Похожие презентации:
Hacking Lab Practice
1.
Hacking LABDr Bishwajeet Pandey, SMIEEE
Professor-Dep. of IS&CS, Astana IT University, Kazakhstan
PhD (Gran Sasso Science Institute, L'Aquila, Italy)
Visiting Professor at
L.N. Gumilyov Eurasian National University, Kazakhstan
UCSI UNIVERSITY-Malaysia
2.
ABOUT COURSE TEACHERPhD from Gran Sasso Science Institute, Italy
PhD Supervisor Prof Paolo Prinetto from Politecnico Di Torino, Italy
MTech from Indian Institute of Information Technology, Gwalior, India
Visited 47 Countries Across The Globe
Written 200+ Research paper with 212 Researcher from 93 Universities
Scopus Profile: https://www.scopus.com/authid/detail.uri?authorId=57203239026
Google Scholar: https://scholar.google.com/citations?user=UZ_8yAMAAAAJ&hl=hi
IBM Certified Solution Designer
EC-Council Certified Ethical Hacker
AWS Certified Cloud Practitioner
Email: bishwajeet.pandey@gssi.it, dr.pandey@ieee.org, bk.pandey@astanait.edu.kz
3.
Hacking LAB: Practices1.
Working with network commands in Windows and Linux (Assignment Week 1: Make a list of 50 Commands with syntax and
usage)
2. Capturing and Analyzing Network Traffic using Wireshark (Assignment Week 2: Case study of TCP 3-way handshake) or
(Assignment Week 2: Capture HTTP packet and extract username and Password using Ettercap and Wireshark)
3. Website technical information gathering using maltego, httrack, whois. (Assignment Week 3: Chose any two tools from
OSINTFramework.com and discuss the steps to use it)
4. Full Scan, Half Open Scan, Stealth Scan and XMAS Scan using NMAP (Assignment Week 4: Run Any 10 NSE Scripts )
5. Perform Host Discovery, Service Discovery(FTP, Telnet, SSH, Java RMI Server, SMB), Port Scanning using Metasploit or
(Assignment Week 5: Demonstrate Eternal Blue, VSFTPD, SSH Login exploit using Metasploit)
6. Social engineering using SEToolkit (Assignment Week 6: Create a Clone of GMAIL using SEToolkit)
7. Web parameter poisoning using burp suite (Assignment Week 7: Change the price of all item to 1 USD on e-commerce shopping
cart)
8. Create Fake Harmless Virus using Notepad (Assignment Week 8: Create a MAC/Window and Android Spyware
with MSFVenom)
9. Malware Classification using Convolutional Neural Networks using Google Colab (Assignment Week 9: Malware Classification
using Convolutional Neural Networks using Jupyter Notebook)
10. Perform session hijacking using Zed Attack Proxy (ZAP) (Assignment Week 10: Perform Session Hijacking using Wireshark)
4.
Week 10 PracticePerform session hijacking using
Zed Attack Proxy (ZAP)
Assignment Week 10: Perform
Session Hijacking
using Wireshark
5.
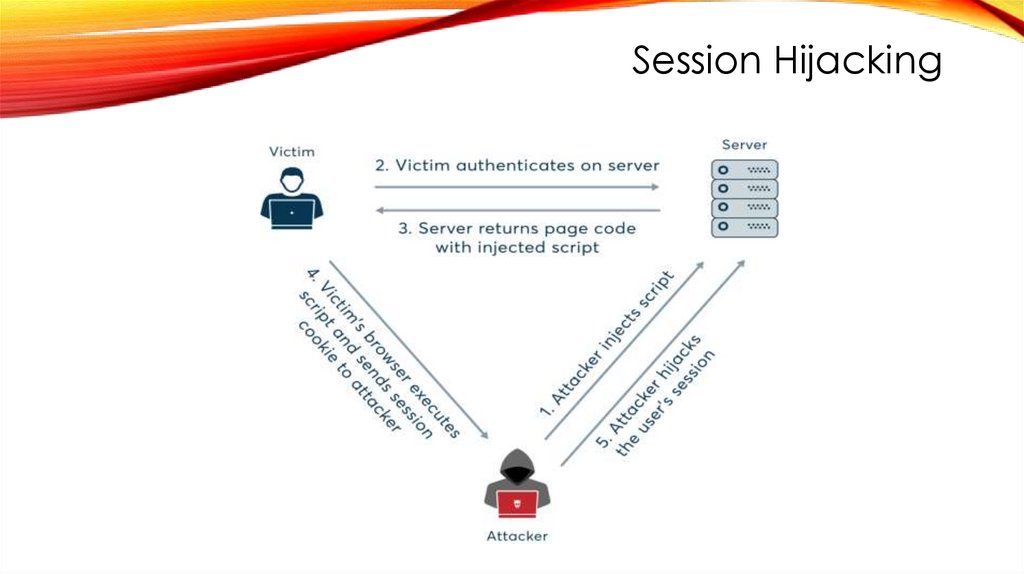
Session Hijacking● A session hijacking attack happens when an attacker takes over your
internet session — for instance, while you're checking your credit card
balance, paying your bills, or shopping at an online store. Session hijackers
usually
target
browser
or
web
application
sessions.
● Session hijacking is an attack where a user session is taken over by an
attacker. To perform session hijacking, an attacker needs to know the
victim's session ID (session key). This can be obtained by stealing the
session cookie or persuading the user to click a malicious link containing a
prepared session ID.
6.
Session Hijacking7.
ZAP(Zed Attack Proxy)OWASP ZAP (SHORT FOR ZED ATTACK PROXY) IS AN OPEN-SOURCE WEB
APPLICATION SECURITY SCANNER. ... WHEN USED AS A PROXY SERVER IT
ALLOWS THE USER TO MANIPULATE ALL OF THE TRAFFIC THAT PASSES
THROUGH IT, INCLUDING TRAFFIC USING HTTPS. IT CAN ALSO RUN IN A
DAEMON MODE WHICH IS THEN CONTROLLED VIA A REST API.
THE ZED ATTACK PROXY (ZAP) IS AN EASY TO USE INTEGRATED
PENETRATION TESTING TOOL FOR FINDING VULNERABILITIES IN WEB
APPLICATIONS. IT IS DESIGNED TO BE USED BY PEOPLE WITH A WIDE RANGE
OF SECURITY EXPERIENCE AND AS SUCH IS IDEAL FOR DEVELOPERS AND
FUNCTIONAL TESTERS WHO ARE NEW TO PENETRATION TESTING.
8.
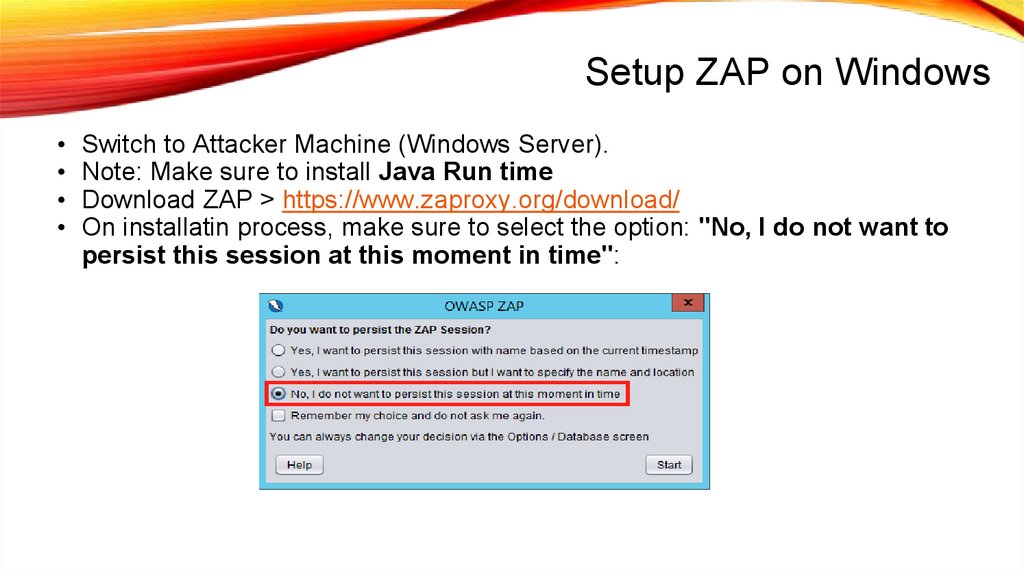
Setup ZAP on Windows• Switch to Attacker Machine (Windows Server).
• Note: Make sure to install Java Run time
• Download ZAP > https://www.zaproxy.org/download/
• On installatin process, make sure to select the option: "No, I do not want to
persist this session at this moment in time":
9.
Setup ZAP on MAC10.
ZAP Features• Free , open source.
• Cross platform.
• Easy to use.
• Easy to install.
• Internationalized.
• Fully documented.
• Involvement actively encouraged.
• Reuse well regarded components.
11.
ZAP Features• Intercepting proxy.
• Automated scanner.
• Passive scanner.
• Brute force scanner.
• Web sockets.
• Advanced sql injection scanner.
• Port scanning.
• Advanced alerts.
12.
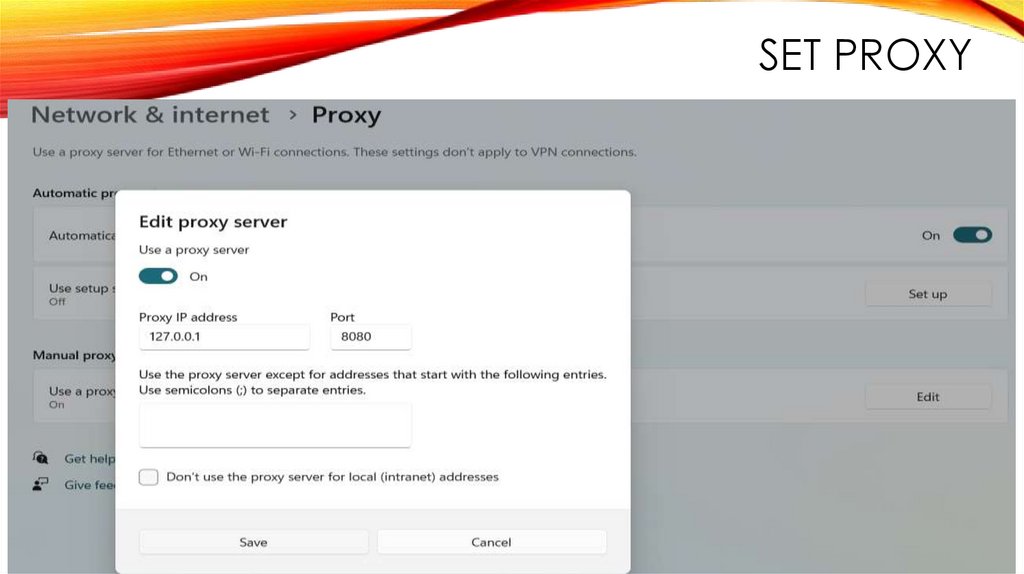
SET PROXY13.
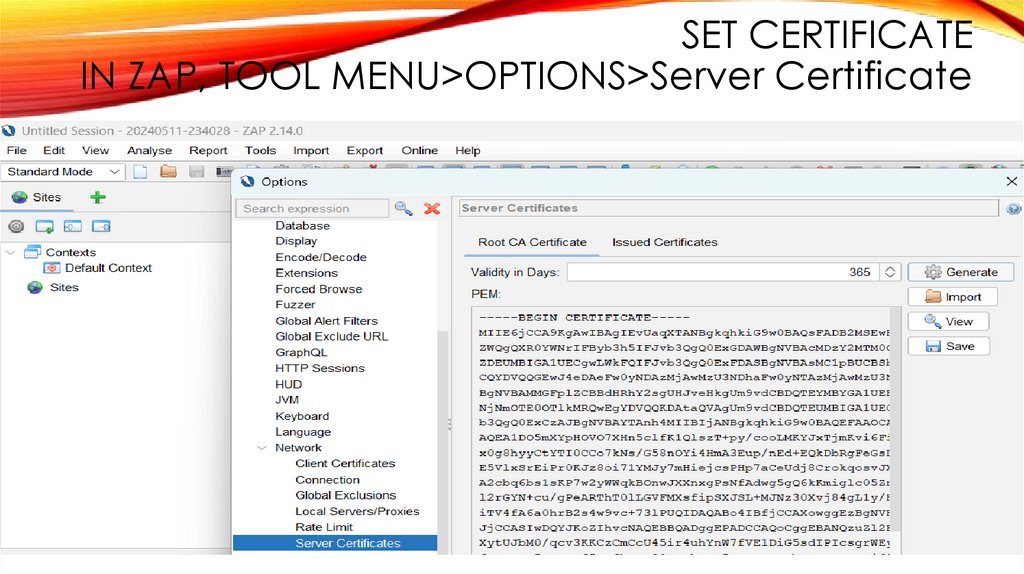
SET CERTIFICATEIN ZAP, TOOL MENU>OPTIONS>Server Certificate
14.
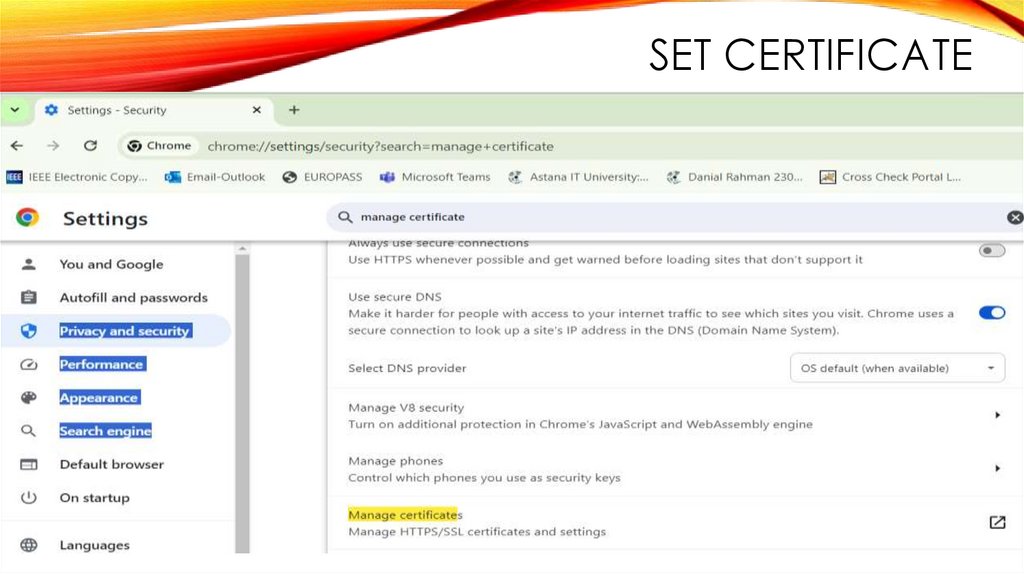
SET CERTIFICATE15.
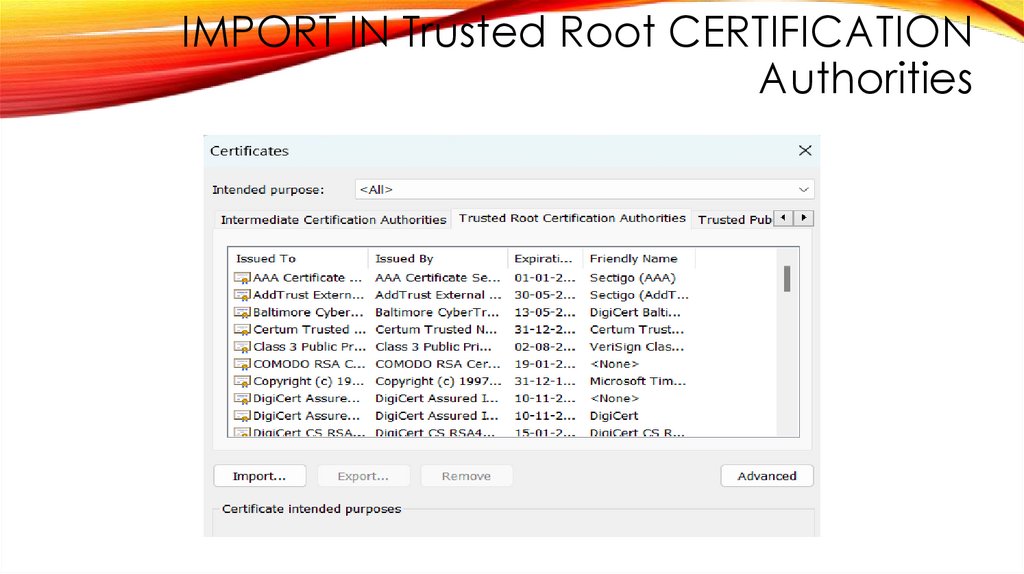
IMPORT IN Trusted Root CERTIFICATIONAuthorities
16.
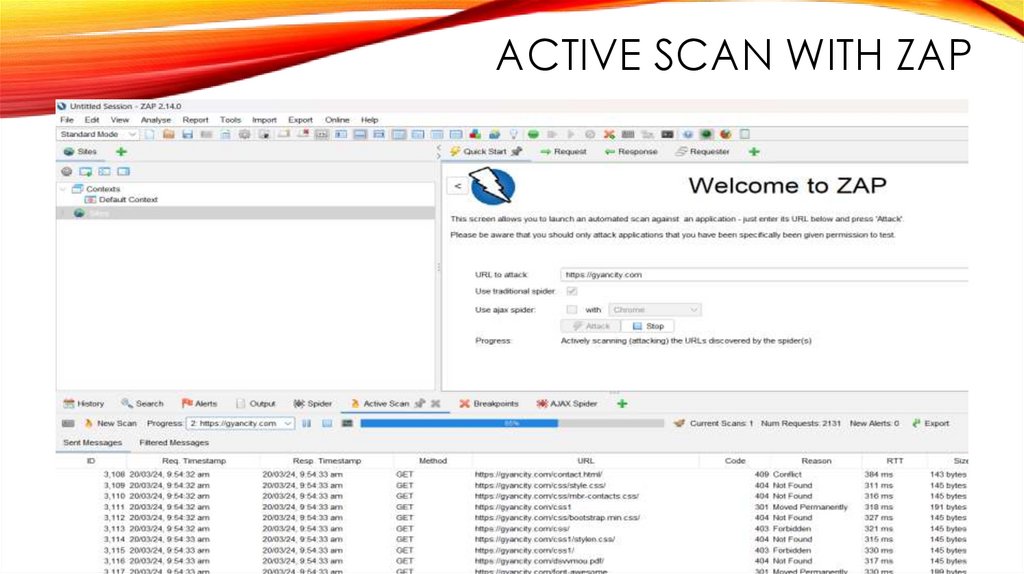
ACTIVE SCAN WITH ZAP17.
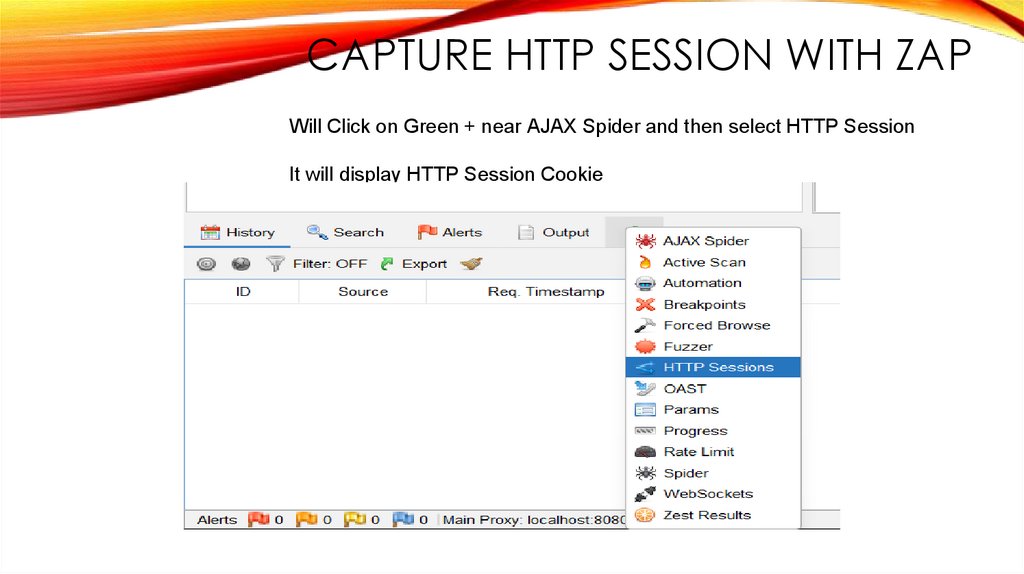
CAPTURE HTTP SESSION WITH ZAPWill Click on Green + near AJAX Spider and then select HTTP Session
It will display HTTP Session Cookie
18.
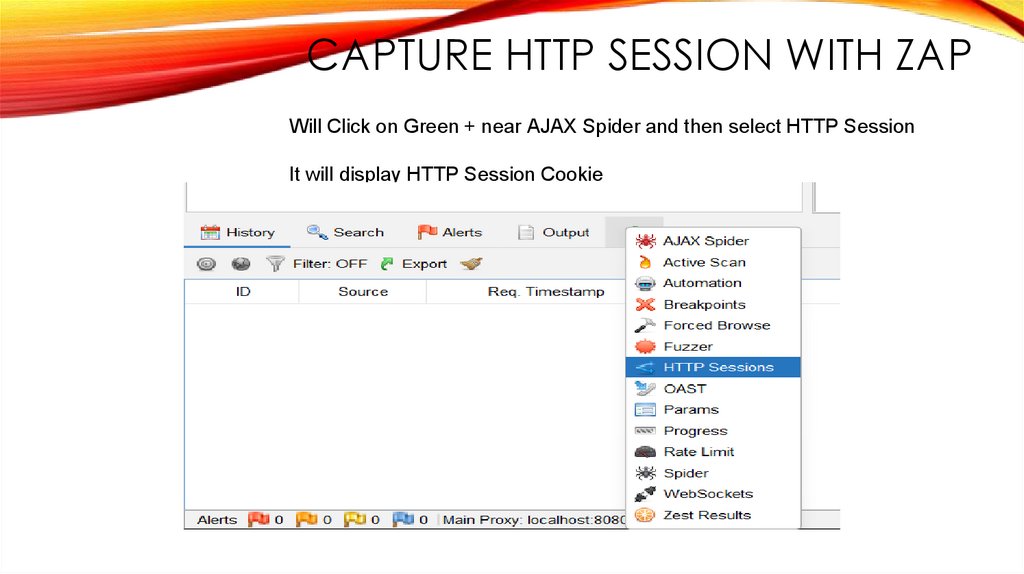
CAPTURE HTTP SESSION WITH ZAPWill Click on Green + near AJAX Spider and then select HTTP Session
It will display HTTP Session Cookie
19.
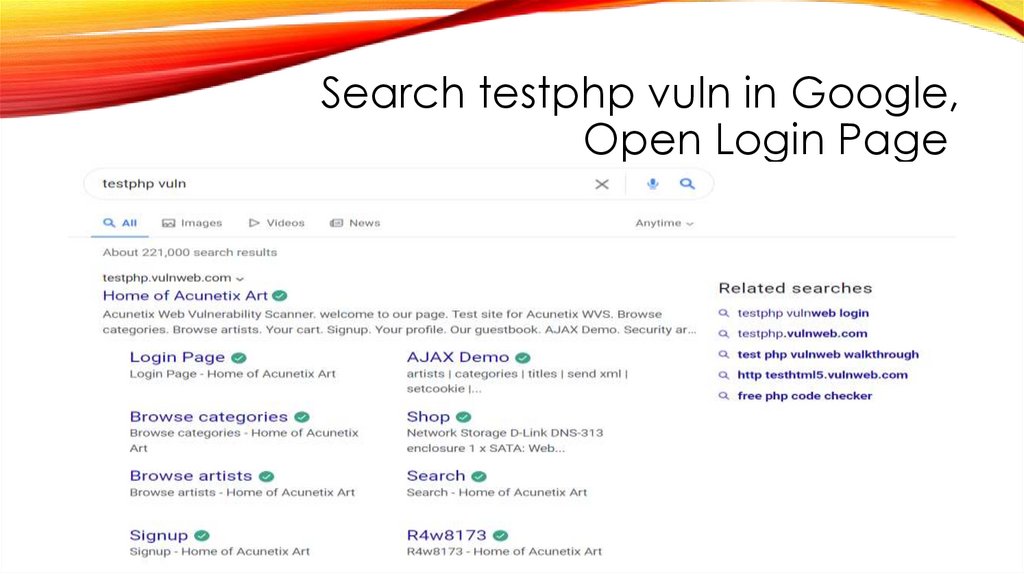
Search testphp vuln in Google,Open Login Page
20.
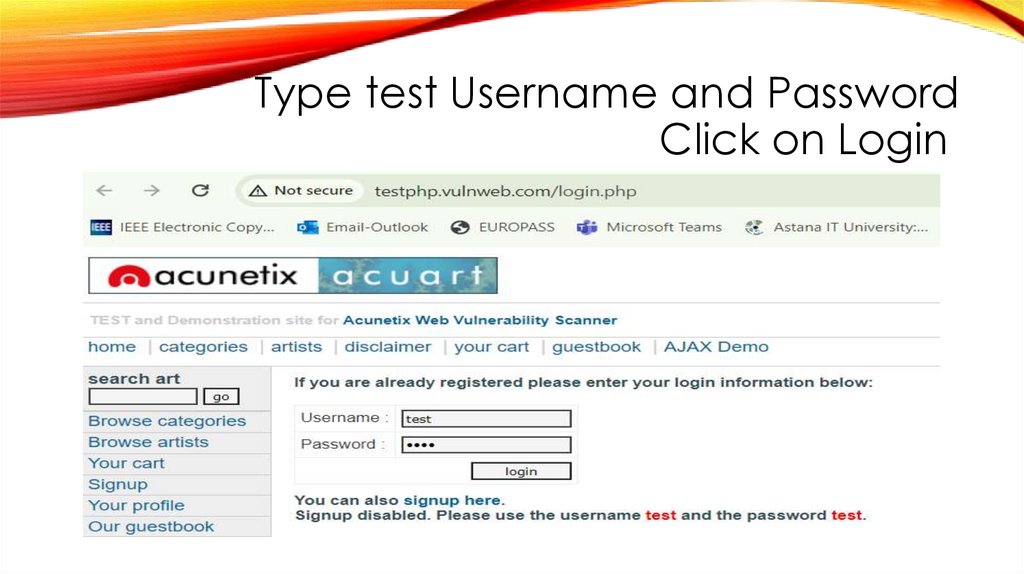
Type test Username and PasswordClick on Login
21.
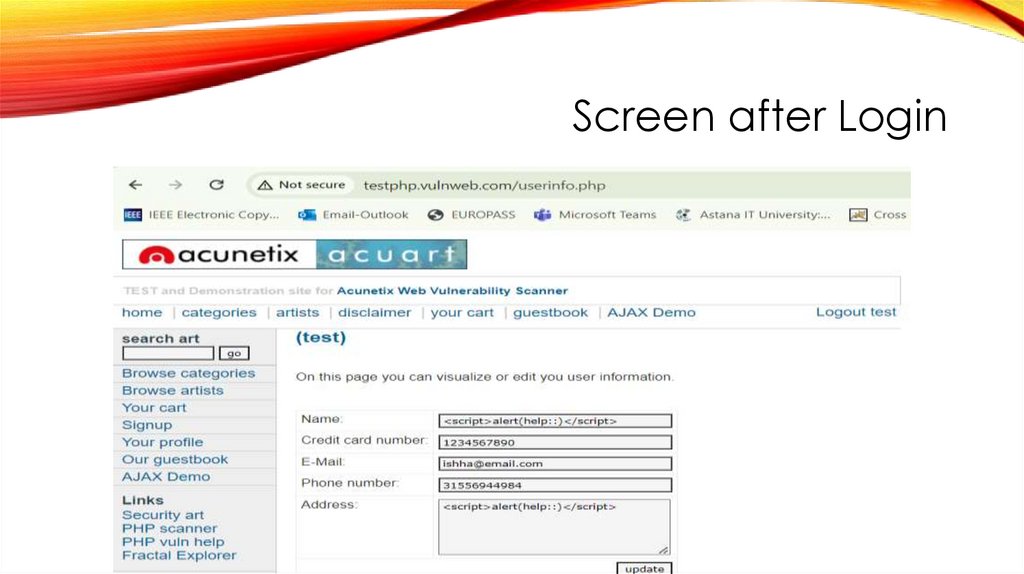
Screen after Login22.
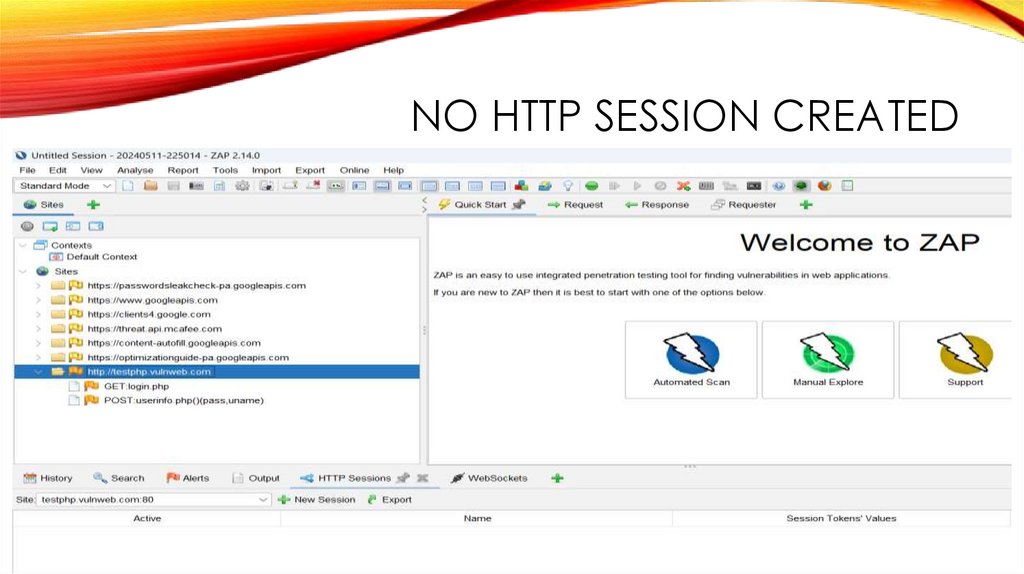
NO HTTP SESSION CREATED23.
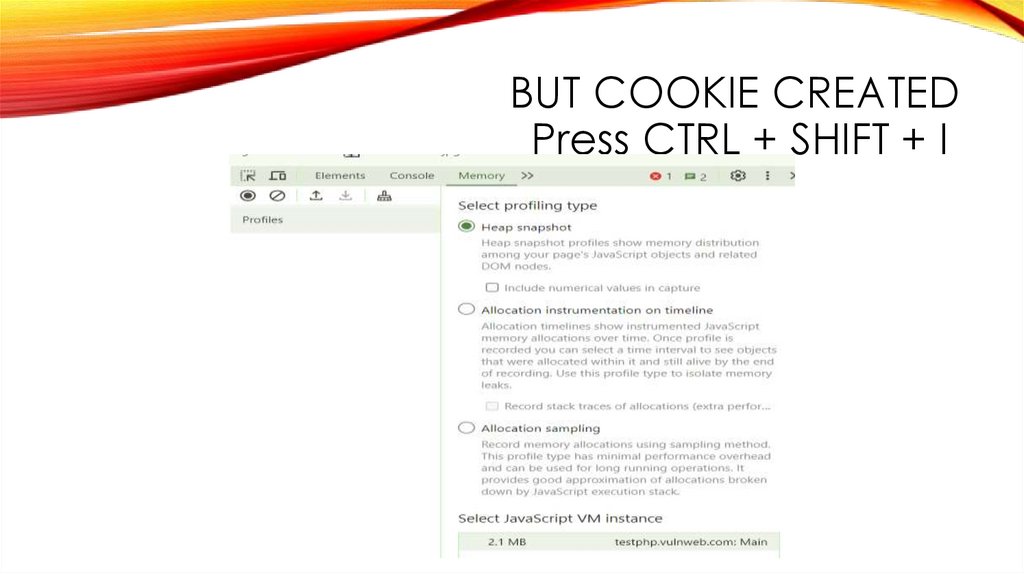
BUT COOKIE CREATEDPress CTRL + SHIFT + I
24.
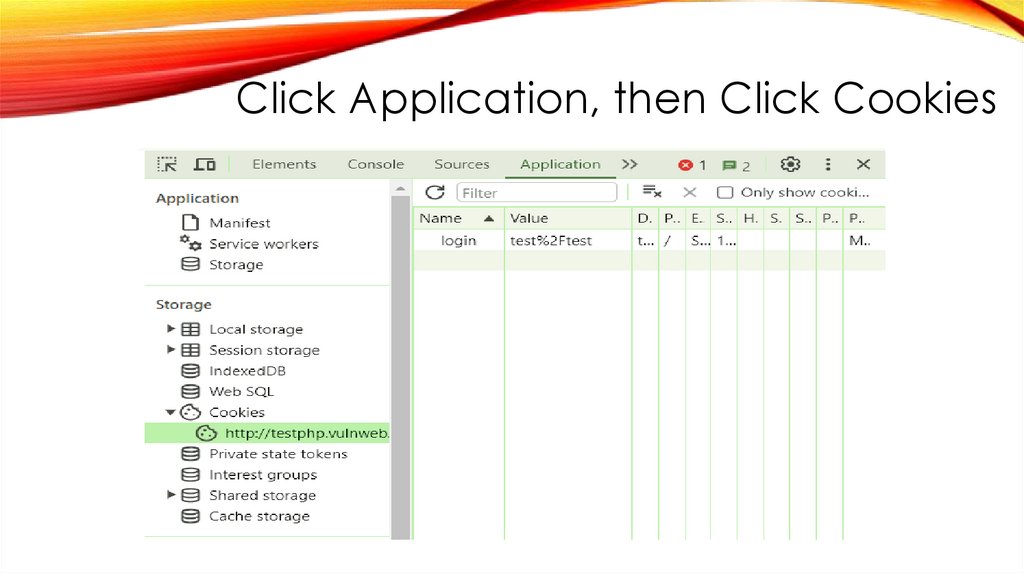
Click Application, then Click Cookies25.
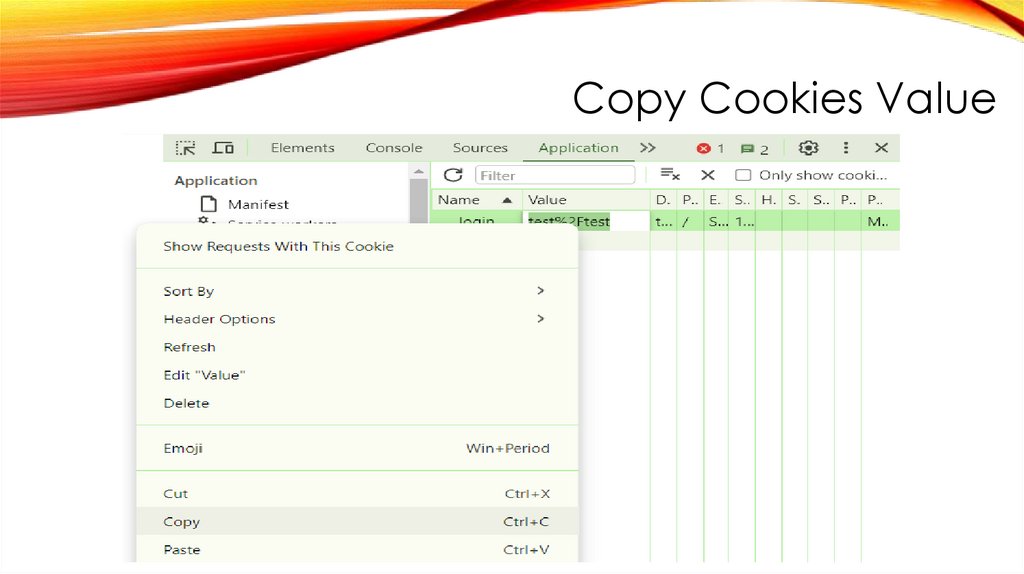
Copy Cookies Value26.
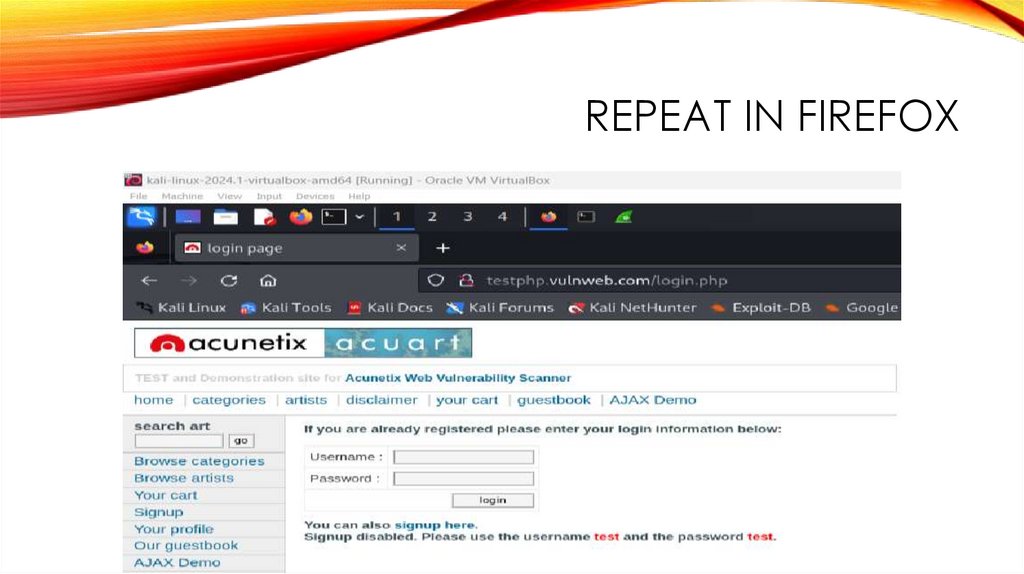
REPEAT IN FIREFOX27.
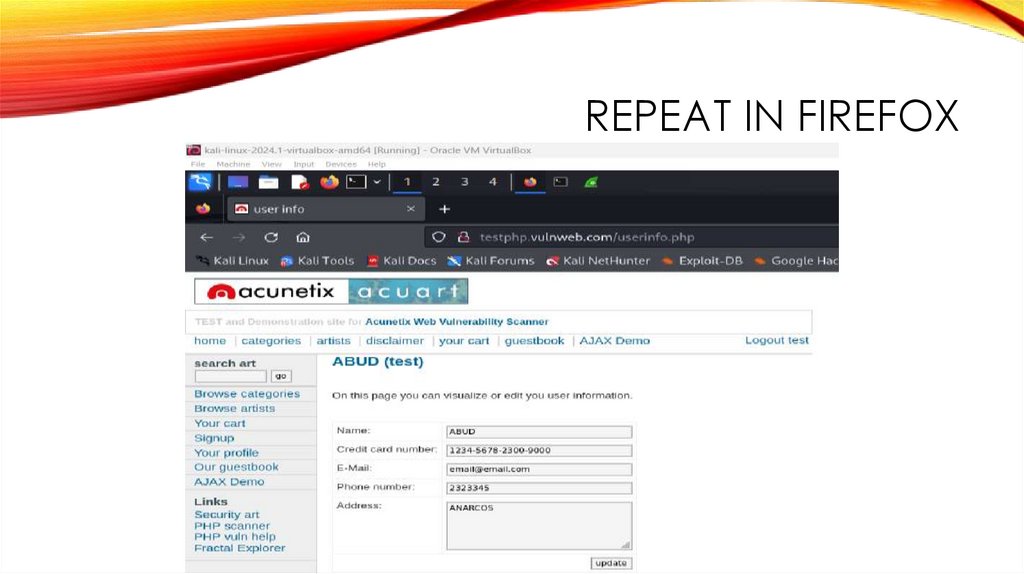
REPEAT IN FIREFOX28.
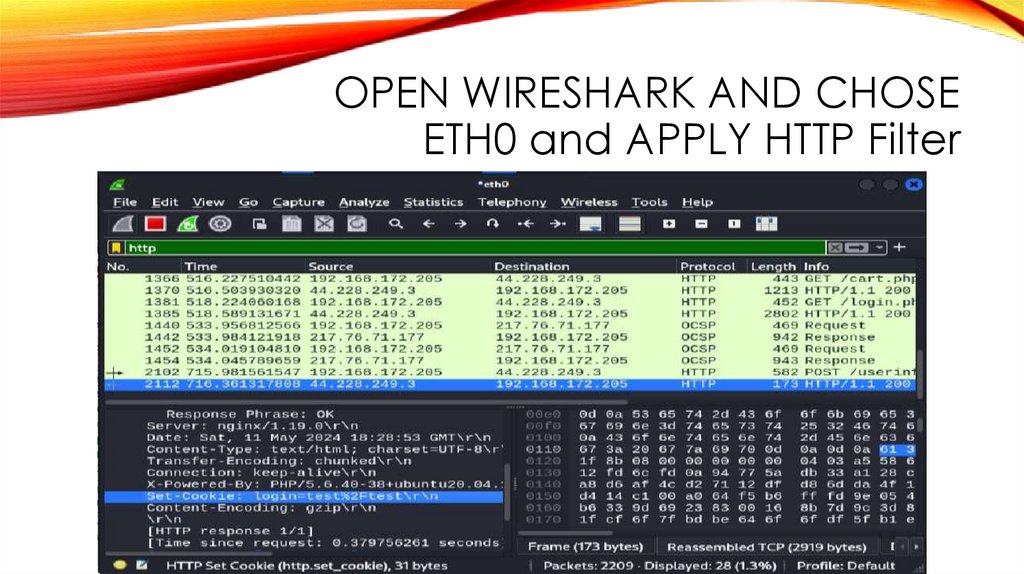
OPEN WIRESHARK AND CHOSEETH0 and APPLY HTTP Filter
29.
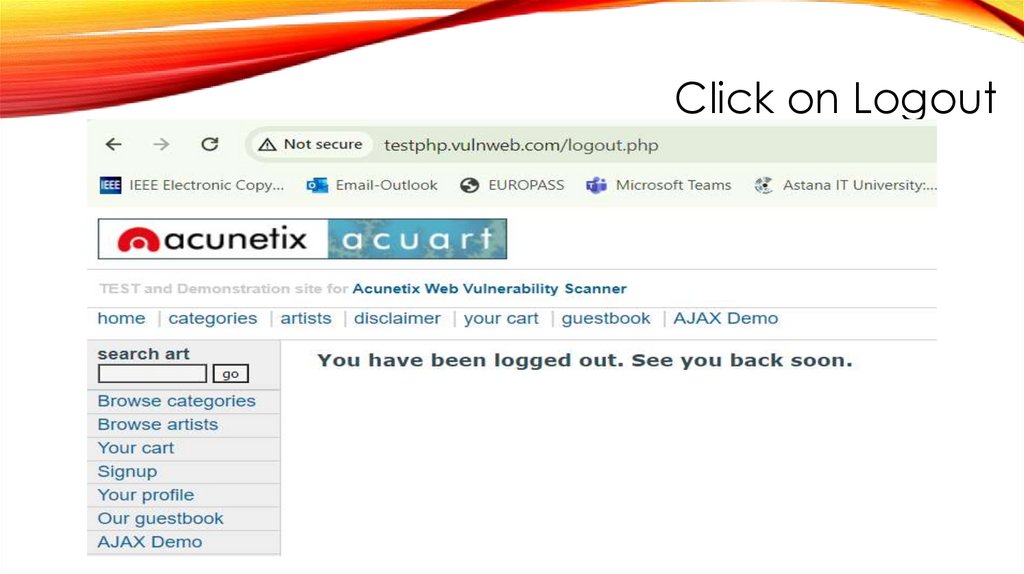
Click on Logout30.
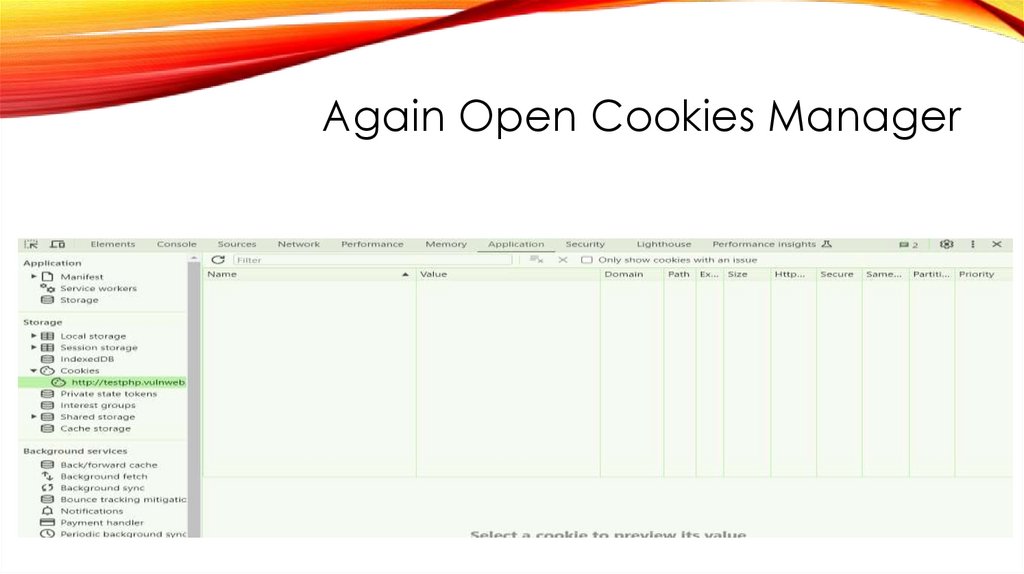
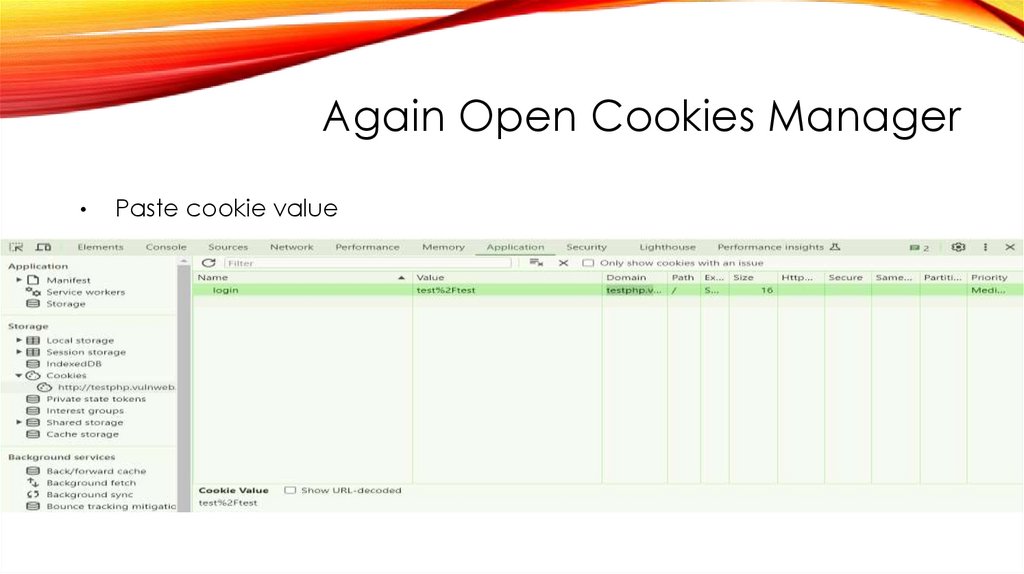
Again Open Cookies Manager31.
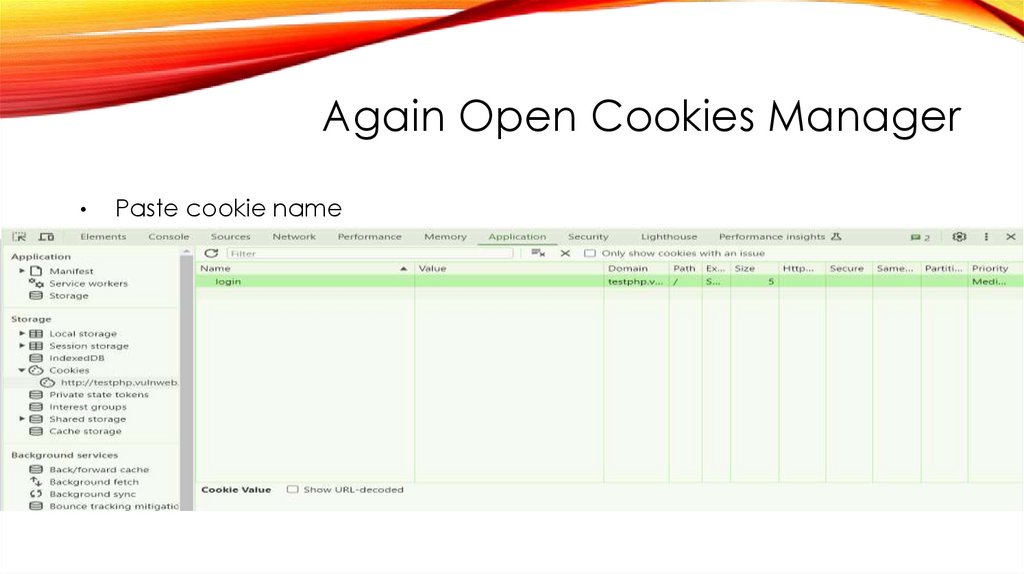
Again Open Cookies ManagerPaste cookie name
32.
Again Open Cookies ManagerPaste cookie value
33.
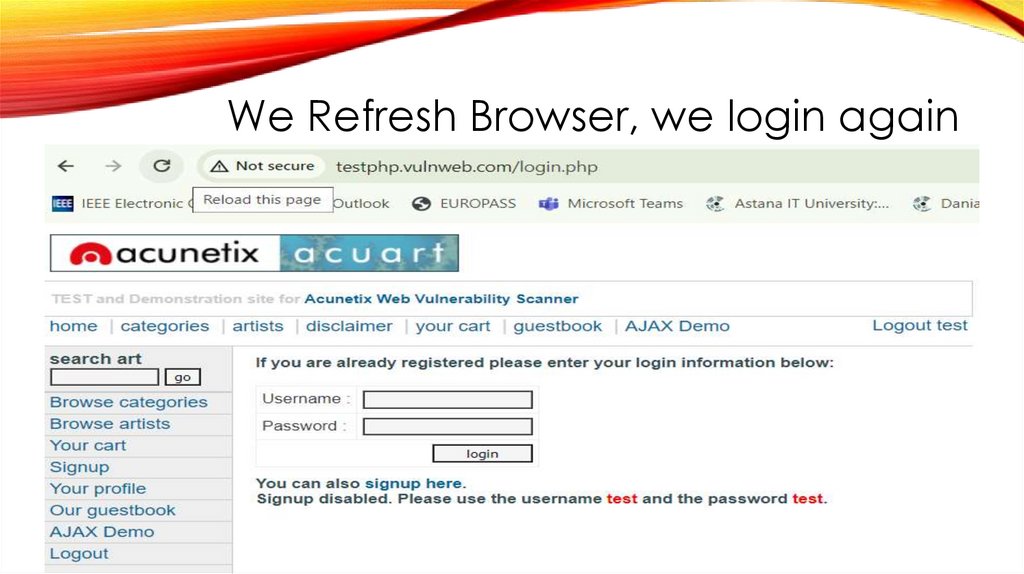
We Refresh Browser, we login again34.
ZAPOPEN ANY
HTTP:://METASPLOITABLE-IP/mutillidae/index.php?page=login.php
HTTP:// METASPLOITABLE-IP/dvwa
We shall get
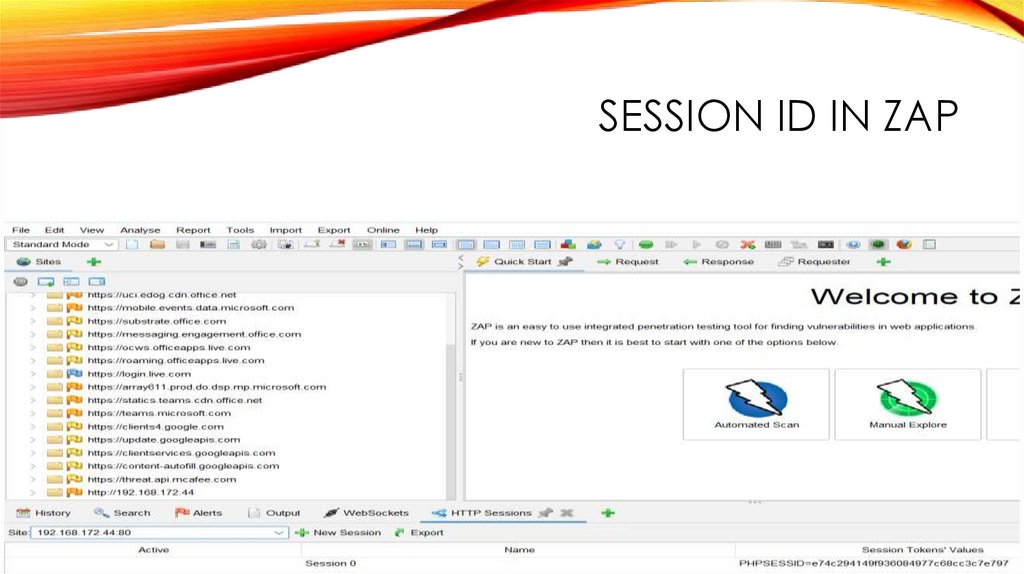
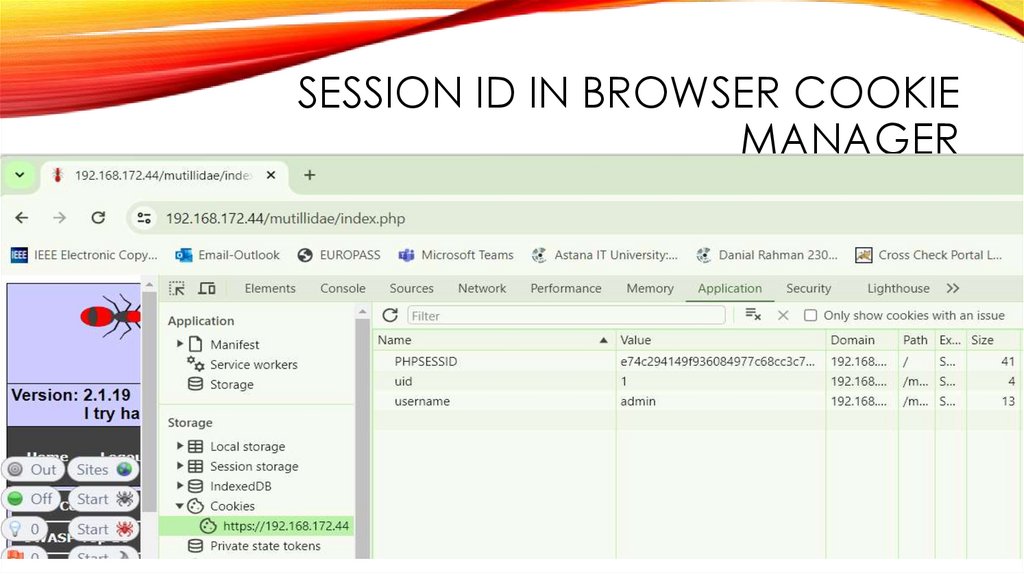
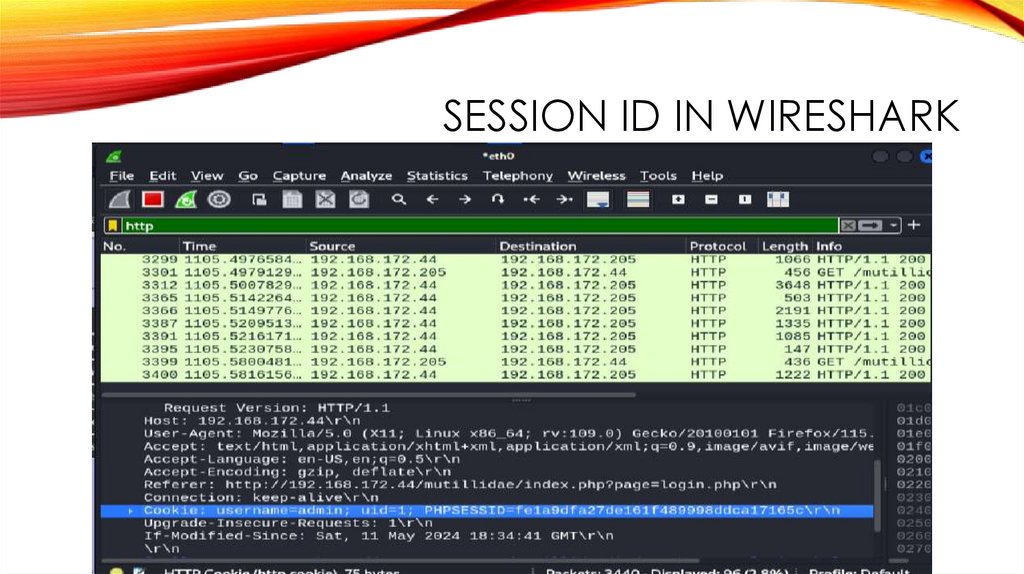
PHPSESSID in 3 Place:
1. ZAP,
2. BROWSER COOKIE Manager,
3. WIRESHARK
35.
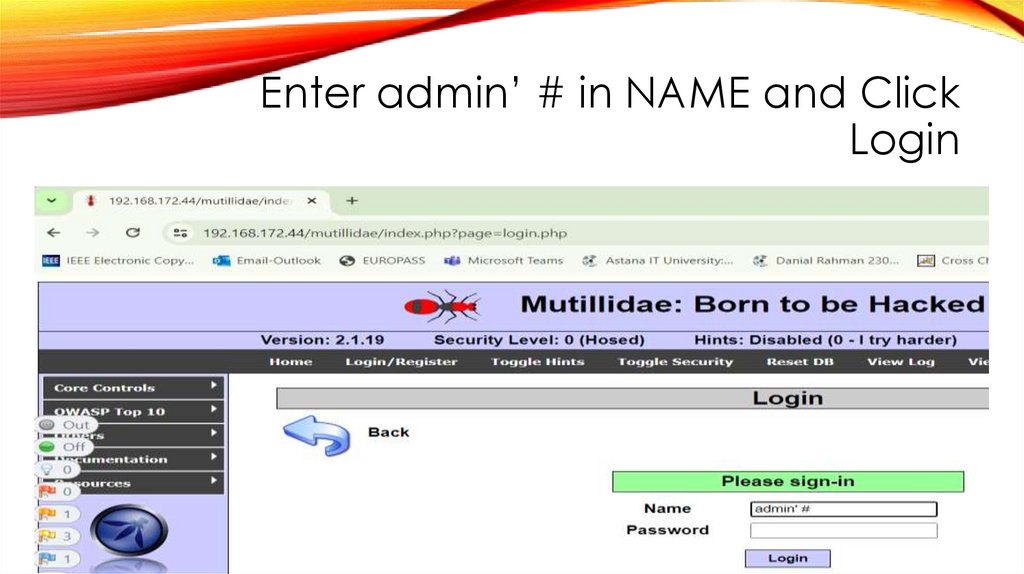
Enter admin’ # in NAME and ClickLogin
36.
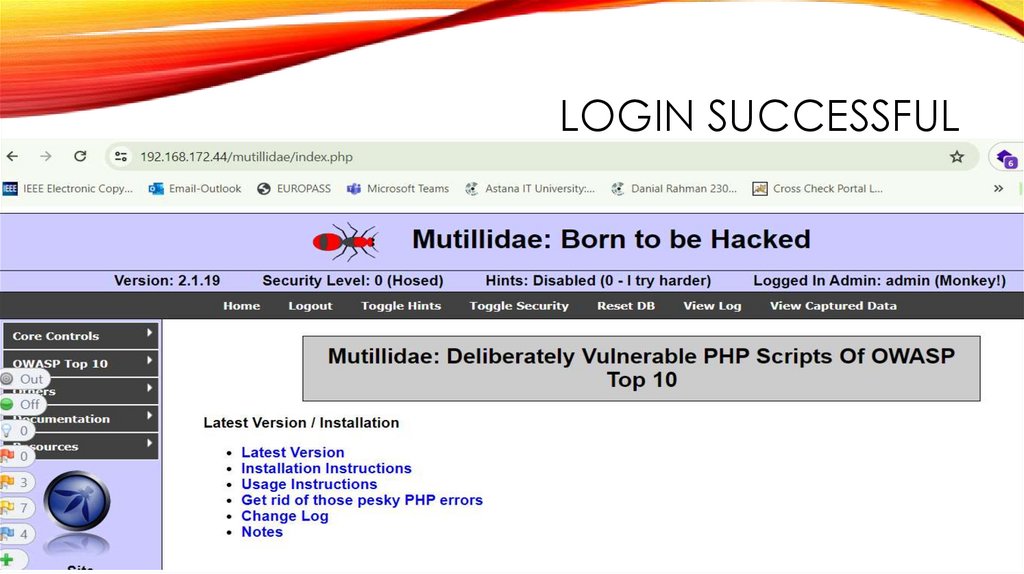
LOGIN SUCCESSFUL37.
SESSION ID IN ZAP38.
SESSION ID IN BROWSER COOKIEMANAGER
39.
SESSION ID IN WIRESHARK40.
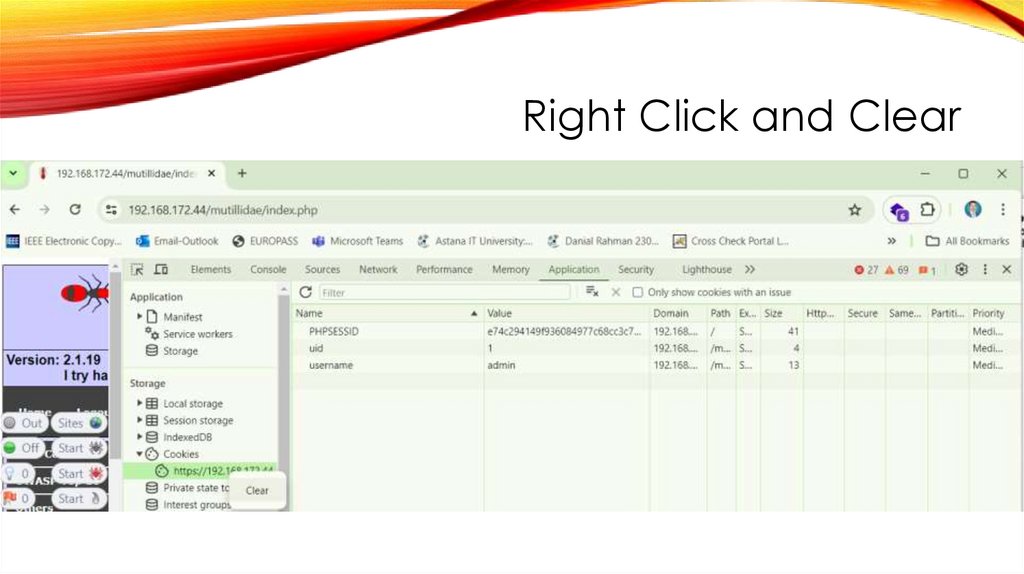
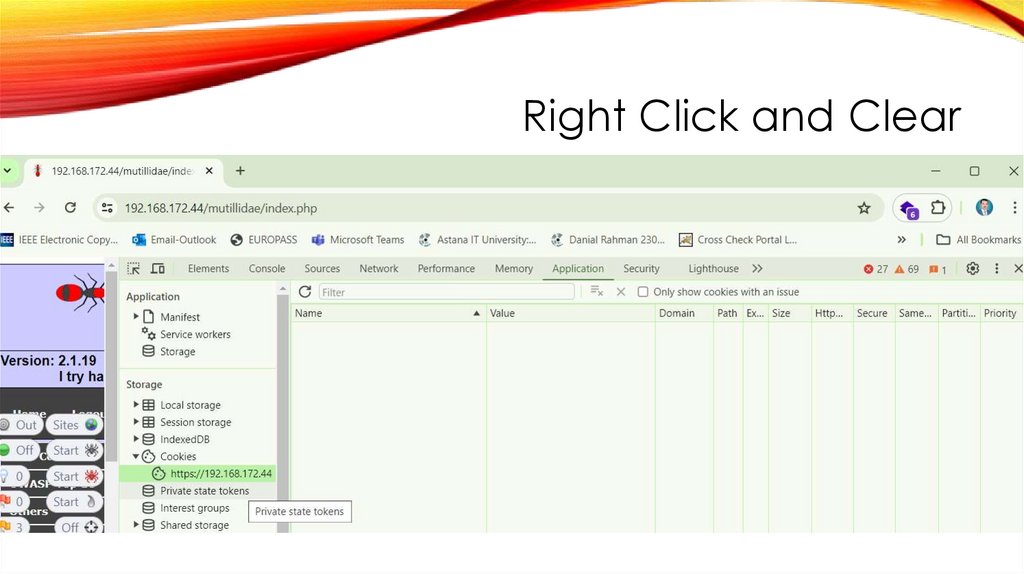
Right Click and Clear41.
Right Click and Clear42.
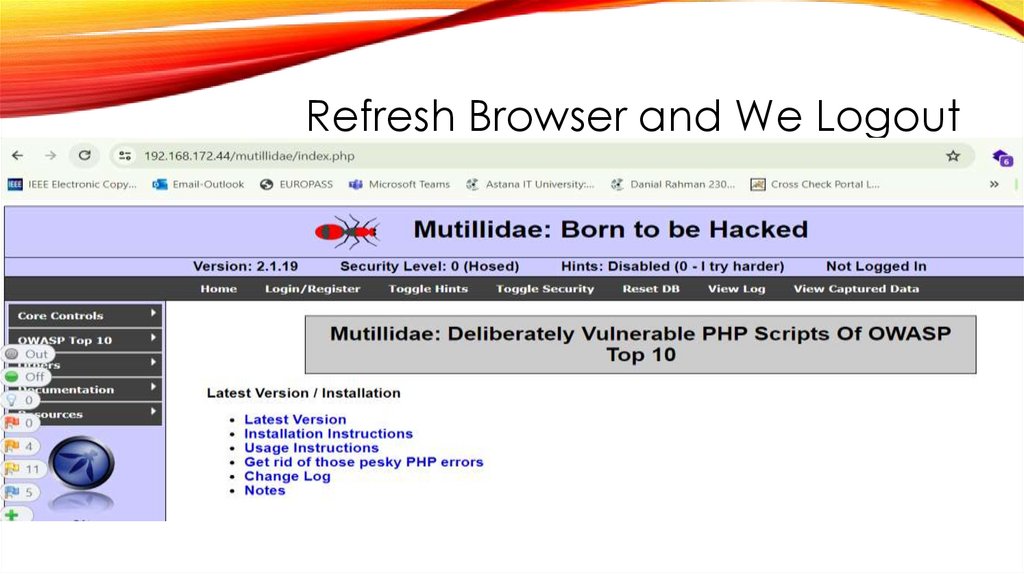
Refresh Browser and We Logout43.
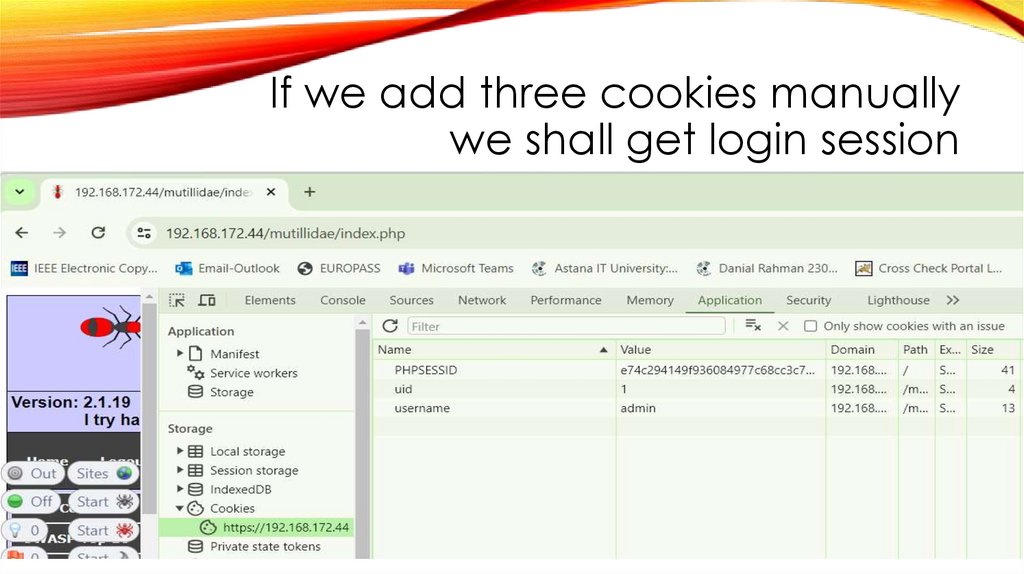
If we add three cookies manuallywe shall get login session
44.
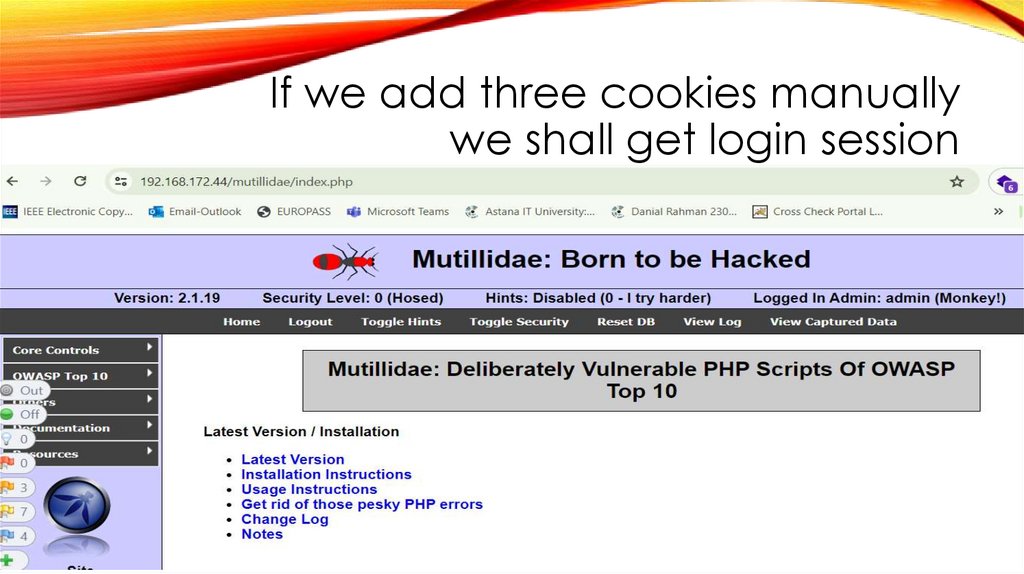
If we add three cookies manuallywe shall get login session
45.
ZAPOPEN ANY
HTTP:// OWASP-BWA-IP/WebGoat
We shall get
JSESSIONID in 3 Place:
1. ZAP,
2. BROWSER COOKIE Manager,
3. WIRESHARK









 Информатика
Информатика








