Похожие презентации:
Introduction to Information Security Challenges
1.
Introduction toInformation Security
Challenges
Information security plays a vital role in protecting sensitive data, systems,
and networks. Cybersecurity threats are constantly evolving, demanding a
robust and proactive approach to safeguarding information assets.
by DEAPOOL
2.
Cyber Threats and VulnerabilitiesModern systems are increasingly interconnected, creating vulnerabilities that can be exploited by
malicious actors. Common threats include malware, phishing attacks, and data breaches.
1
Malware
2
Phishing
Malware can compromise systems, steal
Phishing attacks deceive users into
data, and disrupt operations. Malware can
revealing sensitive information by
spread rapidly through email attachments,
impersonating trusted entities. These
infected websites, and vulnerable software.
attacks often target personal data,
financial credentials, and confidential
information.
3
Data Breaches
4
Ransomware
Data breaches can result in the loss of
Ransomware encrypts a victim's files and
sensitive information, including customer
demands payment to restore access,
data, financial records, and intellectual
impacting business operations and
property.
potentially causing significant financial
losses.
3.
Data Protection and PrivacyData protection and privacy are essential for building trust with customers, complying with
regulations, and maintaining a strong reputation. Organizations must implement measures to
safeguard personal information, such as data encryption, access controls, and privacy policies.
Data Encryption
Access Controls
Data encryption transforms data into an
Access controls restrict access to data
unreadable format, making it inaccessible
based on user roles and permissions,
to unauthorized individuals. Strong
ensuring that only authorized individuals
encryption algorithms are crucial for
can view and modify sensitive information.
safeguarding sensitive information.
This principle of "least privilege" helps
minimize the risk of unauthorized access.
Privacy Policies
Privacy policies outline how organizations collect, use, and protect personal information.
Clear and concise privacy policies build trust with customers and demonstrate a
commitment to data protection.
4.
Access Control and Authentication MethodsAccess control methods restrict unauthorized access to sensitive information and systems. Secure authentication methods ensure
that only authorized users can access resources.
Multi-Factor Authentication
(MFA)
Role-Based Access Control
(RBAC)
Biometric Authentication
Biometric authentication uses unique
MFA adds an extra layer of security by
RBAC assigns users different roles with
biological traits, such as fingerprints,
requiring multiple forms of verification,
specific permissions, restricting access
facial recognition, or iris scanning, to
such as a password, a one-time code, or
to resources based on their
verify identity. This method offers a high
a biometric scan. This makes it
responsibilities. This ensures that users
level of security and convenience.
significantly harder for unauthorized
only have access to the information they
users to gain access to accounts and
need to perform their duties.
systems.
5.
Encryption and Cryptographic MethodsEncryption plays a crucial role in protecting sensitive information during transmission and storage.
Cryptographic methods use mathematical algorithms to transform data into an unreadable format,
making it secure from unauthorized access.
Symmetric-key Encryption
Symmetric-key encryption uses the same key for both encryption and decryption. This
method is fast and efficient but requires secure key management.
Asymmetric-key Encryption
Asymmetric-key encryption uses separate keys for encryption and decryption. This
method provides a higher level of security and is commonly used for digital signatures and
secure communications.
Hashing
Hashing algorithms convert data into a fixed-length string, ensuring data integrity and
authenticity. Hashing is commonly used for password storage and data verification.
6.
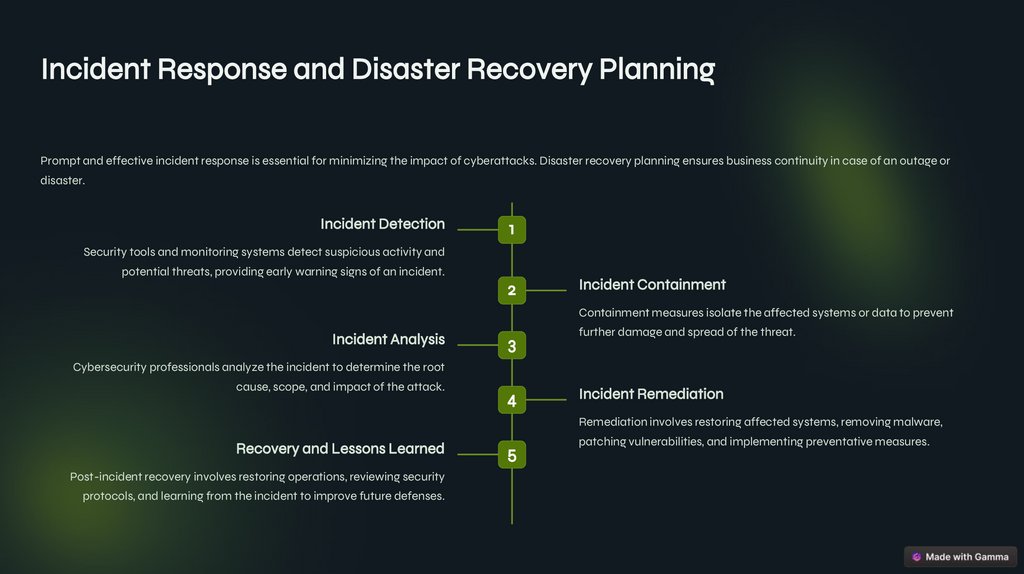
Incident Response and Disaster Recovery PlanningPrompt and effective incident response is essential for minimizing the impact of cyberattacks. Disaster recovery planning ensures business continuity in case of an outage or
disaster.
Incident Detection
1
Security tools and monitoring systems detect suspicious activity and
potential threats, providing early warning signs of an incident.
2
Incident Containment
Containment measures isolate the affected systems or data to prevent
Incident Analysis
3
further damage and spread of the threat.
Cybersecurity professionals analyze the incident to determine the root
cause, scope, and impact of the attack.
4
Incident Remediation
Remediation involves restoring affected systems, removing malware,
Recovery and Lessons Learned
Post-incident recovery involves restoring operations, reviewing security
protocols, and learning from the incident to improve future defenses.
5
patching vulnerabilities, and implementing preventative measures.
7.
Compliance with Regulations andIndustry Standards
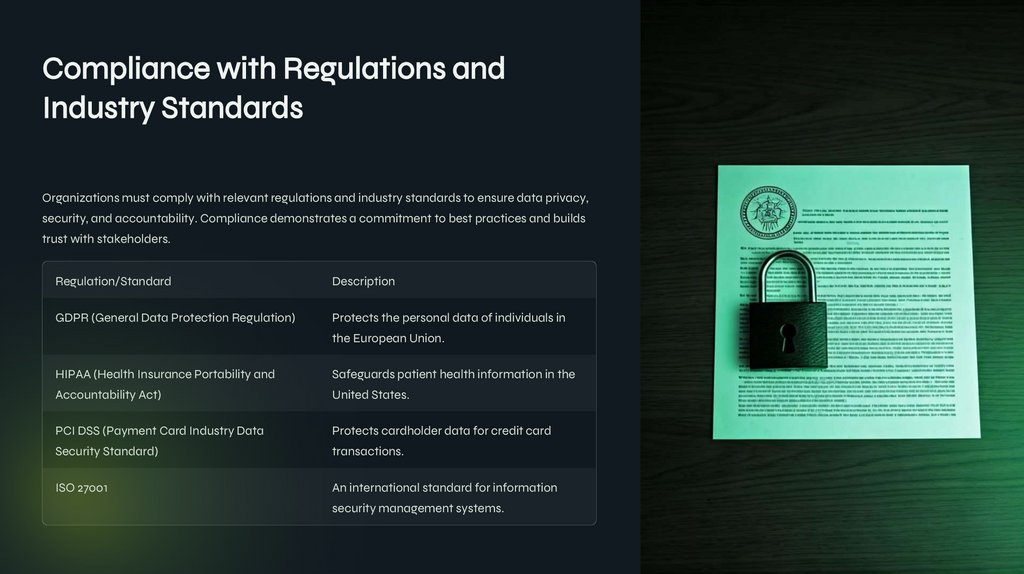
Organizations must comply with relevant regulations and industry standards to ensure data privacy,
security, and accountability. Compliance demonstrates a commitment to best practices and builds
trust with stakeholders.
Regulation/Standard
Description
GDPR (General Data Protection Regulation)
Protects the personal data of individuals in
the European Union.
HIPAA (Health Insurance Portability and
Safeguards patient health information in the
Accountability Act)
United States.
PCI DSS (Payment Card Industry Data
Protects cardholder data for credit card
Security Standard)
transactions.
ISO 27001
An international standard for information
security management systems.
8.
Conclusion and Best PracticesProactive information security practices are crucial for protecting sensitive data, systems, and networks
in today's digital landscape. Staying informed about emerging threats, implementing strong security
measures, and fostering a culture of cybersecurity awareness are essential for minimizing risks and
ensuring data integrity.
Strong Passwords
Two-Factor Authentication
Use complex and unique passwords for each
account, and avoid reusing passwords across
Enable two-factor authentication whenever
different platforms.
possible to add an extra layer of security to your
accounts.
Be Cautious of Phishing
Keep Software Updated
Be wary of suspicious emails, links, and messages
Regularly update your software and operating
that request sensitive information.
systems to patch vulnerabilities and stay
protected.






 Интернет
Интернет








