Похожие презентации:
X.509 at the University of Michigan. Project Goals
1. X.509 at the University of Michigan
CIC-RPG Meeting June 7, 1999Kevin Coffman (kwc@umich.edu)
Bill Doster (billdo@umich.edu)
2. Project Goals
Transparent Web AuthenticationEliminate password prompts
Lotus Notes Authentication
Position for inter-institution
Authentication
3. Non-Goals
Not a complete PKINot to be used for document signing
Not to be used for encryption
Not a complete replacement of the
current cookie method
4. Why X.509?
An accepted standardApplication support out of the box
– Web servers, web browsers, directory
servers, IMAP servers, etc.
Allows the possibility for inter-institution
authentication
No need for N²-1 cross-realm trusts
5. Description
Use short-term (approximately 1 day)certificates - “Junk Keys”
Obtain certificates securely
For Authentication ONLY!
Use OpenSSL for creating and signing
certificates
6. Why “Junk Keys”?
Revocation becomes a non-issuePrivate Key storage is less an issue
Certificate publication for sharing is not
necessary
Certificate management is less critical
7. Drawbacks
Cannot be used for signing orencryption
Not possible to verify certificate via
LDAP
8. Options for obtaining the CA’s Certificate
Bake it into browsers we distributeVia a web interface using SSL and
Verisign Certificate
Store it in the file-system
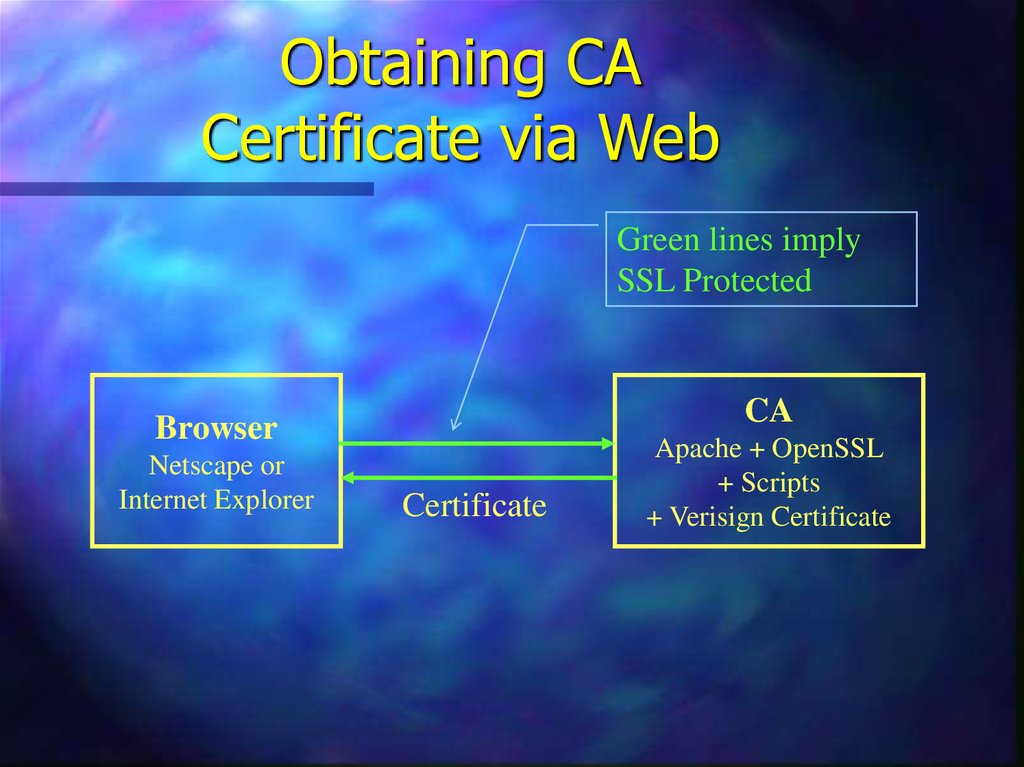
9. Obtaining CA Certificate via Web
Green lines implySSL Protected
CA
Browser
Netscape or
Internet Explorer
Certificate
Apache + OpenSSL
+ Scripts
+ Verisign Certificate
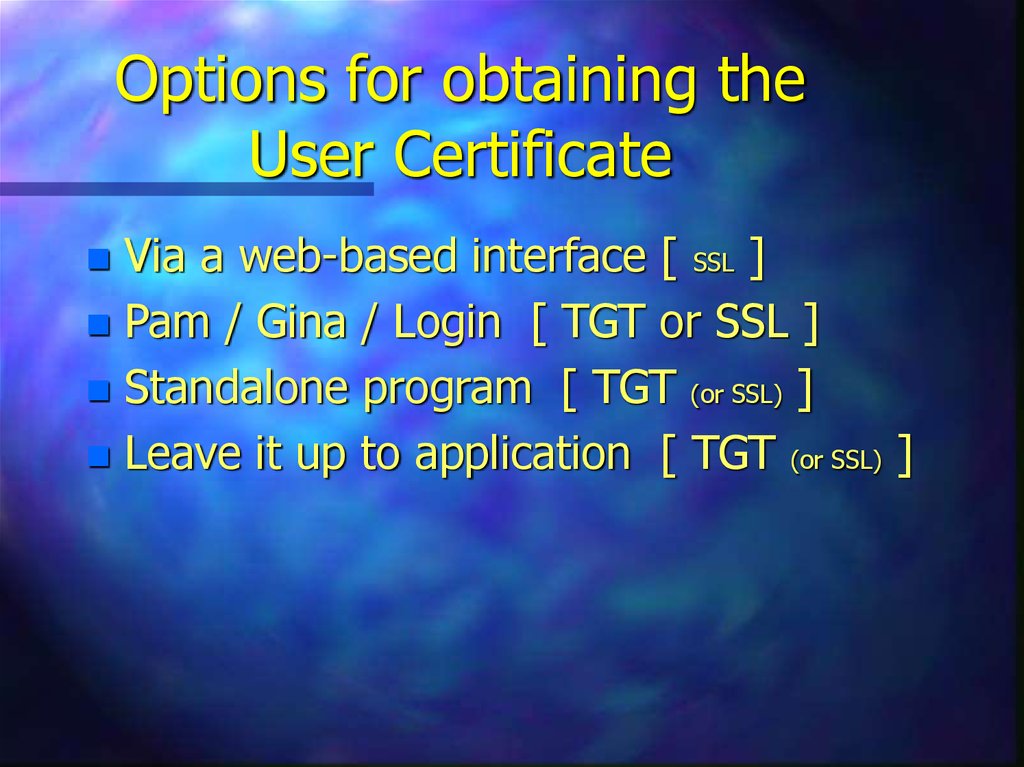
10. Options for obtaining the User Certificate
Via a web-based interface [ SSL ]Pam / Gina / Login [ TGT or SSL ]
Standalone program [ TGT (or SSL) ]
Leave it up to application [ TGT (or SSL) ]
11. Obtaining User Certificate via Web (Netscape)
Web server / CANetscape Browser
User selects URL
ID and password??
ID and password
Verify identity
keyGen
Generate key pair
and store keys
Public Key
Signed Certificate
Store Certificate
• Lookup full name
• Lookup Entity ID
• Generate and
Sign Certificate
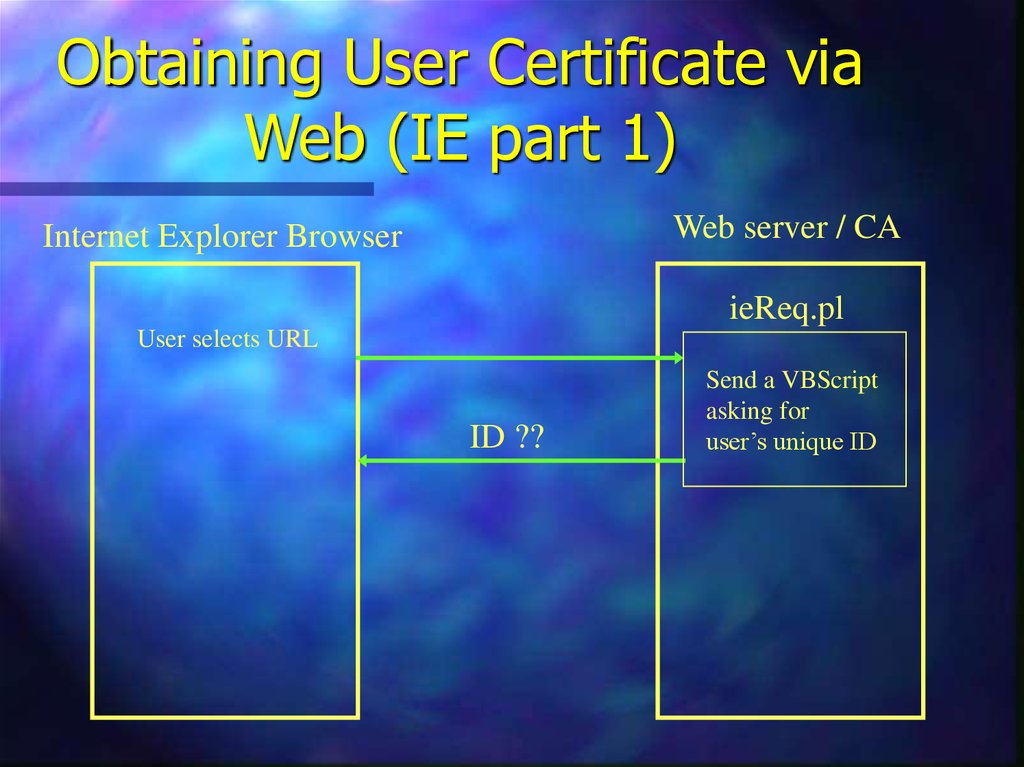
12. Obtaining User Certificate via Web (IE part 1)
Web server / CAInternet Explorer Browser
ieReq.pl
User selects URL
ID ??
Send a VBScript
asking for
user’s unique ID
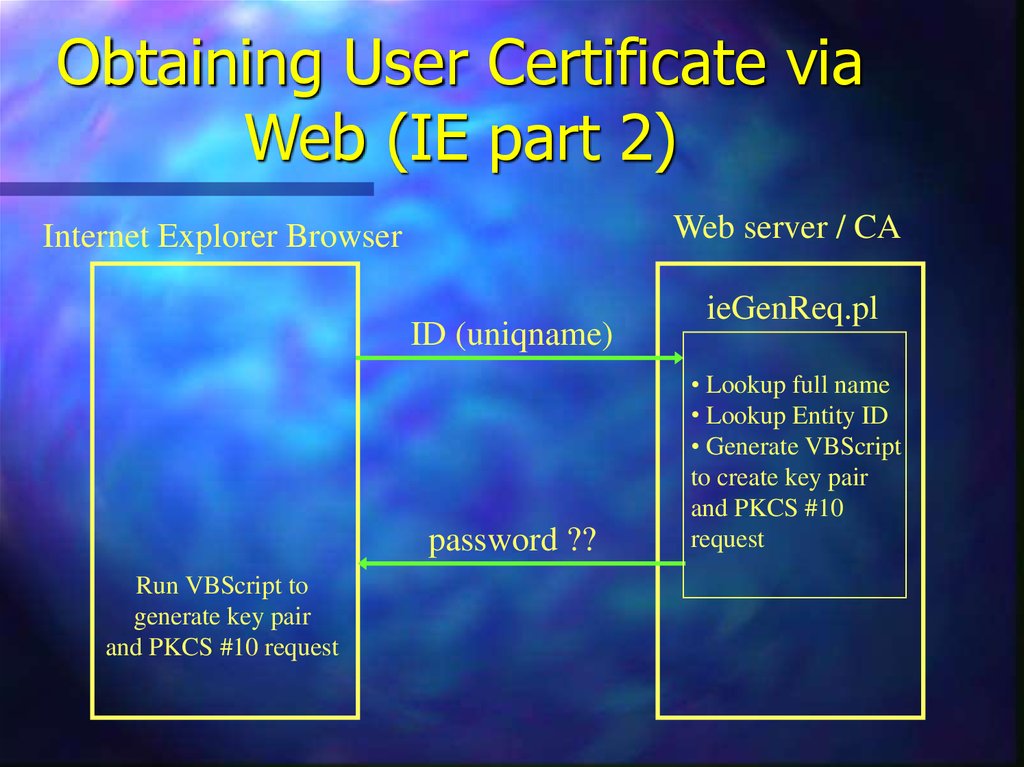
13. Obtaining User Certificate via Web (IE part 2)
Web server / CAInternet Explorer Browser
ID (uniqname)
password ??
Run VBScript to
generate key pair
and PKCS #10 request
ieGenReq.pl
• Lookup full name
• Lookup Entity ID
• Generate VBScript
to create key pair
and PKCS #10
request
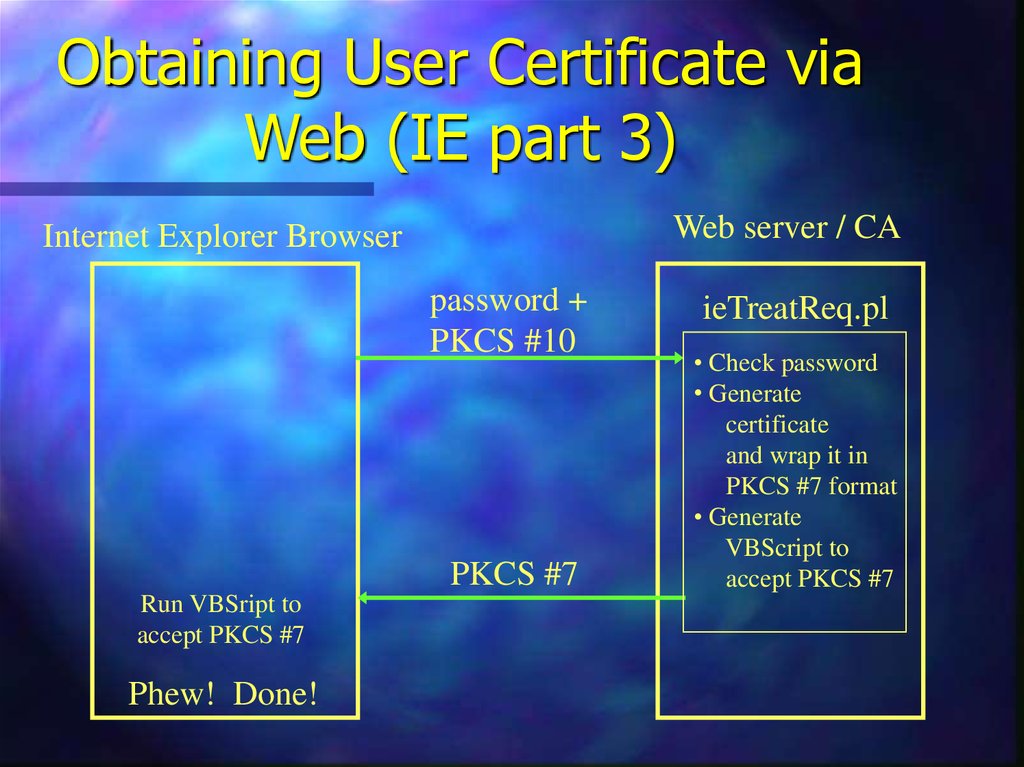
14. Obtaining User Certificate via Web (IE part 3)
Web server / CAInternet Explorer Browser
password +
PKCS #10
PKCS #7
Run VBSript to
accept PKCS #7
Phew! Done!
ieTreatReq.pl
• Check password
• Generate
certificate
and wrap it in
PKCS #7 format
• Generate
VBScript to
accept PKCS #7
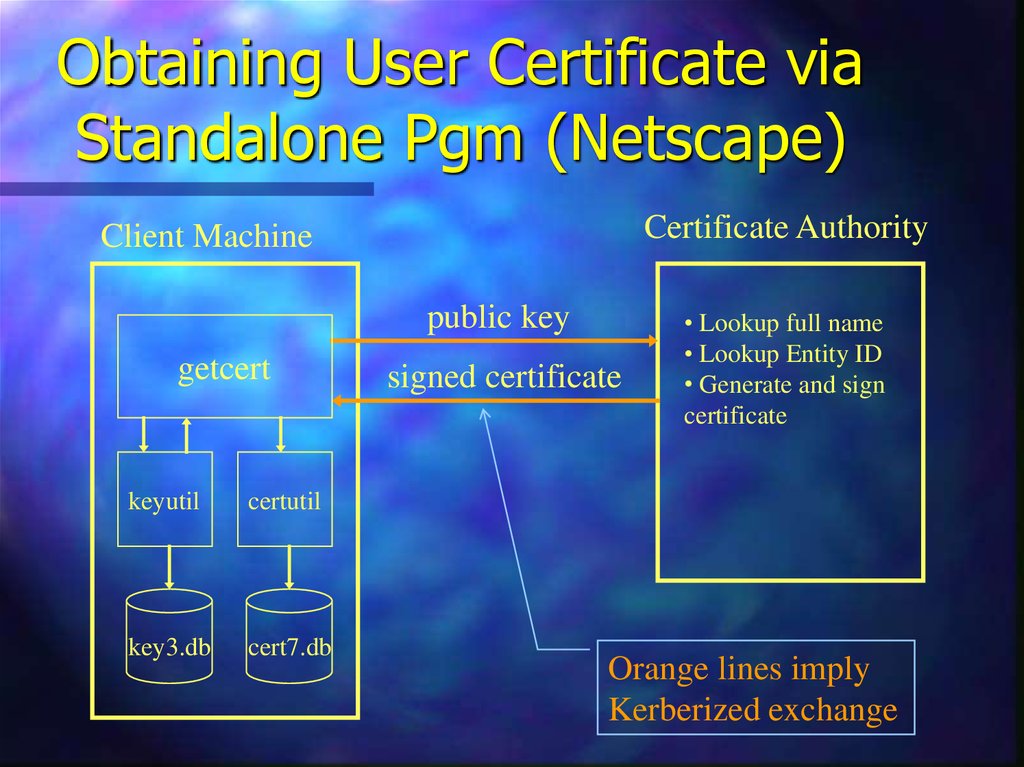
15. Obtaining User Certificate via Standalone Pgm (Netscape)
Certificate AuthorityClient Machine
public key
getcert
keyutil
certutil
key3.db
cert7.db
signed certificate
• Lookup full name
• Lookup Entity ID
• Generate and sign
certificate
Orange lines imply
Kerberized exchange
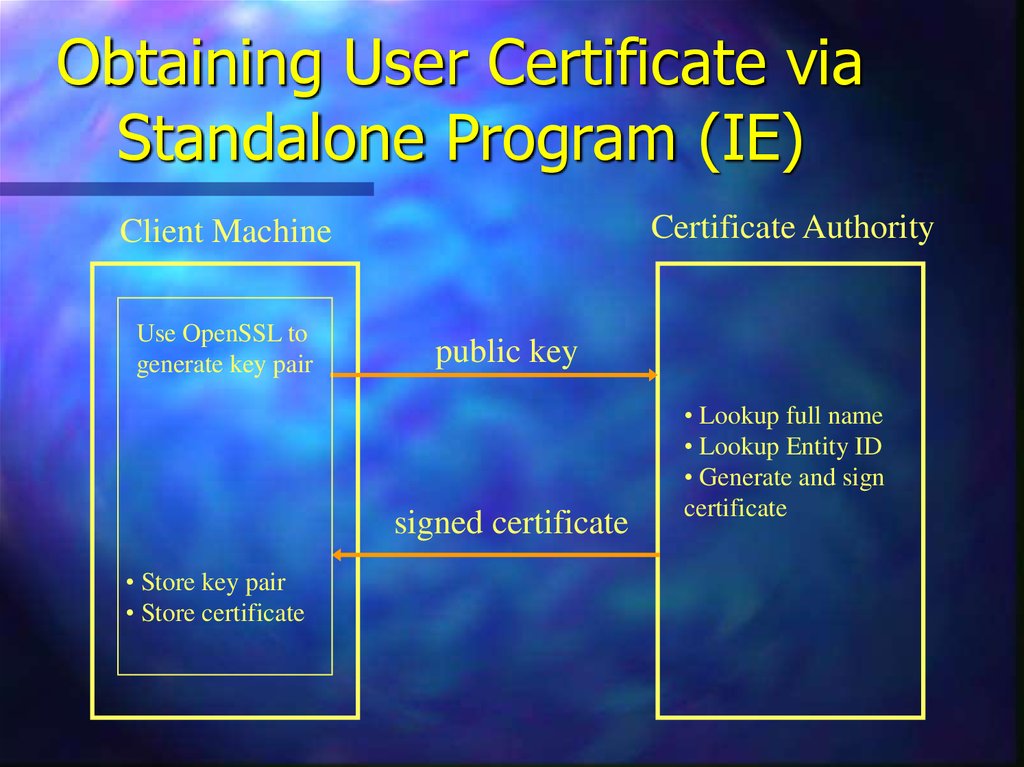
16. Obtaining User Certificate via Standalone Program (IE)
Certificate AuthorityClient Machine
Use OpenSSL to
generate key pair
public key
signed certificate
• Store key pair
• Store certificate
• Lookup full name
• Lookup Entity ID
• Generate and sign
certificate
17. Storing the Certificates
How to destroy the certificates afteruse?
NT 4.0 w/SP3 and later has special
storage classes that lives only for the
life of a login
Make use of Kerberos credential
storage?
Internet Explorer vs. Netscape
18. Problems
Documentation - Flood or DroughtMacintosh support lags other platforms
19. Current Status
Internet Explorer (Windows only) lookspromising
Netscape (Windows, Solaris) do-able
but not clean
Macintosh support does not currently
look promising for either browser
20. References
This presentation:– http://www.citi.umich.edu/u/kwc/Presentations/X509June1999
OpenSSL:
– http://www.openssl.org/
Netscape Security Services:
– http://home.netscape.com/nss/v1.2/index.html
Microsoft CryptoAPI:
– http://www.microsoft.com/security/tech/CryptoAPI/default.asp














 Информатика
Информатика Образование
Образование








