Похожие презентации:
Social engineering. Understanding and defense. Manipulating the human element
1.
Social Engineering:Understanding and
Defense
Manipulating the Human Element
2.
Definition of SocialEngineering
• Social engineering is the art of manipulating
people into performing actions or divulging
confidential information.
• Importance: It's used to gain unauthorized
access to systems or information, often
exploiting human psychology rather than
technical vulnerabilities.
3.
How SocialEngineering Works
• Process: Discuss the steps involved in a
typical social engineering attack, such as
reconnaissance, establishing trust,
exploitation, and execution.
• Principles: Highlight principles like
authority, scarcity, urgency, familiarity,
and social proof that social engineers
often exploit.
4.
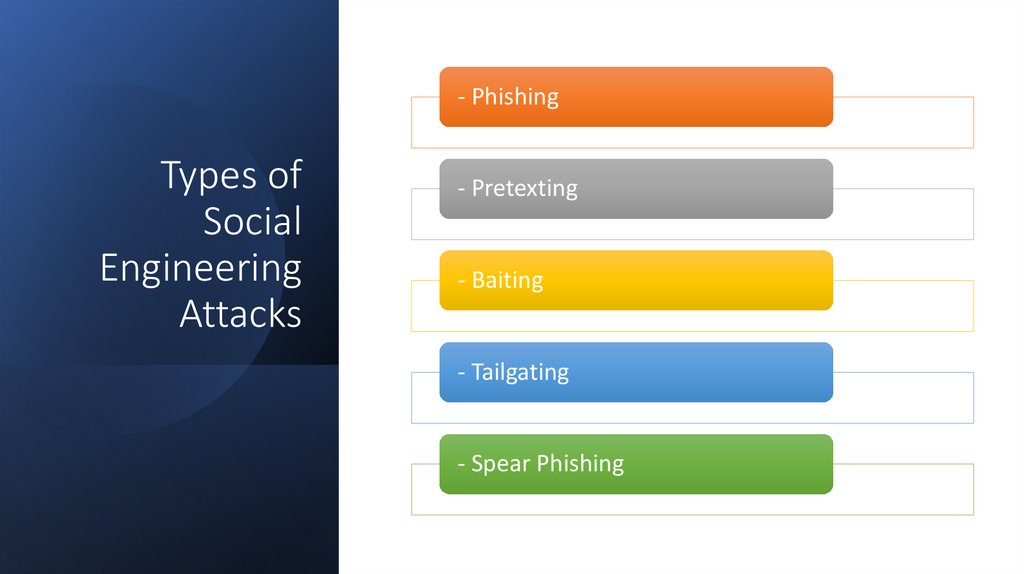
- PhishingTypes of
Social
Engineering
Attacks
- Pretexting
- Baiting
- Tailgating
- Spear Phishing
5.
Defense Against Social Engineering- Education
and Awareness
- Verification
Procedures
- Strong
Authentication
- Security
Policies
- Regular
Updates
6.
Examples of SocialEngineering Attacks
• Include examples of phishing, pretexting,
baiting, tailgating, and spear phishing attacks,
along with relevant statistics.
7.
Statistics on SocialEngineering
• Present relevant statistics on the
prevalence and success rates of social
engineering attacks using graphs, charts,
or infographics.
8.
ConclusionRECAP KEY POINTS ABOUT SOCIAL
ENGINEERING AND ITS IMPACT ON SECURITY.
EMPHASIZE THE IMPORTANCE OF VIGILANCE
AND PROACTIVE MEASURES IN DEFENDING
AGAINST SOCIAL ENGINEERING ATTACKS.
9.
Q&A• Open the floor for questions and discussion.



 Социология
Социология








