Похожие презентации:
Threat Intelligence
1. Threat Intelligence
ThreatIntellige
nce
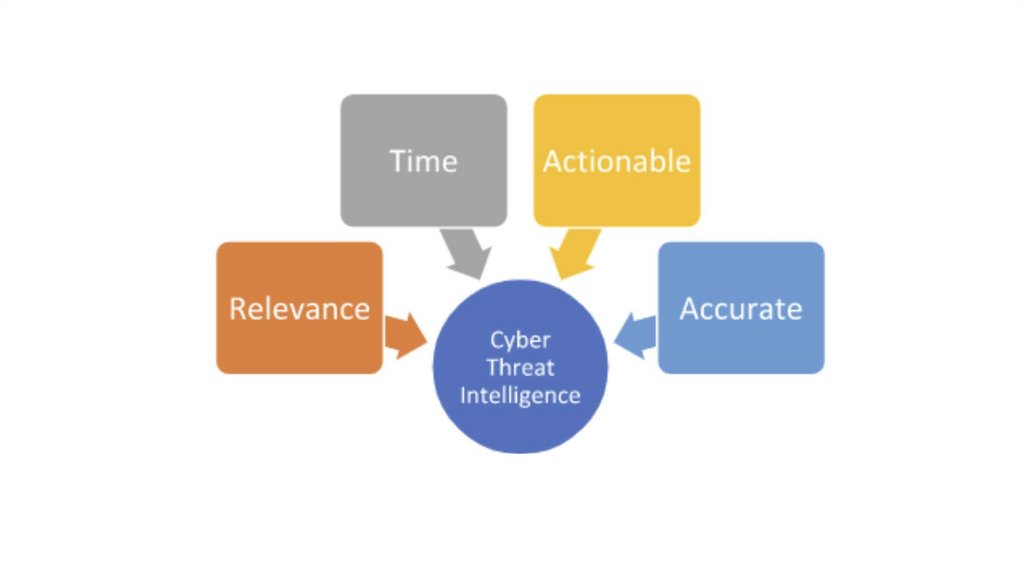
2. Gartner definition for threat intelligence
• Threat intelligence is evidence-basedknowledge, including context, mechanisms,
indicators, implications and actionable
advice, about an existing or emerging
menace or hazard to assets that can be
used to inform decisions regarding the
subject’s response to that menace or
hazard.
3.
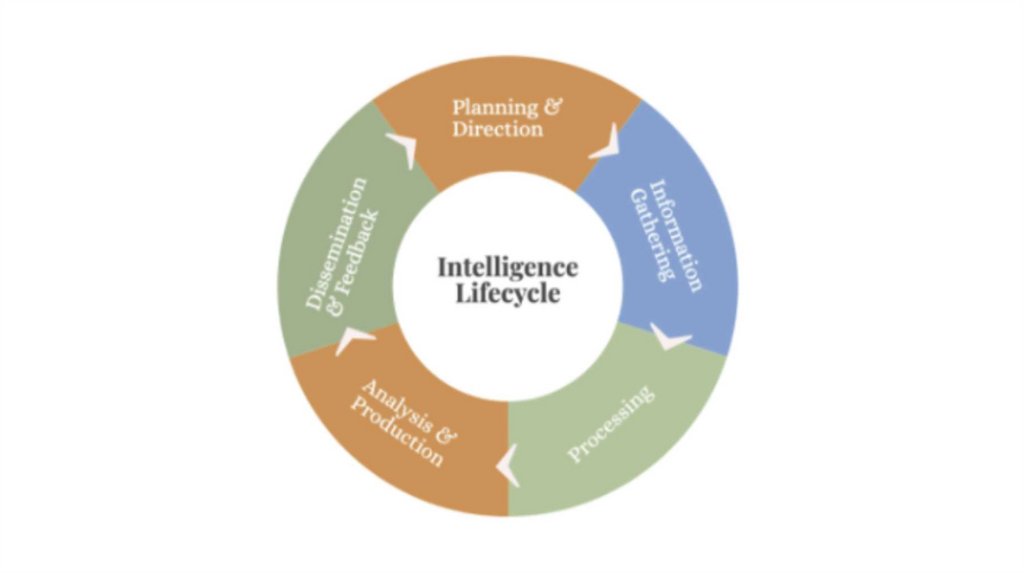
4. Information Gathering
Information
Gatherin
g
5.
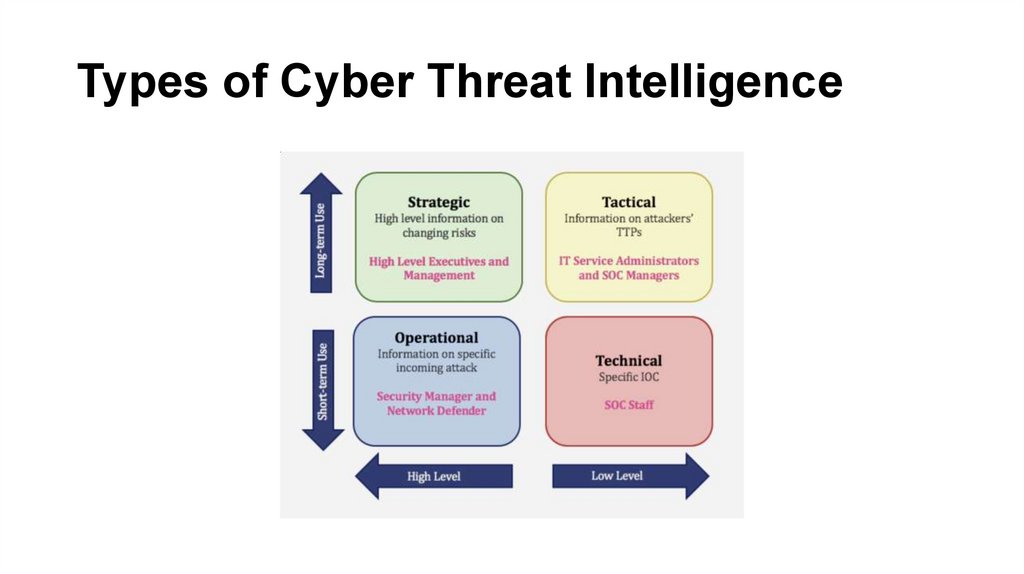
6. Types of Cyber Threat Intelligence
Types of Cyber Threat Intelligence7.
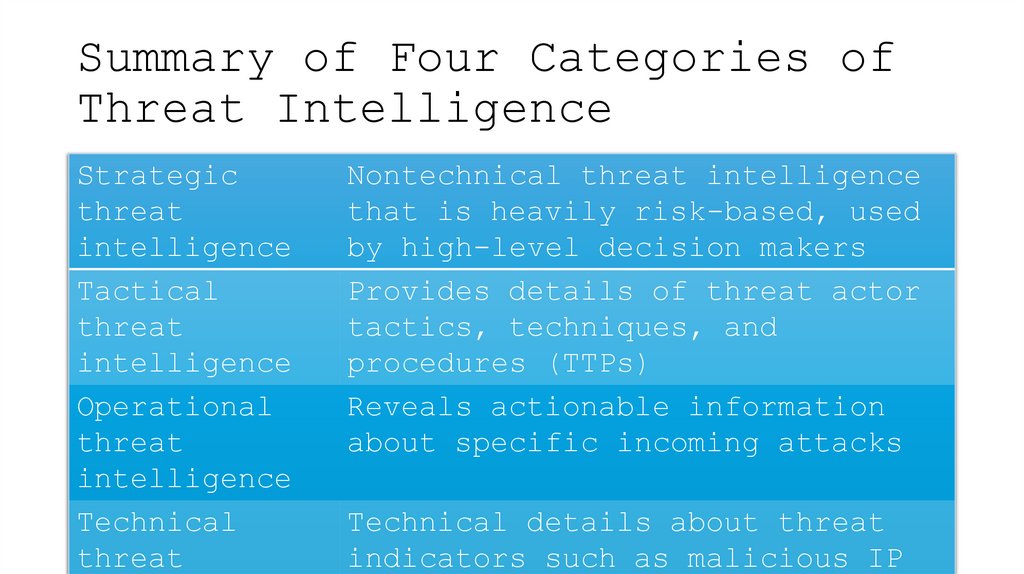
8. Summary of Four Categories of Threat Intelligence
Strategicthreat
intelligence
Tactical
threat
intelligence
Operational
threat
intelligence
Technical
threat
Nontechnical threat intelligence
that is heavily risk-based, used
by high-level decision makers
Provides details of threat actor
tactics, techniques, and
procedures (TTPs)
Reveals actionable information
about specific incoming attacks
Technical details about threat
indicators such as malicious IP
9. Strategic Threat Intelligence
Strategic Threat
Intellig
ence
10. Data Expectations for Strategic Threat Intelligence
DataExpectat
ions for
Strategi
c Threat
Intellig
ence
11. Tactical Threat Intelligence
TacticalThreat
Intellig
ence
12. Data Expectations for Tactical Threat Intelligence
DataExpectat
ions for
Tactical
Threat
Intellig
ence
13. Operational Threat Intelligence
Operational
Threat
Intellig
ence
14. Data Expectations for Operational Threat Intelligence
DataExpectat
ions for
Operatio
nal
Threat
Intellig
ence
15. Technical Threat Intelligence
Technical Threat
Intellig
ence
16. Data Expectations for Technical Threat Intelligence
DataExpectat
ions for
Technica
l Threat
Intellig
ence
17. Threat Intelligence Context
ThreatIntellig
ence
Context
18. Threat Context
ThreatContex
t
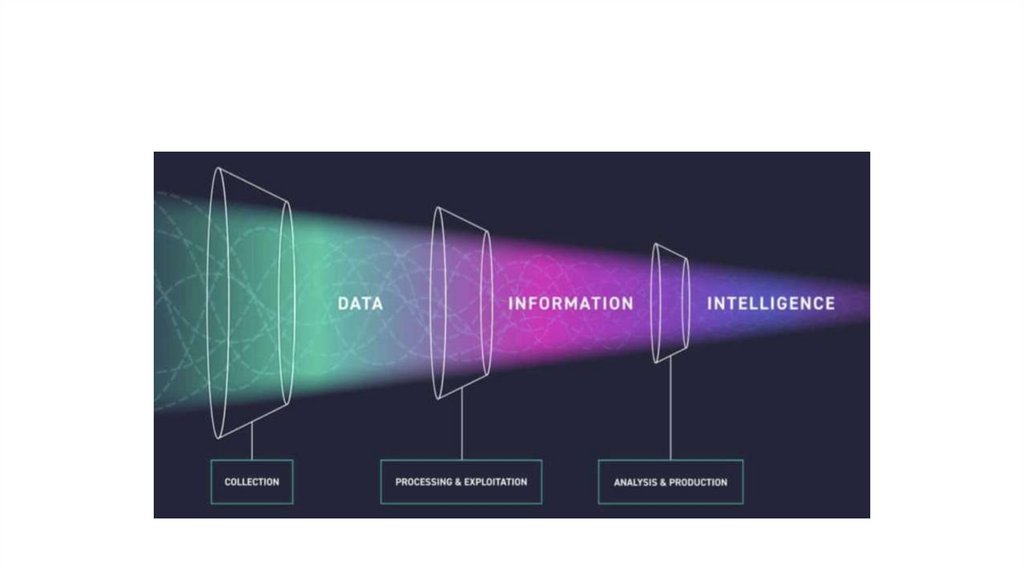
19. Collecting and Processing Intelligence
Collectingand
Processing
Intelligenc
e
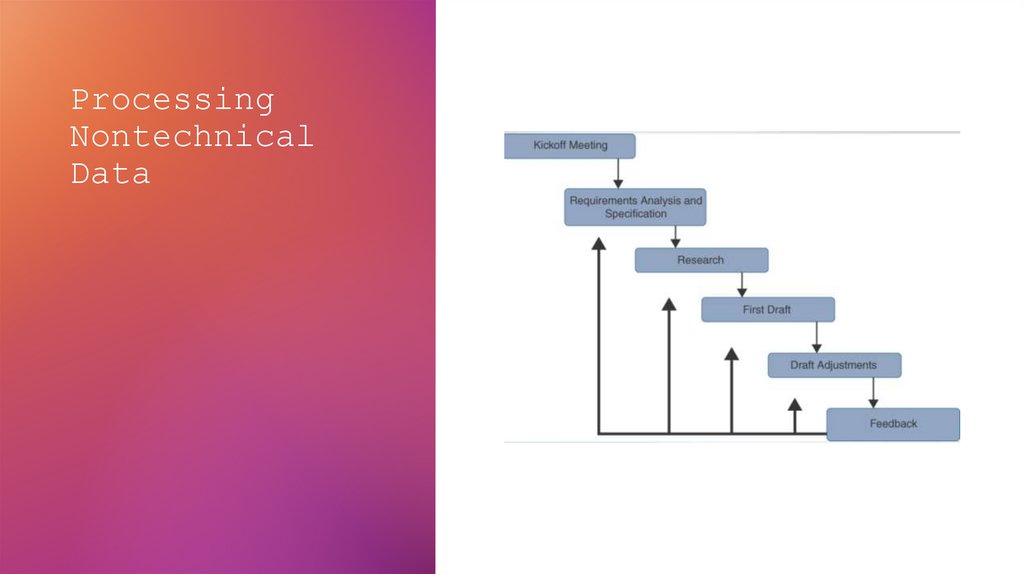
20. Processing Nontechnical Data
21. The process will work as follow:
The kickoff meeting for this project would lay out the
scope of the type of data that is needed for the CEO,
including where the datacenter could be created, what
type of systems could be used, and the type of data
that could be seen within the datacenter.
The analyst would first validate each of these items to
ensure that the analyst’s understanding of the request
is clear before research is performed.
While researching the requested items, the analyst will
collect a lot of data; however, only certain topics
would be useful to the C-level exec, while other
content would not help the C-level exec with upcoming
decisions about the datacenter.
The analyst would present a general review of the type
of data available and confirm which data resources are
valuable before proceeding with a draft.
Once the draft is complete, another checkpoint would
occur to ensure that all topics needed by the C-level
exec are being addressed.
A few more checkpoints might occur as the draft is
converted into a final report, allowing for adjustments
as the research and data are prepared for the C-level
exec. These checkpoints allow for continuous tuning to
the research and writing process, reducing the risk of
the analyst including too much noise or not capturing
what is required for the final report to be useful.
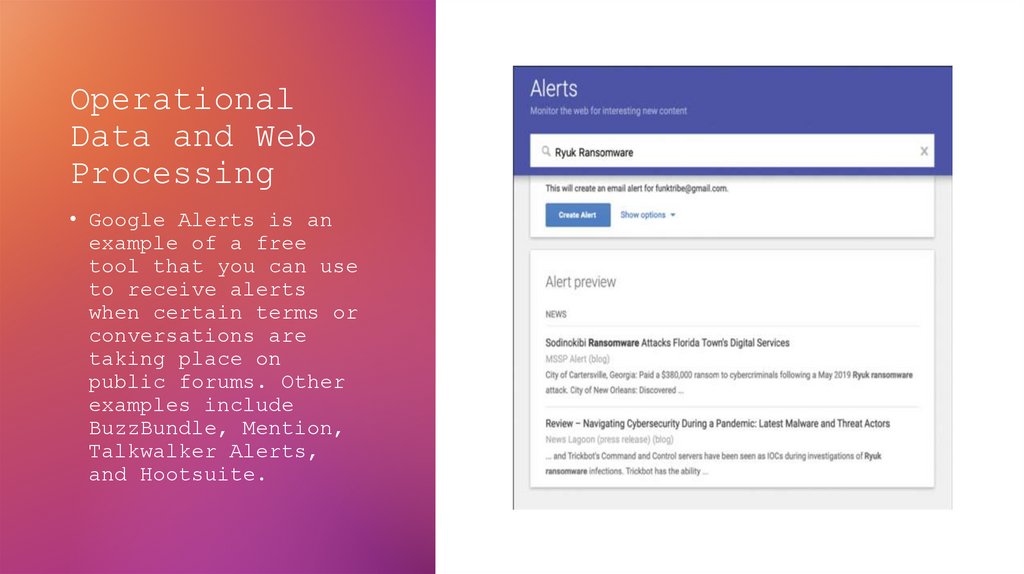
22. Operational Data and Web Processing
• Google Alerts is anexample of a free
tool that you can use
to receive alerts
when certain terms or
conversations are
taking place on
public forums. Other
examples include
BuzzBundle, Mention,
Talkwalker Alerts,
and Hootsuite.
23. Technical Processing
Technical
Processi
ng
24. STIX
25. Technical Threat Intelligence Resources
Technical Threat
Intellig
ence
Resource
s
26. Technical Threat Intelligence Resources
Technical Threat
Intellig
ence
Resource
s
27. Actionable Intelligence
Actionable
Intellig
ence
28. Security Tools and Threat Intelligence
SecurityTools
and
Threat
Intellig
ence
29. Security Information and Event Management
SecurityInformati
on and
Event
Managemen
t
30. Security Orchestration, Automation, and Response
SecurityOrchestrat
ion,
Automation
, and
Response
31. Email Security
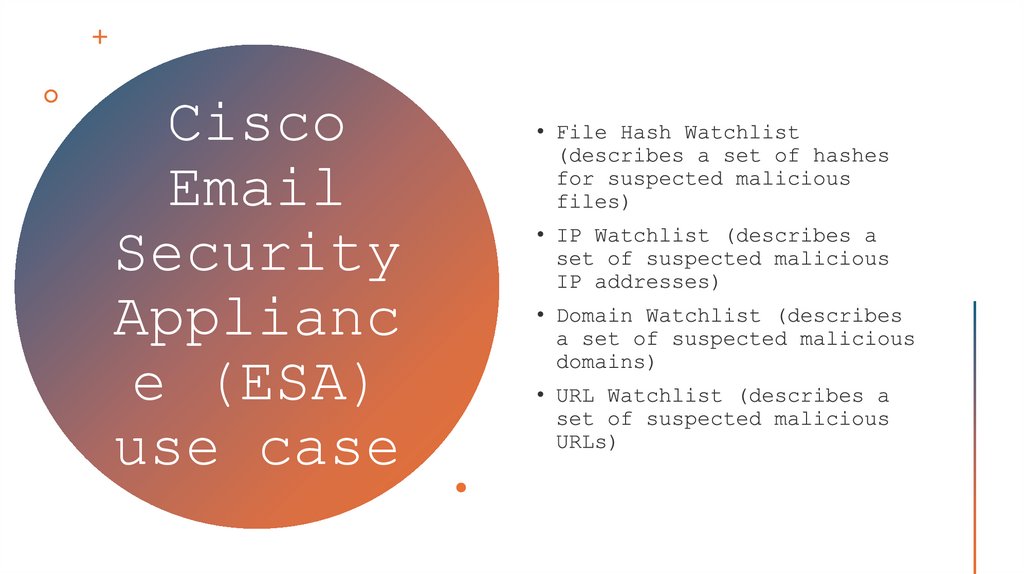
32. Cisco Email Security Appliance (ESA) use case
CiscoSecurity
Applianc
e (ESA)
use case























 Информатика
Информатика








