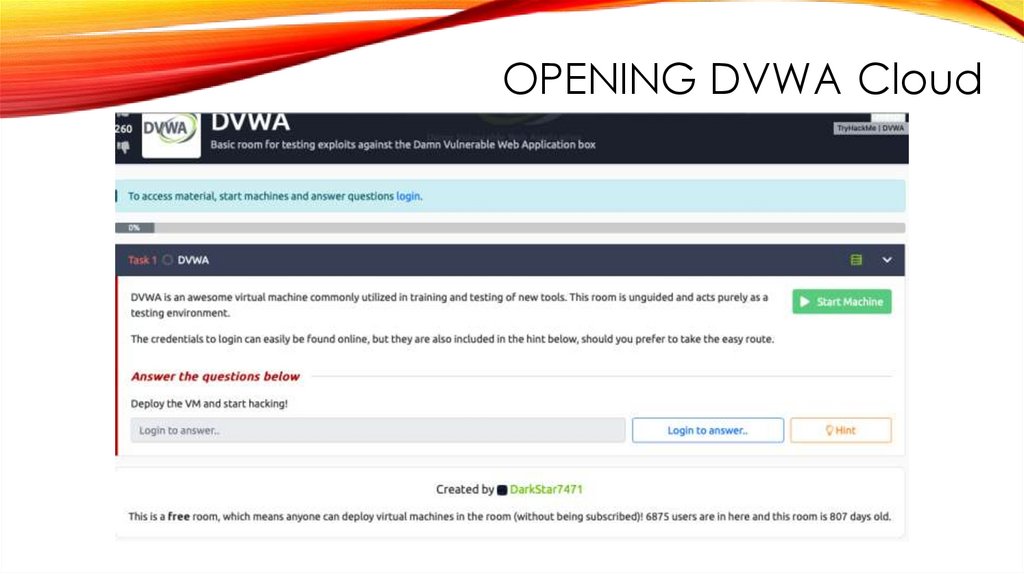
OPENING DVWA Cloud23.
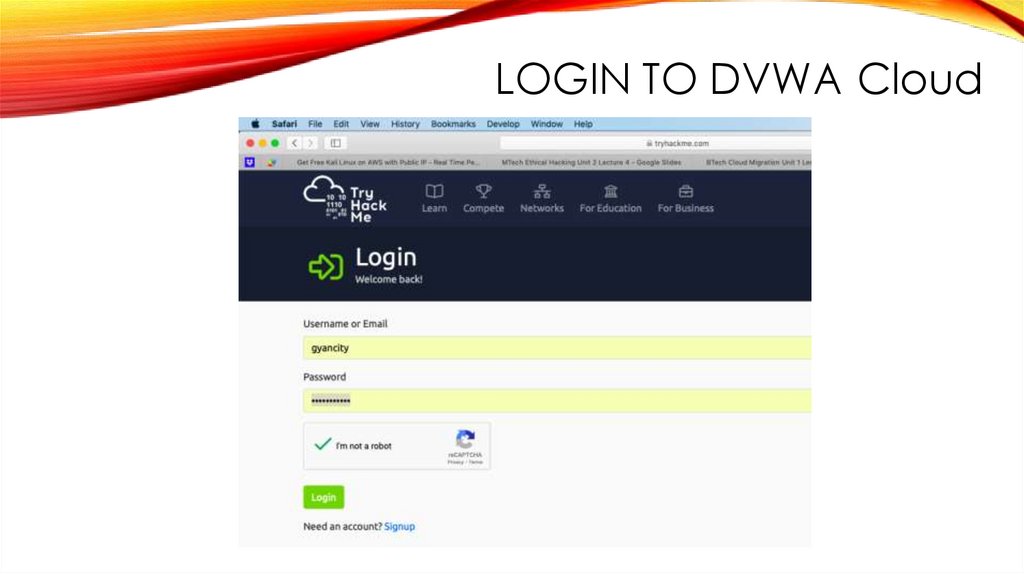
LOGIN TO DVWA Cloud24.
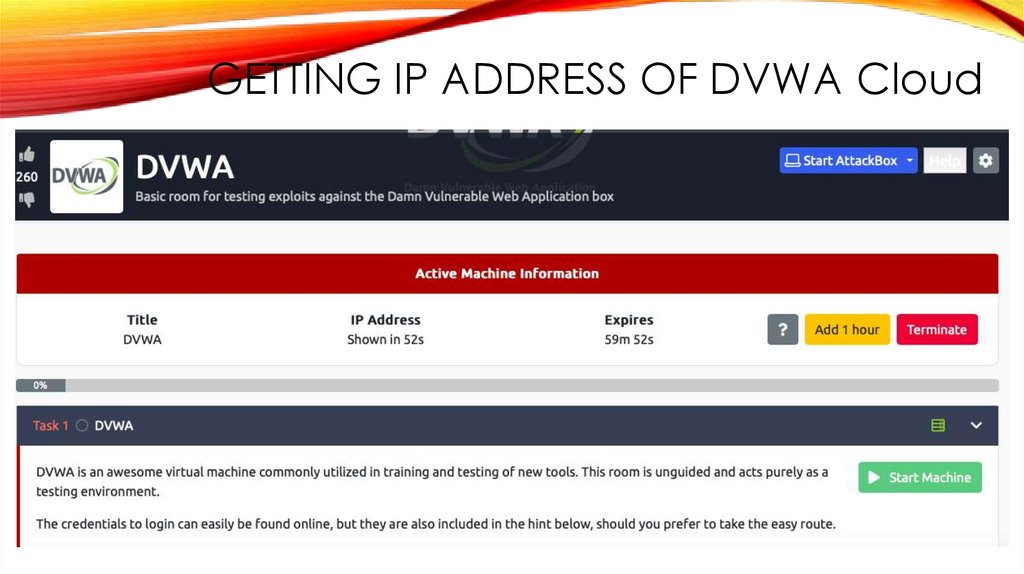
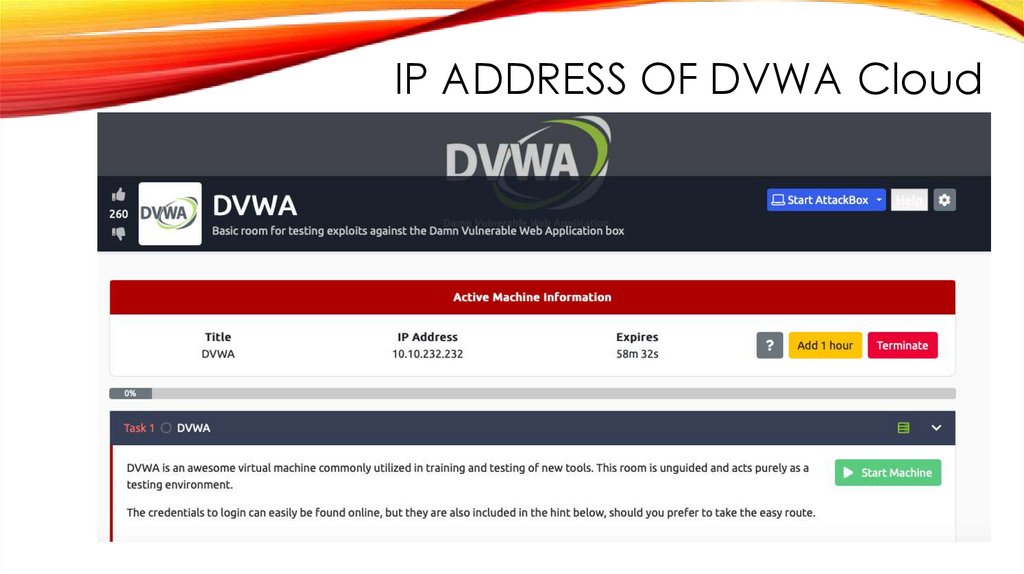
GETTING IP ADDRESS OF DVWA Cloud25.
IP ADDRESS OF DVWA Cloud26.
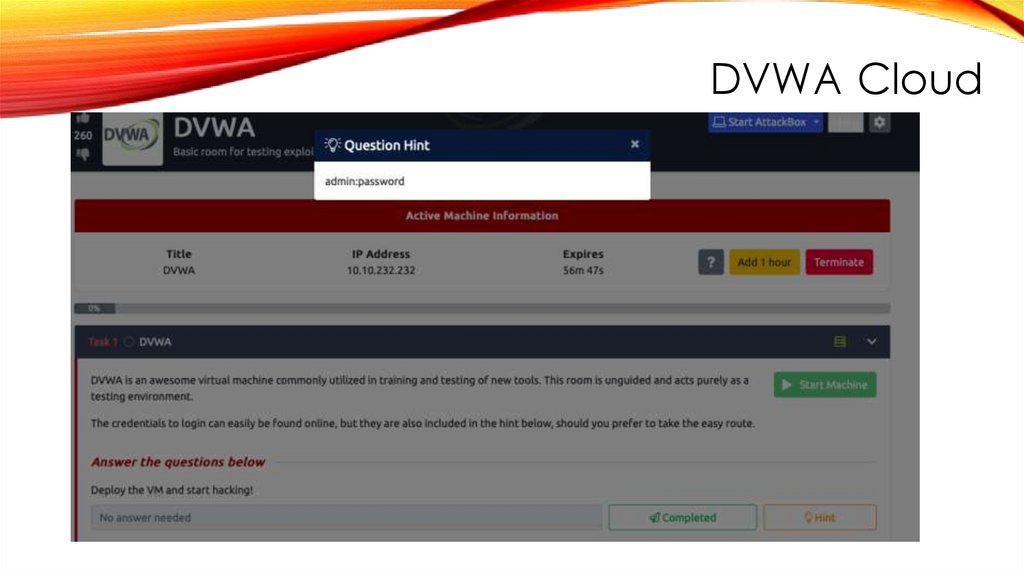
DVWA Cloud27.
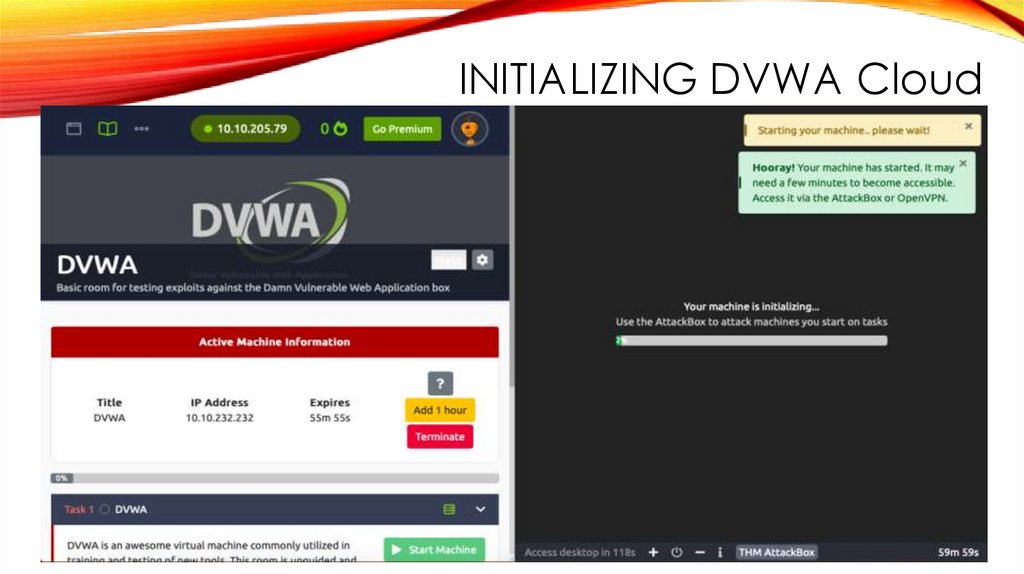
INITIALIZING DVWA Cloud28.
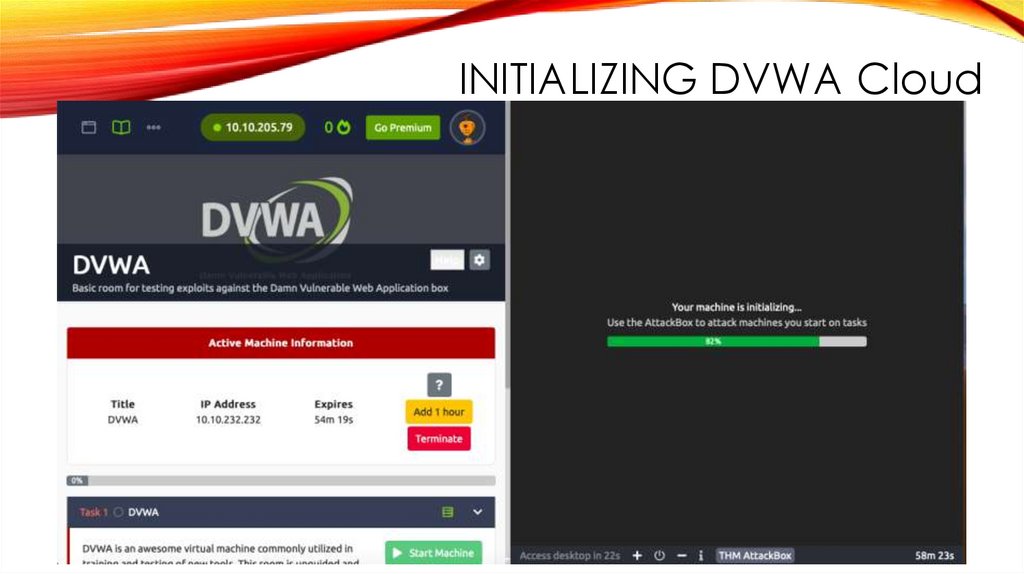
INITIALIZING DVWA Cloud29.
CONNECTING DVWA Cloud30.
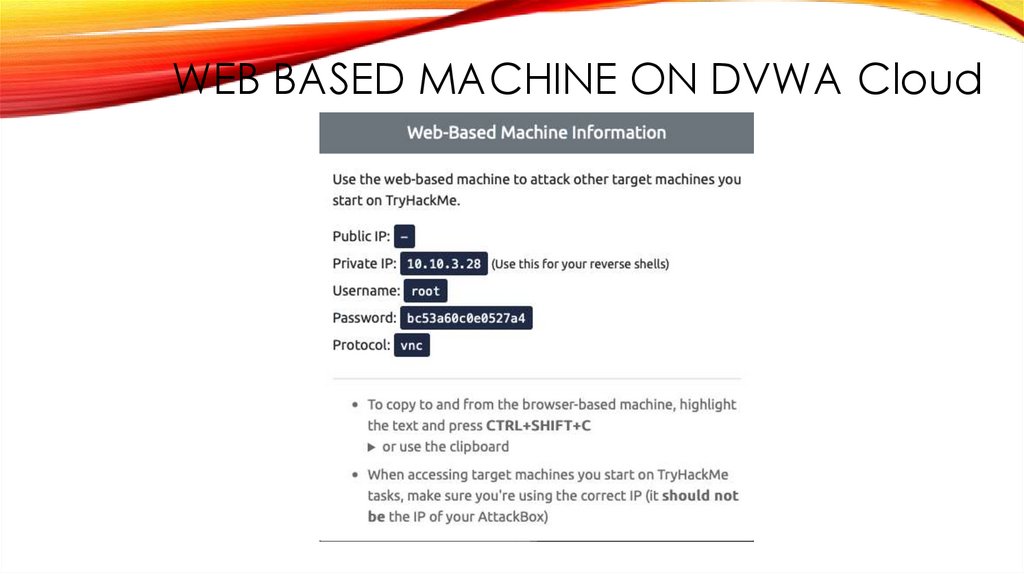
WEB BASED MACHINE ON DVWA Cloud31.
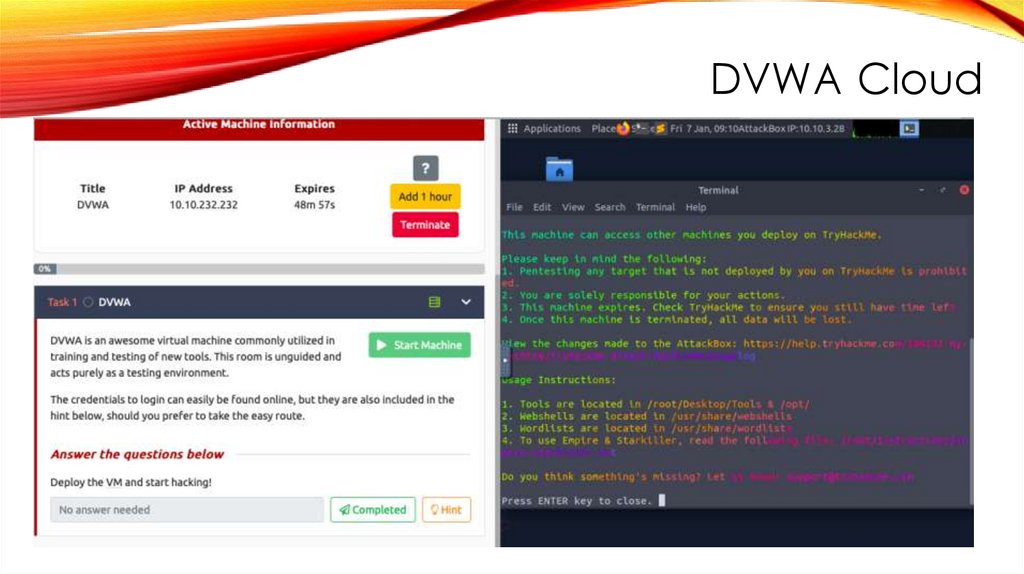
DVWA Cloud32.
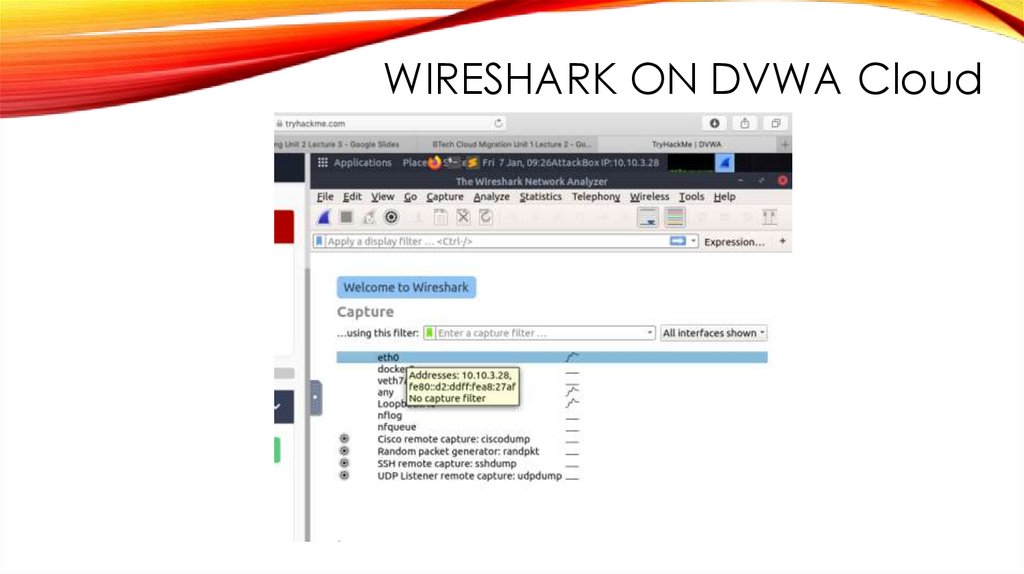
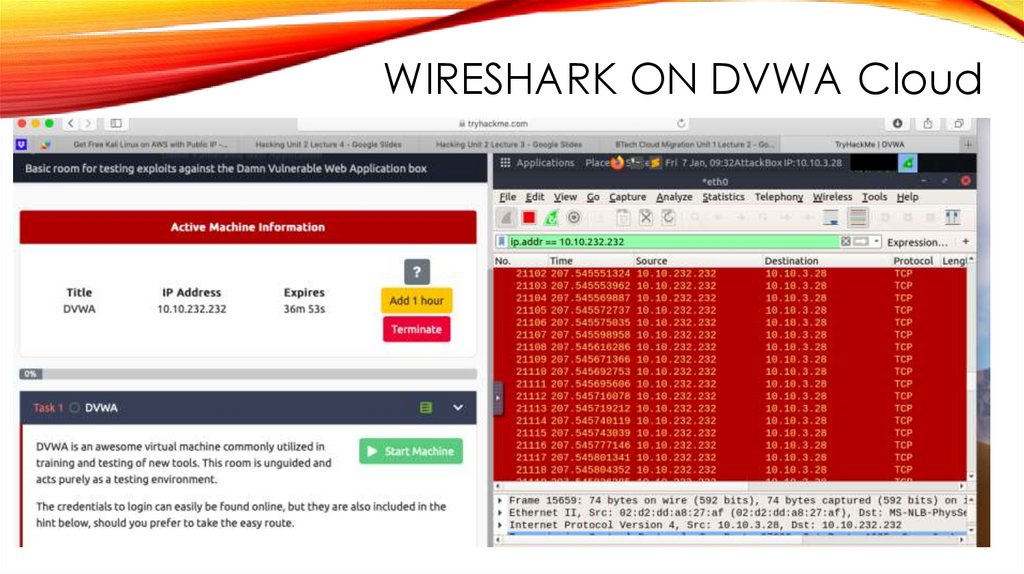
WIRESHARK ON DVWA Cloud33.
WIRESHARK ON DVWA Cloud34.
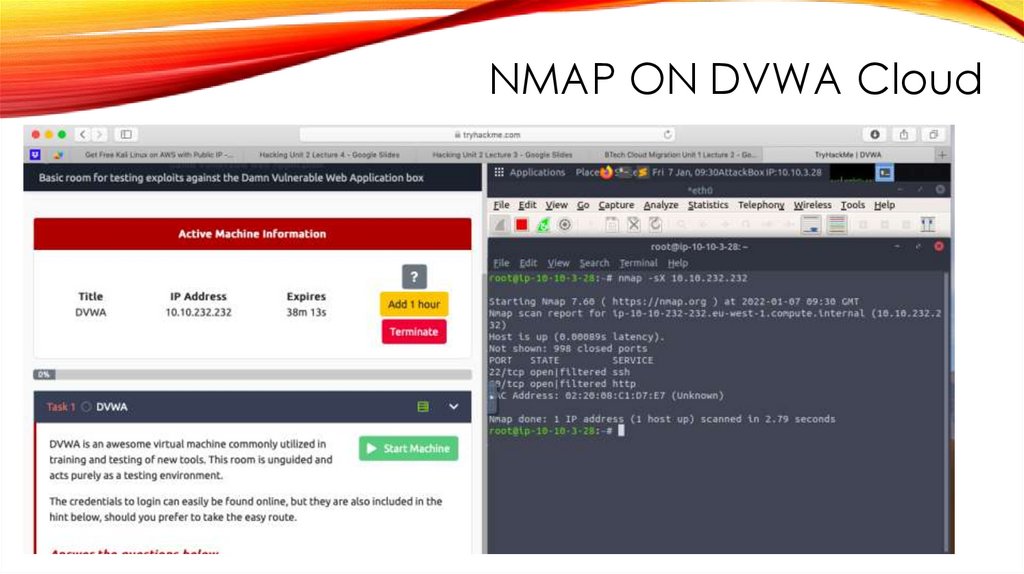
NMAP ON DVWA Cloud35.
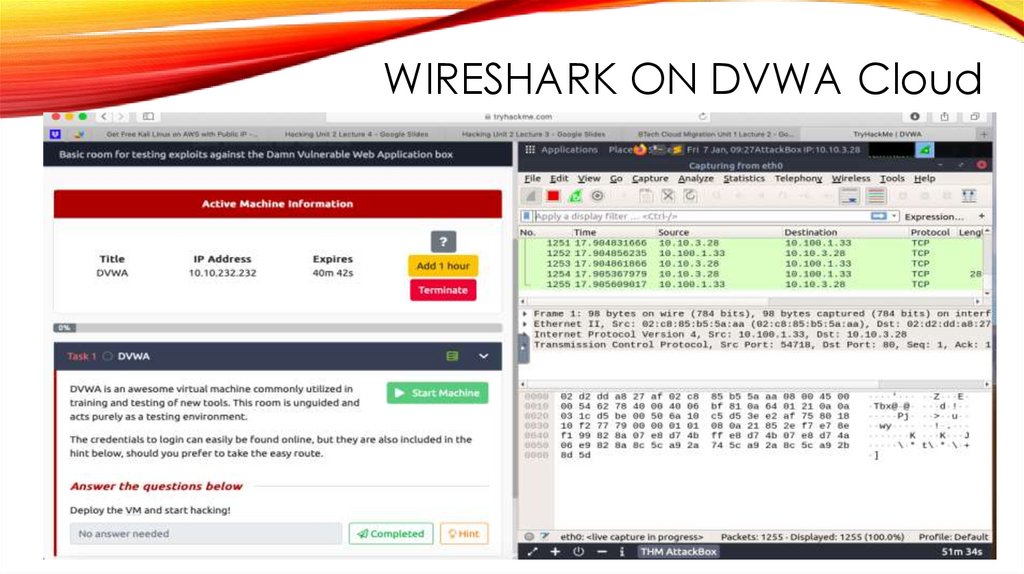
WIRESHARK ON DVWA Cloud36.
ETTERCAP on TRYHACKMEFirst Start Machine
Run Attackbox
Login with SSh using IP address of Target Machine
Using su -
ETTERCAP -C then select eth0 or eth1
ETTERCAP -Tq -i eth0
ETTERCAP -Tq -i eth1
ETTERCAP -G -i eth0
37.
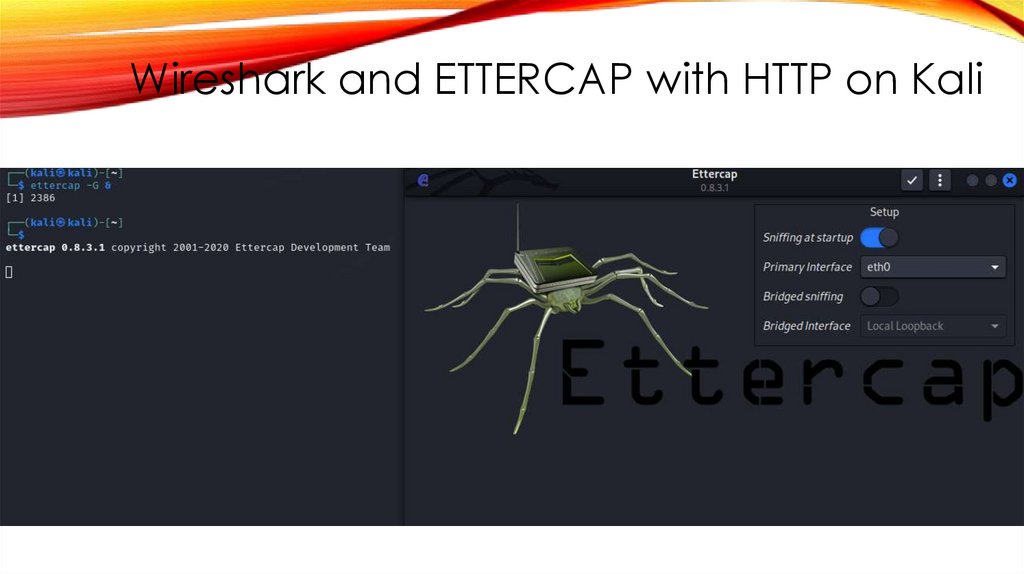
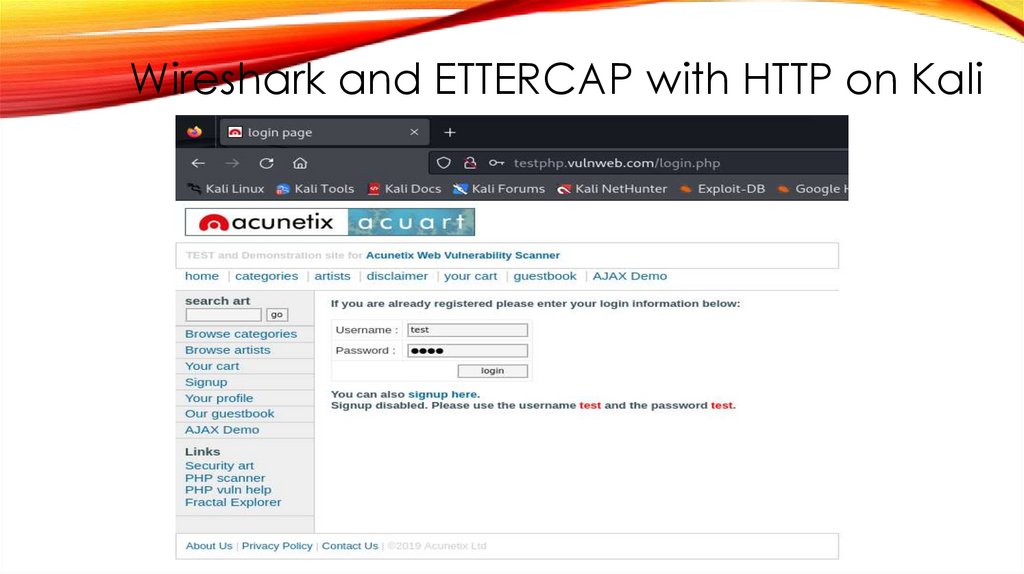
Wireshark and ETTERCAP with HTTP on Kali38.
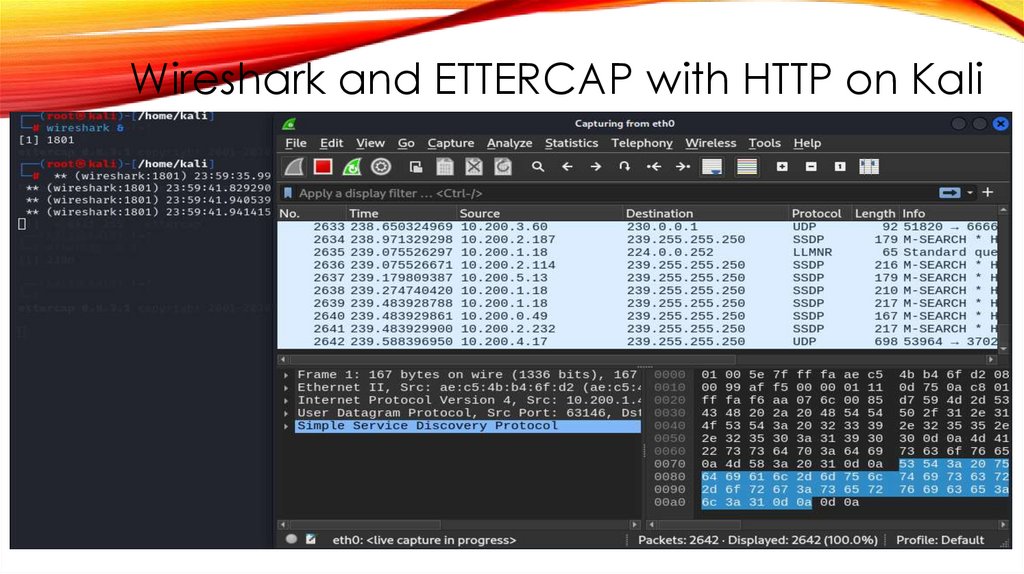
Wireshark and ETTERCAP with HTTP on Kali39.
Wireshark and ETTERCAP with HTTP on Kali40.
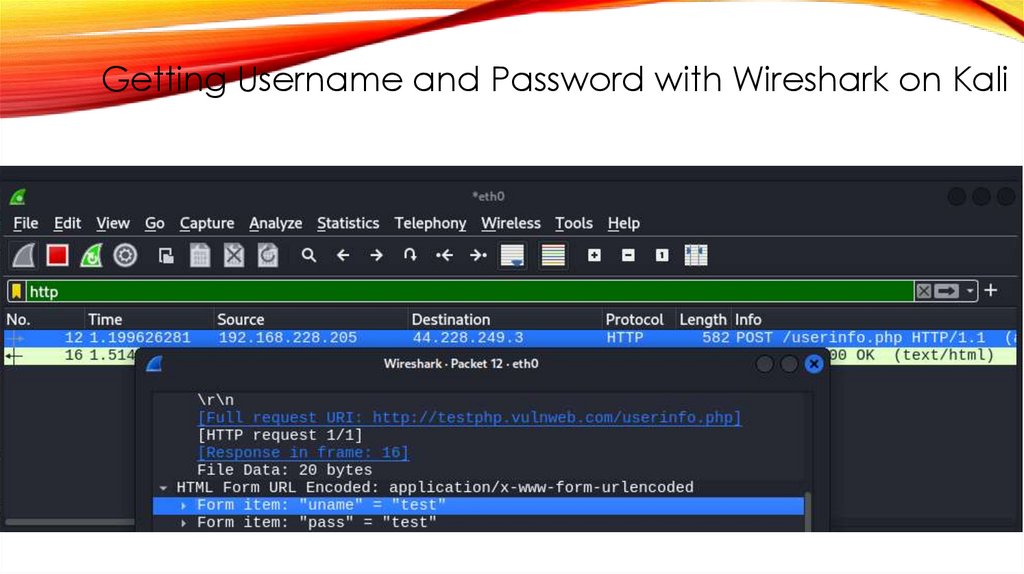
Getting Username and Password with Wireshark on Kali41.
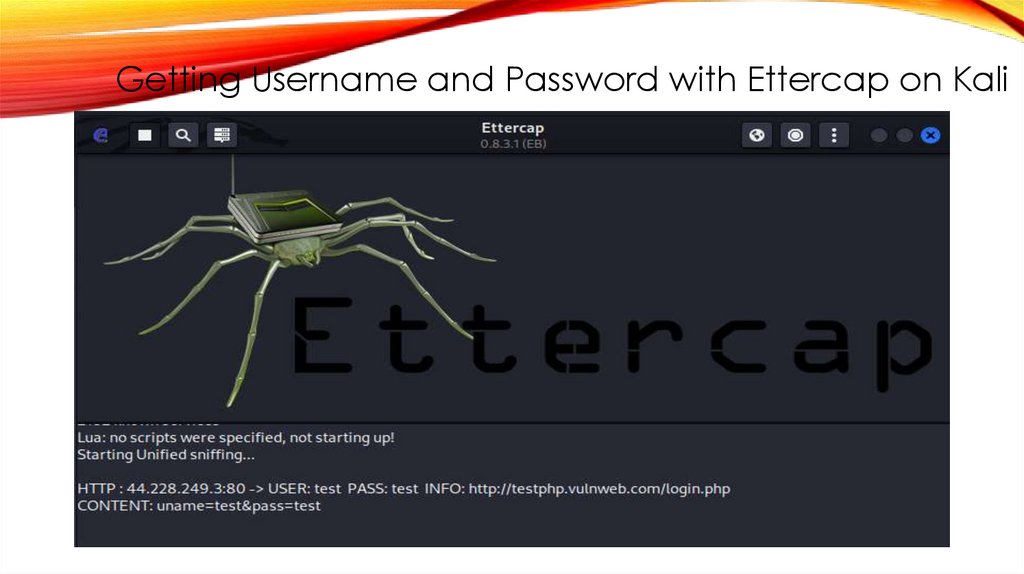
Getting Username and Password with Ettercap on Kali42.
Week 2 AssignmentAssignment Week 2: Case study of TCP 3-way
handshake
or
Assignment Week 2: Capture HTTP packet and extract
username and Password using Wireshark & Ettercap







 Информатика
Информатика








