Похожие презентации:
Интенсив про эксперимент
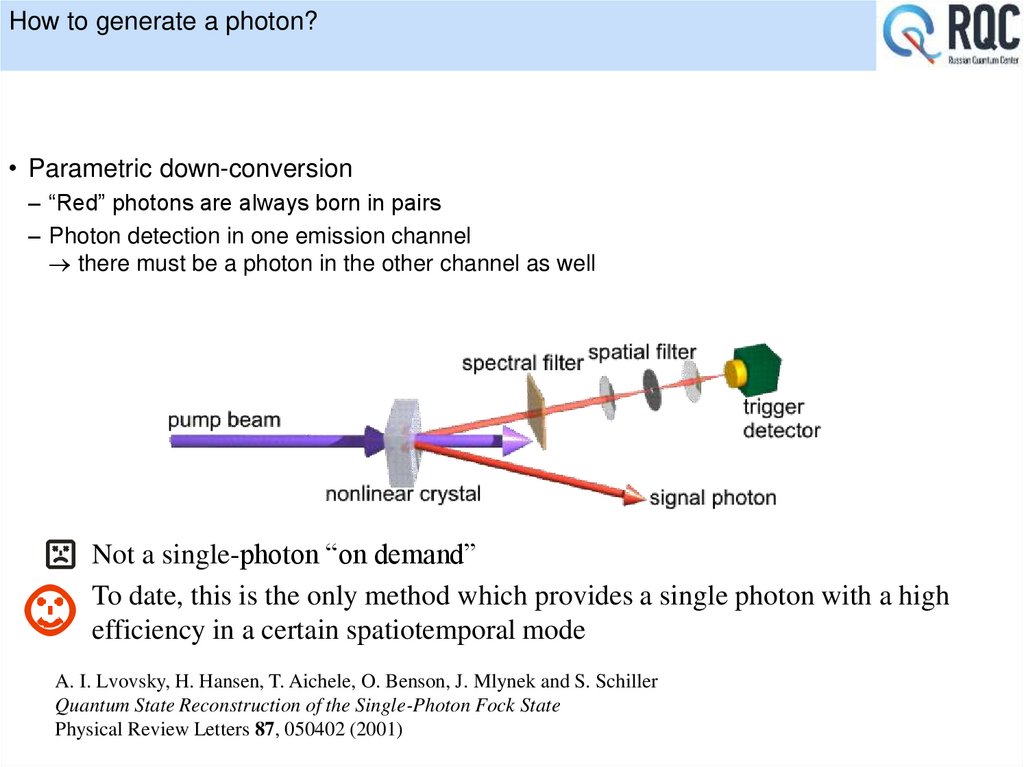
1. A single photon application: quantum cryptography
RQC 20162. Оглавление
• Introduction• Quantum cryptography idea
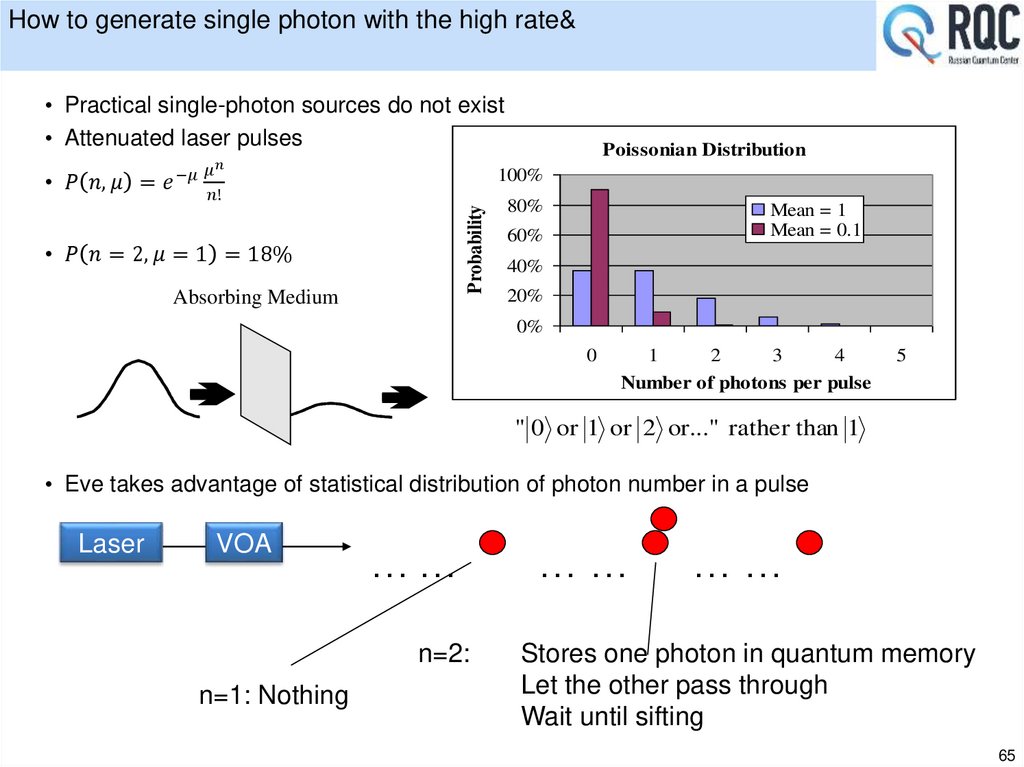
• Quantum key distribution experiments
• Single photon detectors
• QKD threats
• Quantum key applications
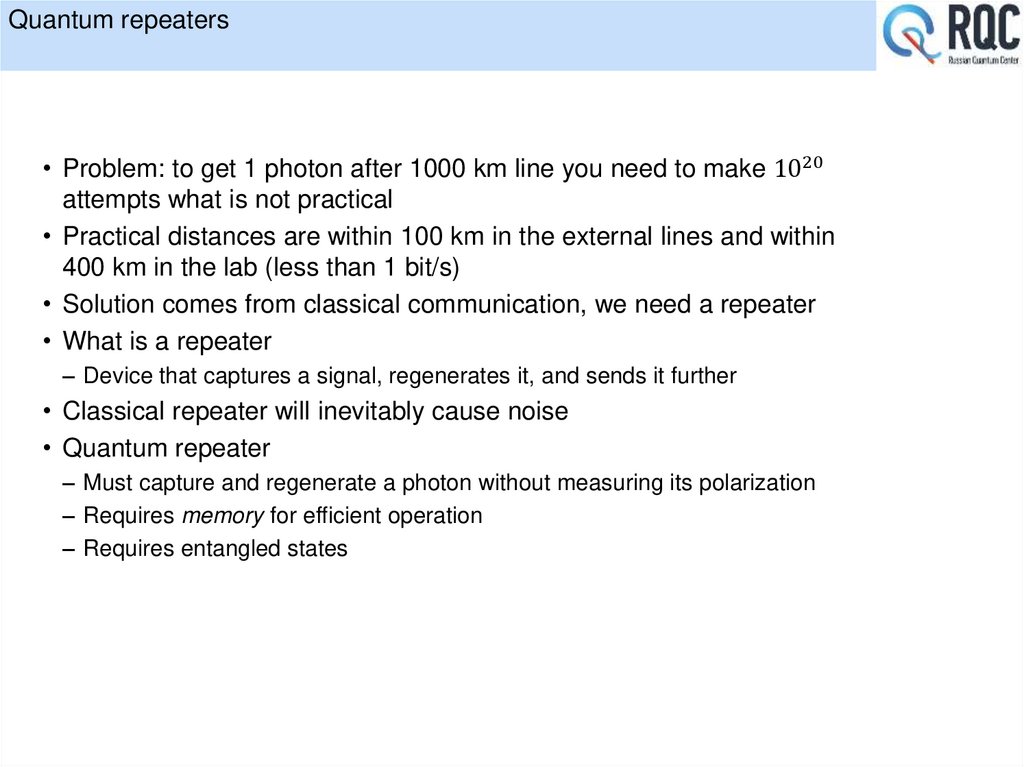
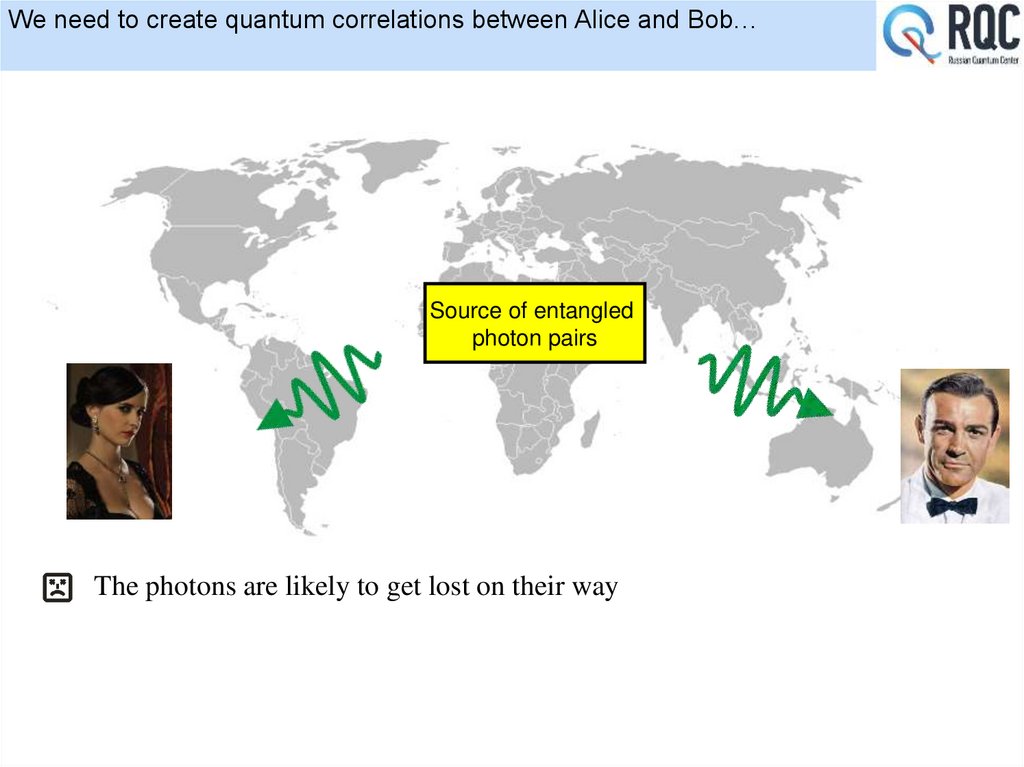
• Quantum repeaters
• Space QKD
2
3.
• Introduction3
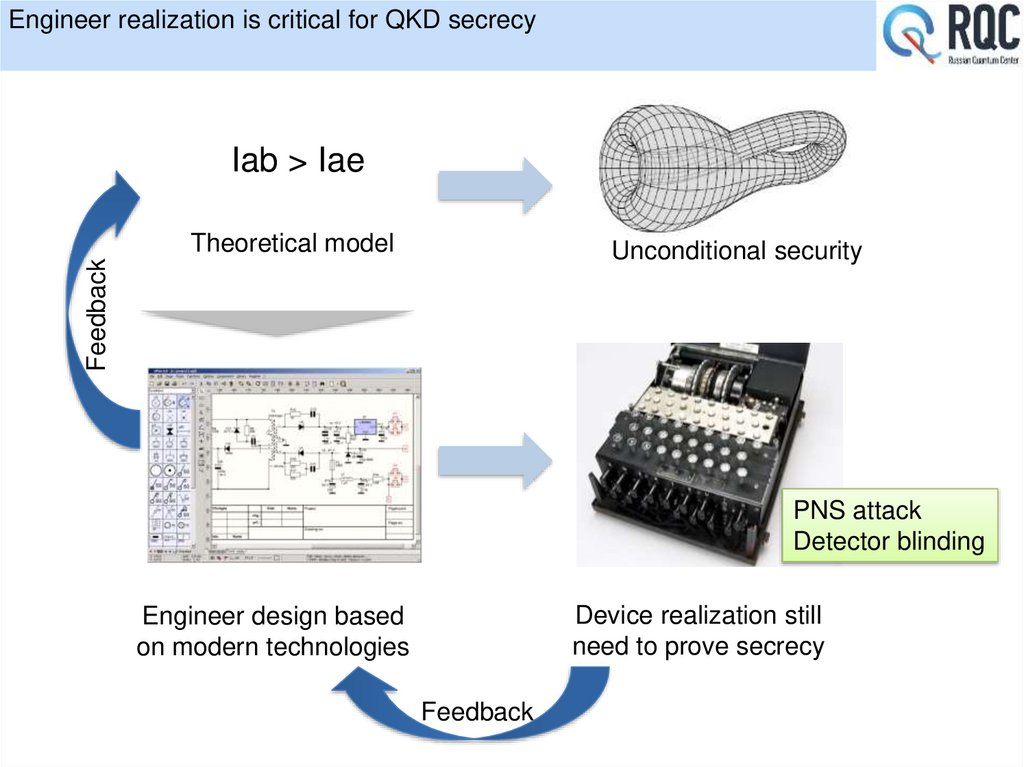
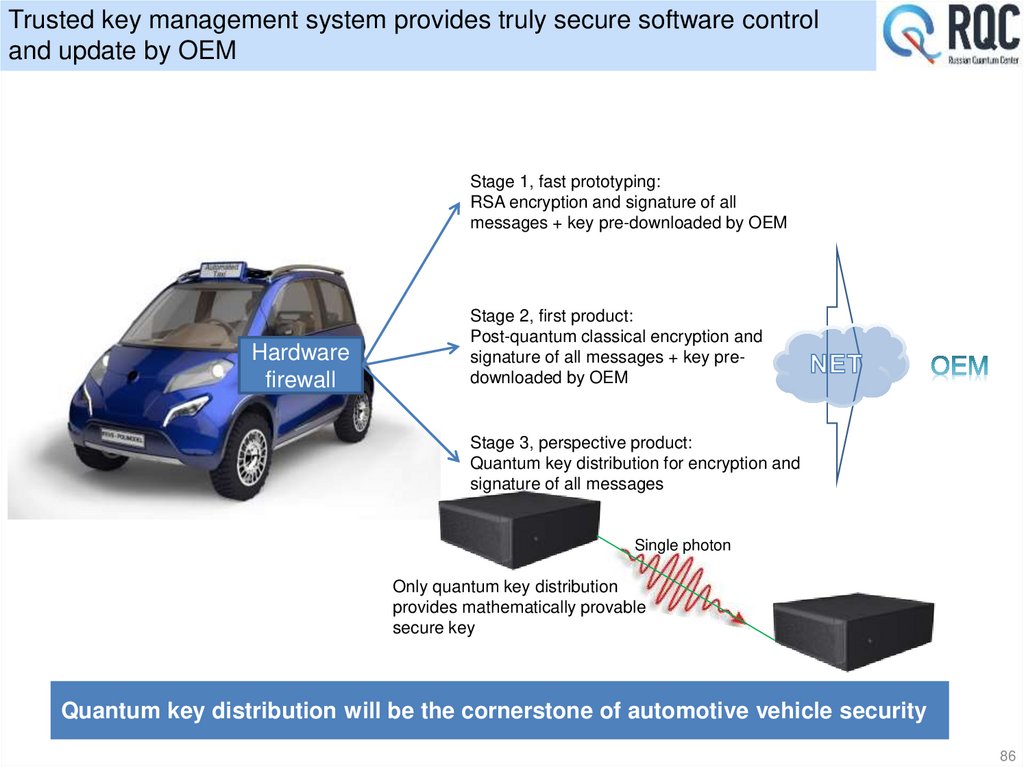
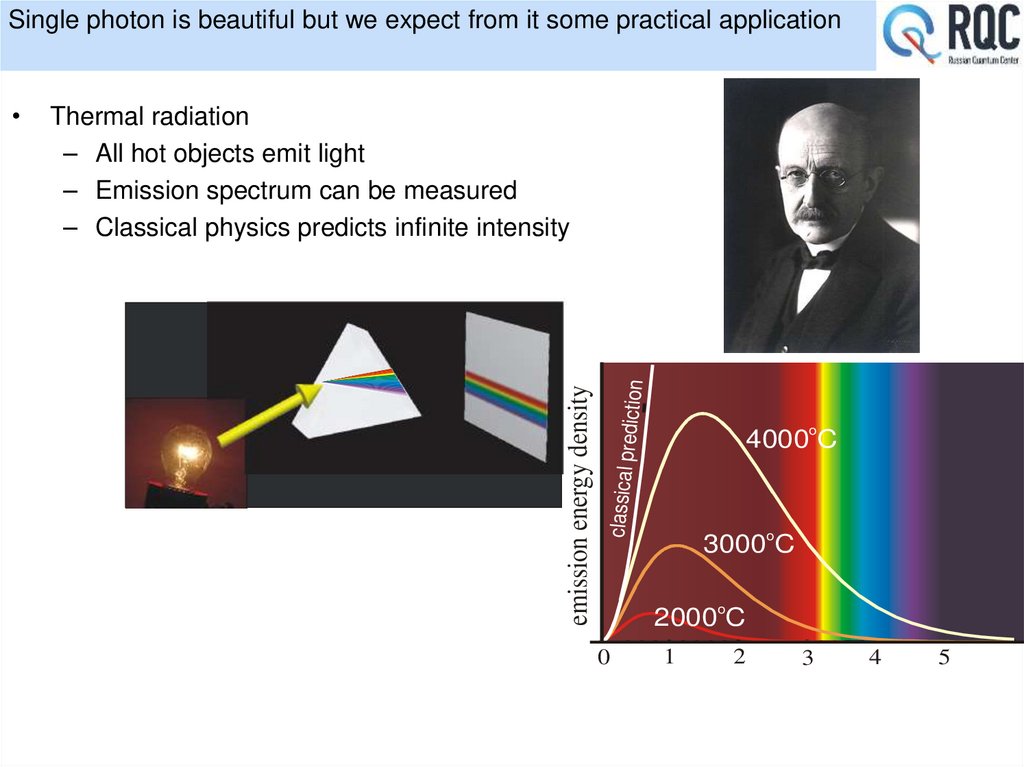
4. Single photon is beautiful but we expect from it some practical application
classical prediction
Thermal radiation
– All hot objects emit light
– Emission spectrum can be measured
– Classical physics predicts infinite intensity
emission energy density
o
4000 C
3000oC
2000oC
0
1
2
3
4
5
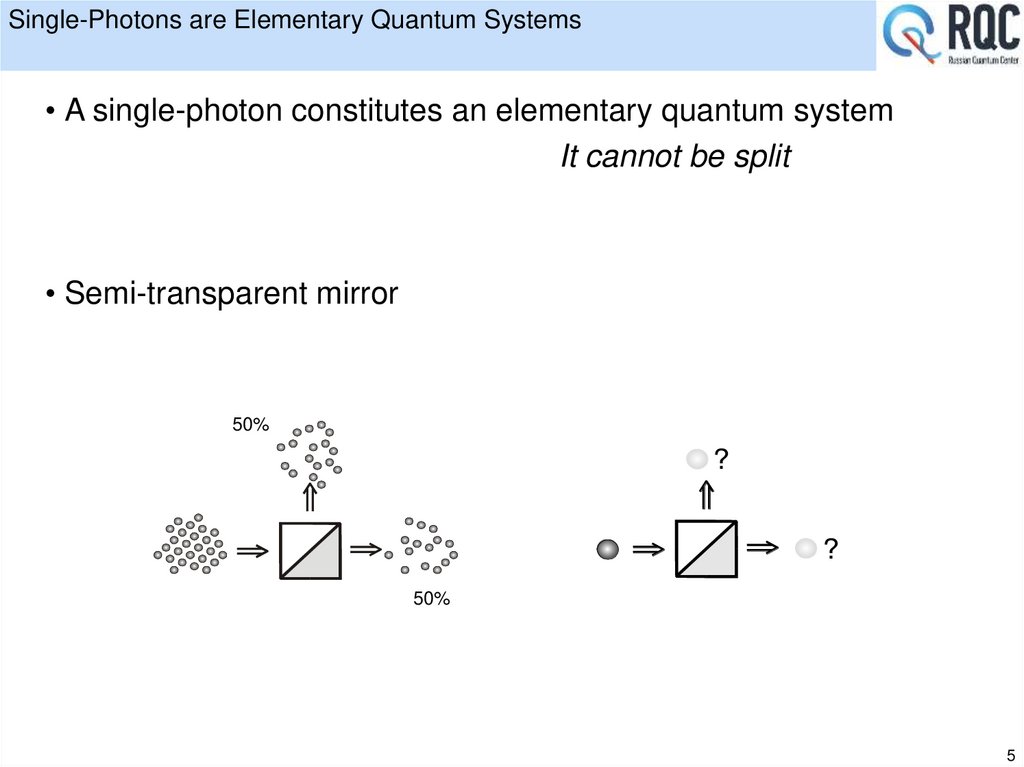
5. Single-Photons are Elementary Quantum Systems
• A single-photon constitutes an elementary quantum systemIt cannot be split
• Semi-transparent mirror
50%
?
?
50%
5
6. The “bomb” paradox [A. Elitzur and L. Vaidman (1993)]
• Mach-Zehnder interferometer tuned to get all signal on AA
B
• If we move to single photon signal all clicks will still be on A
7. The “bomb” paradox [A. Elitzur and L. Vaidman (1993)]
• Mach-Zehnder interferometer tuned to get all signal on AA
B
• If cut one arm the signal will be split 50/50
?
• Single photon will click random detector
?
8. The “bomb” paradox [A. Elitzur and L. Vaidman (1993)]
• Interaction-free weapons inspection– Insert a single-photon sensitive bomb into one of the interferometer arms
A
B
• Bomb absent
interference observed: all photons emerge at A
• Bomb present
no interference: photons emerge at A or B
bomb may or may not explode
• Photon detected at B (probability = 1/4)
bomb is present
bomb has been detected without any interaction!
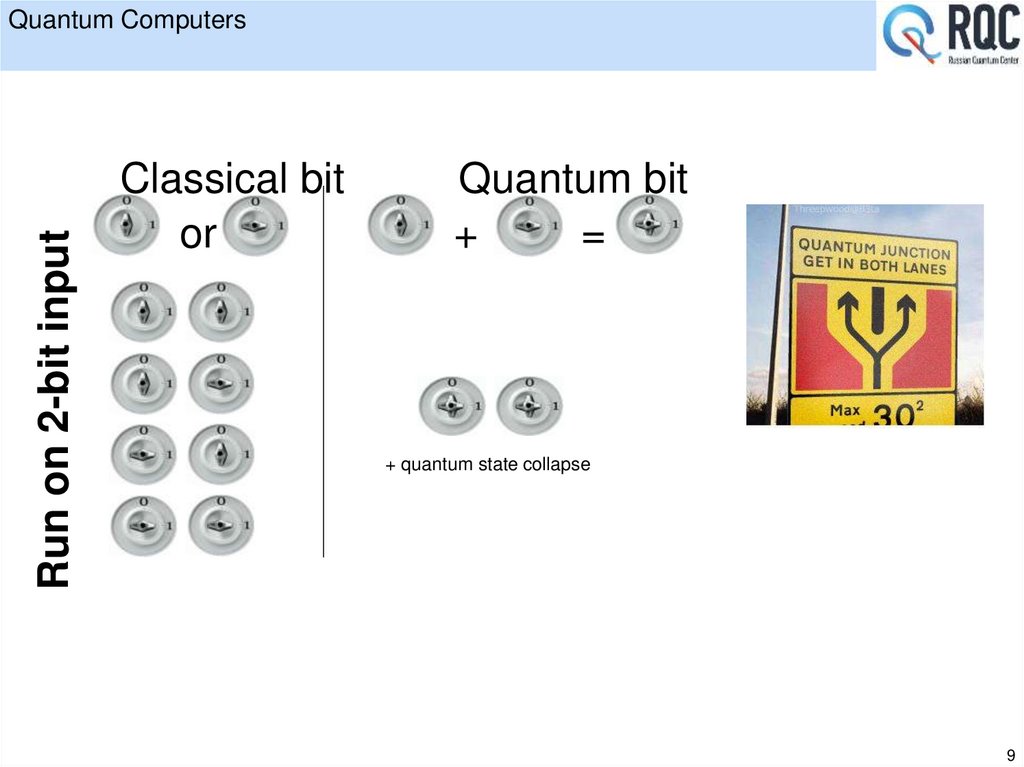
9. Quantum Computers
Run on 2-bit inputQuantum Computers
Classical bit
or
Quantum bit
+
=
+ quantum state collapse
9
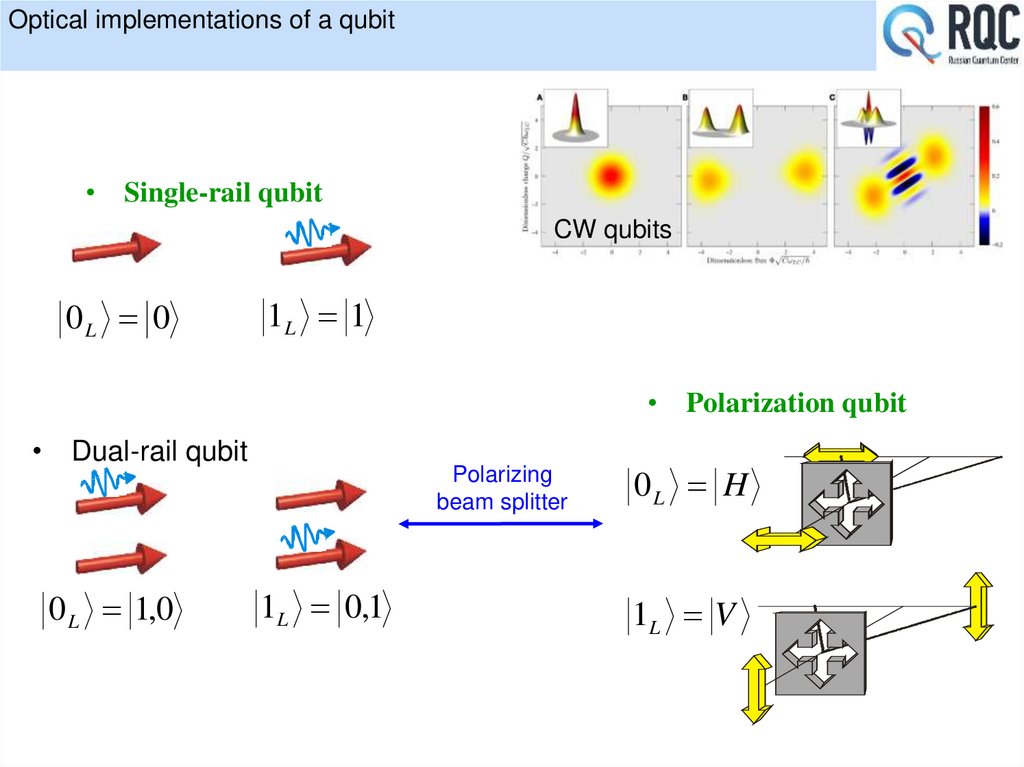
10. Optical implementations of a qubit
• Single-rail qubitCW qubits
0L 0
1L 1
• Polarization qubit
• Dual-rail qubit
0 L 1,0
Polarizing
beam splitter
1L 0,1
0L H
1L V
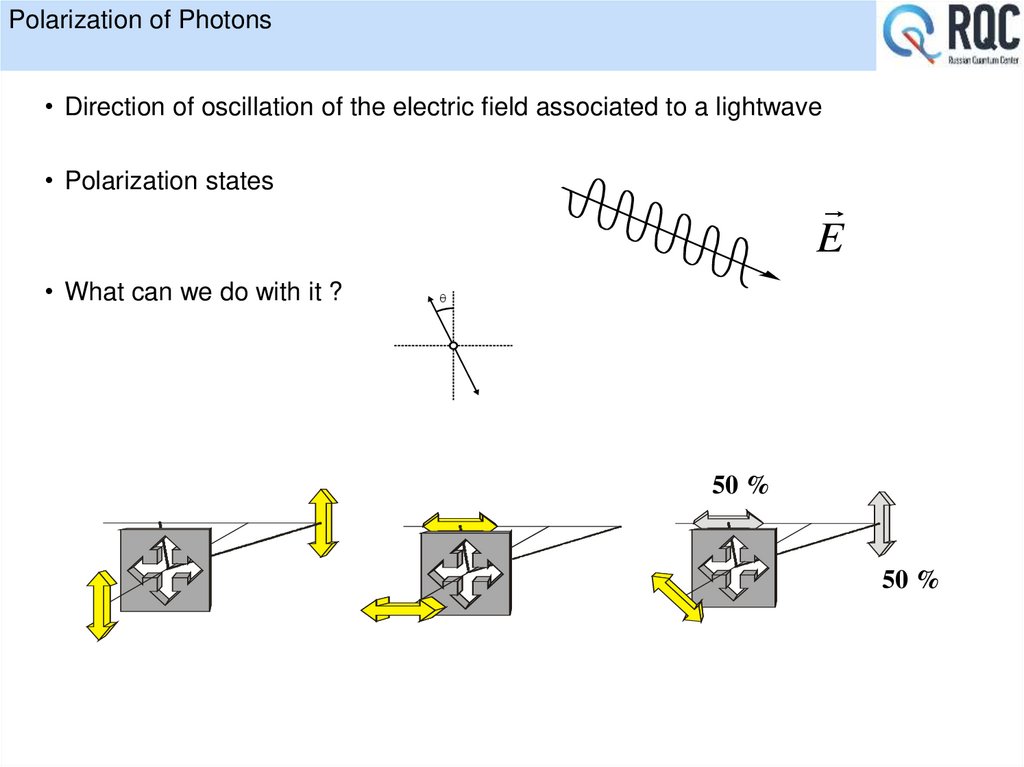
11. Polarization of Photons
• Direction of oscillation of the electric field associated to a lightwave• Polarization states
• What can we do with it ?
E
50 %
50 %
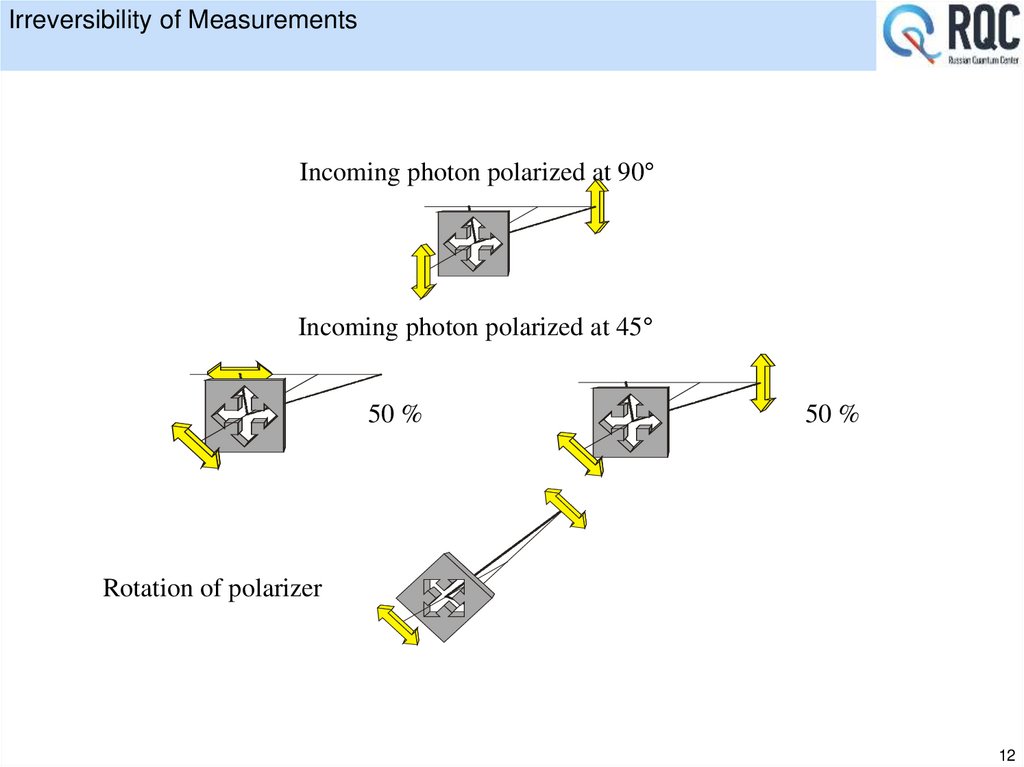
12. Irreversibility of Measurements
Incoming photon polarized at 90Incoming photon polarized at 45
50 %
50 %
Rotation of polarizer
12
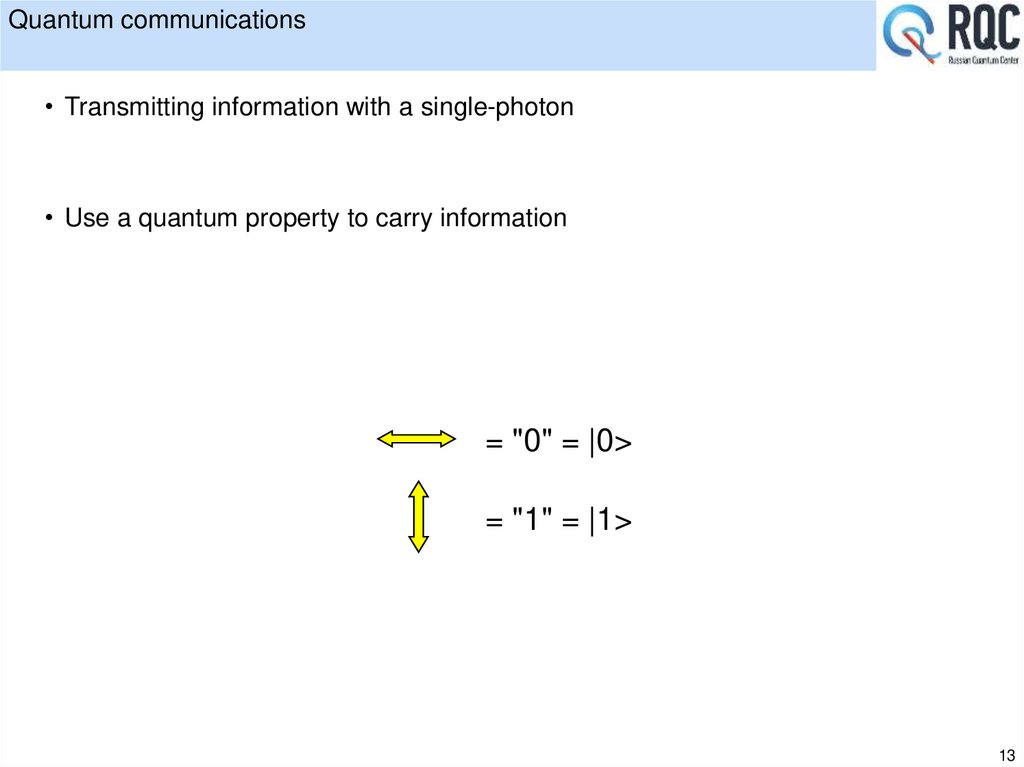
13. Quantum communications
• Transmitting information with a single-photon• Use a quantum property to carry information
Liner States
= "0" = |0>
= "1" = |1>
13
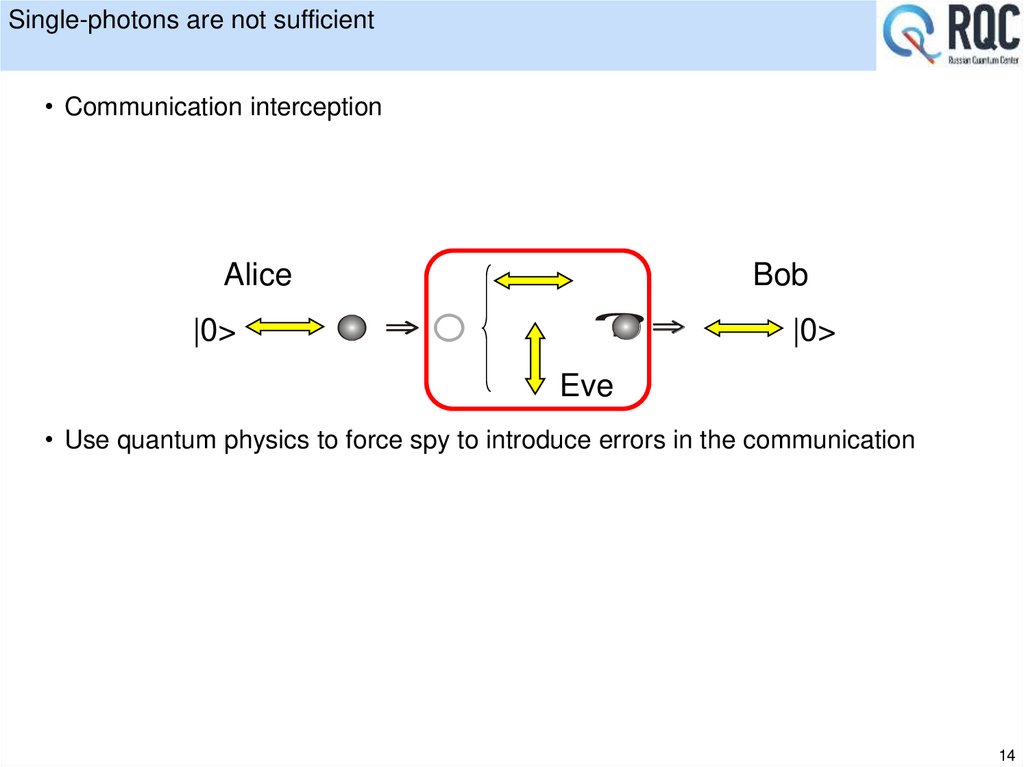
14. Single-photons are not sufficient
• Communication interceptionAlice
|0>
Bob
?
|0>
Eve
• Use quantum physics to force spy to introduce errors in the communication
14
15.
• Quantum cryptography idea15
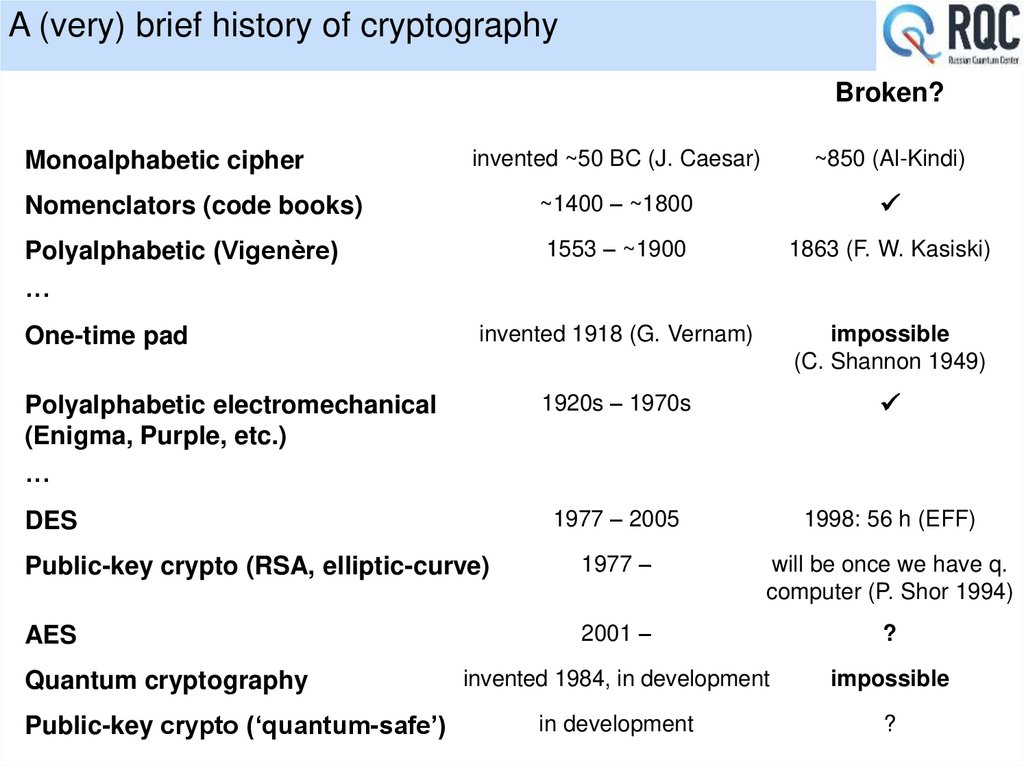
16. A (very) brief history of cryptography
Broken?invented ~50 BC (J. Caesar)
~850 (Al-Kindi)
Nomenclators (code books)
~1400 – ~1800
Polyalphabetic (Vigenère)
1553 – ~1900
1863 (F. W. Kasiski)
invented 1918 (G. Vernam)
impossible
(C. Shannon 1949)
1920s – 1970s
1977 – 2005
1998: 56 h (EFF)
Public-key crypto (RSA, elliptic-curve)
1977 –
will be once we have q.
computer (P. Shor 1994)
AES
2001 –
?
invented 1984, in development
impossible
in development
?
Monoalphabetic cipher
···
One-time pad
Polyalphabetic electromechanical
(Enigma, Purple, etc.)
···
DES
Quantum cryptography
Public-key crypto (‘quantum-safe’)
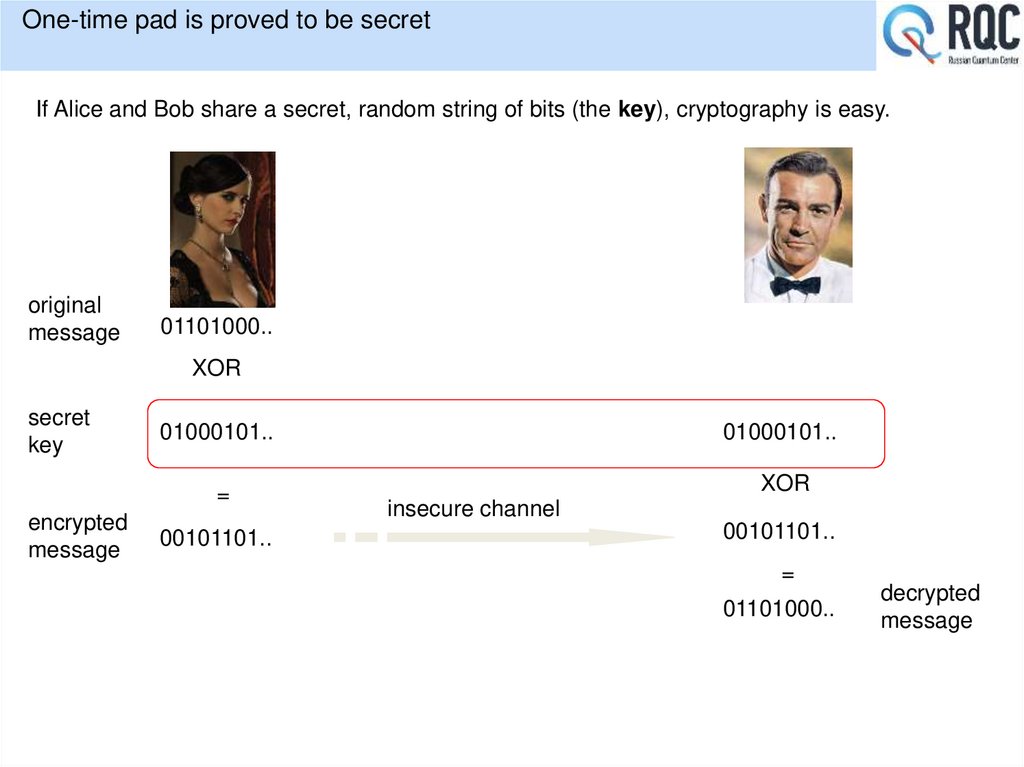
17. One-time pad is proved to be secret
If Alice and Bob share a secret, random string of bits (the key), cryptography is easy.original
message
01101000..
XOR
secret
key
encrypted
message
01000101..
01000101..
=
XOR
00101101..
insecure channel
00101101..
=
01101000..
decrypted
message
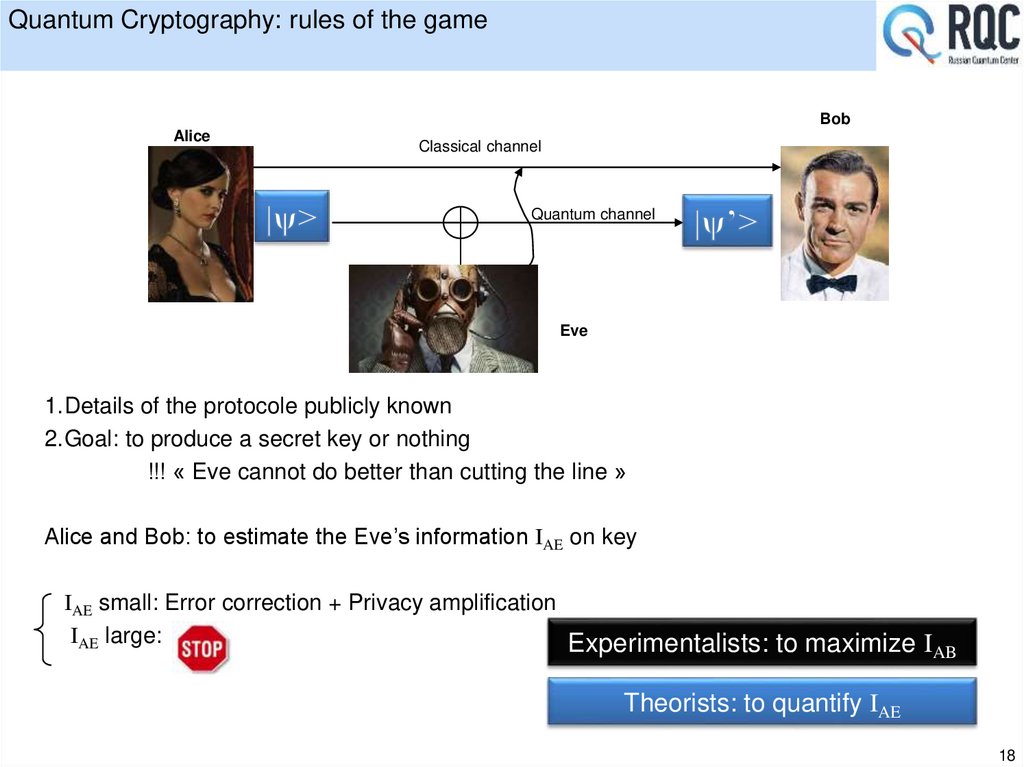
18. Quantum Cryptography: rules of the game
BobAlice
Classical channel
Quantum channel
Eve
1.Details of the protocole publicly known
2.Goal: to produce a secret key or nothing
!!! « Eve cannot do better than cutting the line »
Alice and Bob: to estimate the Eve’s information IAE on key
IAE small: Error correction + Privacy amplification
IAE large:
Experimentalists: to maximize I
AB
Theorists: to quantify IAE
18
19.
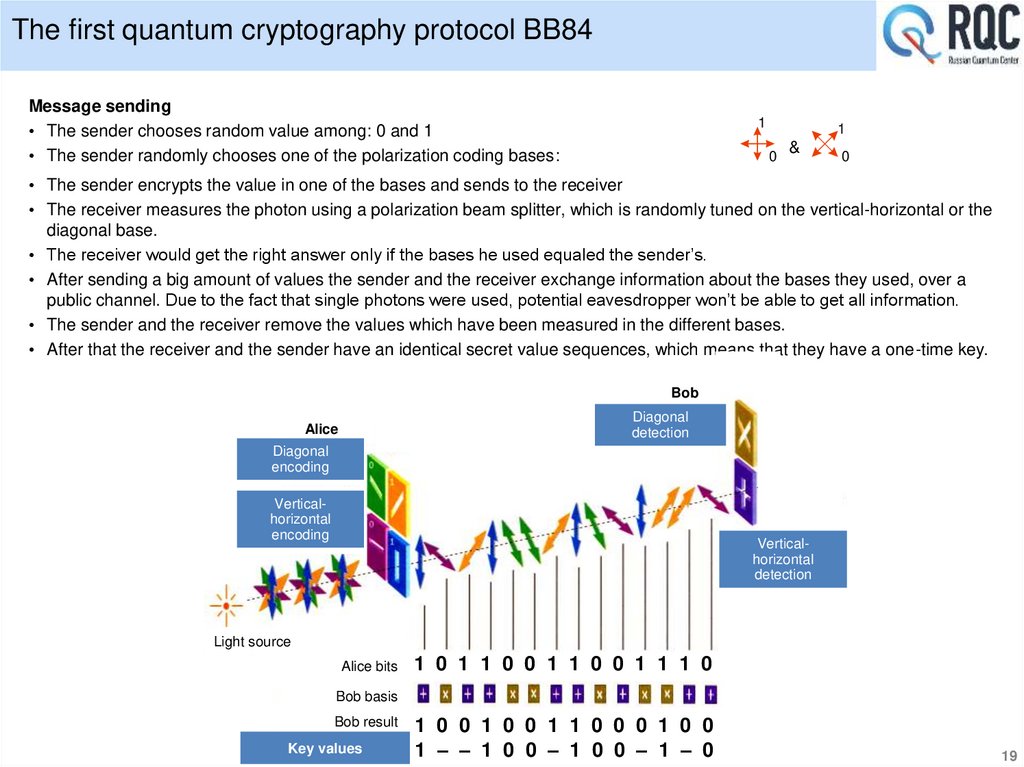
The first quantum cryptography protocol BB84Message sending
• The sender chooses random value among: 0 and 1
• The sender randomly chooses one of the polarization coding bases:
1
1
0
&
0
• The sender encrypts the value in one of the bases and sends to the receiver
• The receiver measures the photon using a polarization beam splitter, which is randomly tuned on the vertical-horizontal or the
diagonal base.
The receiver would get the right answer only if the bases he used equaled the sender’s.
After sending a big amount of values the sender and the receiver exchange information about the bases they used, over a
public channel. Due to the fact that single photons were used, potential eavesdropper won’t be able to get all information.
The sender and the receiver remove the values which have been measured in the different bases.
After that the receiver and the sender have an identical secret value sequences, which means that they have a one-time key.
Bob
Diagonal
detection
Alice
Diagonal
encoding
Verticalhorizontal
encoding
Verticalhorizontal
detection
Light source
Alice bits
1 0 1 1 0 0 1 1 0 0 1 1 1 0
Bob basis
Bob result
Key values
1 0 0 1 0 0 1 1 0 0 0 1 0 0
1 – – 1 0 0 – 1 0 0 – 1 – 0
19
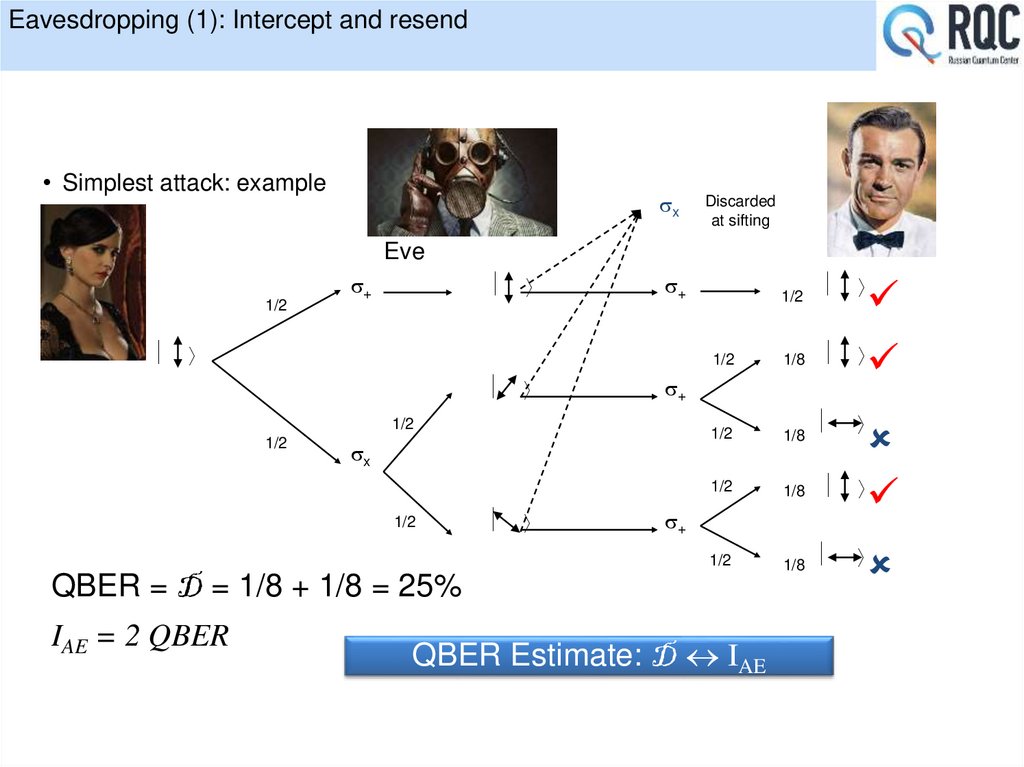
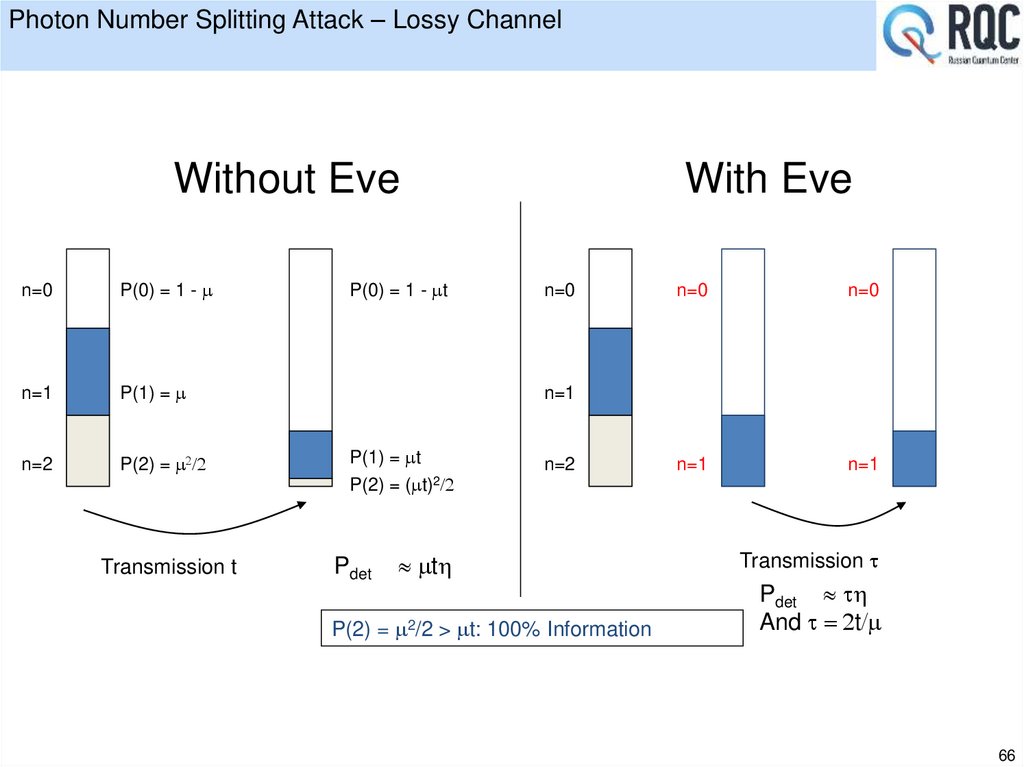
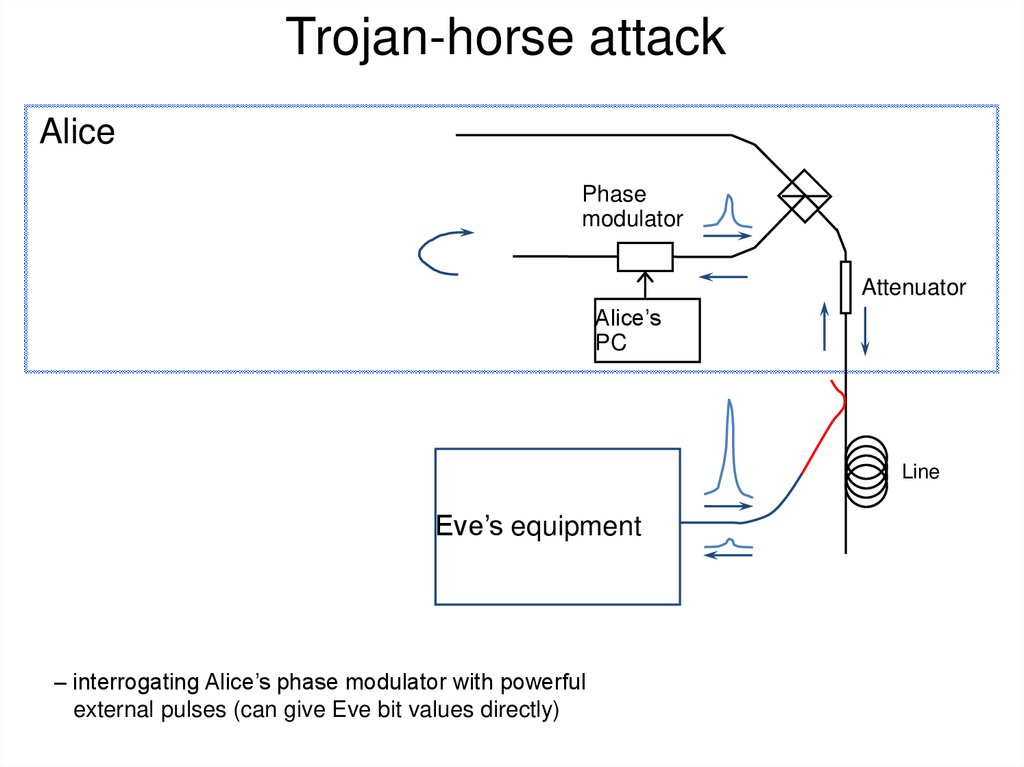
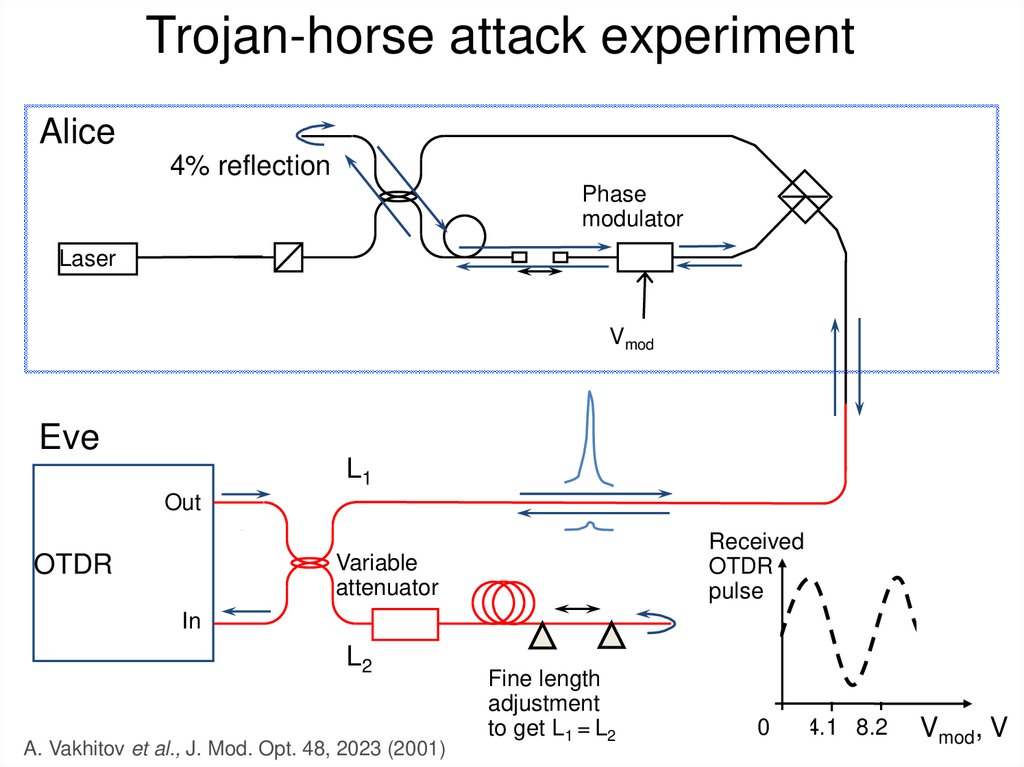
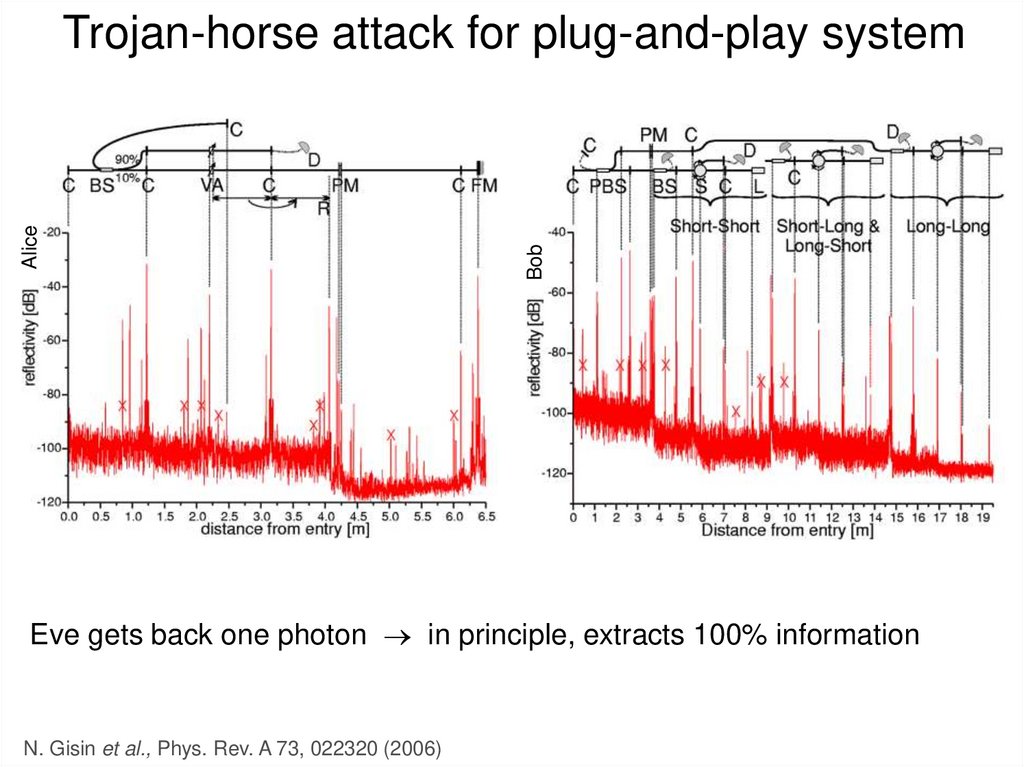
20. Eavesdropping (1): Intercept and resend
• Simplest attack: examplesx
Discarded
at sifting
Eve
1/2
s+
s+
sx
1/2
1/2
1/8
1/2
1/8
1/2
1/8
1/2
1/8
s+
1/2
1/2
1/2
s+
QBER = D = 1/8 + 1/8 = 25%
IAE = 2 QBER
QBER Estimate: D IAE
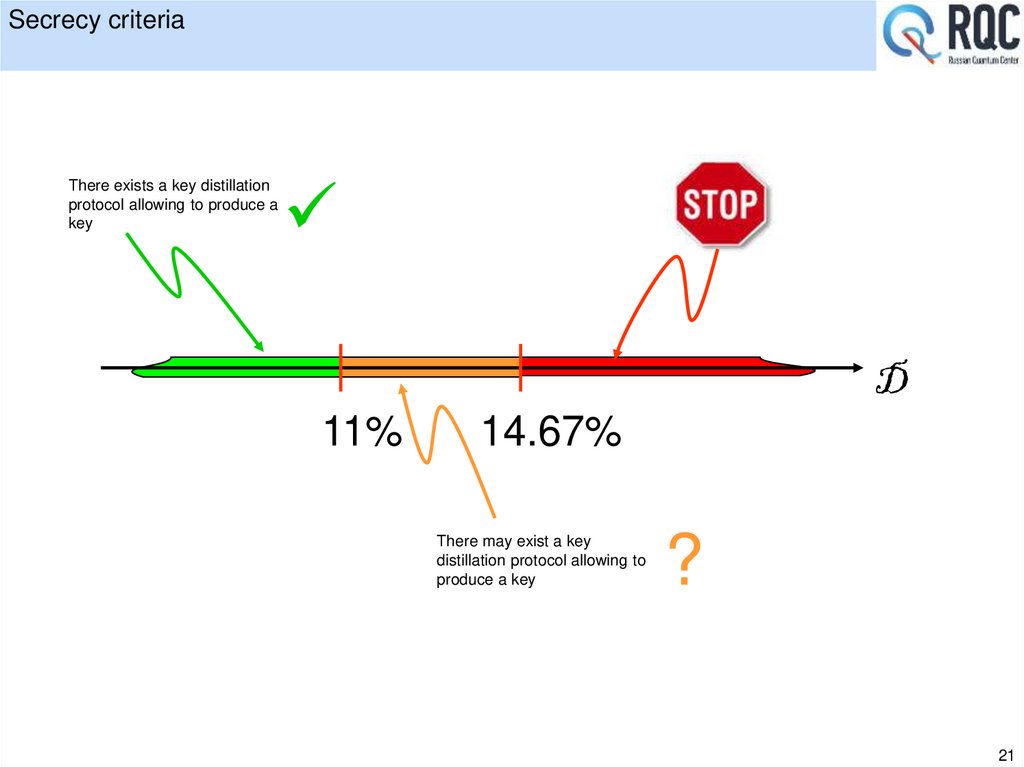
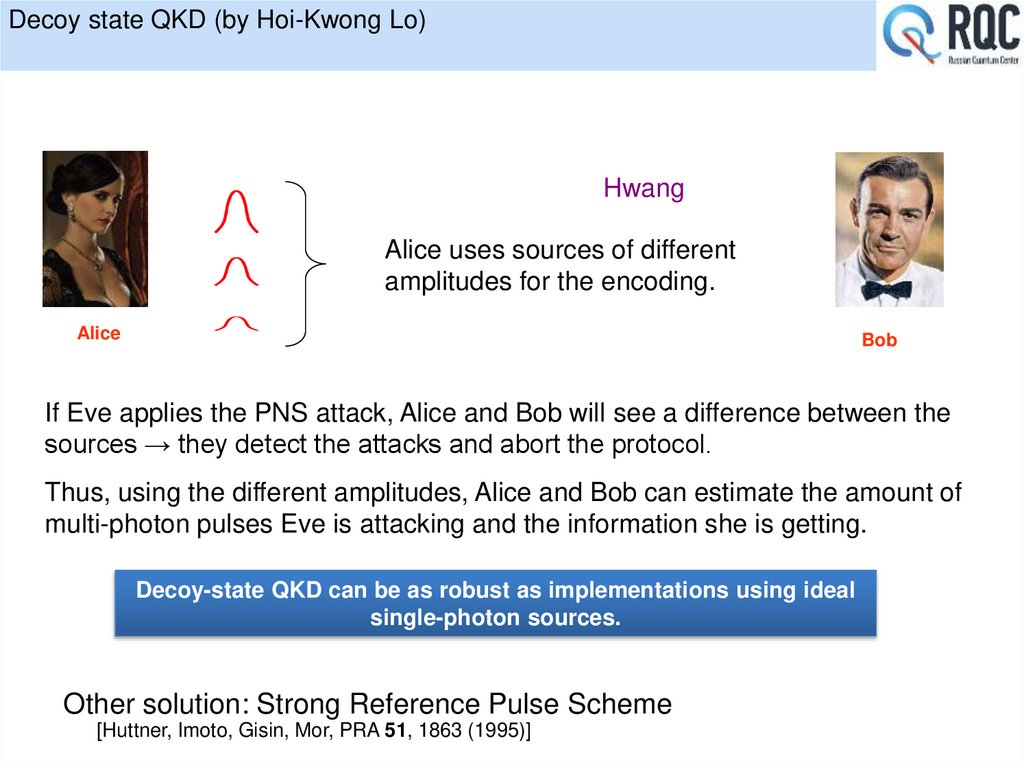
21. Secrecy criteria
There exists a key distillationprotocol allowing to produce a
key
D
11%
14.67%
There may exist a key
distillation protocol allowing to
produce a key
?
21
22.
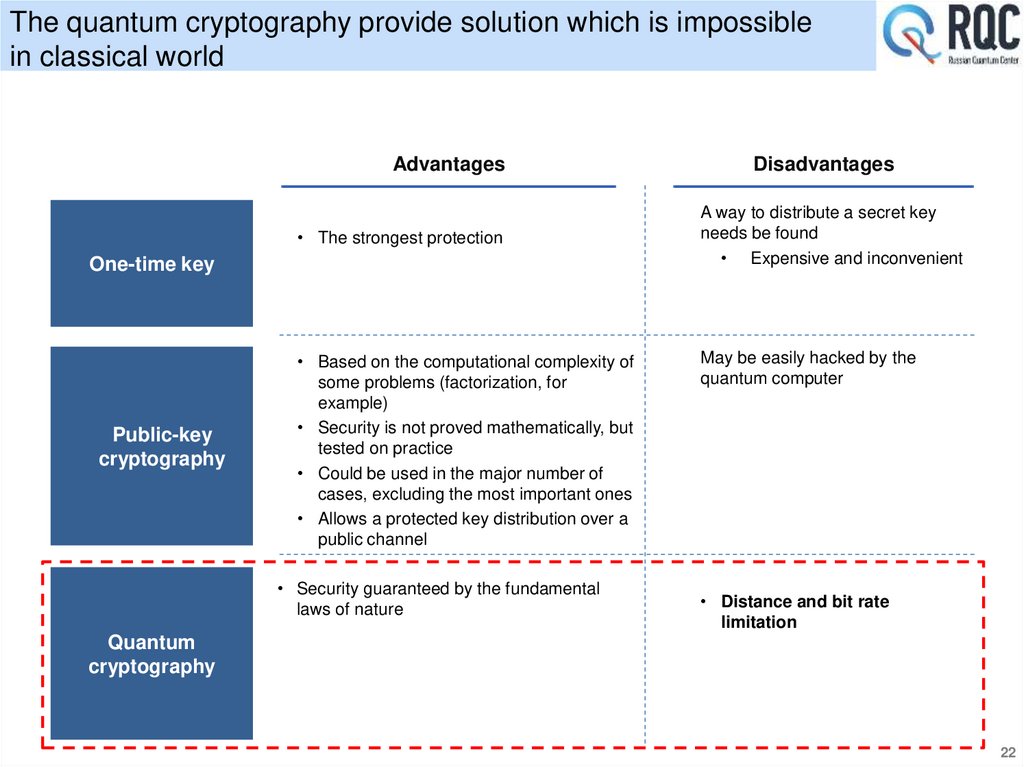
The quantum cryptography provide solution which is impossiblein classical world
Advantages
• The strongest protection
One-time key
Public-key
cryptography
• Based on the computational complexity of
some problems (factorization, for
example)
• Security is not proved mathematically, but
tested on practice
• Could be used in the major number of
cases, excluding the most important ones
• Allows a protected key distribution over a
public channel
• Security guaranteed by the fundamental
laws of nature
Disadvantages
A way to distribute a secret key
needs be found
• Expensive and inconvenient
May be easily hacked by the
quantum computer
• Distance and bit rate
limitation
Quantum
cryptography
22
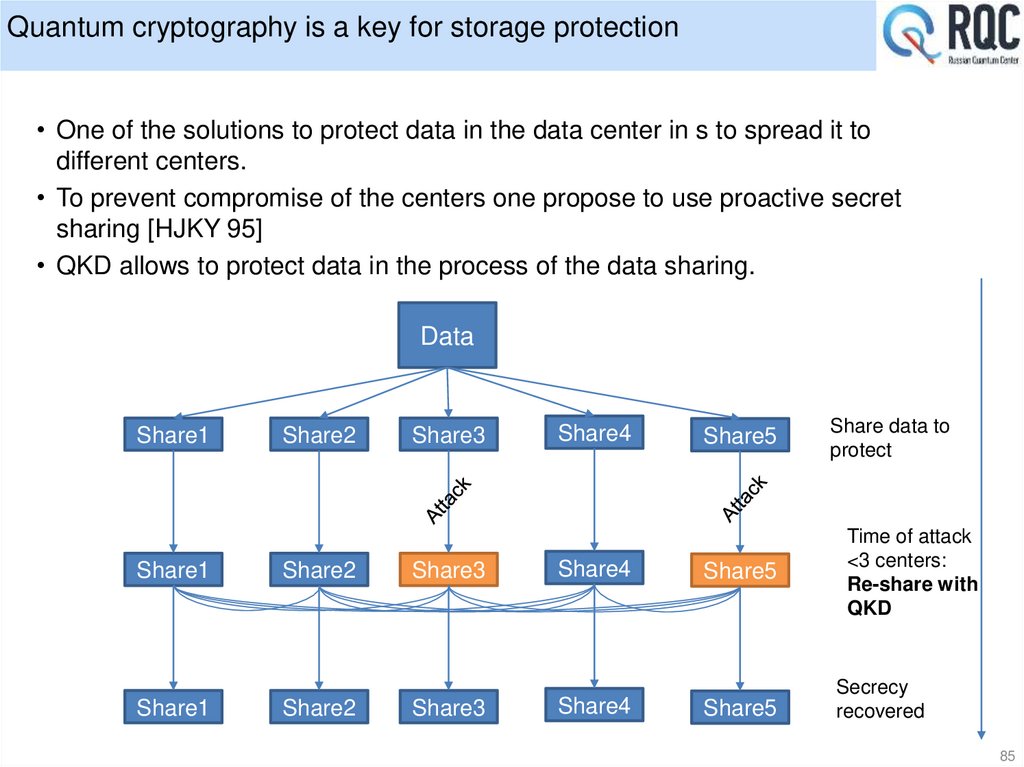
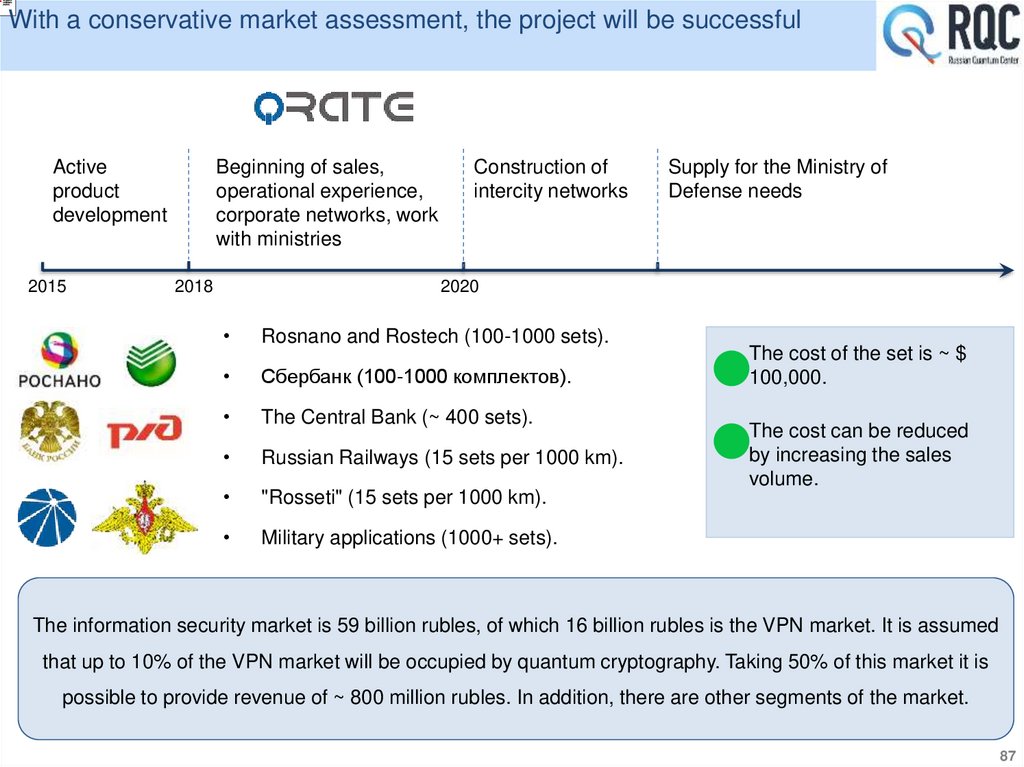
23.
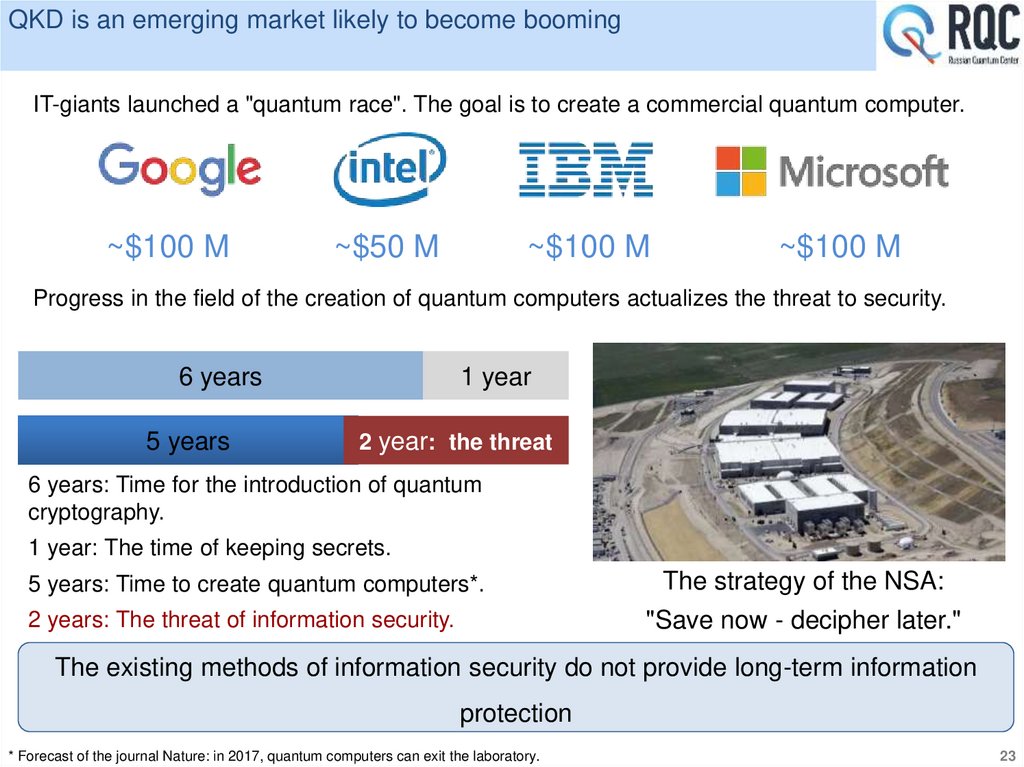
QKD is an emerging market likely to become boomingIT-giants launched a "quantum race". The goal is to create a commercial quantum computer.
~$100 M
~$50 M
~$100 M
~$100 M
Progress in the field of the creation of quantum computers actualizes the threat to security.
6 years
5 years
1 year
2 year: the threat
6 years: Time for the introduction of quantum
cryptography.
1 year: The time of keeping secrets.
5 years: Time to create quantum computers*.
The strategy of the NSA:
2 years: The threat of information security.
"Save now - decipher later."
The existing methods of information security do not provide long-term information
protection
* Forecast of the journal Nature: in 2017, quantum computers can exit the laboratory.
23
24.
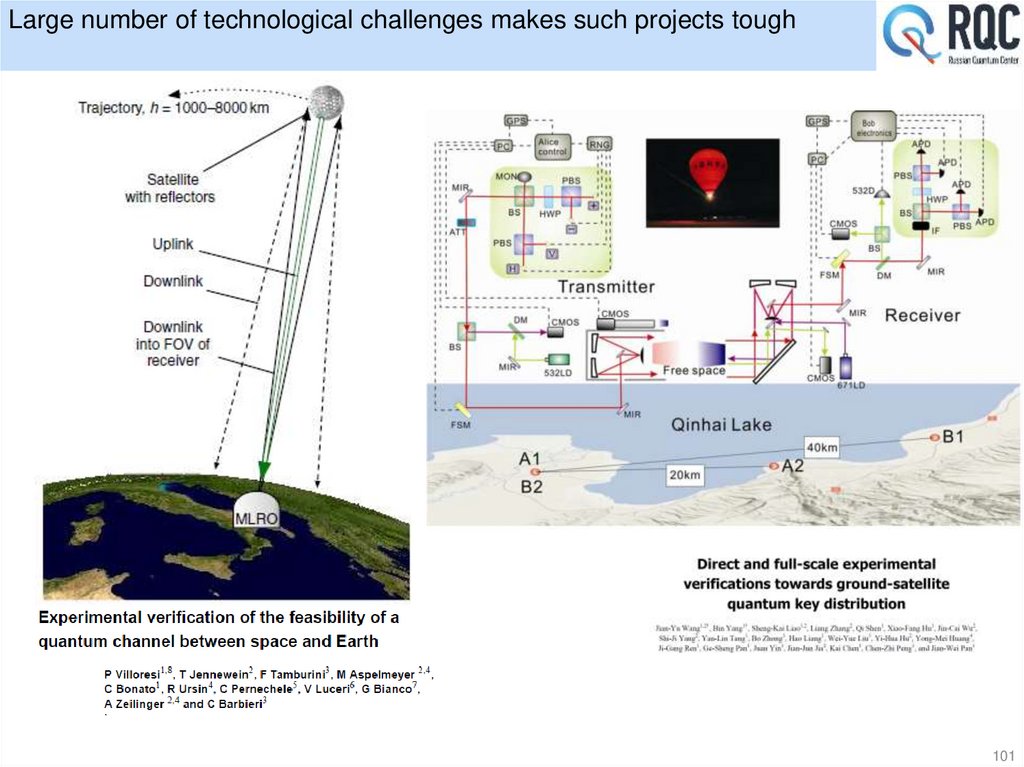
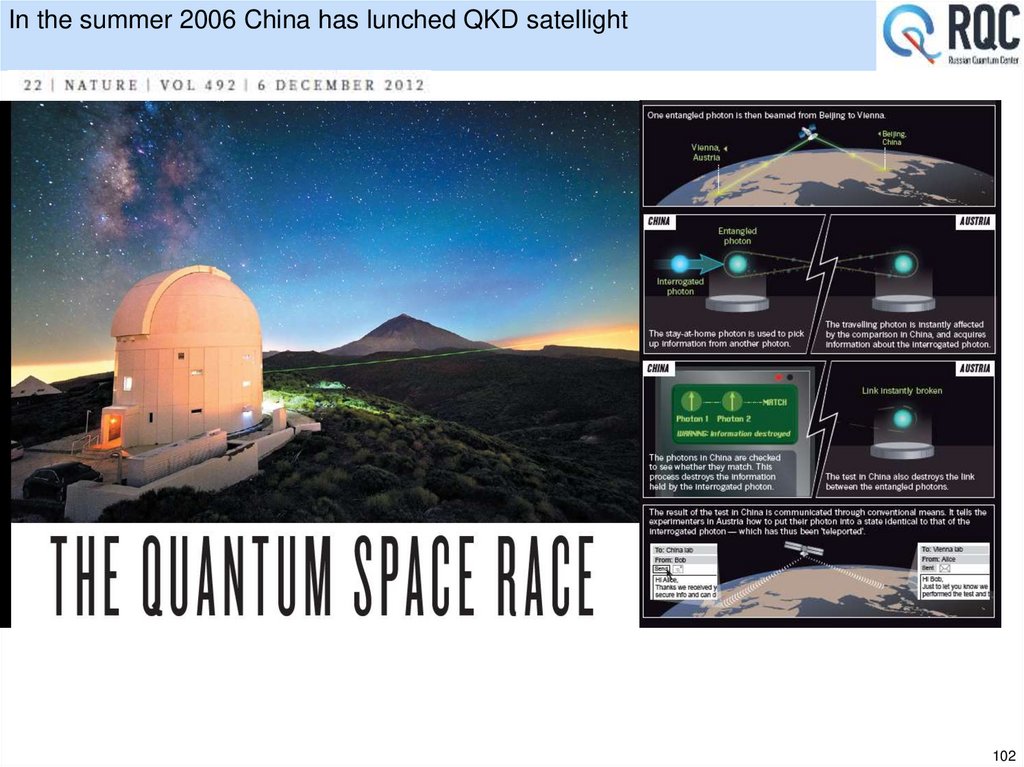
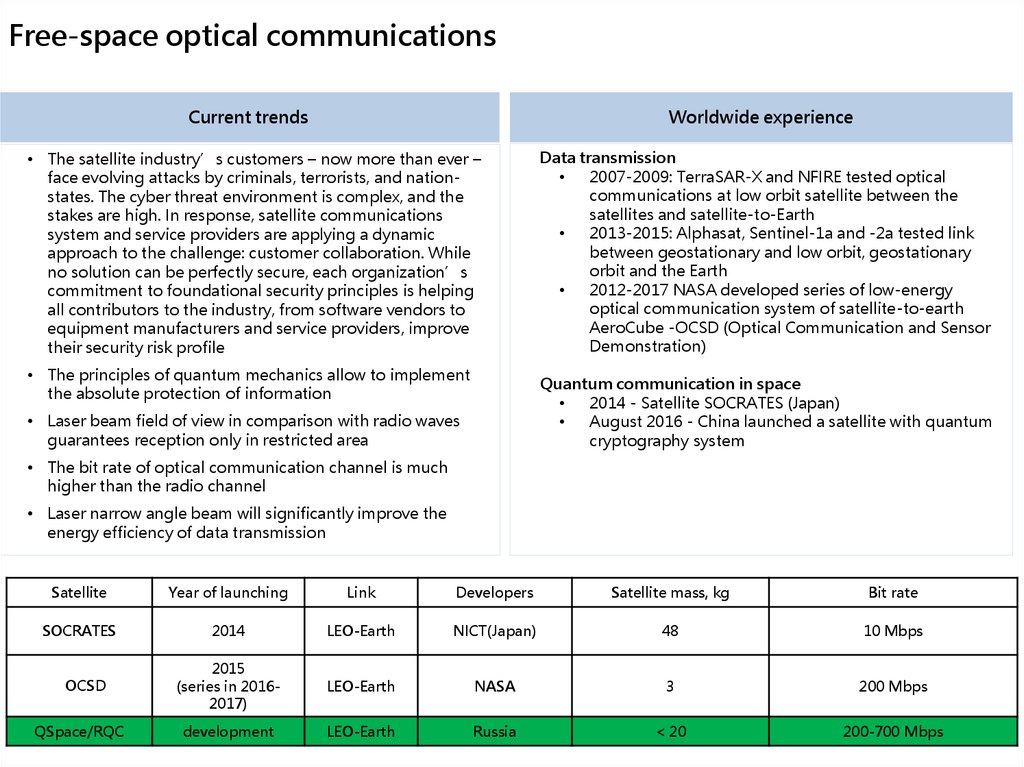
• Quantum key distribution experiments24
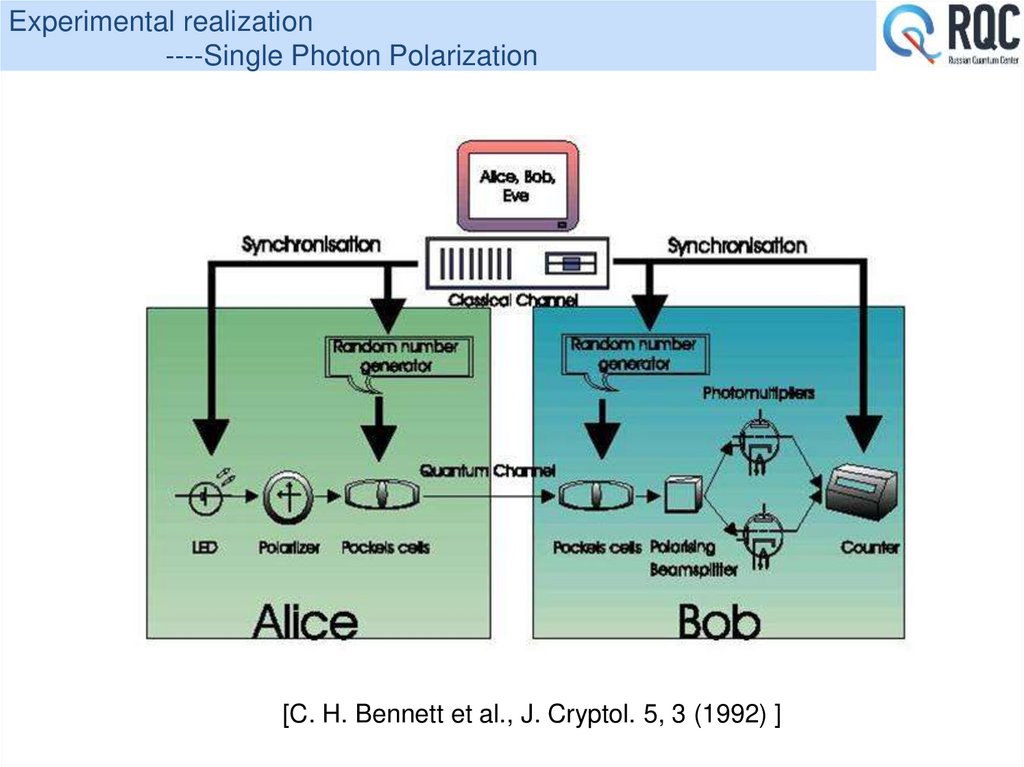
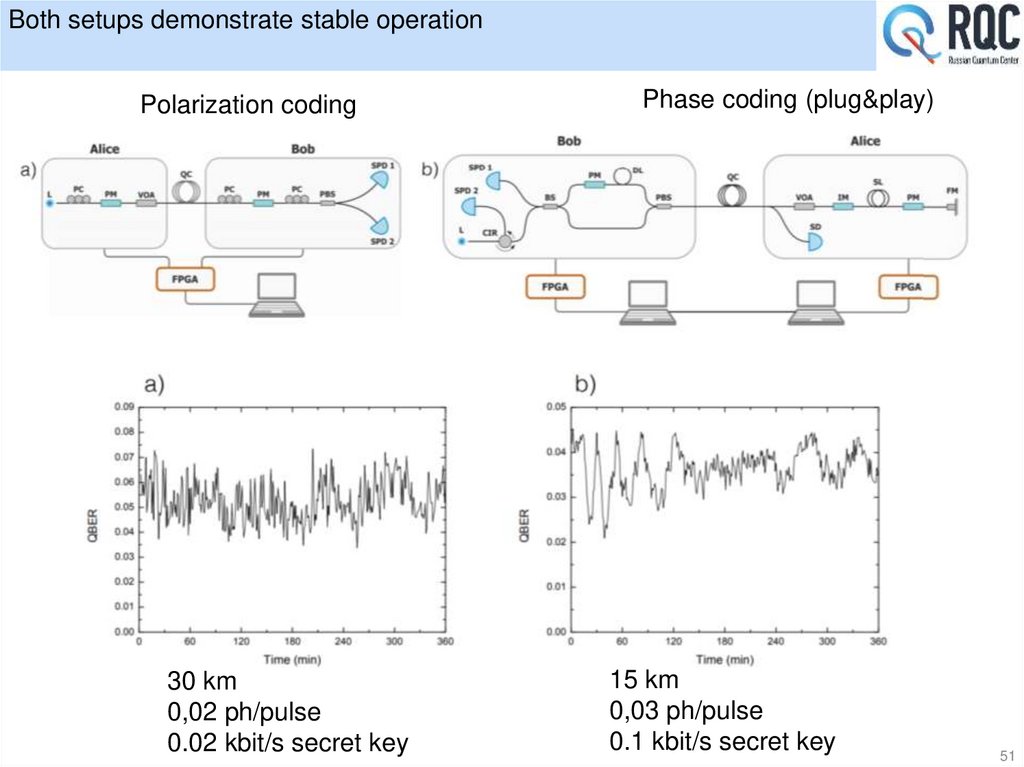
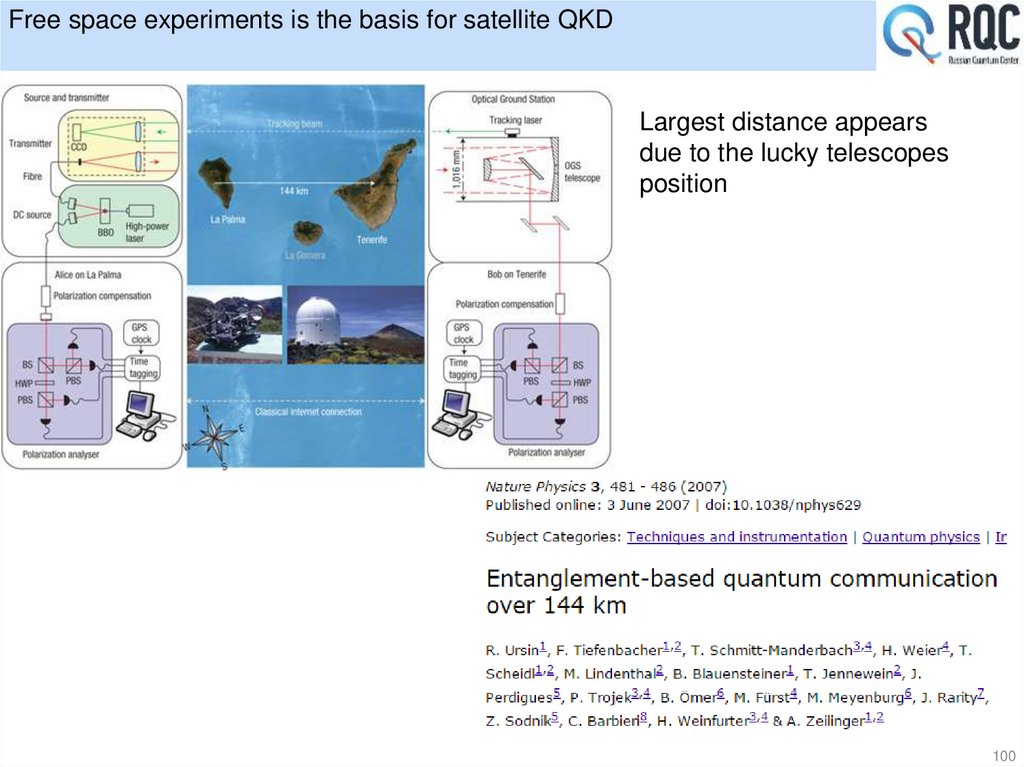
25. Experimental realization ----Single Photon Polarization
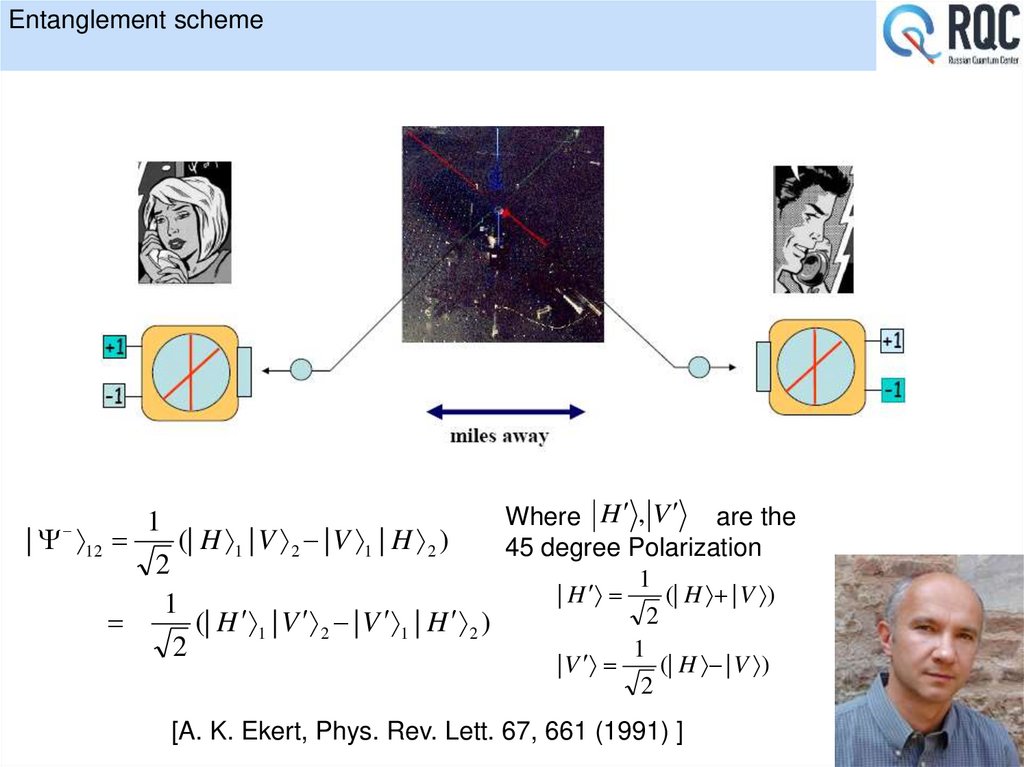
[C. H. Bennett et al., J. Cryptol. 5, 3 (1992) ]26. Entanglement scheme
Where H , V are the1
| 12
(| H 1 | V 2 | V 1 | H 2 )
45 degree Polarization
2
1
|
H
(| H | V )
1
2
(| H 1 | V 2 | V 1 | H 2 )
2
1
| V
2
(| H | V )
[A. K. Ekert, Phys. Rev. Lett. 67, 661 (1991) ]
26
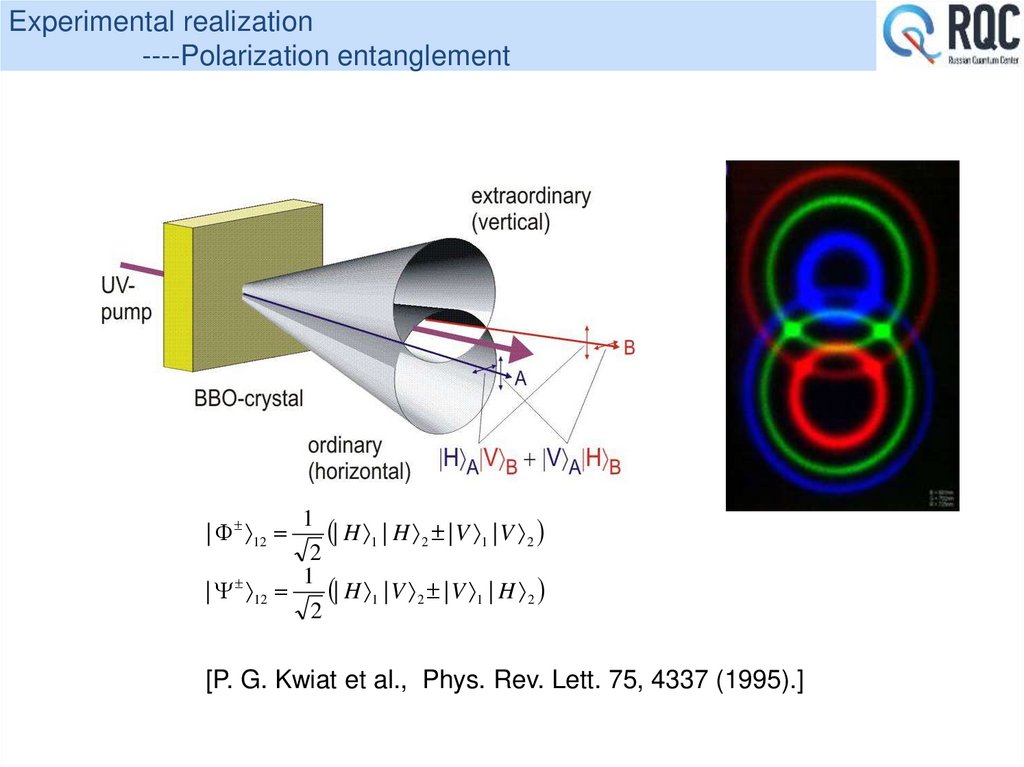
27. Experimental realization ----Polarization entanglement
1| H 1 | H 2 | V 1 | V 2
2
1
| H 1 | V 2 | V 1 | H 2
| 12
2
| 12
[P. G. Kwiat et al., Phys. Rev. Lett. 75, 4337 (1995).]
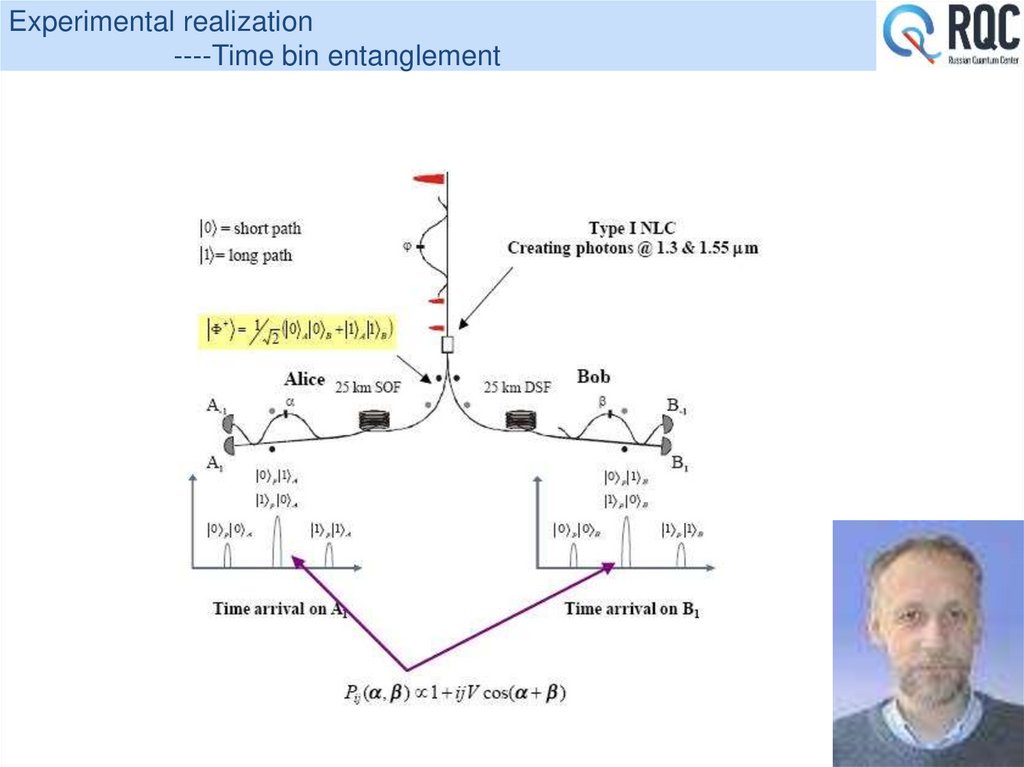
28. Experimental realization ----Time bin entanglement
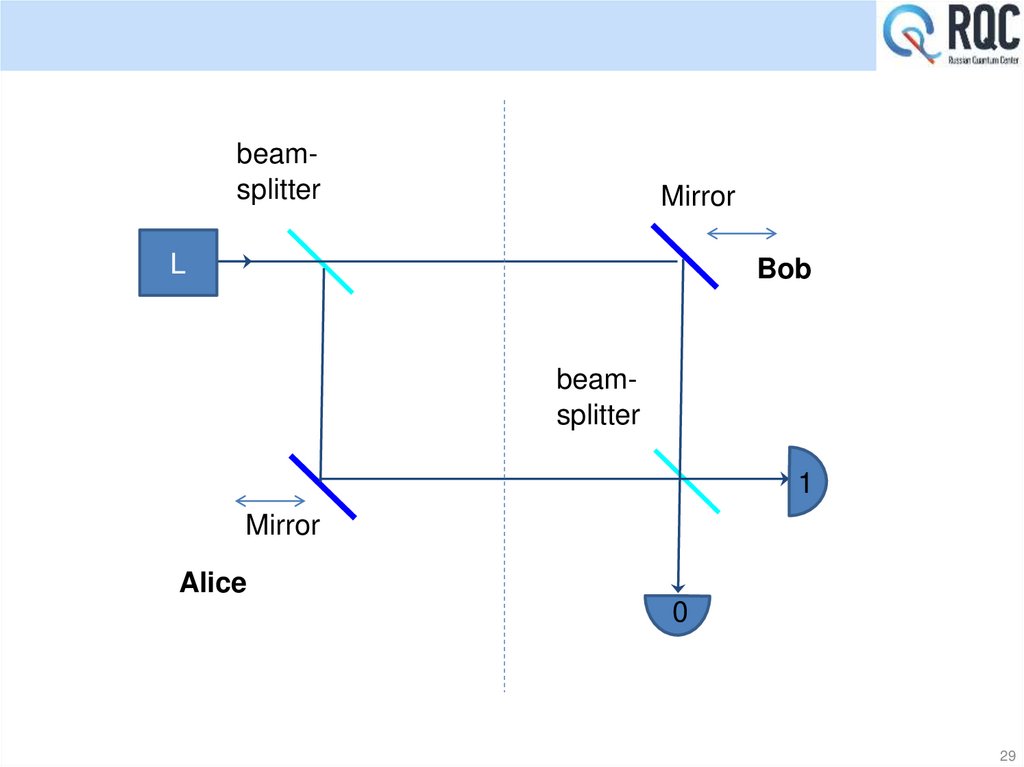
29.
beamsplitterMirror
L
Bob
beamsplitter
1
Mirror
Alice
0
29
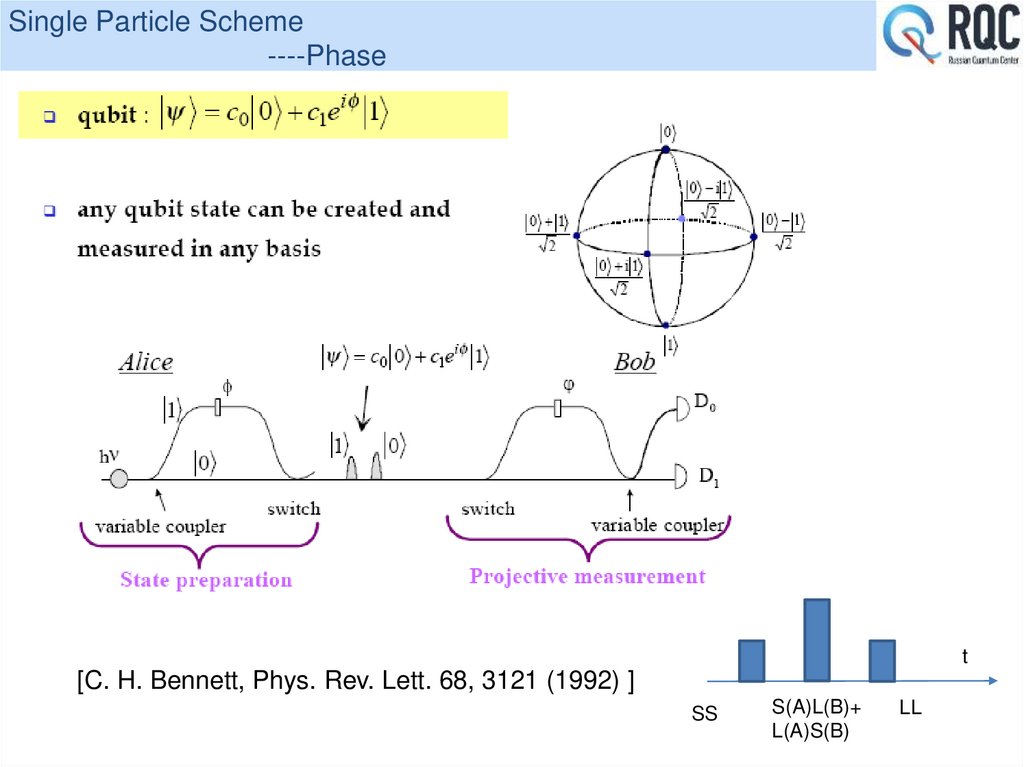
30. Single Particle Scheme ----Phase
t[C. H. Bennett, Phys. Rev. Lett. 68, 3121 (1992) ]
SS
S(A)L(B)+
L(A)S(B)
LL
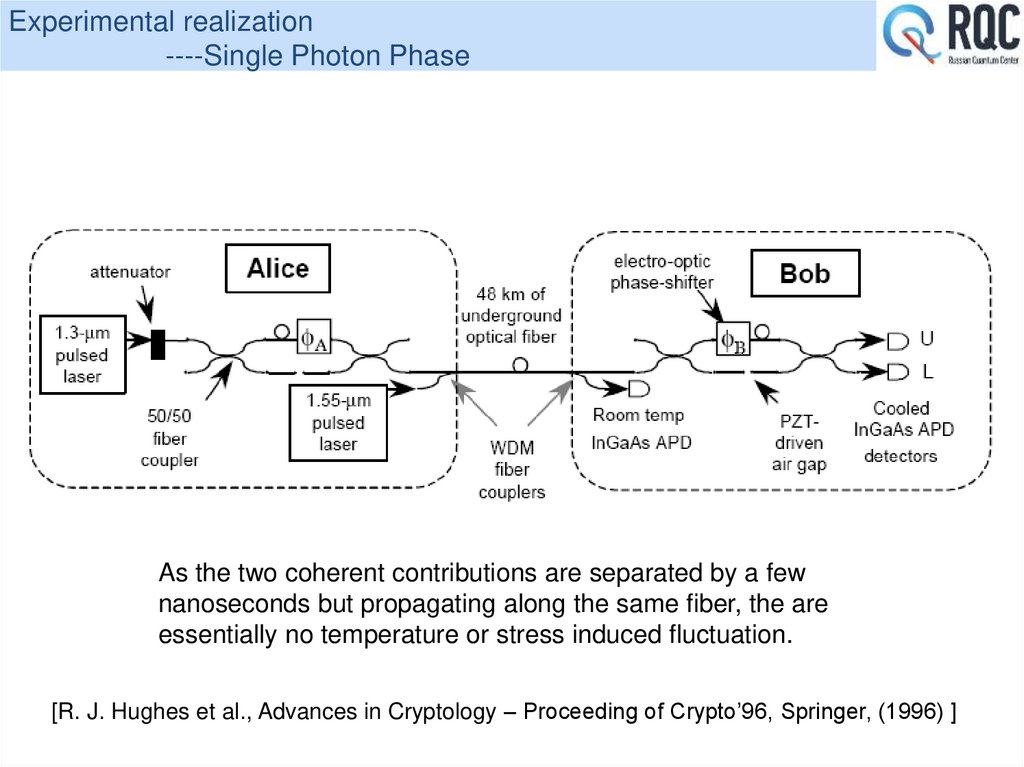
31. Experimental realization ----Single Photon Phase
As the two coherent contributions are separated by a fewnanoseconds but propagating along the same fiber, the are
essentially no temperature or stress induced fluctuation.
[R. J. Hughes et al., Advances in Cryptology – Proceeding of Crypto’96, Springer, (1996) ]
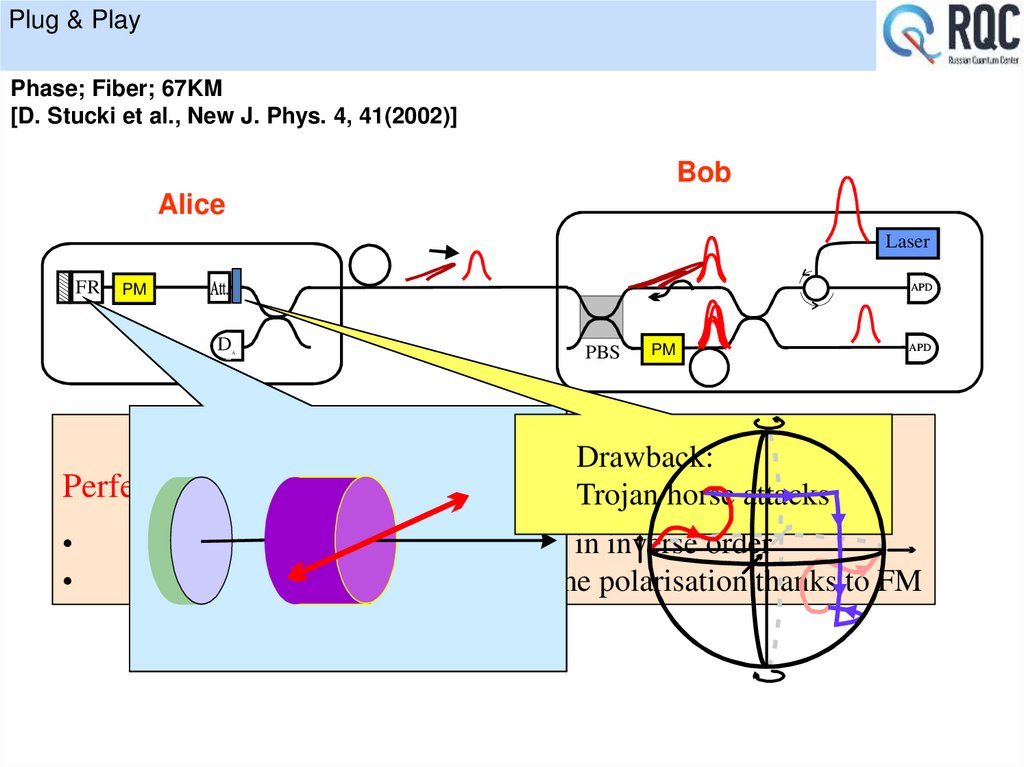
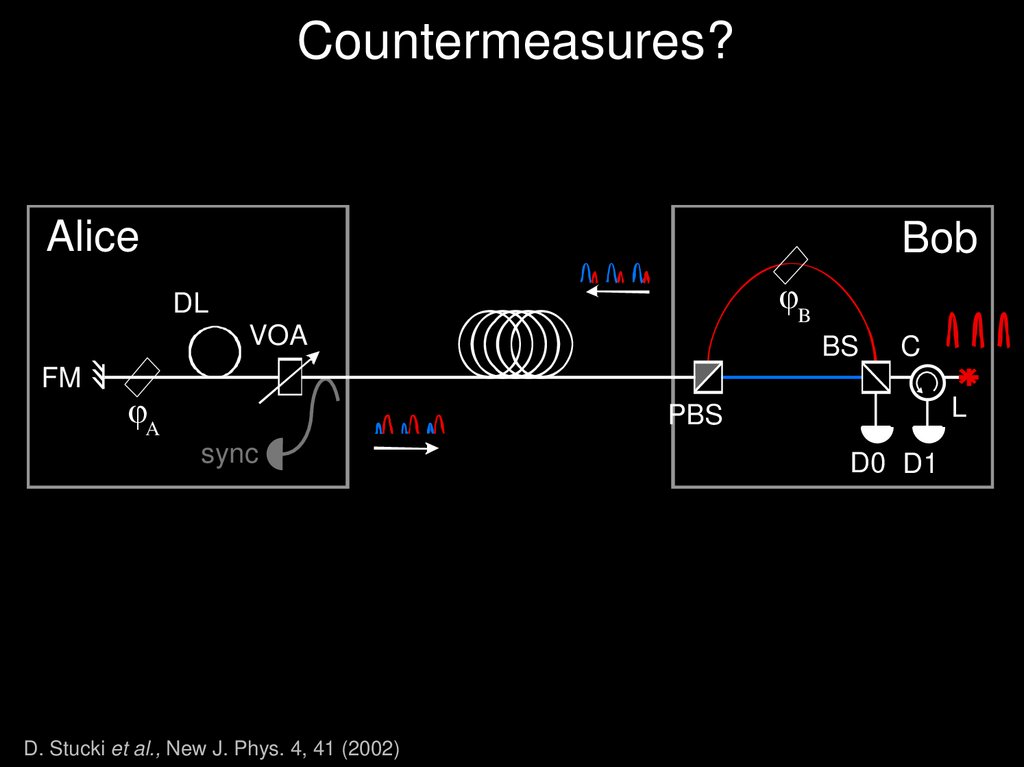
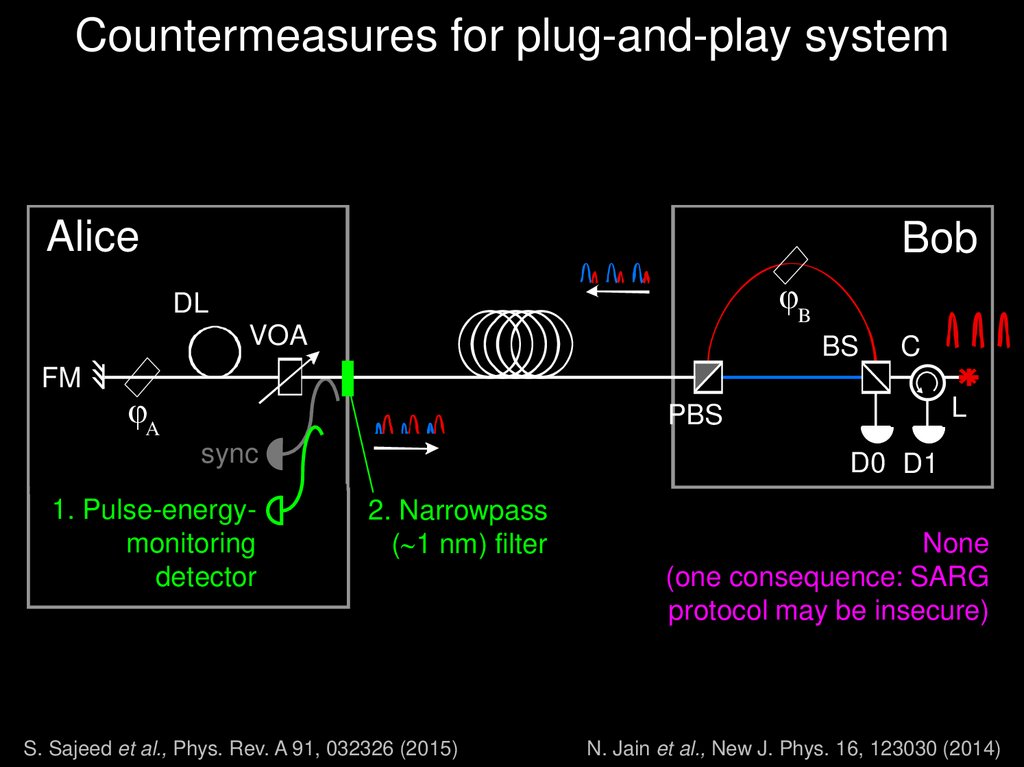
32. Plug & Play
Plug & PlayPhase; Fiber; 67KM
[D. Stucki et al., New J. Phys. 4, 41(2002)]
Bob
Alice
Laser
FR
PM
APD
D
A
PBS
PM
APD
Drawback:
Perfect interference (V 99%) withoutTrojan
any adjustments
, since:
horse attacks
both pulses travel the same path in inverse order
both pulses have exactly the same polarisation thanks to FM
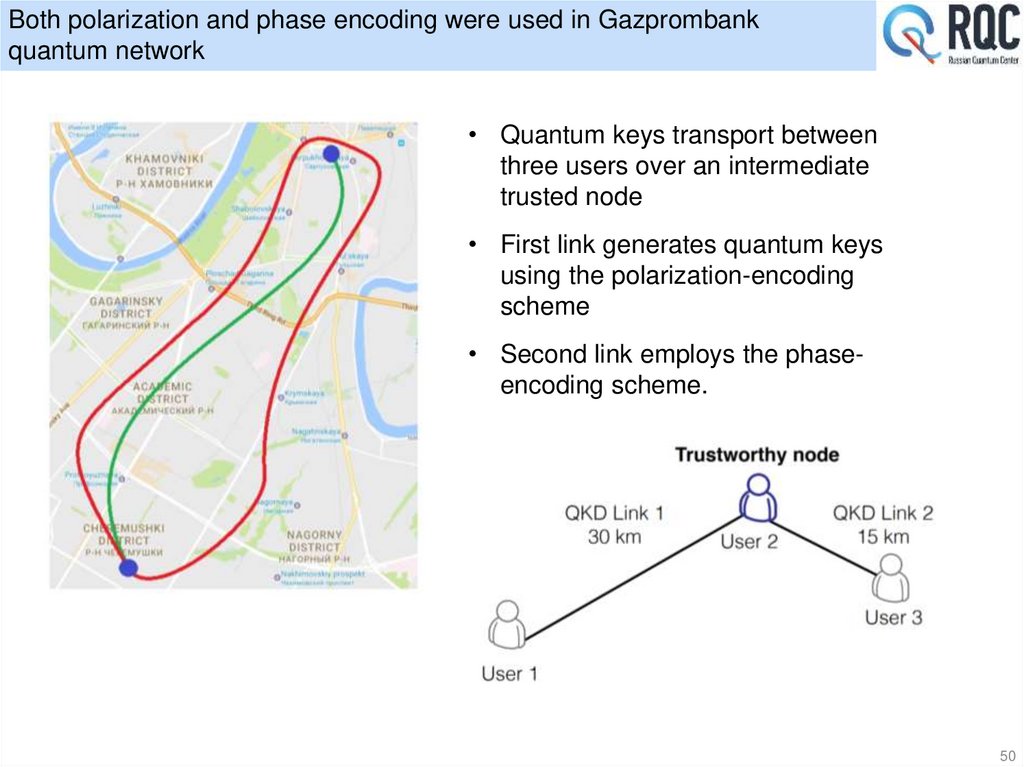
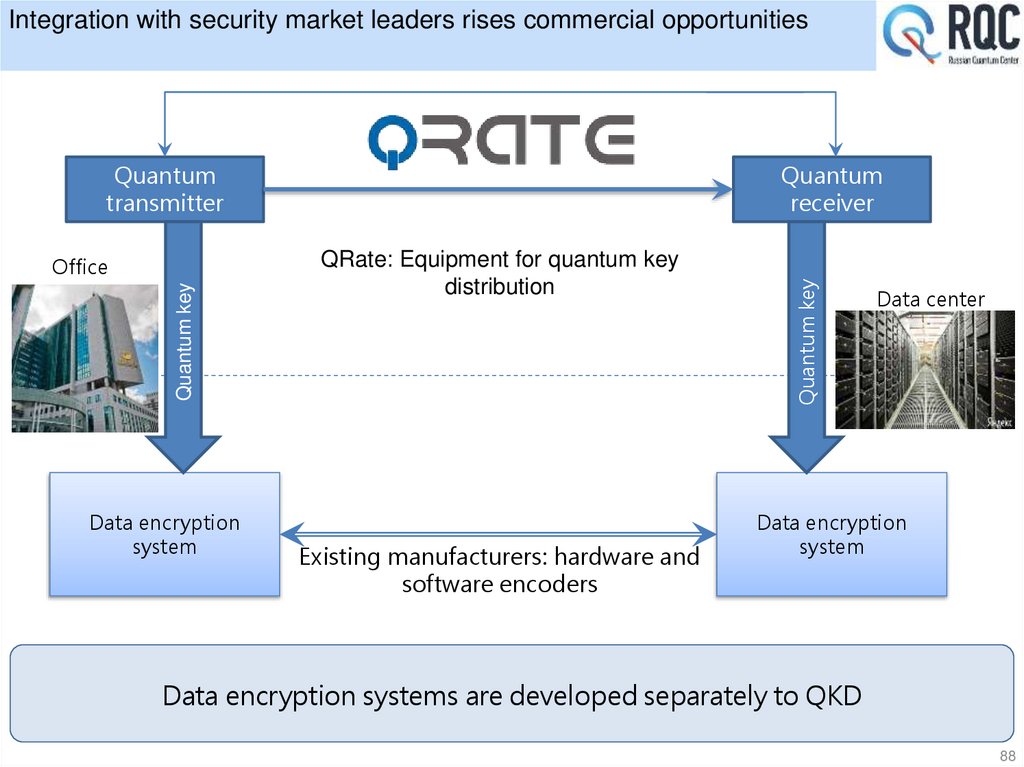
33. First in Russia fiber based quantum cryptography setup developed in ISP
BOBAssembly
BOB
Case
SPCM
Assembly
Quantum
Channel
25 km
Storage
Line
25 km
ALICE
Assembly
ALICE
Case
25 km quantum channel of single mode fiber for 1550nm
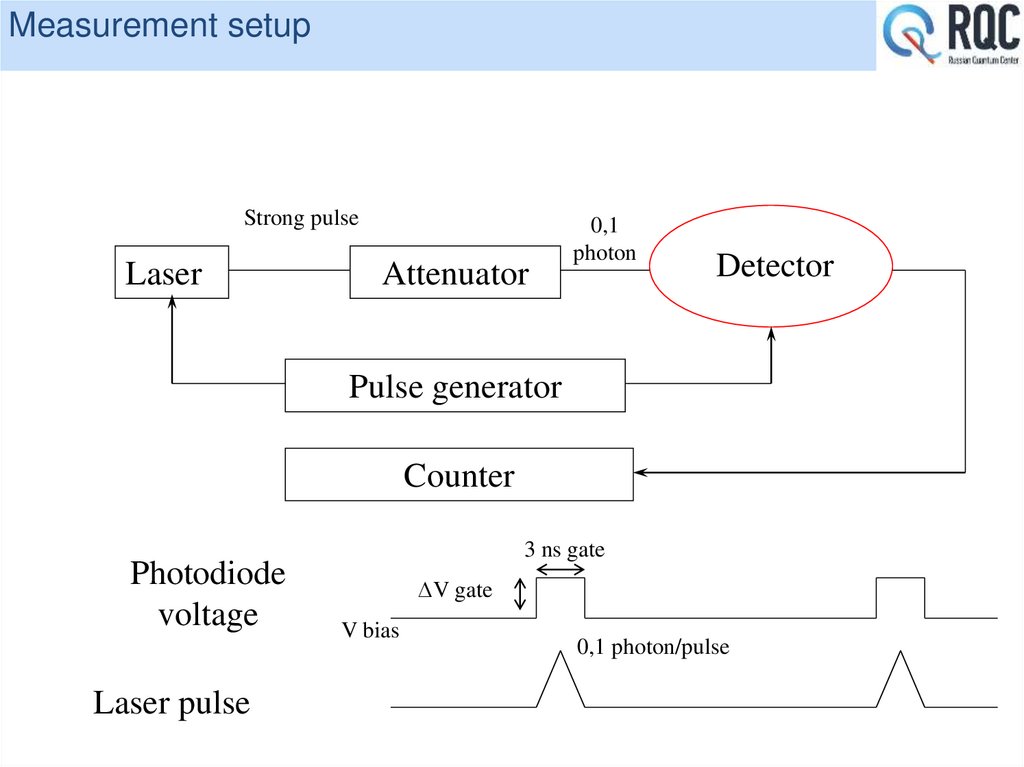
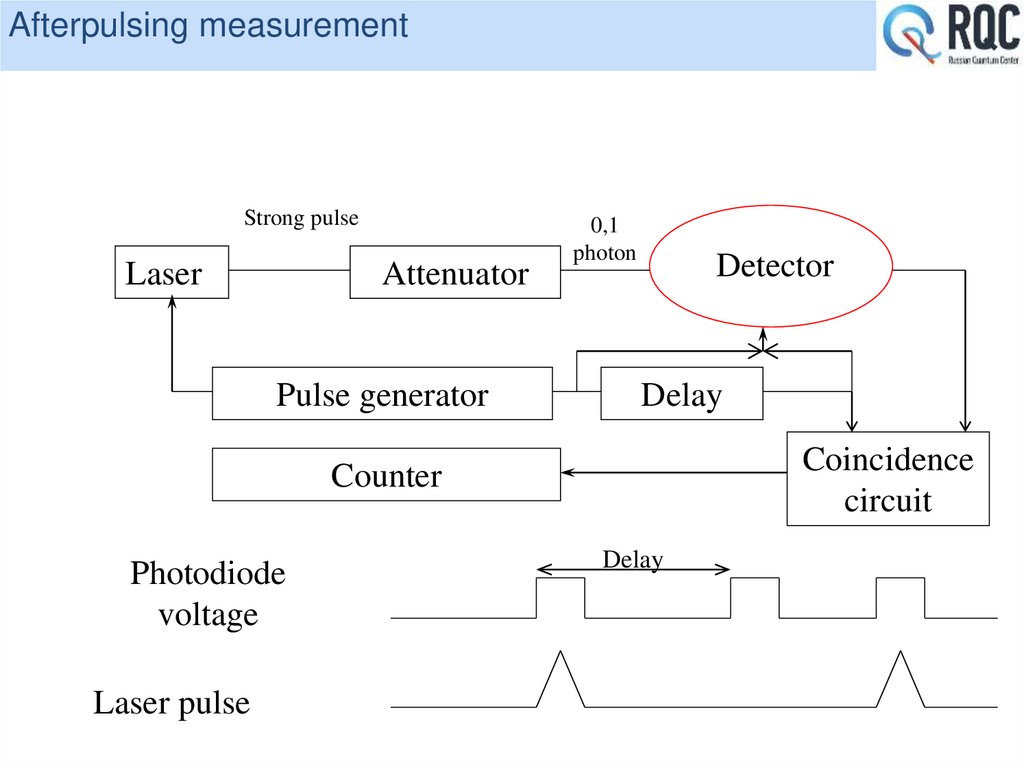
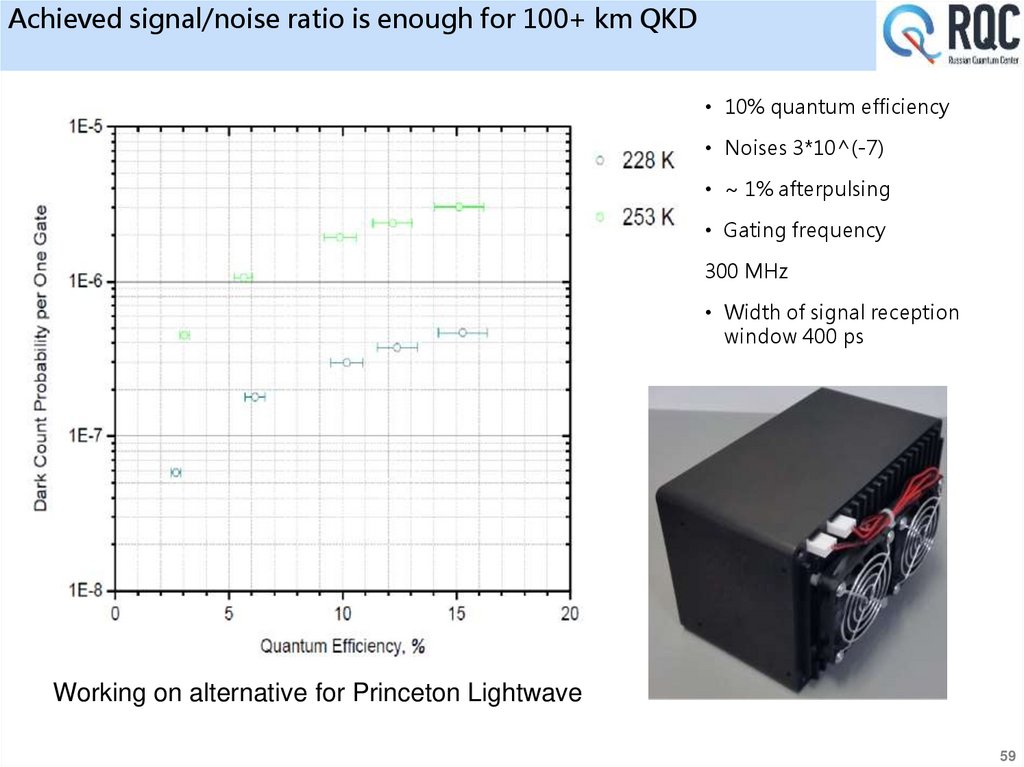
10% quantum efficiency at 5*10-5 dark count probability per 3 ns gate.
Operates at 0,1-0,2 photon/pulse (BB84 protocol)
30 bit/s sifted key rate demonstrated
34.
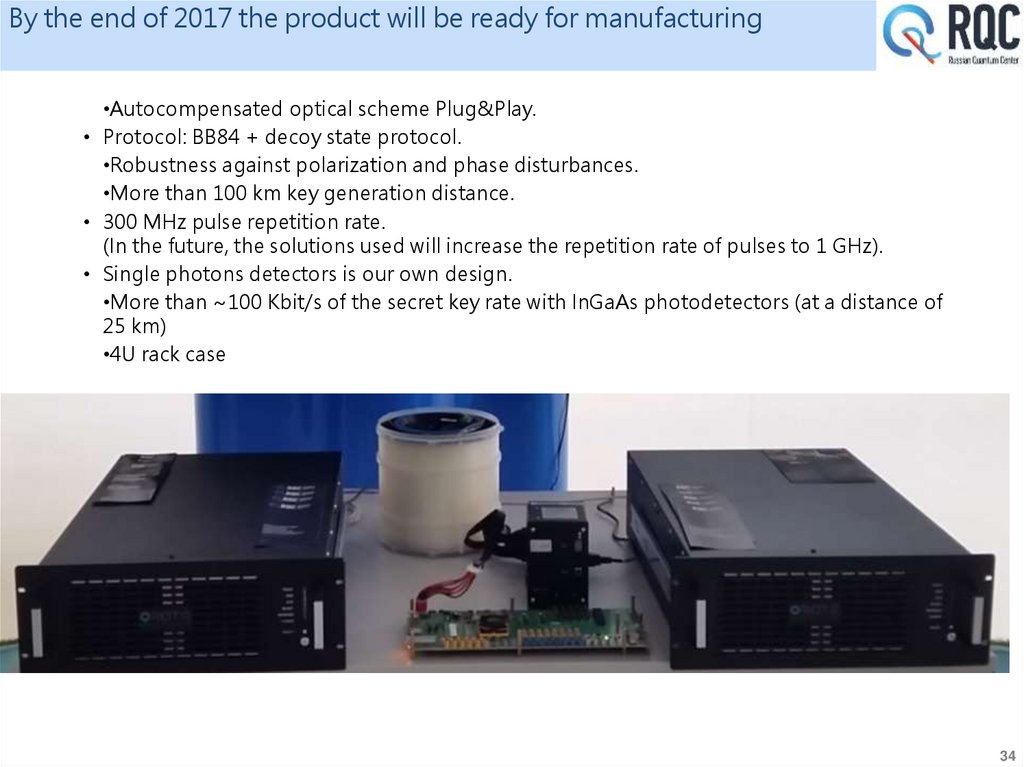
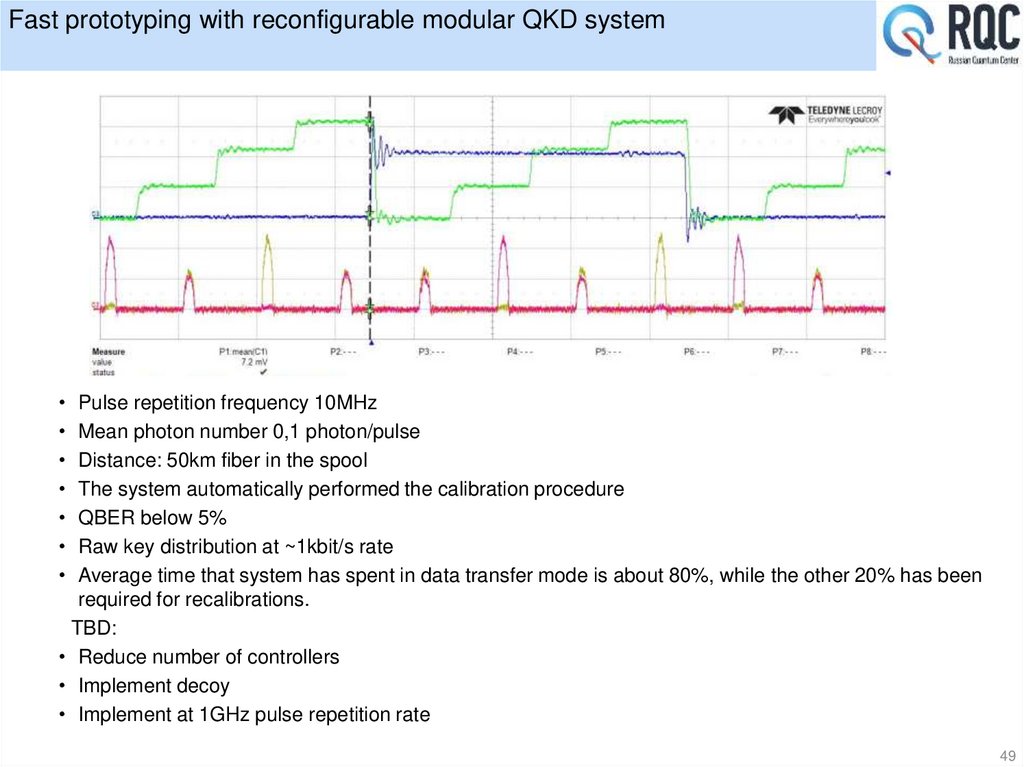
By the end of 2017 the product will be ready for manufacturing•Autocompensated optical scheme Plug&Play.
• Protocol: BB84 + decoy state protocol.
•Robustness against polarization and phase disturbances.
•More than 100 km key generation distance.
• 300 MHz pulse repetition rate.
(In the future, the solutions used will increase the repetition rate of pulses to 1 GHz).
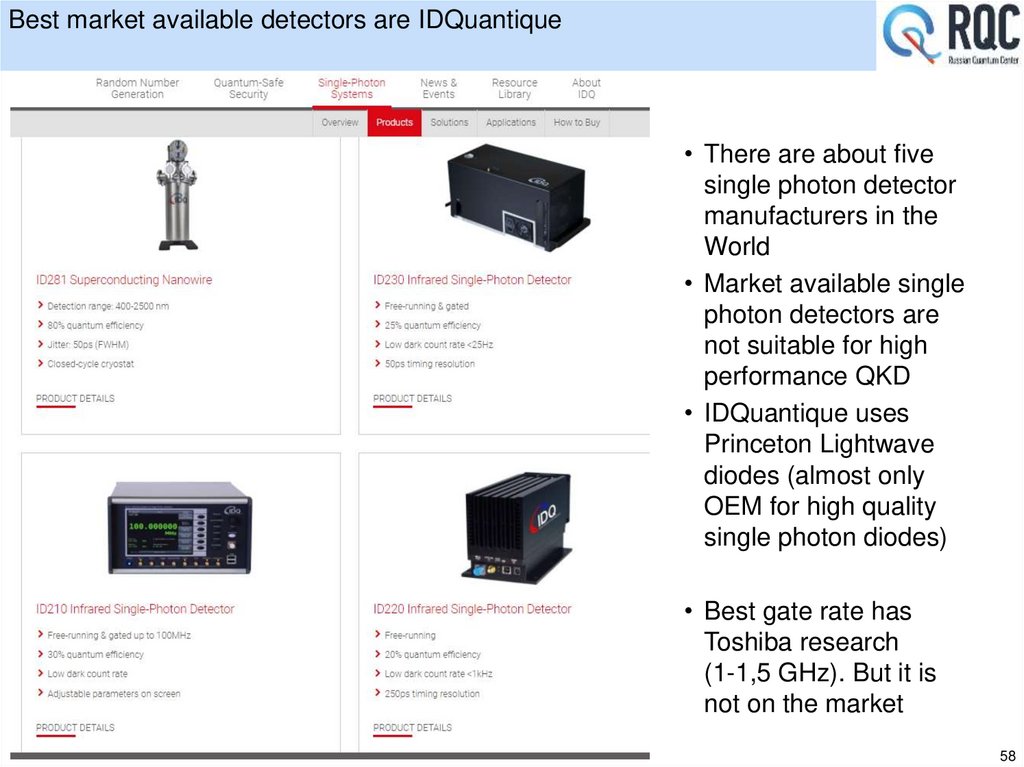
• Single photons detectors is our own design.
•More than ~100 Kbit/s of the secret key rate with InGaAs photodetectors (at a distance of
25 km)
•4U rack case
34
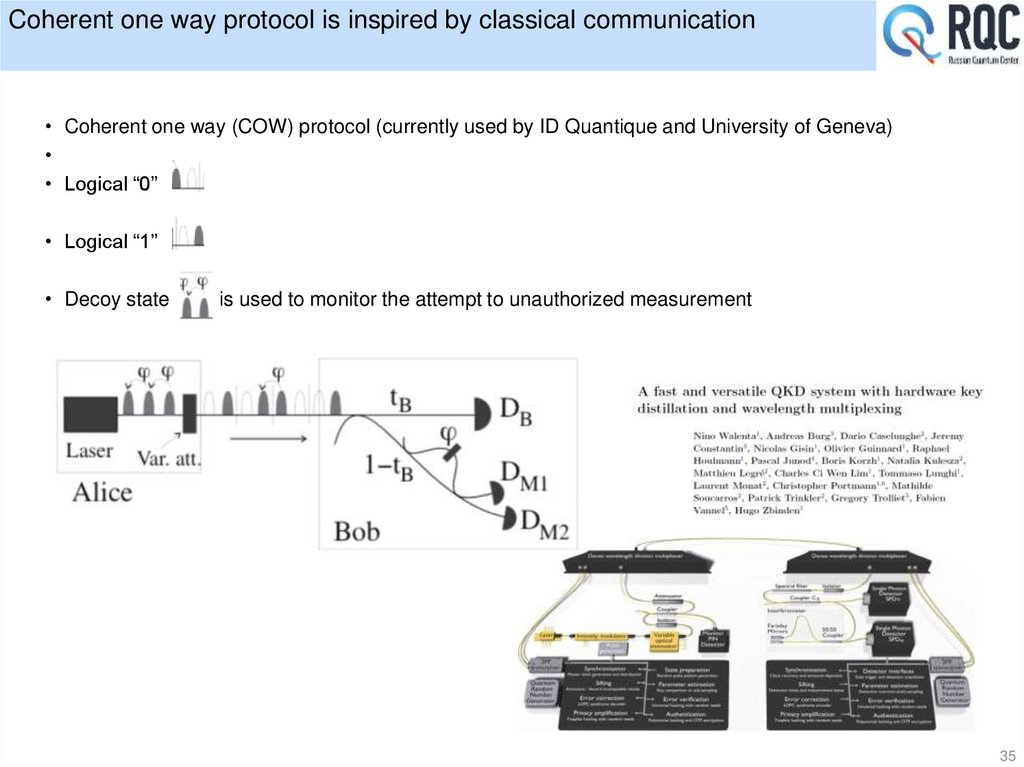
35. Coherent one way protocol is inspired by classical communication
• Coherent one way (COW) protocol (currently used by ID Quantique and University of Geneva)• Logical “0”
• Logical “1”
• Decoy state
is used to monitor the attempt to unauthorized measurement
35
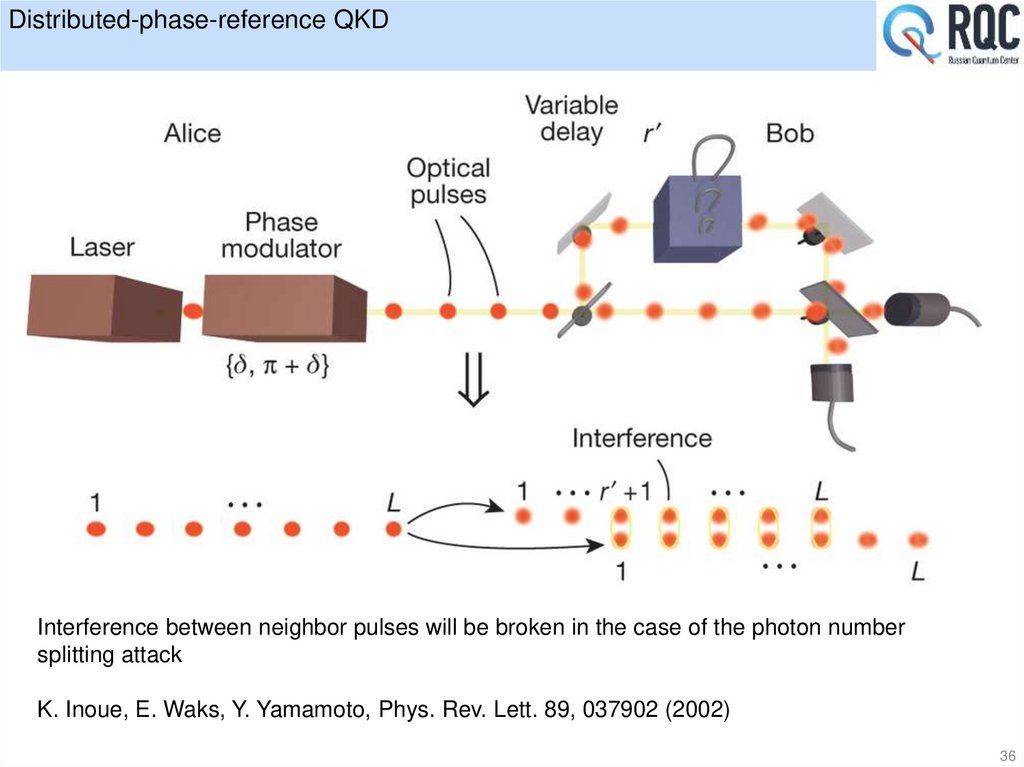
36. Distributed-phase-reference QKD
Interference between neighbor pulses will be broken in the case of the photon numbersplitting attack
K. Inoue, E. Waks, Y. Yamamoto, Phys. Rev. Lett. 89, 037902 (2002)
36
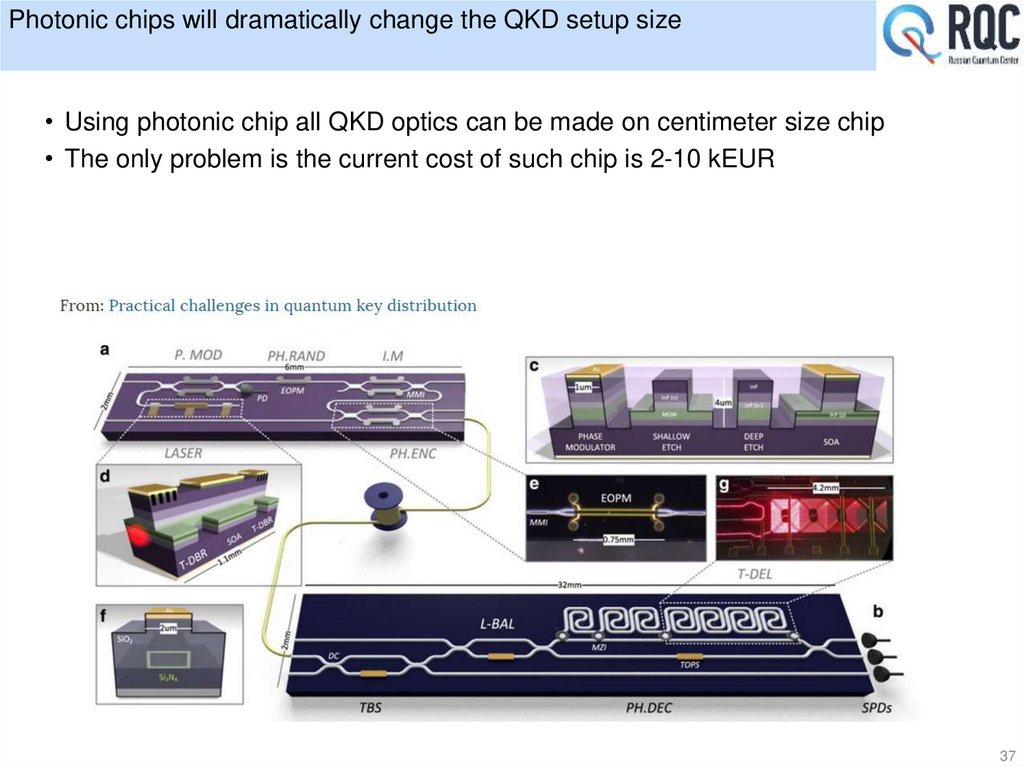
37. Photonic chips will dramatically change the QKD setup size
• Using photonic chip all QKD optics can be made on centimeter size chip• The only problem is the current cost of such chip is 2-10 kEUR
37
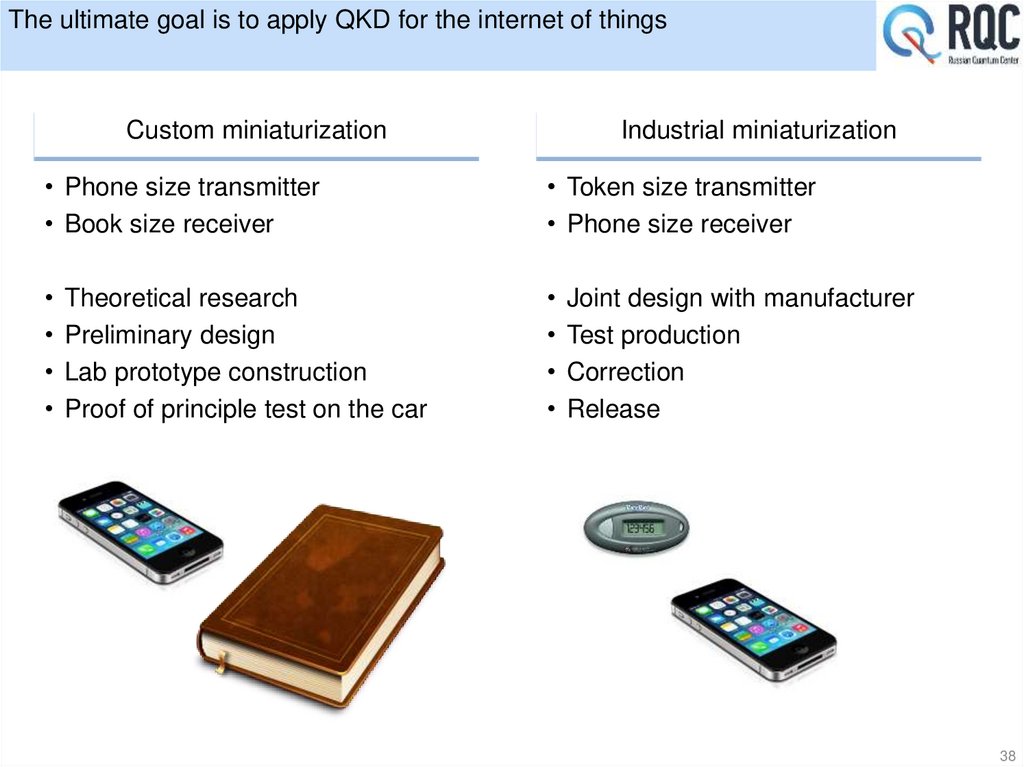
38. The ultimate goal is to apply QKD for the internet of things
Custom miniaturizationIndustrial miniaturization
• Phone size transmitter
• Book size receiver
• Token size transmitter
• Phone size receiver
• Theoretical research
• Preliminary design
• Lab prototype construction
• Proof of principle test on the car
• Joint design with manufacturer
• Test production
• Correction
• Release
38
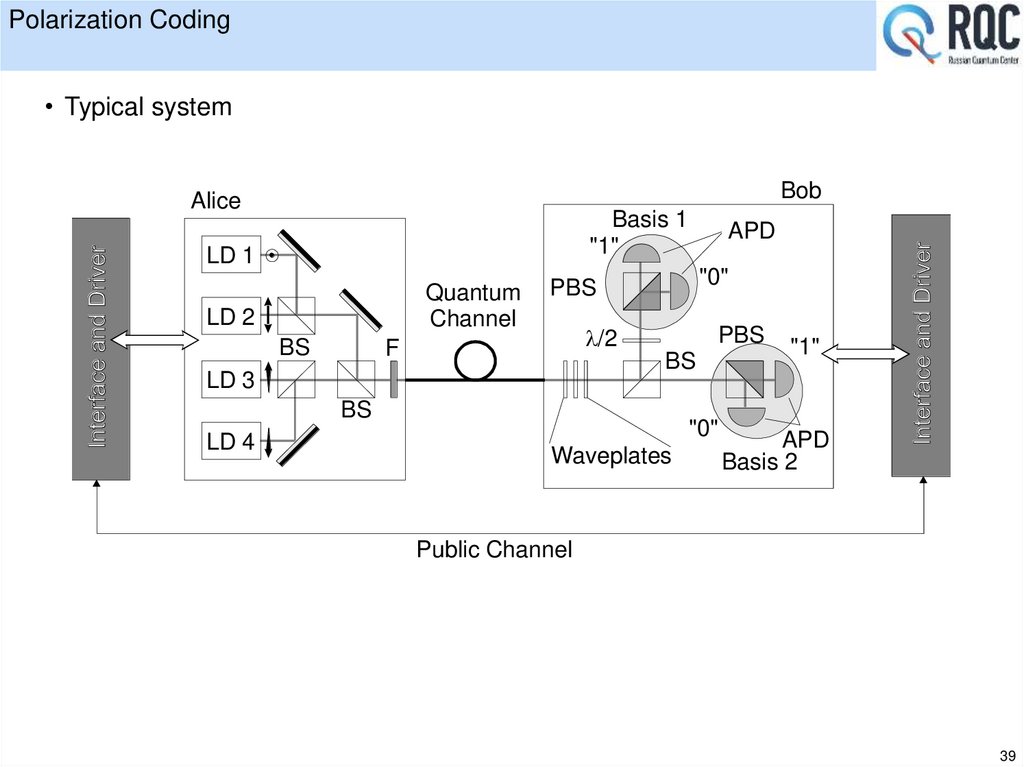
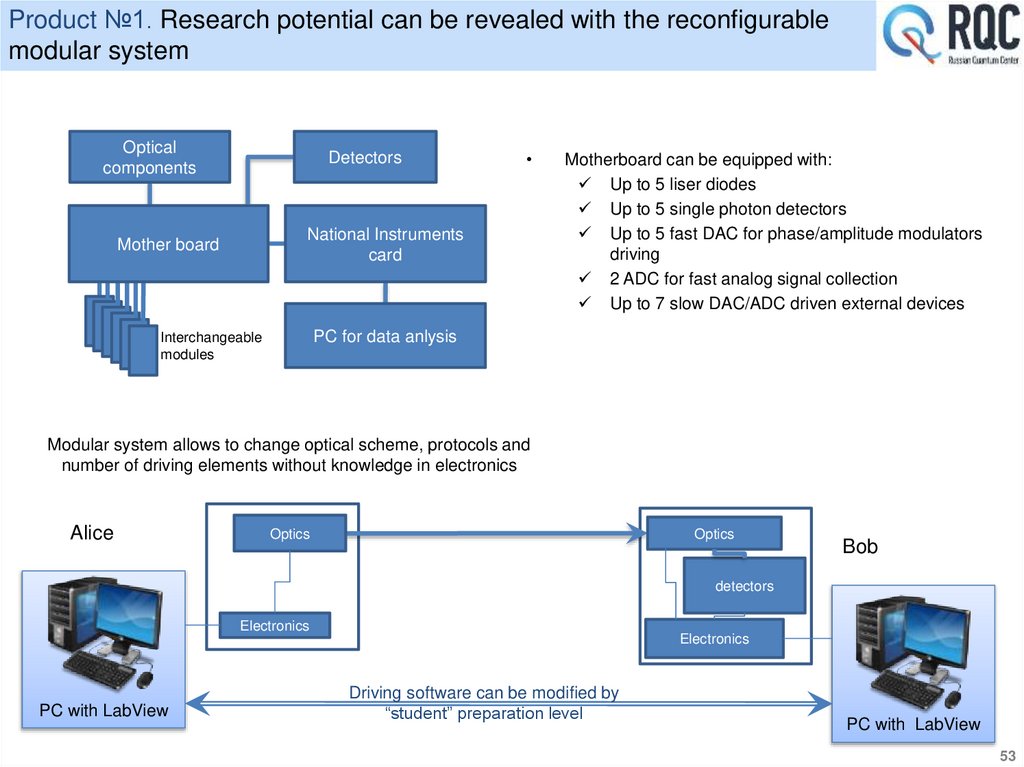
39. Polarization Coding
• Typical systemBob
Alice
Basis 1
"1"
LD 1
Quantum
Channel
LD 2
BS
"0"
PBS
/2
F
PBS
BS
LD 3
BS
LD 4
APD
"0"
Waveplates
"1"
APD
Basis 2
Public Channel
39
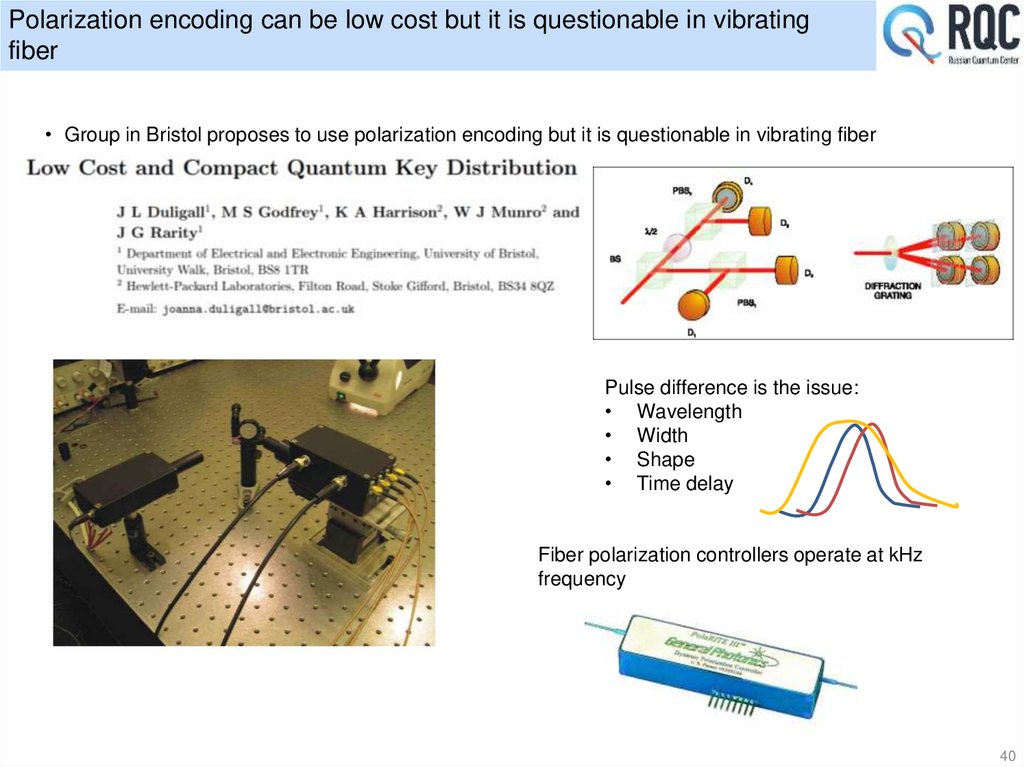
40. Polarization encoding can be low cost but it is questionable in vibrating fiber
• Group in Bristol proposes to use polarization encoding but it is questionable in vibrating fiberPulse difference is the issue:
• Wavelength
• Width
• Shape
• Time delay
Fiber polarization controllers operate at kHz
frequency
40
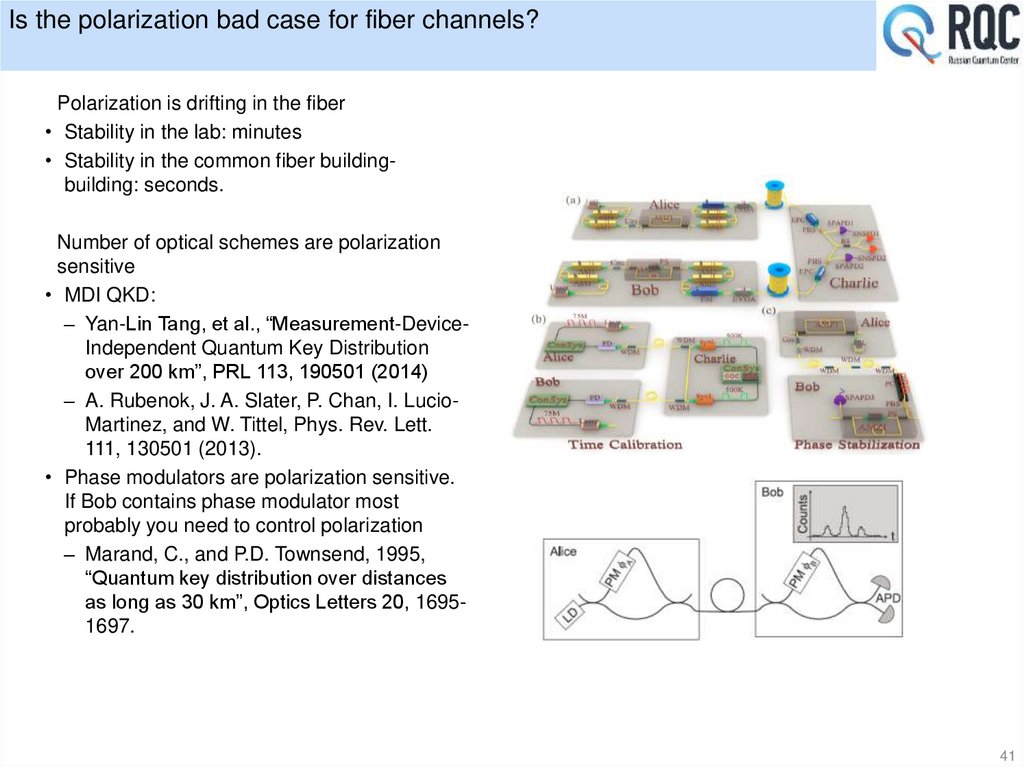
41. Is the polarization bad case for fiber channels?
Polarization is drifting in the fiber• Stability in the lab: minutes
• Stability in the common fiber buildingbuilding: seconds.
Number of optical schemes are polarization
sensitive
• MDI QKD:
– Yan-Lin Tang, et al., “Measurement-DeviceIndependent Quantum Key Distribution
over 200 km”, PRL 113, 190501 (2014)
– A. Rubenok, J. A. Slater, P. Chan, I. LucioMartinez, and W. Tittel, Phys. Rev. Lett.
111, 130501 (2013).
• Phase modulators are polarization sensitive.
If Bob contains phase modulator most
probably you need to control polarization
– Marand, C., and P.D. Townsend, 1995,
“Quantum key distribution over distances
as long as 30 km”, Optics Letters 20, 16951697.
41
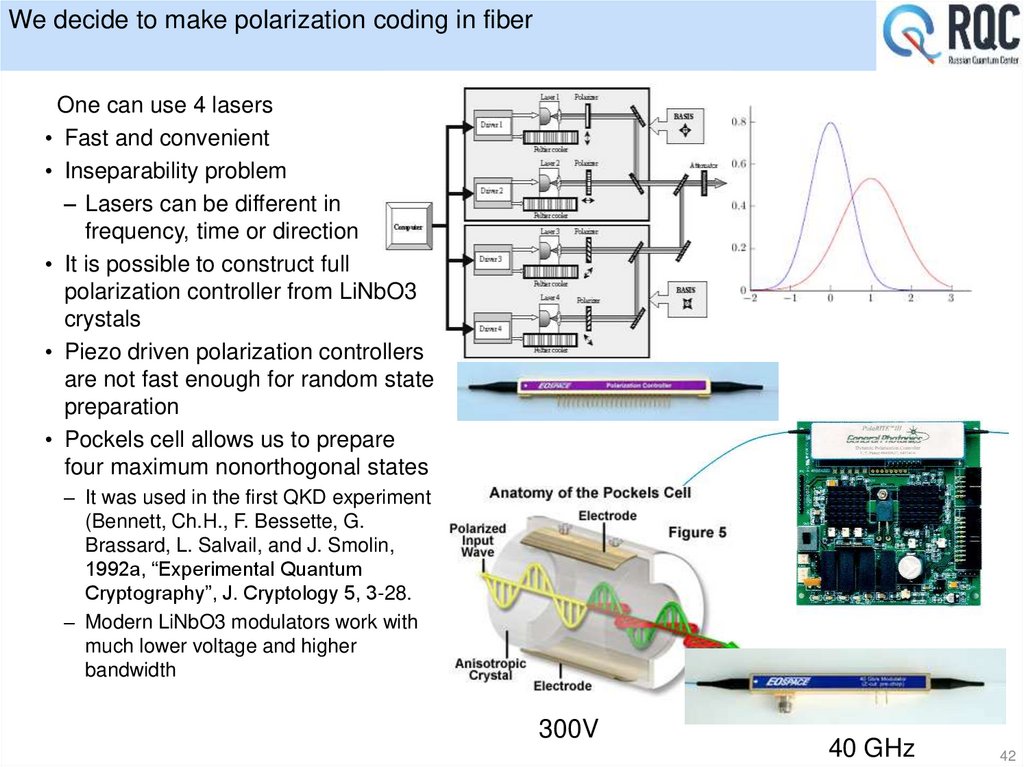
42. We decide to make polarization coding in fiber
One can use 4 lasers• Fast and convenient
• Inseparability problem
– Lasers can be different in
frequency, time or direction
• It is possible to construct full
polarization controller from LiNbO3
crystals
• Piezo driven polarization controllers
are not fast enough for random state
preparation
• Pockels cell allows us to prepare
four maximum nonorthogonal states
– It was used in the first QKD experiment
(Bennett, Ch.H., F. Bessette, G.
Brassard, L. Salvail, and J. Smolin,
1992a, “Experimental Quantum
Cryptography”, J. Cryptology 5, 3-28.
– Modern LiNbO3 modulators work with
much lower voltage and higher
bandwidth
300V
40 GHz
42
43. Polarization mode dispersion is the problem
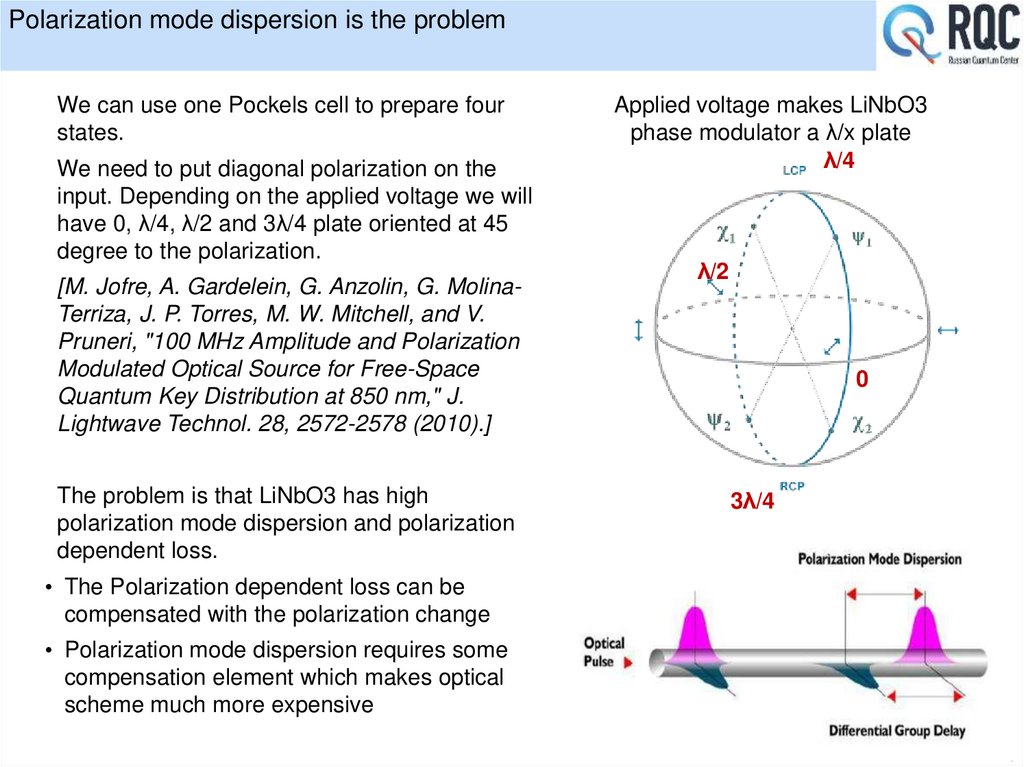
We can use one Pockels cell to prepare fourstates.
We need to put diagonal polarization on the
input. Depending on the applied voltage we will
have 0, λ/4, λ/2 and 3λ/4 plate oriented at 45
degree to the polarization.
[M. Jofre, A. Gardelein, G. Anzolin, G. MolinaTerriza, J. P. Torres, M. W. Mitchell, and V.
Pruneri, "100 MHz Amplitude and Polarization
Modulated Optical Source for Free-Space
Quantum Key Distribution at 850 nm," J.
Lightwave Technol. 28, 2572-2578 (2010).]
The problem is that LiNbO3 has high
polarization mode dispersion and polarization
dependent loss.
Applied voltage makes LiNbO3
phase modulator a λ/x plate
λ/4
λ/2
0
3λ/4
• The Polarization dependent loss can be
compensated with the polarization change
• Polarization mode dispersion requires some
compensation element which makes optical
scheme much more expensive
43
44. Two identical crystals allows to restore original states
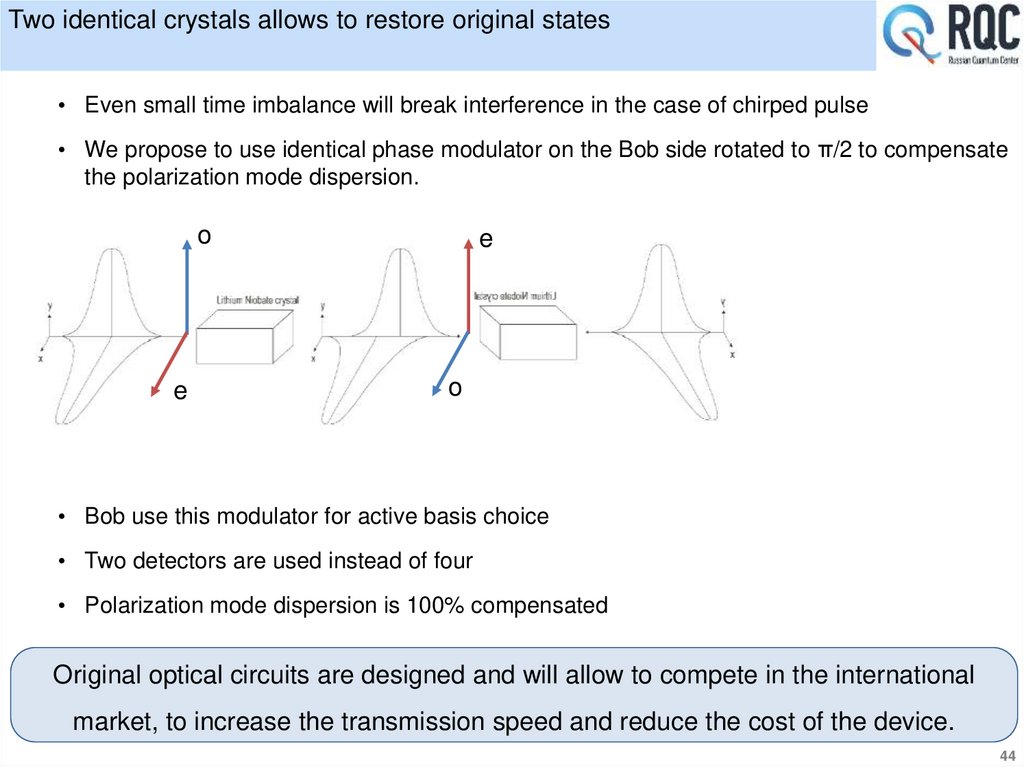
• Even small time imbalance will break interference in the case of chirped pulse• We propose to use identical phase modulator on the Bob side rotated to π/2 to compensate
the polarization mode dispersion.
o
e
e
o
• Bob use this modulator for active basis choice
• Two detectors are used instead of four
• Polarization mode dispersion is 100% compensated
Original optical circuits are designed and will allow to compete in the international
market, to increase the transmission speed and reduce the cost of the device.
44
45. Optical scheme becomes very simple
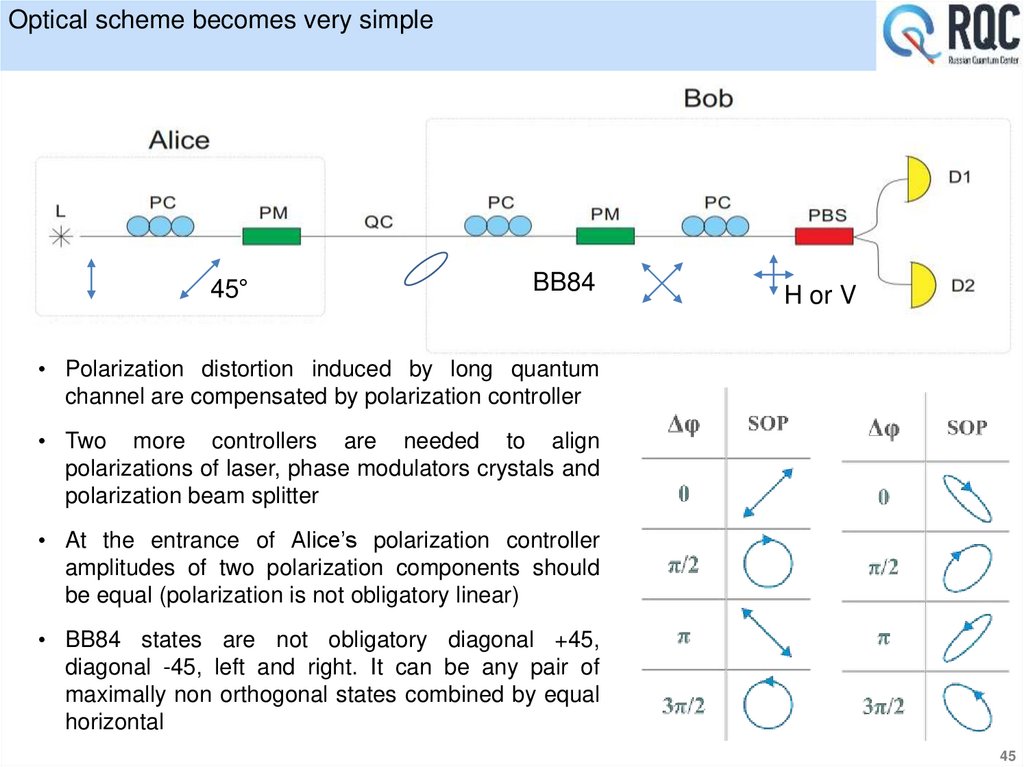
45°BB84
H or V
• Polarization distortion induced by long quantum
channel are compensated by polarization controller
• Two more controllers are needed to align
polarizations of laser, phase modulators crystals and
polarization beam splitter
• At the entrance of Alice’s polarization controller
amplitudes of two polarization components should
be equal (polarization is not obligatory linear)
• BB84 states are not obligatory diagonal +45,
diagonal -45, left and right. It can be any pair of
maximally non orthogonal states combined by equal
horizontal
45
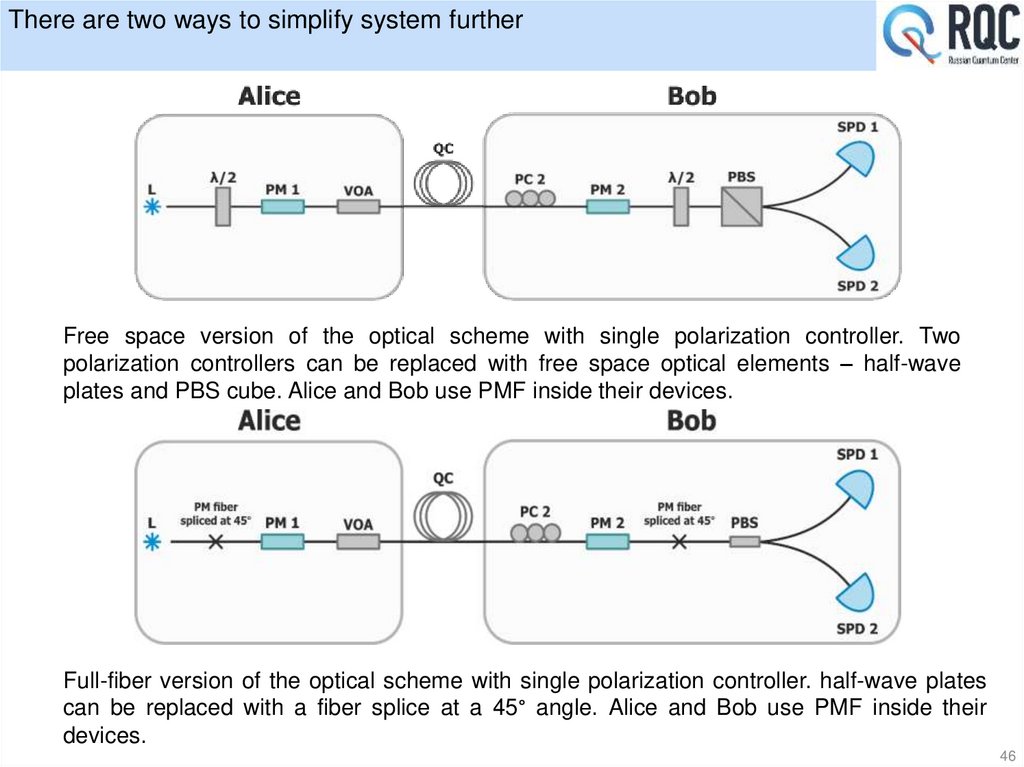
46. There are two ways to simplify system further
Free space version of the optical scheme with single polarization controller. Twopolarization controllers can be replaced with free space optical elements – half-wave
plates and PBS cube. Alice and Bob use PMF inside their devices.
Full-fiber version of the optical scheme with single polarization controller. half-wave plates
can be replaced with a fiber splice at a 45° angle. Alice and Bob use PMF inside their
devices.
46
47. The scheme is equivalent to other BB84 implementation
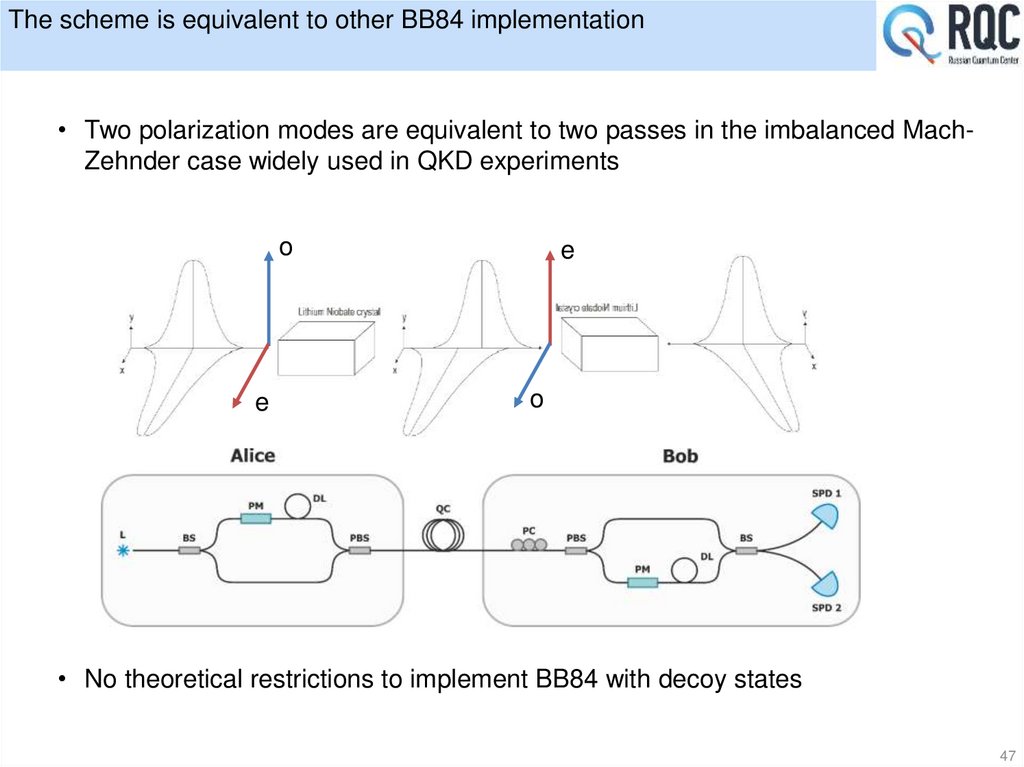
• Two polarization modes are equivalent to two passes in the imbalanced MachZehnder case widely used in QKD experimentso
e
e
o
• No theoretical restrictions to implement BB84 with decoy states
47
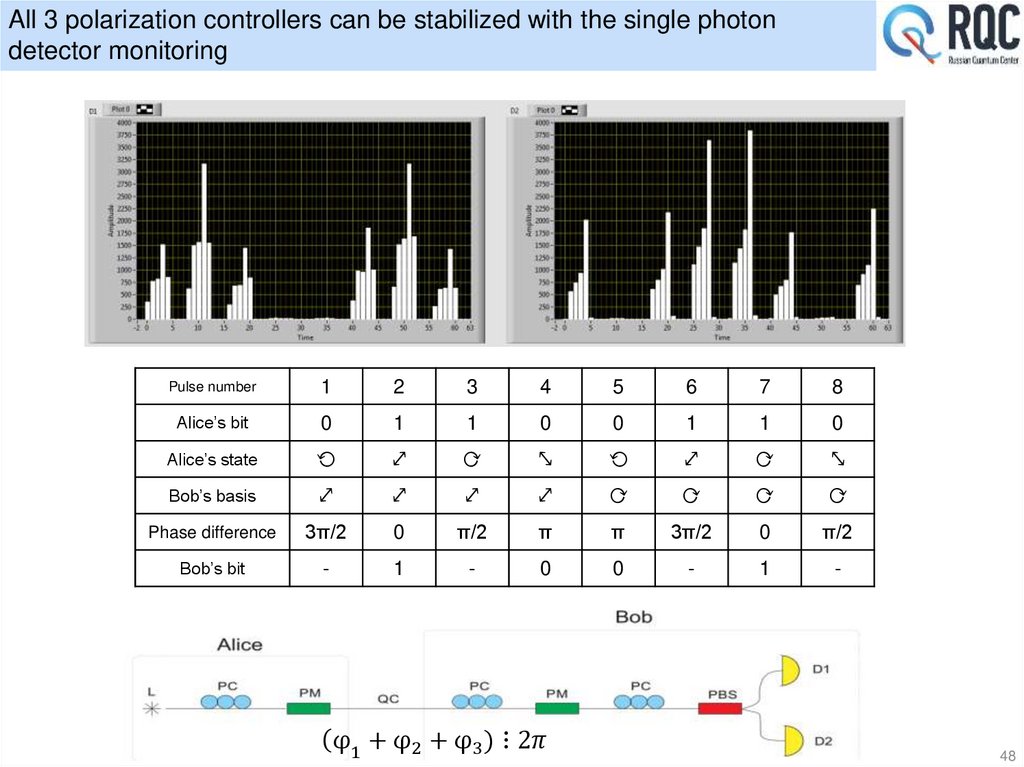
48. All 3 polarization controllers can be stabilized with the single photon detector monitoring
Pulse number1
2
3
4
5
6
7
8
Alice’s bit
0
1
1
0
0
1
1
0
Alice’s state
⟲
⤢
⟳
⤡
⟲
⤢
⟳
⤡
Bob’s basis
⤢
⤢
⤢
⤢
⟳
⟳
⟳
⟳
Phase difference
3π/2
0
π/2
π
π
3π/2
0
π/2
Bob’s bit
-
1
-
0
0
-
1
-
ሺφ1 + φ2 + φ3 ) ⋮ 2


![The “bomb” paradox [A. Elitzur and L. Vaidman (1993)] The “bomb” paradox [A. Elitzur and L. Vaidman (1993)]](https://cf5.ppt-online.org/files5/slide/5/5368RK0tiTWFGJ2pCsUB7OAHIjNl9qD4kEzSP1/slide-5.jpg)
![The “bomb” paradox [A. Elitzur and L. Vaidman (1993)] The “bomb” paradox [A. Elitzur and L. Vaidman (1993)]](https://cf5.ppt-online.org/files5/slide/5/5368RK0tiTWFGJ2pCsUB7OAHIjNl9qD4kEzSP1/slide-6.jpg)
![The “bomb” paradox [A. Elitzur and L. Vaidman (1993)] The “bomb” paradox [A. Elitzur and L. Vaidman (1993)]](https://cf5.ppt-online.org/files5/slide/5/5368RK0tiTWFGJ2pCsUB7OAHIjNl9qD4kEzSP1/slide-7.jpg)