Похожие презентации:
Module 1 - Security Threat Landscape_0617
1. Securing Windows Server 2016 Module 1: Security Threat Landscape
2.
Objectives3. Objectives
Lessons4. Lessons
Security Threat LandscapeLesson 1: Security, attacks and
threats
Section: Introduction
5. Security Threat Landscape
Security is a Top Priority for ITIncreasing
incidents
Multiple
motivations
Bigger risk
6.
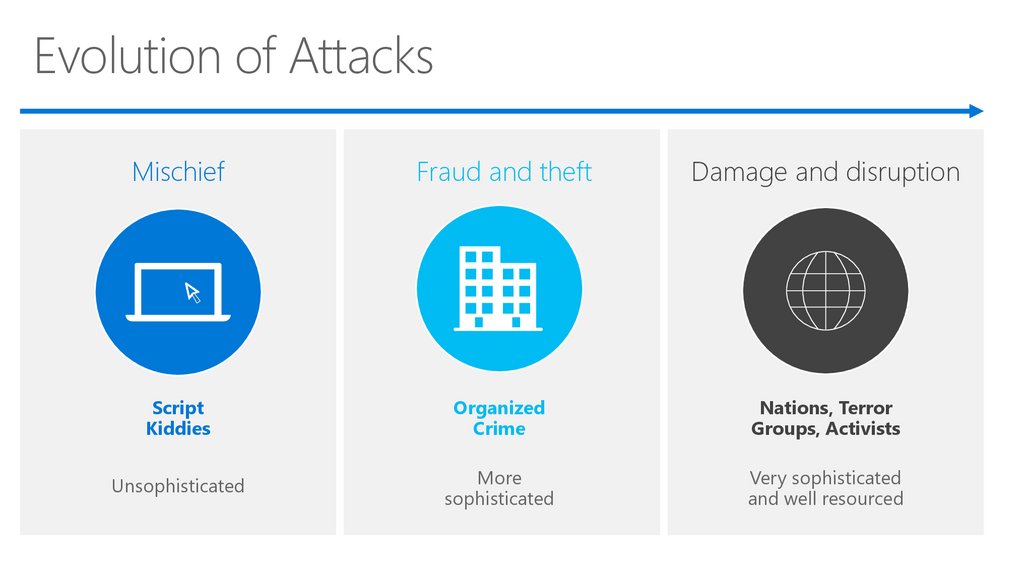
Evolution of AttacksMischief
Fraud and theft
Damage and disruption
Script
Kiddies
Organized
Crime
Nations, Terror
Groups, Activists
Unsophisticated
More
sophisticated
Very sophisticated
and well resourced
7. Evolution of Attacks
“Cyber security is a CEO issue.”-McKinsey
$ 3.0
Tr i l l i o n
Impact of lost productivity
and growth
$4
Million
Average cost of a data breach
(15% YoY increase)
$ 500
Corporate liability
coverage.
Cyber threats are a m a t e r i a l r i s k to your business
Source: McKinsey, Ponemon Institute, Verizon
Million
8.
AfterBefore
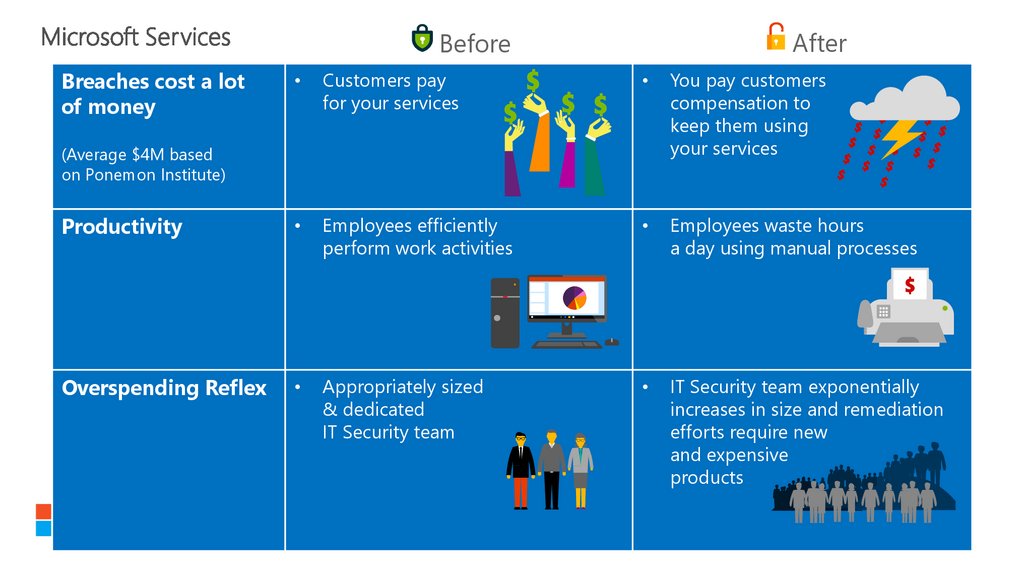
Breaches cost a lot
of money
Customers pay
for your services
$
$
$ $
You pay customers
compensation to
keep them using
your services
Employees waste hours
a day using manual processes
(Average $4M based
on Ponemon Institute)
Productivity
Employees efficiently
perform work activities
$
Overspending Reflex
Appropriately sized
& dedicated
IT Security team
IT Security team exponentially
increases in size and remediation
efforts require new
and expensive
products
9.
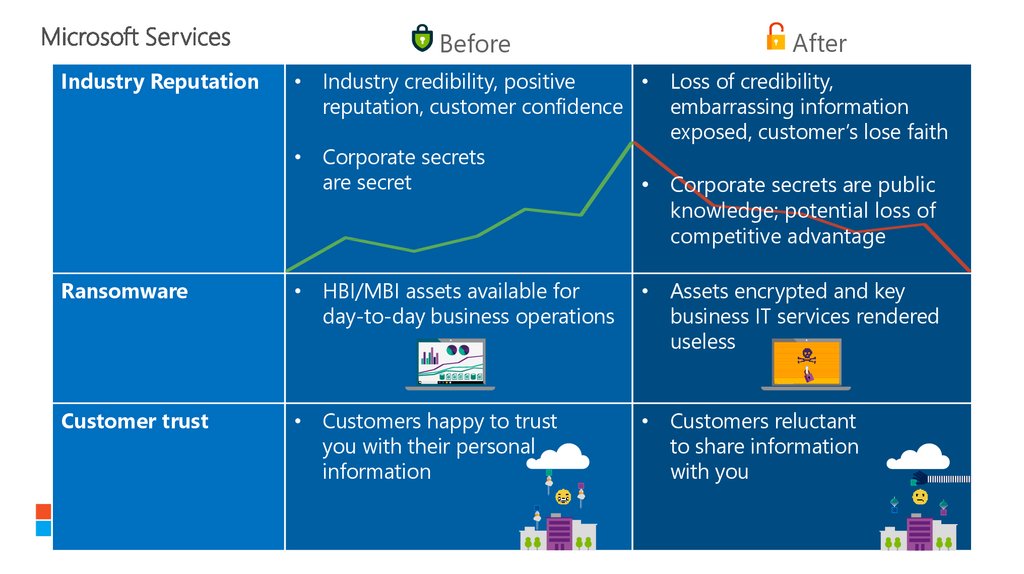
BeforeAfter
Industry Reputation
• Industry credibility, positive
• Loss of credibility,
reputation, customer confidence
embarrassing information
exposed, customer’s lose faith
• Corporate secrets
are secret
• Corporate secrets are public
knowledge; potential loss of
competitive advantage
Ransomware
• HBI/MBI assets available for
day-to-day business operations
• Assets encrypted and key
business IT services rendered
useless
Customer trust
• Customers happy to trust
you with their personal
information
• Customers reluctant
to share information
with you
10.
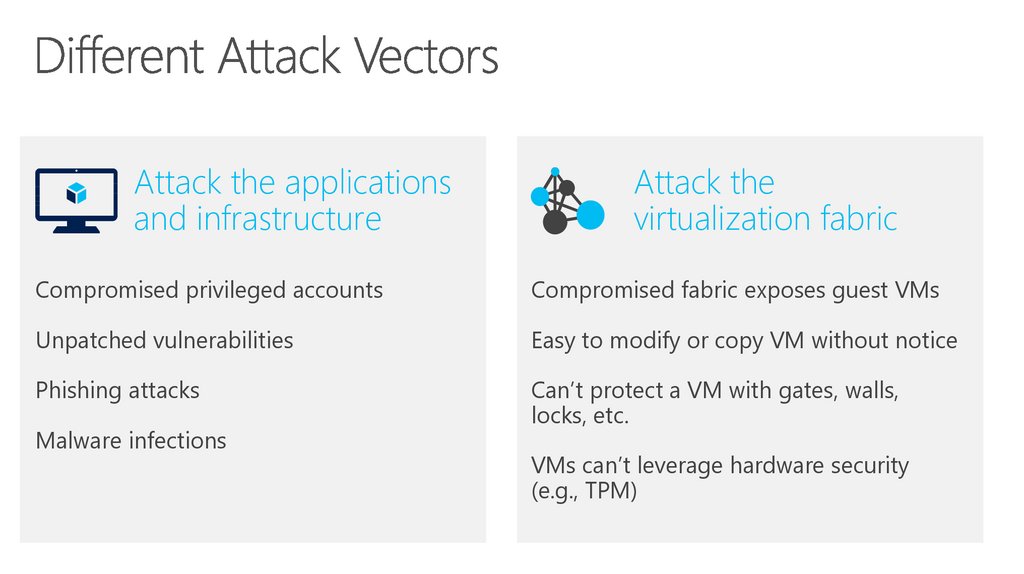
Attack the applicationsand infrastructure
Attack the
virtualization fabric
Compromised privileged accounts
Compromised fabric exposes guest VMs
Unpatched vulnerabilities
Easy to modify or copy VM without notice
Phishing attacks
Can’t protect a VM with gates, walls,
locks, etc.
Malware infections
VMs can’t leverage hardware security
(e.g., TPM)
11. Different Attack Vectors
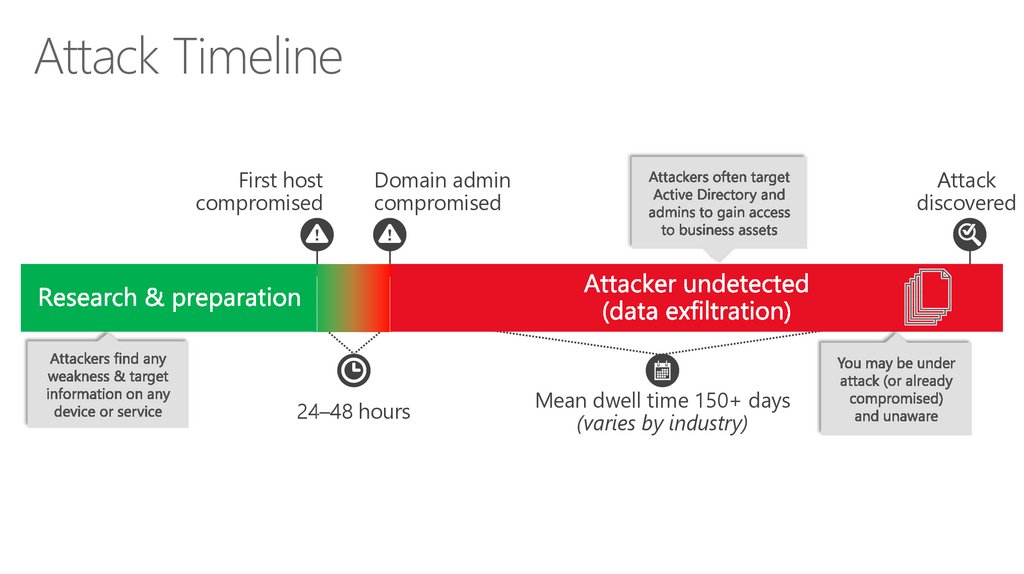
Attack TimelineFirst host
compromised
Domain admin
compromised
24–48 hours
Attack
discovered
Mean dwell time 150+ days
(varies by industry)
12. Attack Timeline
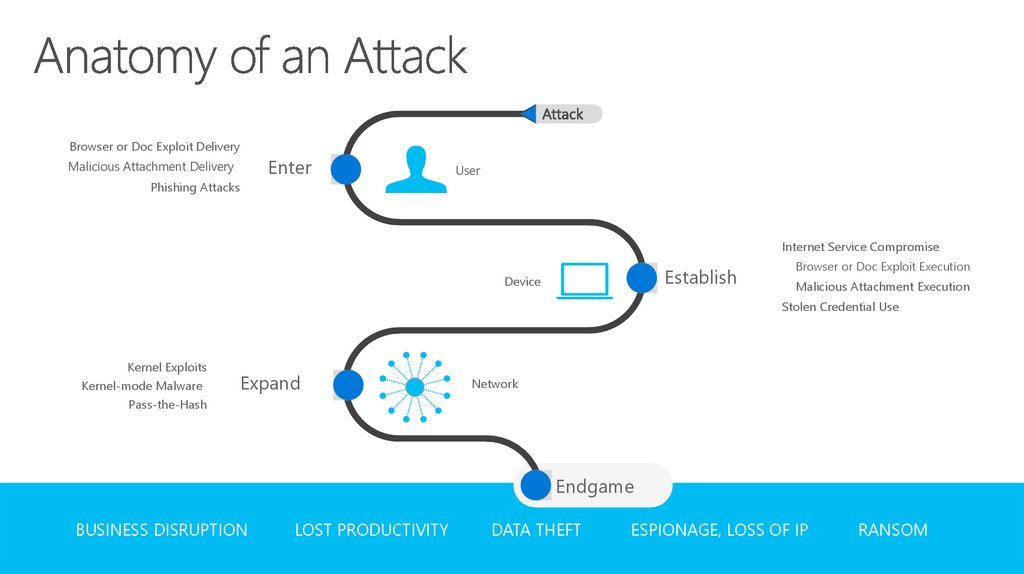
Browser or Doc Exploit DeliveryEnter
Malicious Attachment Delivery
User
Phishing Attacks
Internet Service Compromise
Establish
Device
Browser or Doc Exploit Execution
Malicious Attachment Execution
Stolen Credential Use
Kernel Exploits
Kernel-mode Malware
Expand
Network
Pass-the-Hash
Endgame
BUSINESS DISRUPTION
LOST PRODUCTIVITY
DATA THEFT
ESPIONAGE, LOSS OF IP
RANSOM
13. Anatomy of an Attack
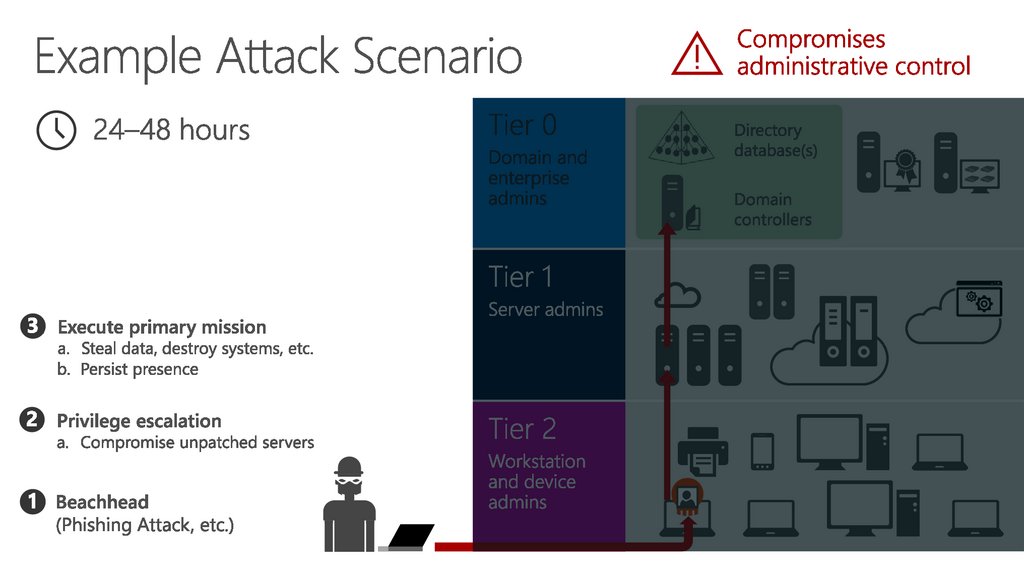
14. Example Attack Scenario
Schoolboard50 Employees
300 Students
Public funds
Construction
4,000 Employees
$30 millions YR
Private funds
Energy
95,000 Employees
$5 billions YR
Private funds
Shareholders
15.
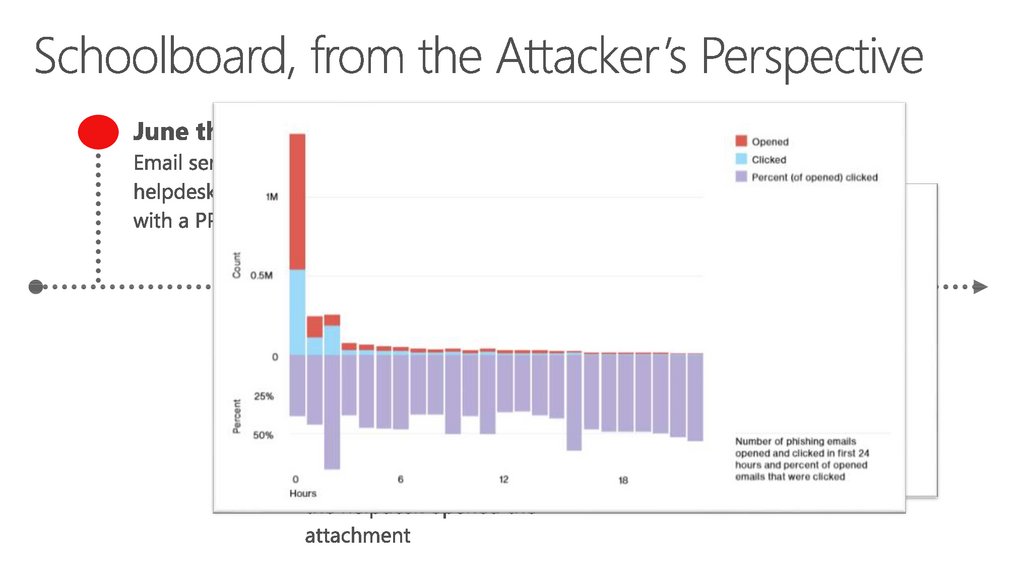
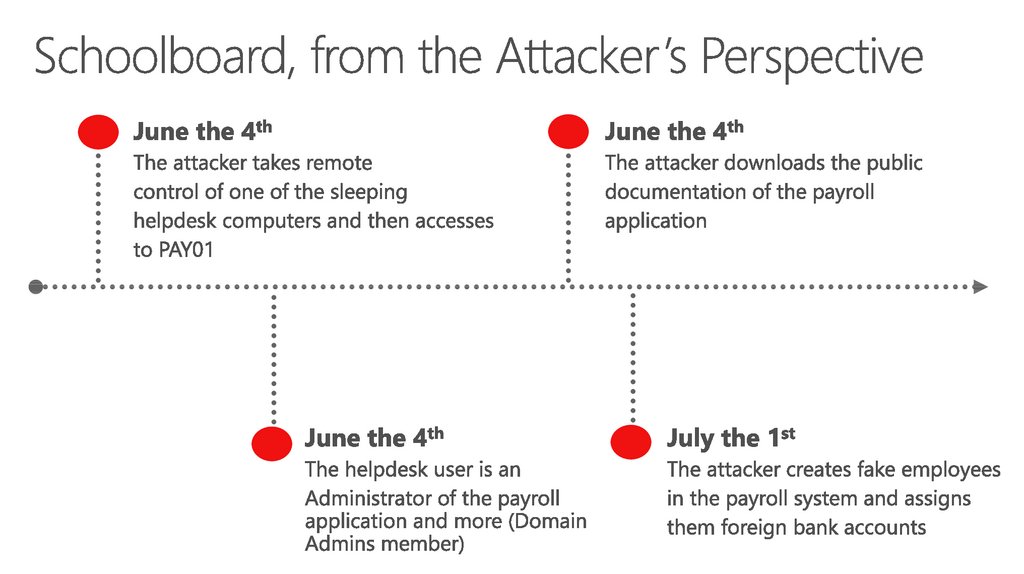
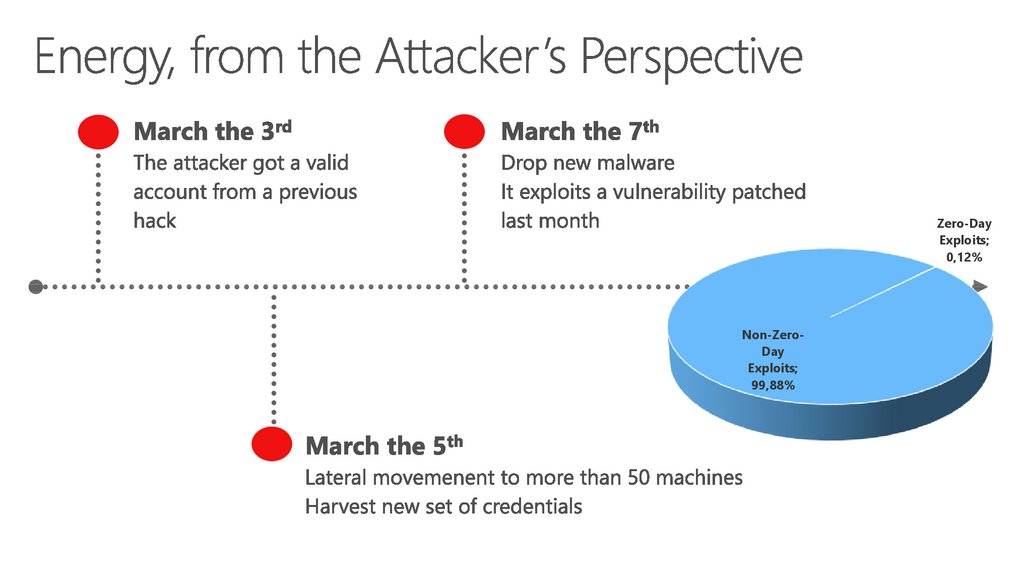
16. Schoolboard, from the Attacker’s Perspective
17. Schoolboard, from the Attacker’s Perspective
18. Schoolboard, from the Attacker’s Perspective
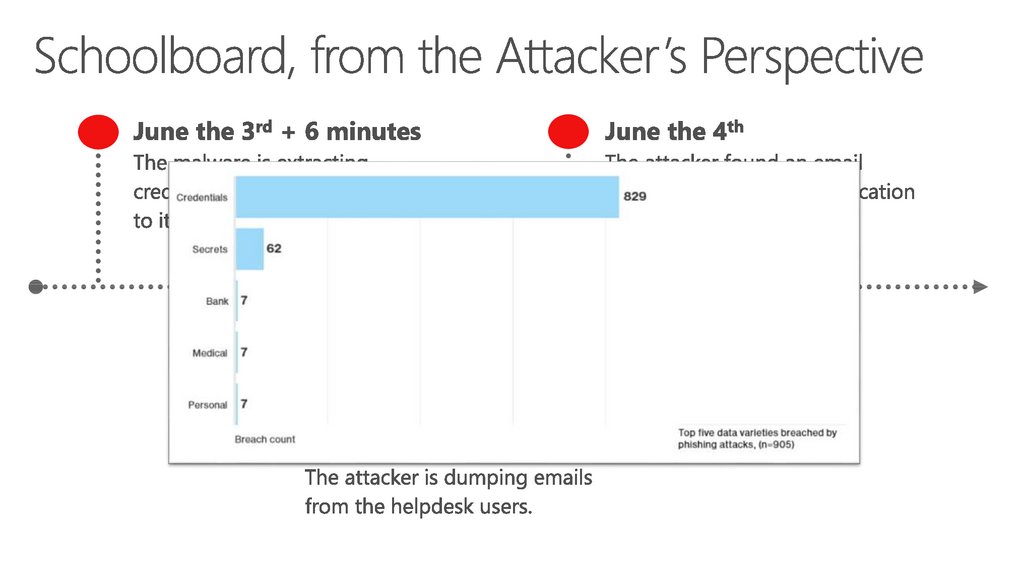
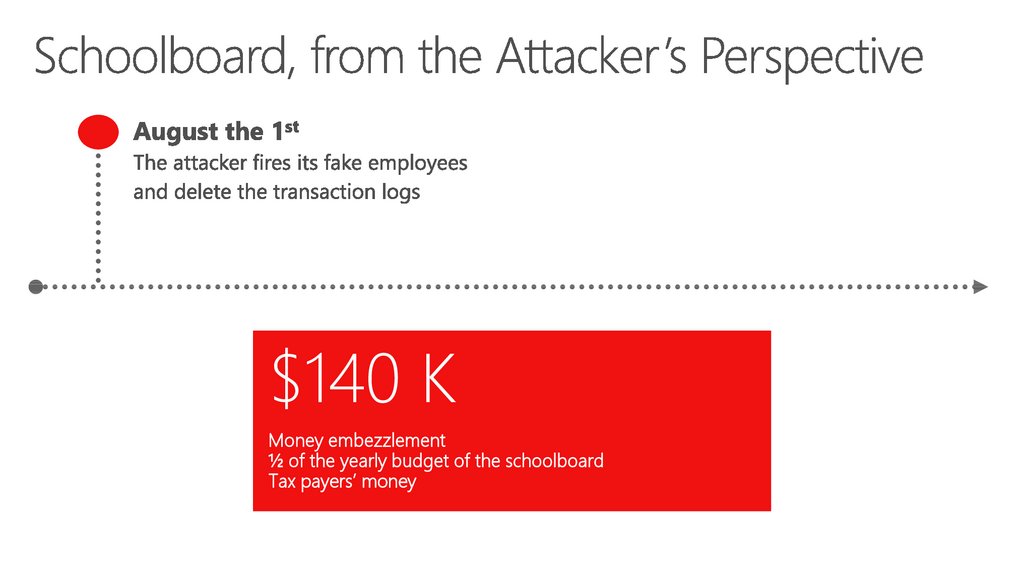
$140 KMoney embezzlement
½ of the yearly budget of the schoolboard
Tax payers’ money
19. Schoolboard, from the Attacker’s Perspective
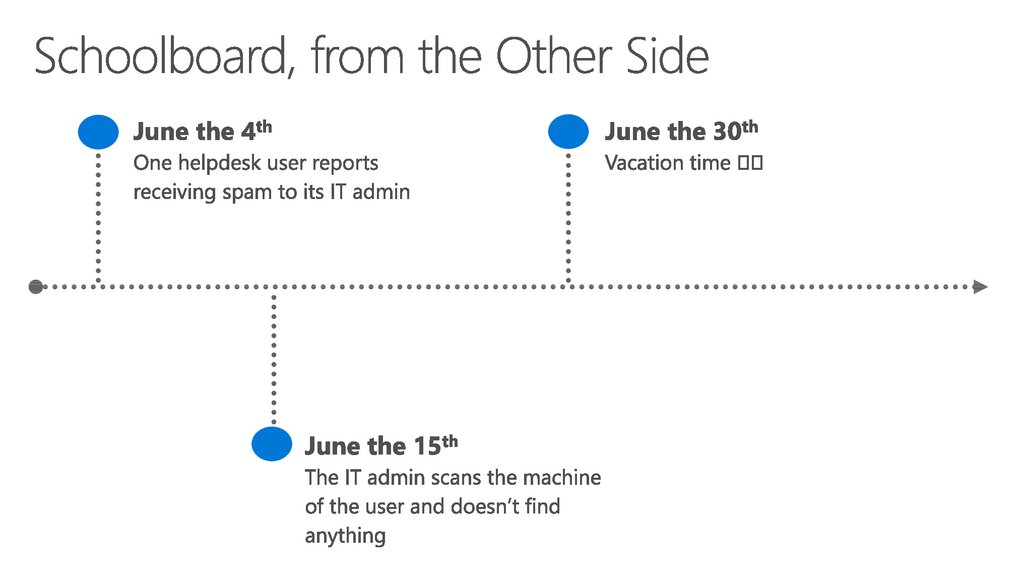
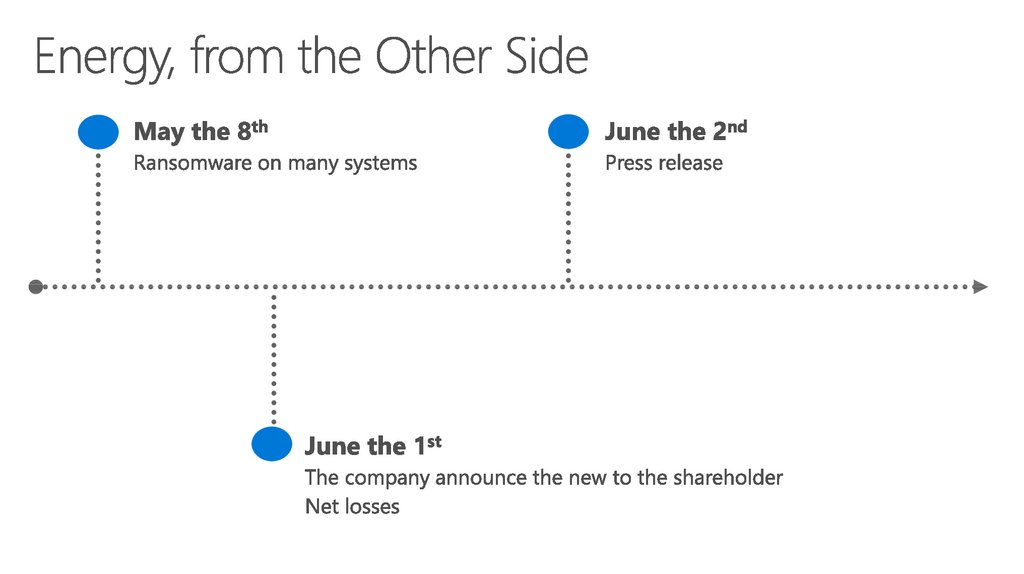
20. Schoolboard, from the Other Side
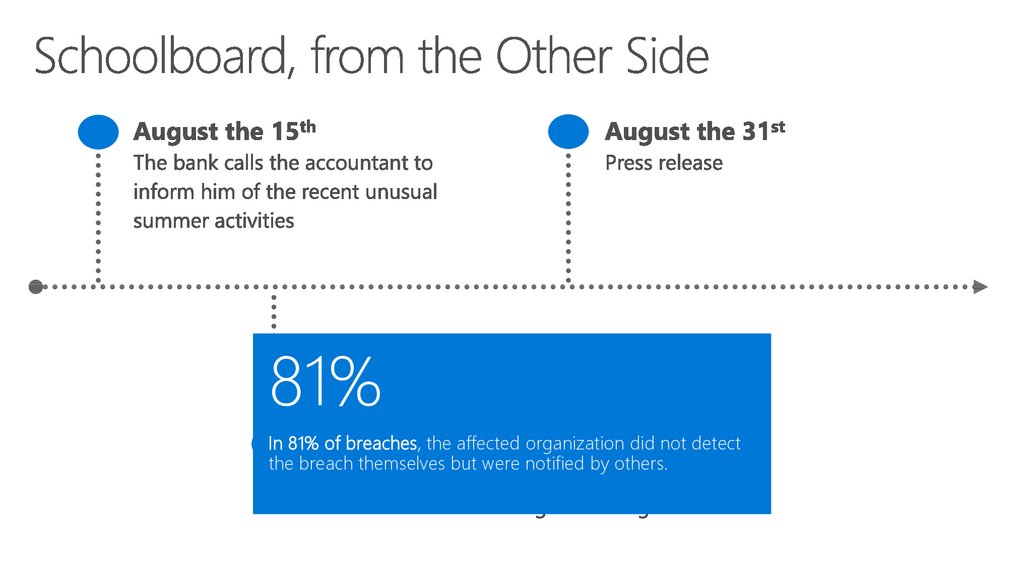
81%In 81% of breaches, the affected organization did not detect
the breach themselves but were notified by others.
21. Schoolboard, from the Other Side
22. What went wrong?
Construction4,000 Employees
$30 millions YR
Private funds
23.
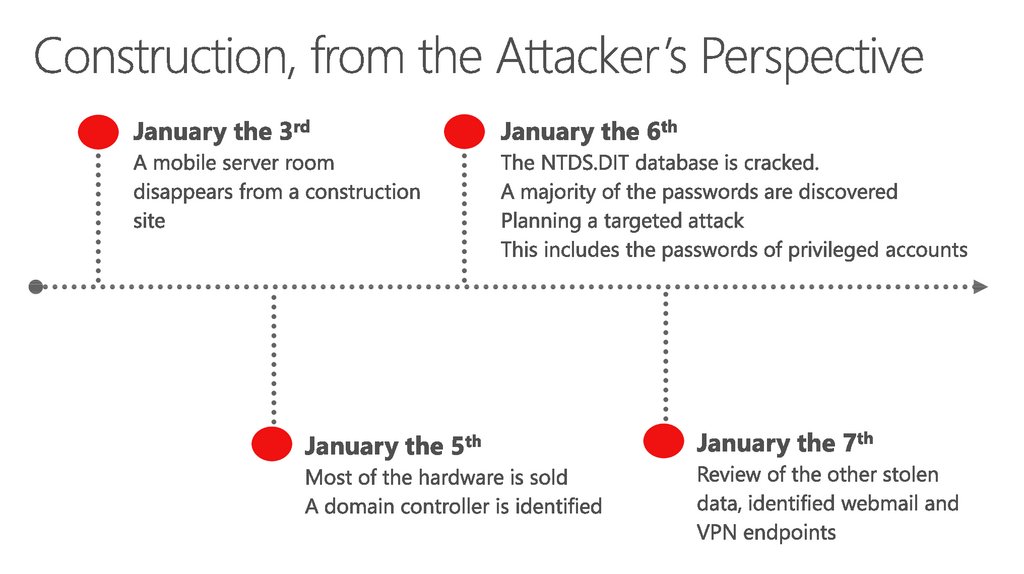
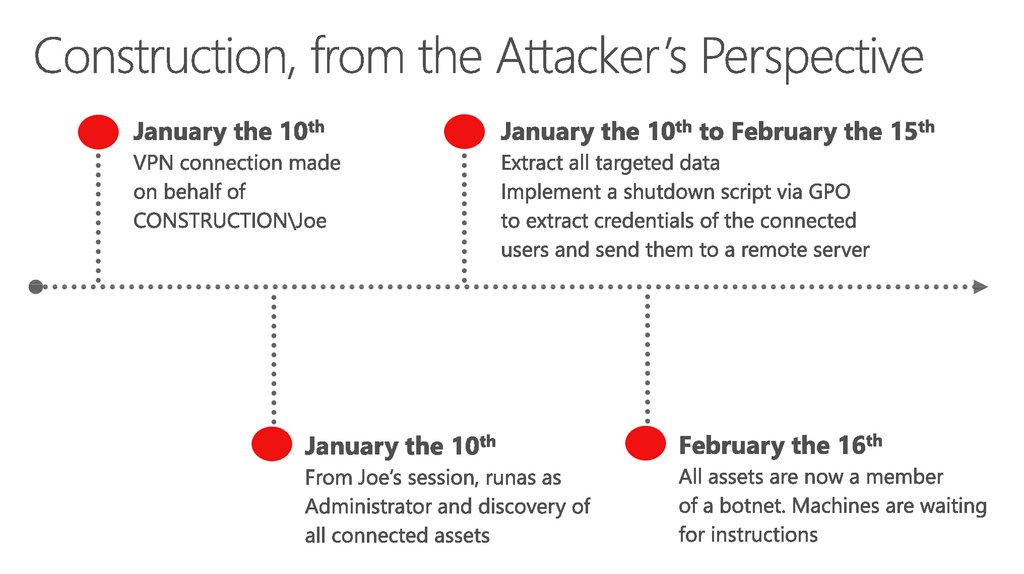
24. Construction, from the Attacker’s Perspective
25. Construction, from the Attacker’s Perspective
26. Construction, from the Attacker’s Perspective
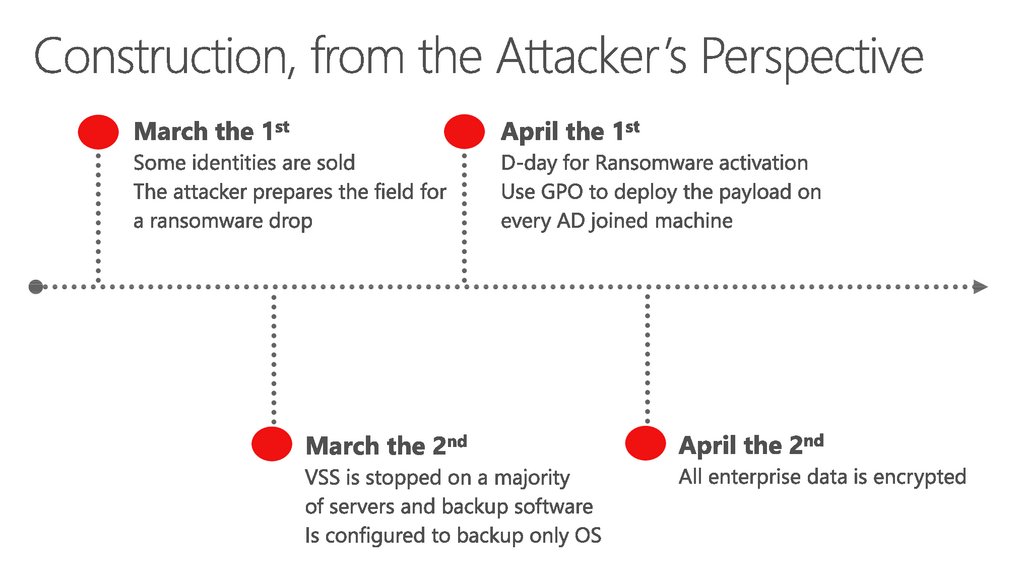
$220K ransomSome old data has been restored
The attacker is still present on the network
$2M business impact
Lost work / Cannot respond to offers
27. Construction, from the Attacker’s Perspective
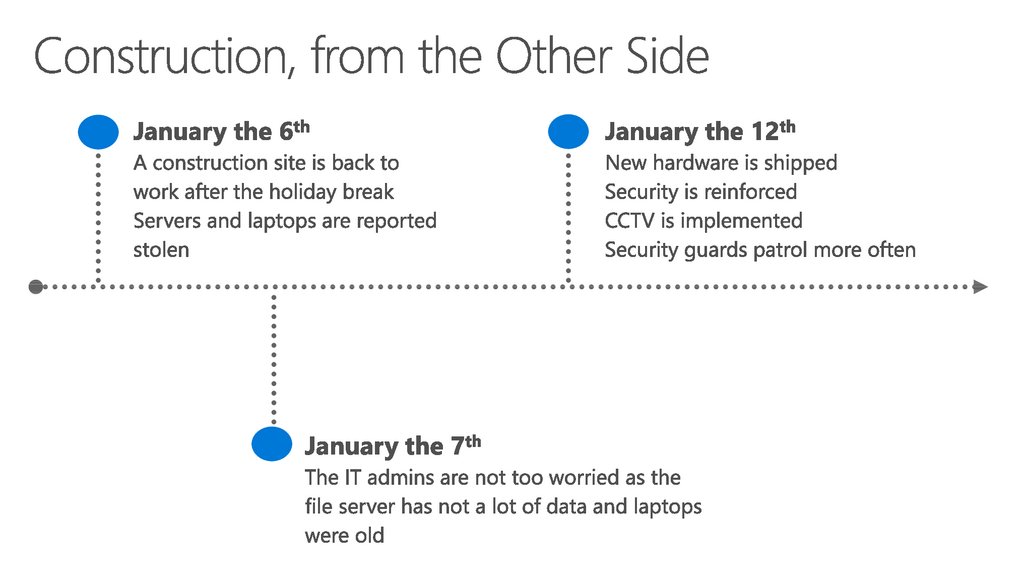
28. Construction, from the Other Side
~200 daysMost of attacks go undetected for around a year (on
average), leaving organizations vulnerable to ongoing loss
and damage.
29. Construction, from the Other Side
30. What went wrong?
EnergyNetworks
95,000 Employees
Corporate
network
$5 billions
YR in
Closed
network
Private funds
production
sites
Shareholders
31.
Exploit Breakdown H1 2011Zero-Day
Exploits;
0,12%
Non-ZeroDay
Exploits;
99,88%
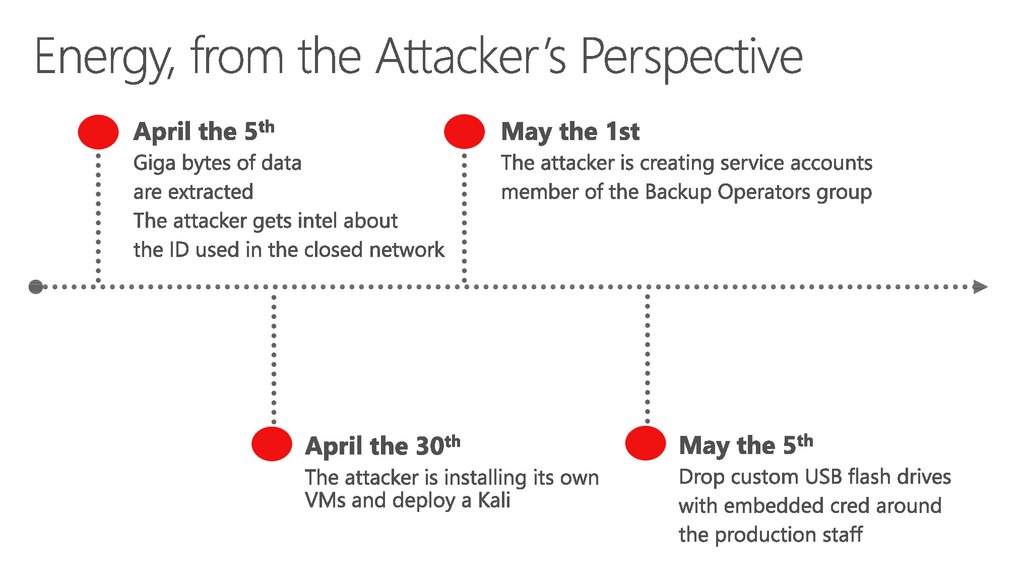
32. Energy, from the Attacker’s Perspective
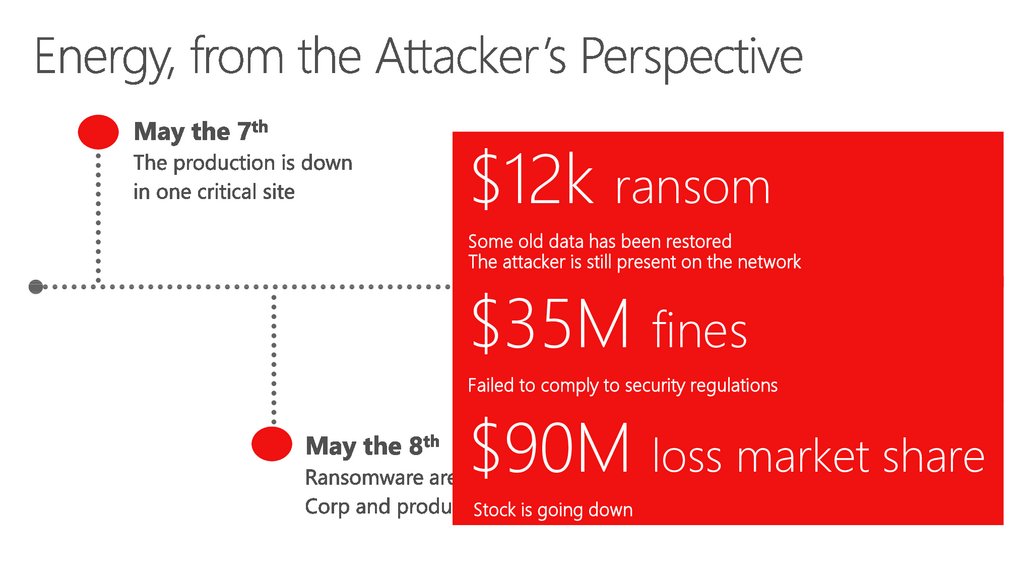
33. Energy, from the Attacker’s Perspective
$12k ransomSome old data has been restored
The attacker is still present on the network
$35M fines
Failed to comply to security regulations
$90M loss market share
Stock is going down
34. Energy, from the Attacker’s Perspective
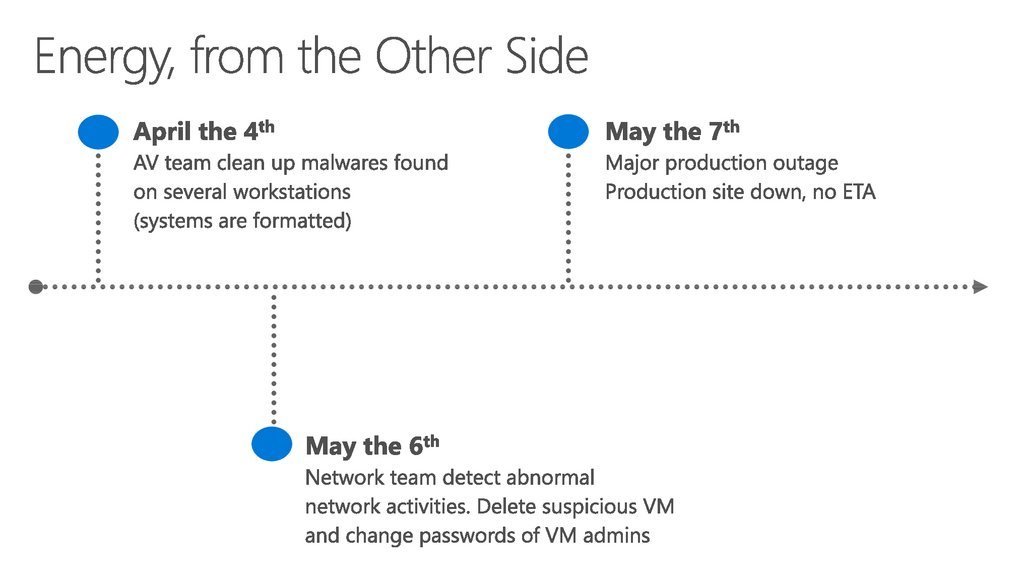
35. Energy, from the Other Side
36. Energy, from the Other Side
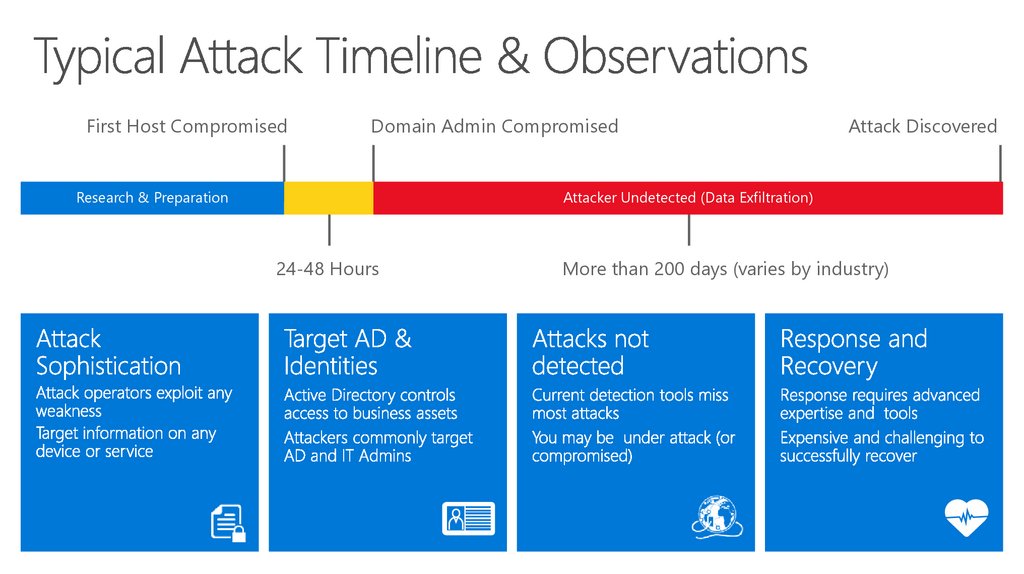
First Host CompromisedDomain Admin Compromised
Research & Preparation
Attack Discovered
Attacker Undetected (Data Exfiltration)
24-48 Hours
More than 200 days (varies by industry)
37. Typical Attack Timeline & Observations
Cost of an attackThe cost of these attacks to the global economy, and to an individual company, is
significant. It is estimated that the total potential cost of cybercrime to the global
economy is $500 billion. The average cost of a data breach to a company is estimated
at $3.5 million. However, the cumulative impact as a result from damage to brand
reputation, loss of confidential data, and intellectual property is just as, if not more,
damaging.
(Source: CSIS-McAfee Report)
(Source: Ponemon Institute releases 2014 Cost of Data Breach)
38.
Security Threat LandscapeLesson 2: Securing the
environment
Section: Basics
39. Security Threat Landscape
The network is no longer the securityperimeter (it hasn’t been for some time)
Identity is the (new) security perimeter
Entry—we can’t stop this from happening
People will be fooled, bribed, blackmailed, etc.
Eliminating human error isn’t possible
Phishing works and will continue to do so
Insider-attacks are a big problem
Anomalous activity monitoring helps in detection;
limit access through identity management & isolation
Compliance is very important
But compliance and security are not the same thing:
compliant != secure
Prevention methods aren’t always technical
or architectural
Many will be operational and that will impose some
level of additional operational friction—security has a
price $$$
40. Hard Lessons…
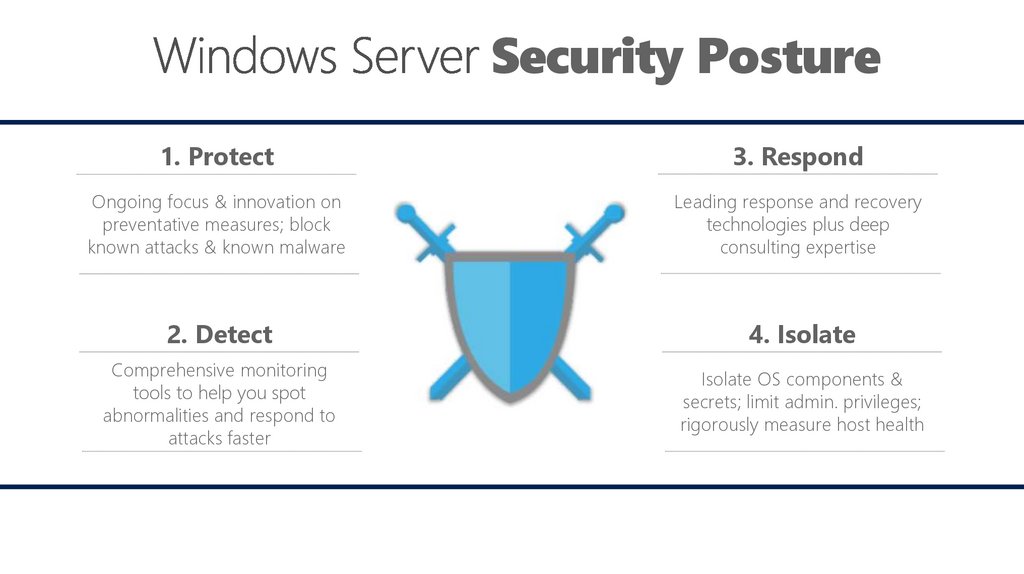
Security Posture1. Protect
3. Respond
Ongoing focus & innovation on
preventative measures; block
known attacks & known malware
Leading response and recovery
technologies plus deep
consulting expertise
2. Detect
4. Isolate
Comprehensive monitoring
tools to help you spot
abnormalities and respond to
attacks faster
Isolate OS components &
secrets; limit admin. privileges;
rigorously measure host health
41.
Managed privileged identitiesSecure the OS
Secure virtualization
42. What do we need to secure and how?
43. Fundamentals of Information Security
The CIA TriadInformation
Security
Concepts and
Fundamental
Principles
Confidentiality
Integrity
Availability
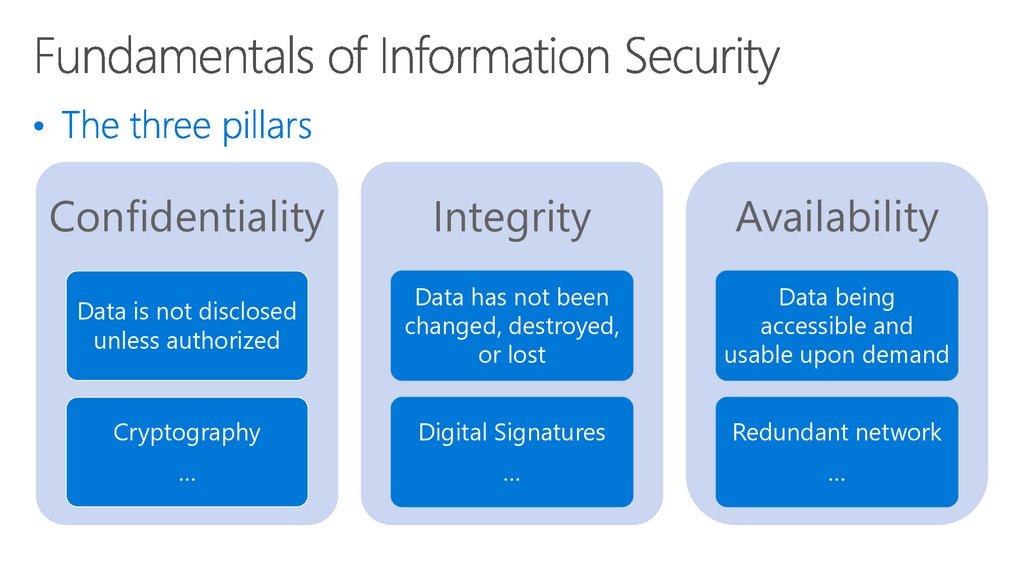
44. Information Security Concepts and Fundamental Principles
ConfidentialityIntegrity
Availability
Data is not disclosed
unless authorized
Data has not been
changed, destroyed,
or lost
Data being
accessible and
usable upon demand
Cryptography
Digital Signatures
Redundant network
…
…
…
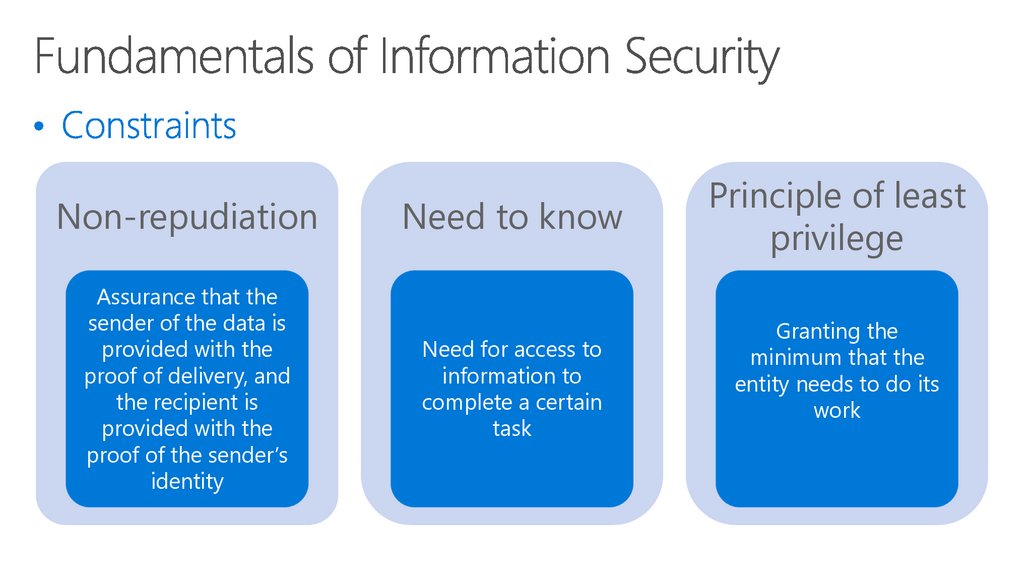
45. Fundamentals of Information Security
Non-repudiationAssurance that the
sender of the data is
provided with the
proof of delivery, and
the recipient is
provided with the
proof of the sender’s
identity
Need to know
Need for access to
information to
complete a certain
task
Principle of least
privilege
Granting the
minimum that the
entity needs to do its
work
46. HIDDEN – More Information
47. Fundamentals of Information Security
Securitydocuments,
user
education
Firewalls,
Network
Access
Quarantine
Control,
NAP
Network
segments,
IPsec,
NIDS
ACLs,
encryption,
Rights
management
Operating
system hardening,
authentication,
patch
management,
HIDS
Guards,
locks,
tracking
devices
Application
design,
antivirus
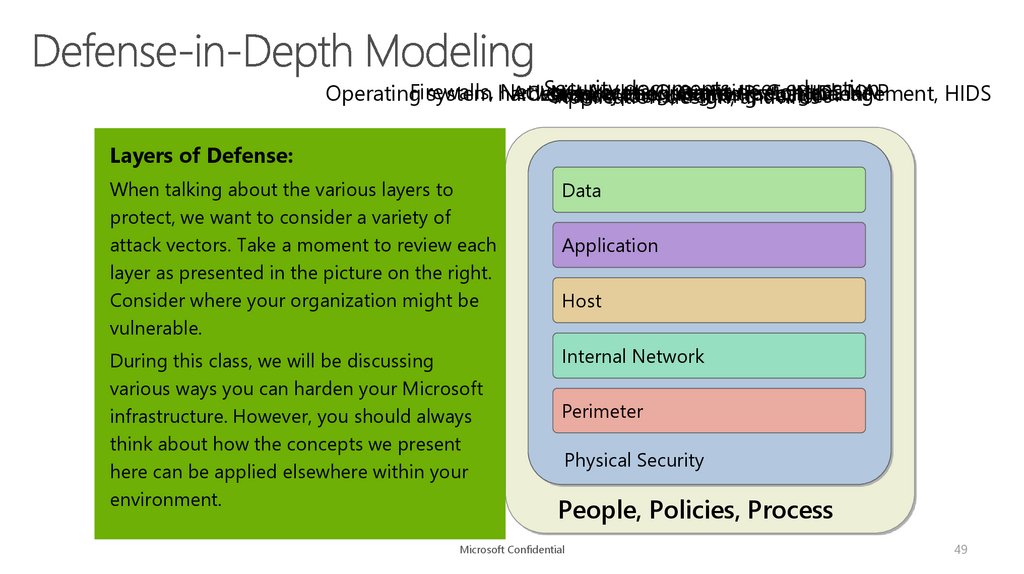
Layers of Defense:
When talking about the various layers to
protect, we want to consider a variety of
attack vectors. Take a moment to review each
layer as presented in the picture on the right.
Consider where your organization might be
vulnerable.
Data
During this class, we will be discussing
various ways you can harden your Microsoft
infrastructure. However, you should always
think about how the concepts we present
here can be applied elsewhere within your
environment.
Internal Network
Application
Host
Perimeter
Physical Security
People, Policies, Process
Microsoft Confidential
49
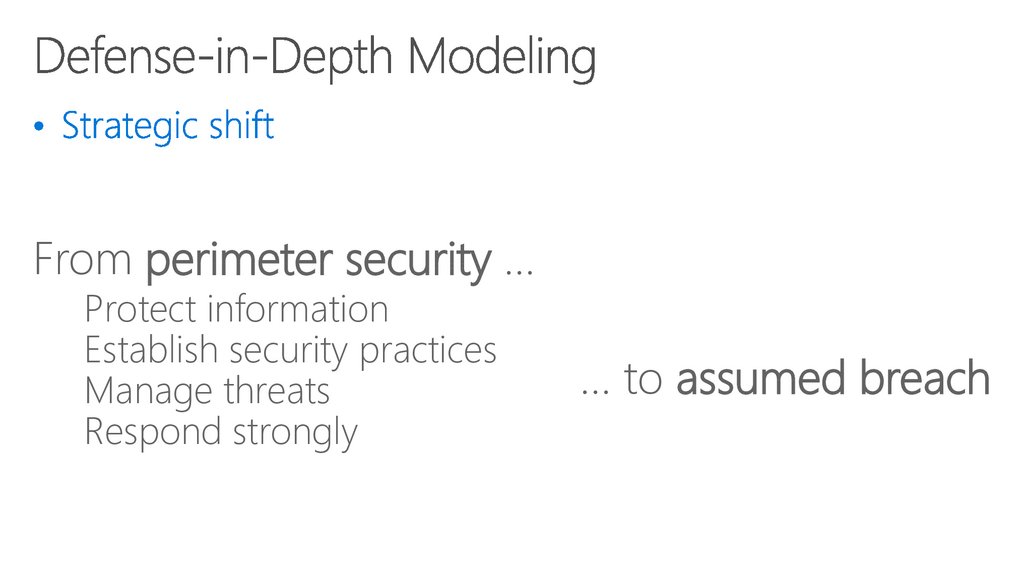
48. Defense-in-Depth Modeling
5049. Defense-in-Depth Modeling
5150.
From perimeter security …Protect information
Establish security practices
Manage threats
Respond strongly
… to assumed breach
51.
Basic SecurityPrinciples:
How We
Protect It
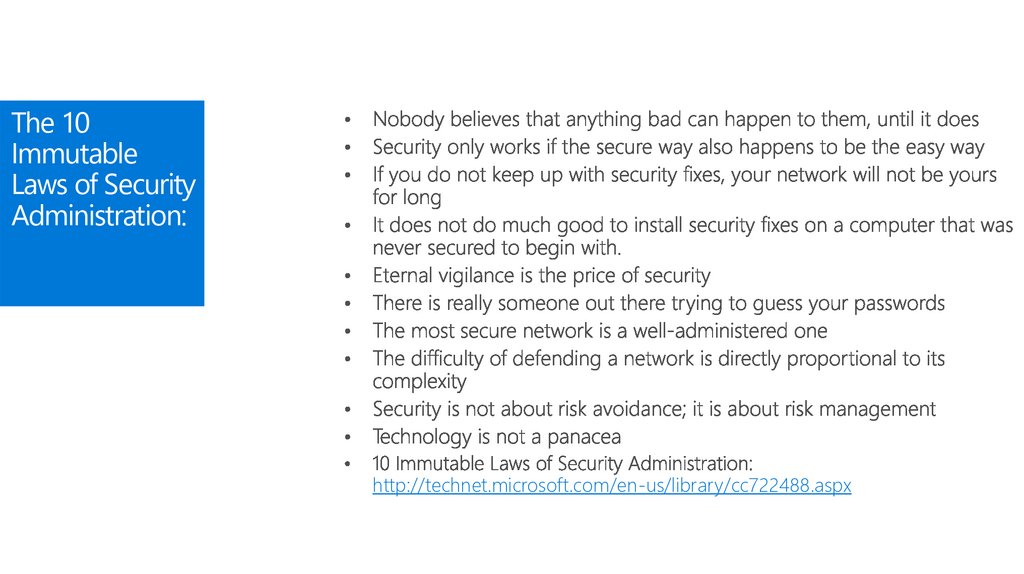
52. Defense-in-Depth Modeling
The 10Immutable
Laws of Security
Administration:
http://technet.microsoft.com/en-us/library/cc722488.aspx
53. Risk Management
The 10Immutable
Laws of Security
Administration:
54. Key Concepts
59Sample AD
assets
Domain Controllers
Active Directory Backups
Administrative Accounts and Groups
Identities and attributes
Group Policies
Administrative Workstations
Administrative Delegations
Administration Team
55. Basic Security Principles
60Vulnerabilities
A flaw or weakness in a system’s design, implementation, or operation and
management that could be exploited to violate the system’s security policy
Examples:
56. Basic Security Principles: How We Protect It
61Vulnerabilities
(continued)
57. The 10 Immutable Laws of Security Administration:
62Vulnerabilities
(continued)
58. The 10 Immutable Laws of Security Administration:
63Vulnerabilities
(continued)
59. Sample AD assets
Security Threat LandscapeLesson 2: Securing the
environment
Section: Help protect credentials
and privileged access
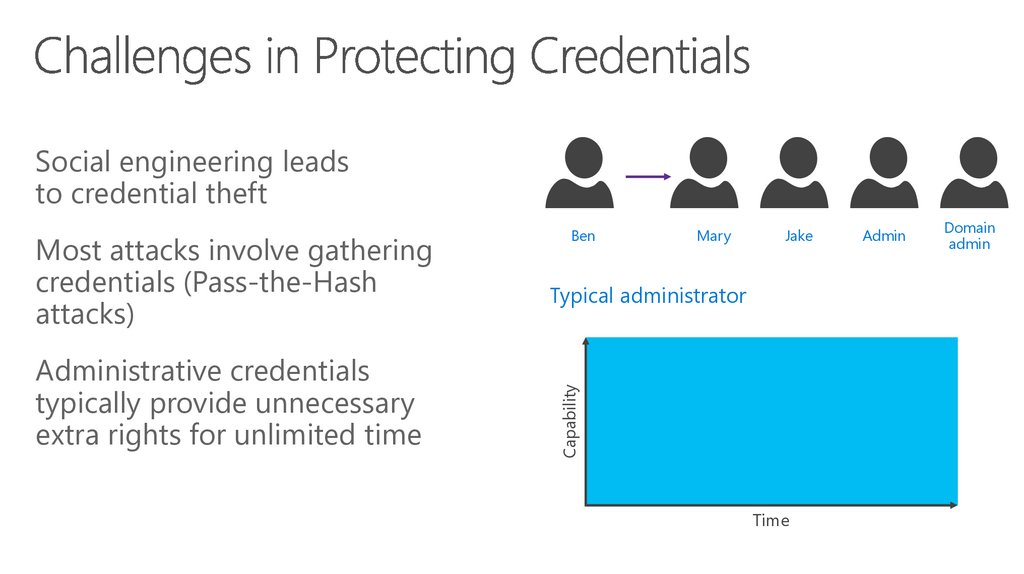
60. Vulnerabilities
Social engineering leadsto credential theft
Administrative credentials
typically provide unnecessary
extra rights for unlimited time
Mary
Jake
Typical administrator
Capability
Most attacks involve gathering
credentials (Pass-the-Hash
attacks)
Ben
Time
Admin
Domain
admin
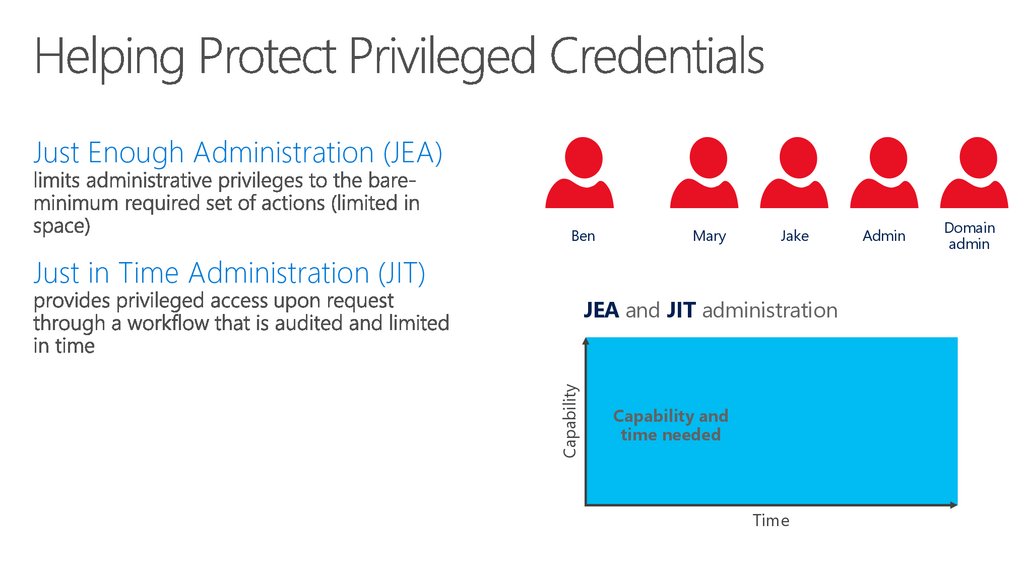
61. Vulnerabilities (continued)
Just Enough Administration (JEA)Ben
Mary
Jake
Just in Time Administration (JIT)
Capability
JEA and JIT administration
Capability and
time needed
Time
Admin
Domain
admin
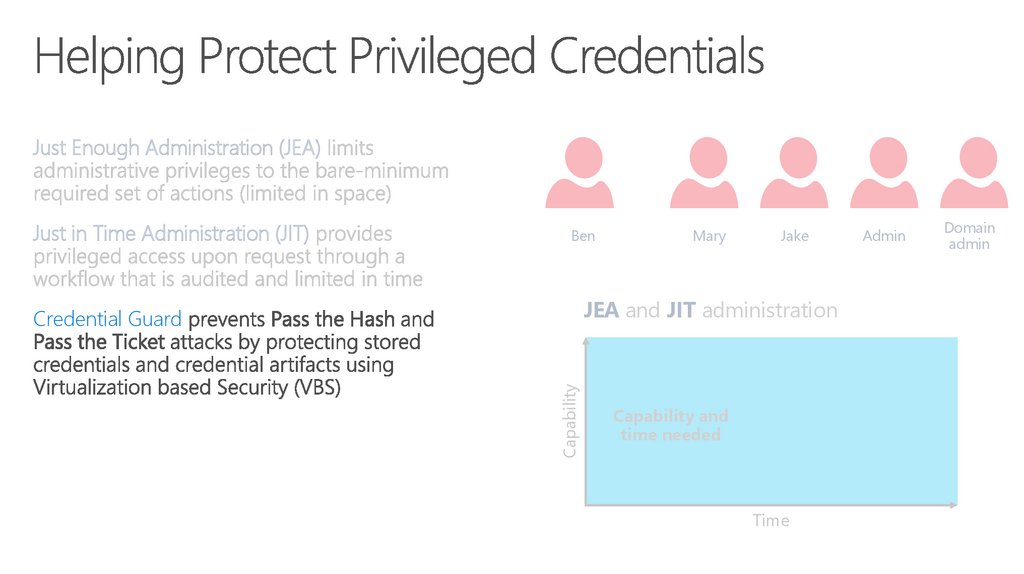
62. Vulnerabilities (continued)
Just Enough Administration (JEA)Just in Time Administration (JIT)
Ben
Mary
Jake
JEA and JIT administration
Capability
Credential Guard
Capability and
time needed
Time
Admin
Domain
admin
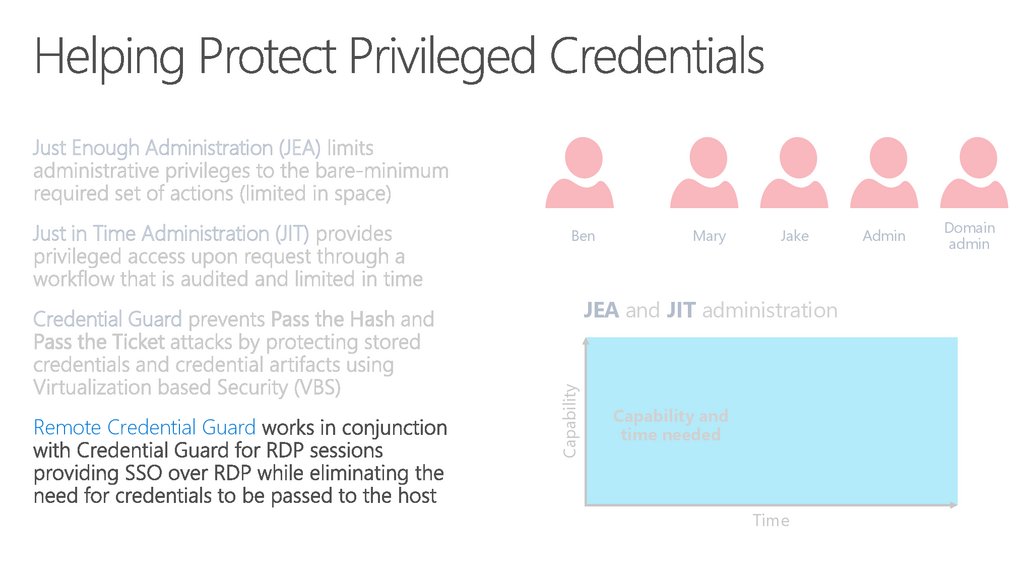
63. Vulnerabilities (continued)
Just Enough Administration (JEA)Just in Time Administration (JIT)
Ben
Jake
JEA and JIT administration
Capability
Credential Guard
Remote Credential Guard
Mary
Capability and
time needed
Time
Admin
Domain
admin
64. Security Threat Landscape
Lesson 2: Securing theenvironment
Section: Help protect
applications and data in any
cloud
65. Challenges in Protecting Credentials
Challenges Protecting the OS and ApplicationsNew exploits can attack the OS
boot-path all the way up through
applications operations
?
Known and unknown threats
need to be blocked without
impacting legitimate workloads
Security Information and Event
Management (SIEM) systems are
only as intelligent as the
information provided from the
OS
?
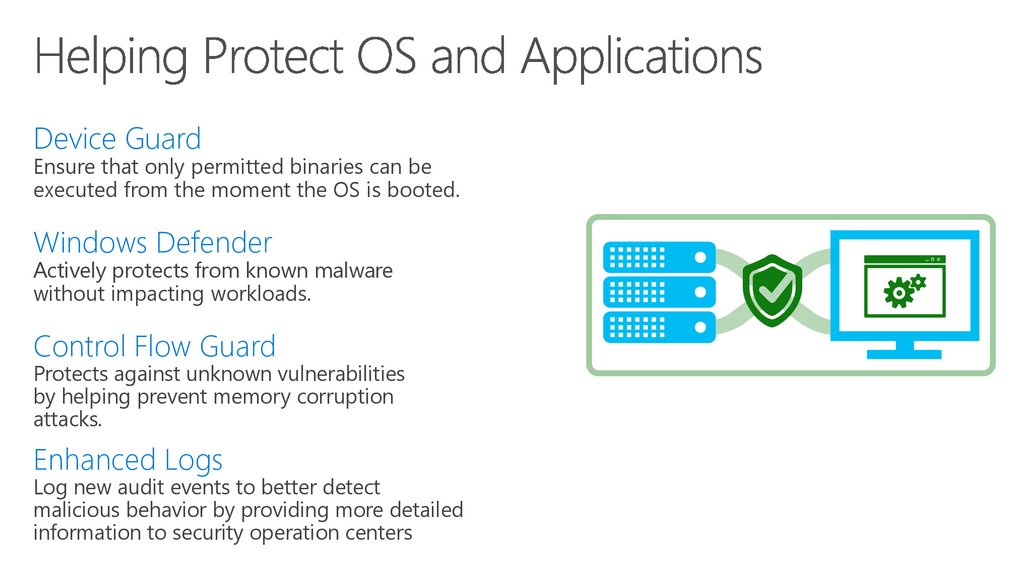
66. Helping Protect Privileged Credentials
Device GuardEnsure that only permitted binaries can be
executed from the moment the OS is booted.
Windows Defender
Actively protects from known malware
without impacting workloads.
Control Flow Guard
Protects against unknown vulnerabilities
by helping prevent memory corruption
attacks.
Enhanced Logs
Log new audit events to better detect
malicious behavior by providing more detailed
information to security operation centers
67. Helping Protect Privileged Credentials
Security Threat LandscapeLesson 2: Securing the
environment
Section: Help protect the
virtualization fabric
68. Helping Protect Privileged Credentials
Help Protect theVirtualization
Fabric
69. Security Threat Landscape
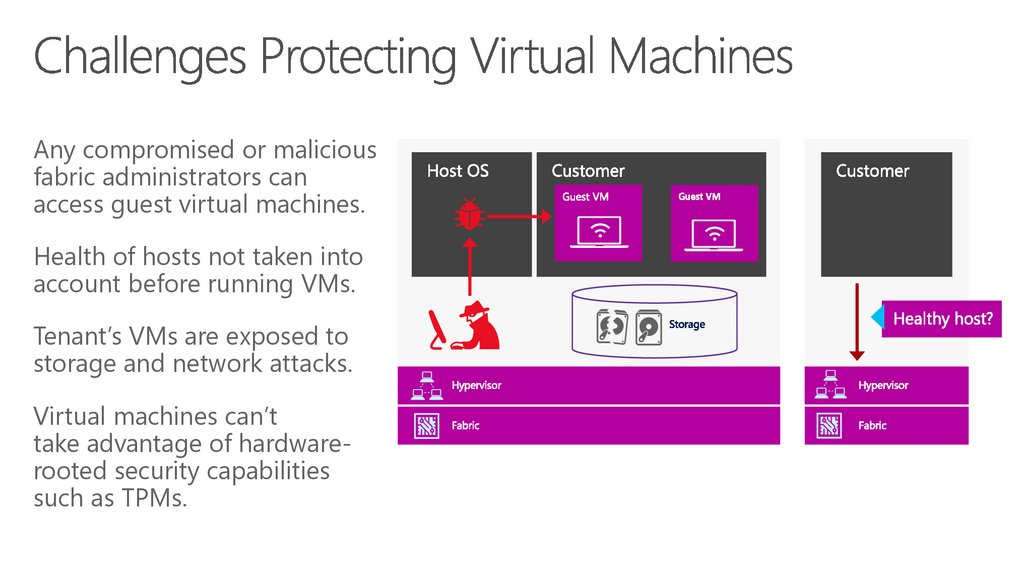
Any compromised or maliciousfabric administrators can
access guest virtual machines.
Health of hosts not taken into
account before running VMs.
Tenant’s VMs are exposed to
storage and network attacks.
Virtual machines can’t
take advantage of hardwarerooted security capabilities
such as TPMs.
70. Challenges Protecting the OS and Applications
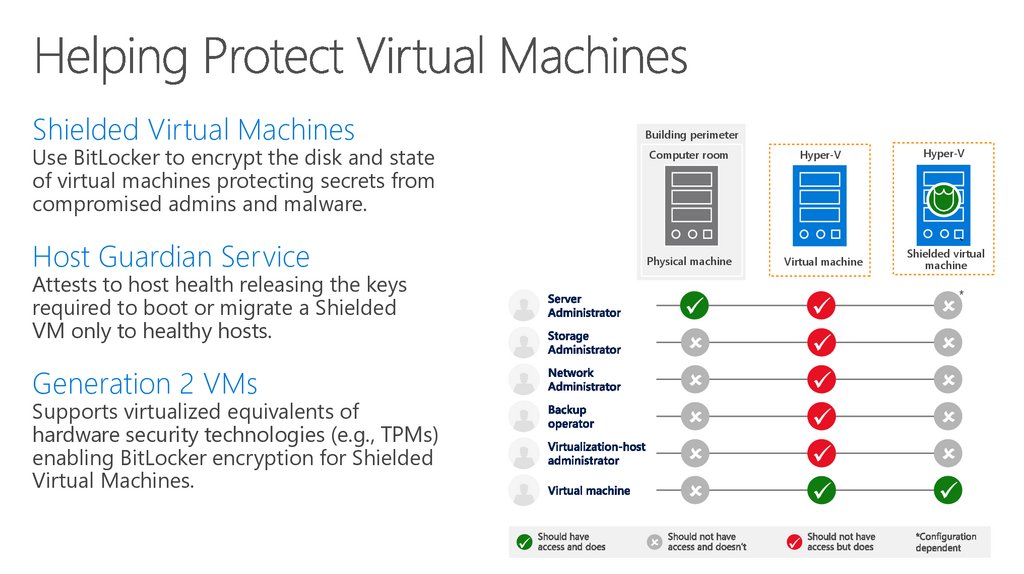
Shielded Virtual MachinesBuilding perimeter
Use BitLocker to encrypt the disk and state
of virtual machines protecting secrets from
compromised admins and malware.
Host Guardian Service
Computer room
Hyper-V
Hyper-V
Physical machine
Virtual machine
Shielded virtual
machine
Attests to host health releasing the keys
required to boot or migrate a Shielded
VM only to healthy hosts.
Generation 2 VMs
Supports virtualized equivalents of
hardware security technologies (e.g., TPMs)
enabling BitLocker encryption for Shielded
Virtual Machines.
`
*
71. Helping Protect OS and Applications
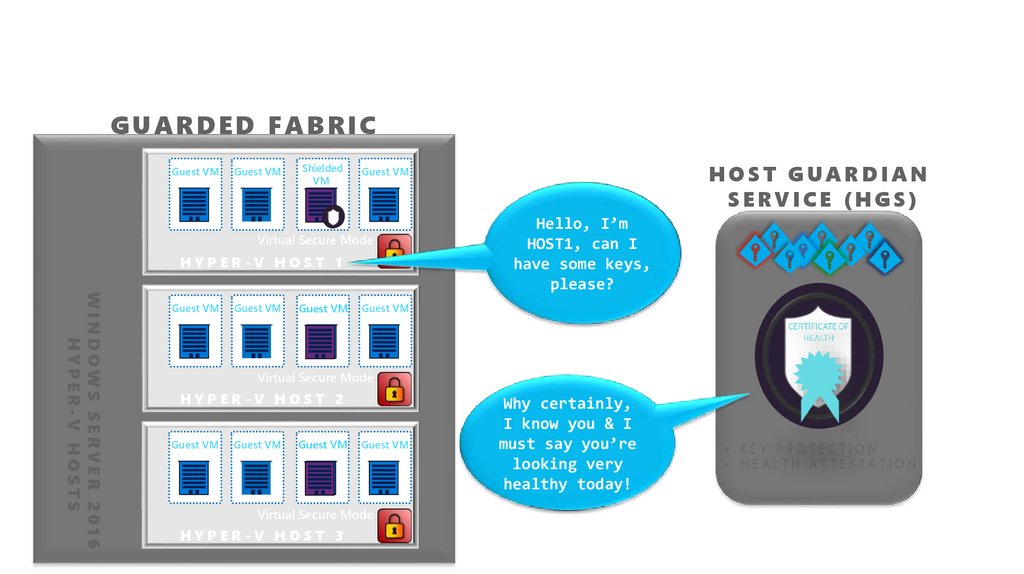
Decryption keys: controlled by external systemGUARDED FABRIC
Guest VM
Guest VM
Shielded
VM
Virtual Secure Mode
HYPER-V HOST 1
WINDOWS SERVER 2016
HYPER-V HOSTS
Guest VM
Guest VM
Guest VM
HOST GUARDIAN
SERVICE (HGS)
Guest VM
Hello, I’m
HOST1, can I
have some keys,
please?
Guest VM
Virtual Secure Mode
HYPER-V HOST 2
Guest VM
Guest VM
Guest VM
Guest VM
Virtual Secure Mode
HYPER-V HOST 3
Why certainly,
I know you & I
must say you’re
looking very
healthy today!
+ KEY PROTECTION
+ HEALTH ATTESTATION
72. Security Threat Landscape
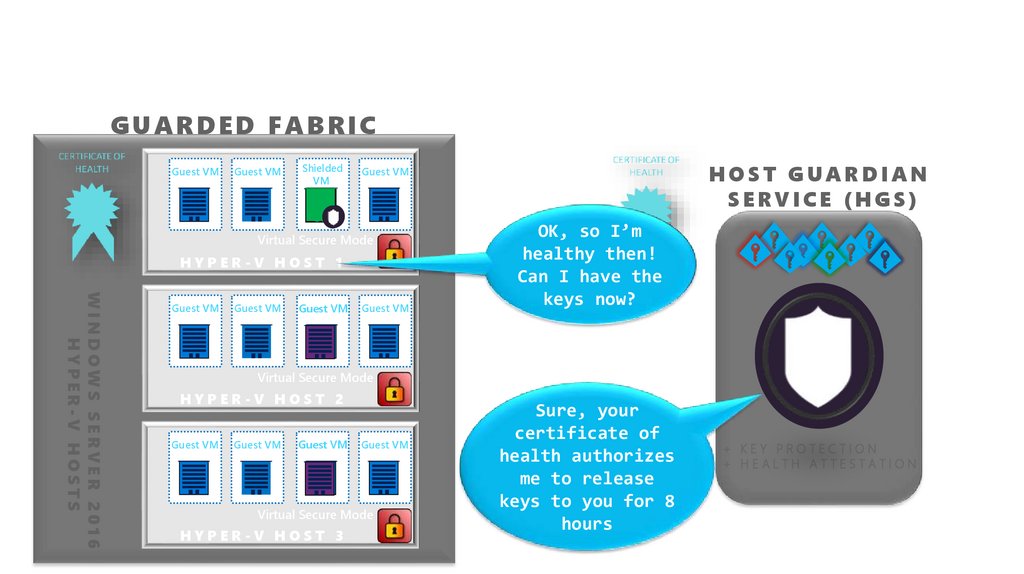
Decryption keys: controlled by external systemGUARDED FABRIC
Guest VM
Guest VM
Shielded
VM
Virtual Secure Mode
HYPER-V HOST 1
WINDOWS SERVER 2016
HYPER-V HOSTS
Guest VM
Guest VM
Guest VM
HOST GUARDIAN
SERVICE (HGS)
Guest VM
Guest VM
OK, so I’m
healthy then!
Can I have the
keys now?
Virtual Secure Mode
HYPER-V HOST 2
Guest VM
Guest VM
Guest VM
Guest VM
Virtual Secure Mode
HYPER-V HOST 3
Sure, your
certificate of
health authorizes
me to release
keys to you for 8
hours
+ KEY PROTECTION
+ HEALTH ATTESTATION
73. Help Protect the Virtualization Fabric
Security Threat LandscapeLesson 2: Securing the
environment
Section: Protect
with just
enough OS
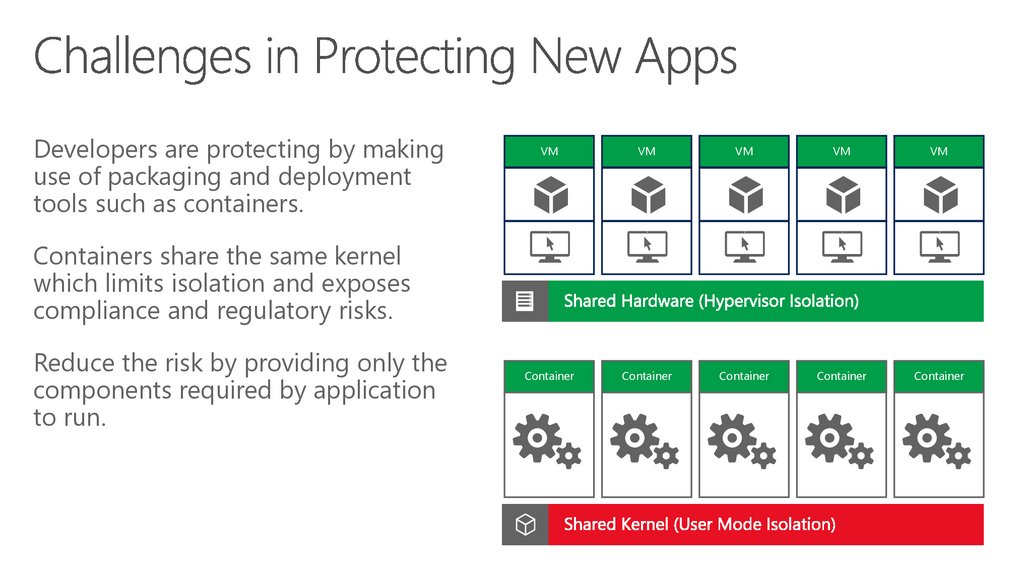
74. Challenges Protecting Virtual Machines
Developers are protecting by makinguse of packaging and deployment
tools such as containers.
VM
VM
VM
VM
VM
Container
Container
Container
Container
Container
Containers share the same kernel
which limits isolation and exposes
compliance and regulatory risks.
Reduce the risk by providing only the
components required by application
to run.
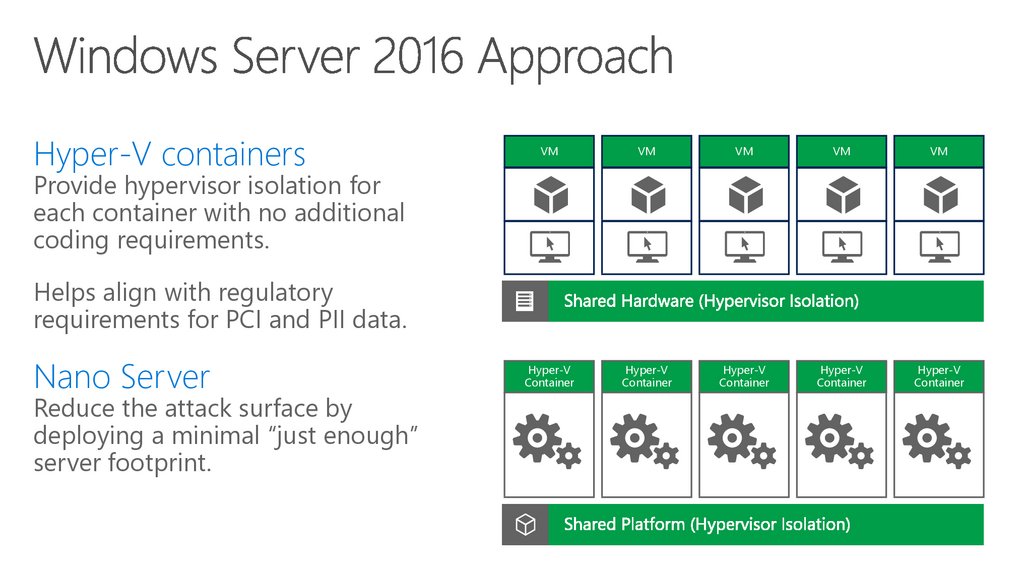
75. Helping Protect Virtual Machines
Hyper-V containersVM
VM
VM
VM
VM
Hyper-V
Container
Hyper-V
Container
Hyper-V
Container
Hyper-V
Container
Hyper-V
Container
Provide hypervisor isolation for
each container with no additional
coding requirements.
Helps align with regulatory
requirements for PCI and PII data.
Nano Server
Reduce the attack surface by
deploying a minimal “just enough”
server footprint.
76. Decryption keys: controlled by external system
Security Threat LandscapeLesson 2: Securing the
environment
Section: Windows Server 2016
security summary
77. Decryption keys: controlled by external system
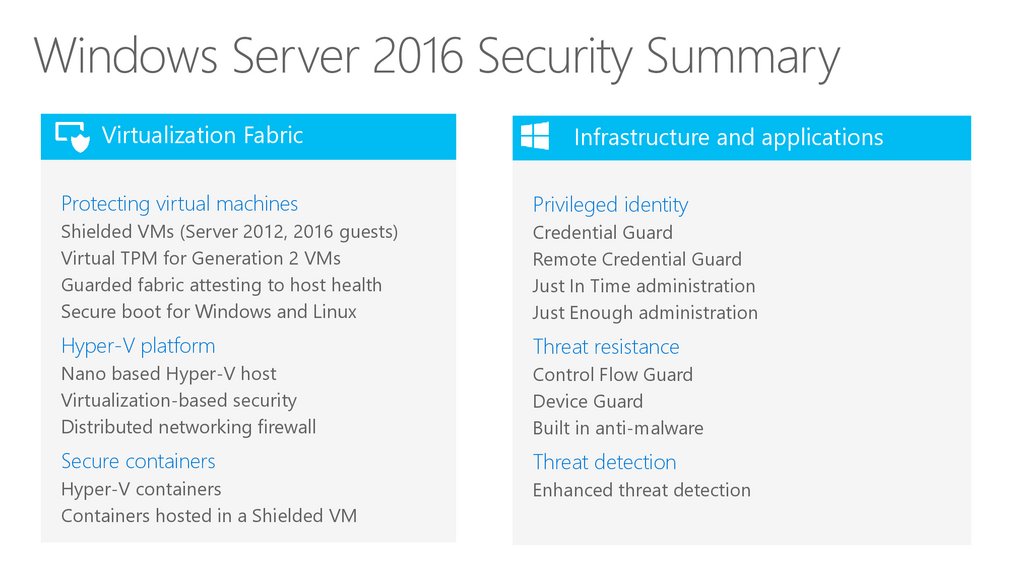
Windows Server 2016 Security SummaryVirtualization Fabric
Infrastructure and applications
Protecting virtual machines
Privileged identity
Shielded VMs (Server 2012, 2016 guests)
Virtual TPM for Generation 2 VMs
Guarded fabric attesting to host health
Secure boot for Windows and Linux
Credential Guard
Remote Credential Guard
Just In Time administration
Just Enough administration
Hyper-V platform
Threat resistance
Nano based Hyper-V host
Virtualization-based security
Distributed networking firewall
Control Flow Guard
Device Guard
Built in anti-malware
Secure containers
Threat detection
Hyper-V containers
Containers hosted in a Shielded VM
Enhanced threat detection