Похожие презентации:
Denial-of-service attacks
1.
What maycause such a
problem?
2.
Denial-of-service attacksCS 468/568 Contemporary Topics in Networking – Spring 2023
Mokrov Semen
3.
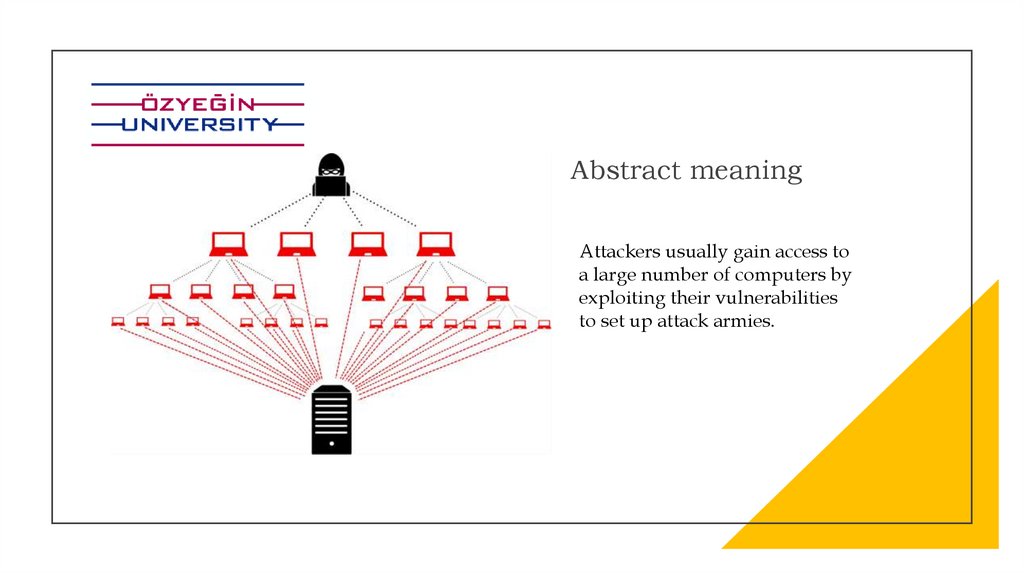
Abstract meaningAttackers usually gain access to
a large number of computers by
exploiting their vulnerabilities
to set up attack armies.
4.
HistoryDOS attacks have been known to the
network research community since the
early 1980s
5.
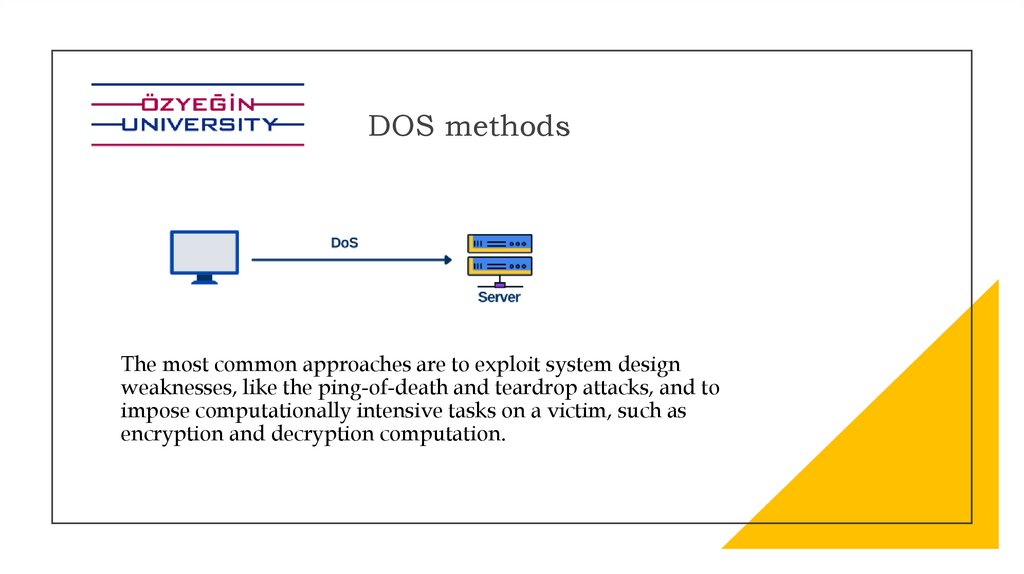
DOS methodsThe most common approaches are to exploit system design
weaknesses, like the ping-of-death and teardrop attacks, and to
impose computationally intensive tasks on a victim, such as
encryption and decryption computation.
6.
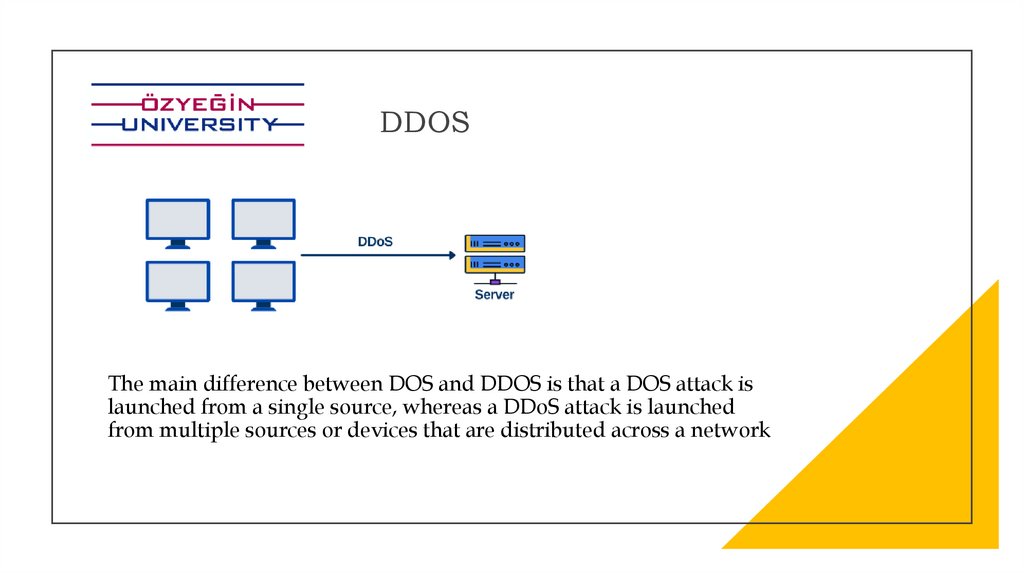
DDOSThe main difference between DOS and DDOS is that a DOS attack is
launched from a single source, whereas a DDoS attack is launched
from multiple sources or devices that are distributed across a network
7.
Attackers incentivesThe motivation of attackers
Financial/economical gain
Revenge
Ideological belief
Intellectual Challenge
Cyberwarfare
8.
Impact of the DDOS Attacks• Disruption of services
• Revenue loss
• Data theft
• Damage reputation
• Financial impact
9.
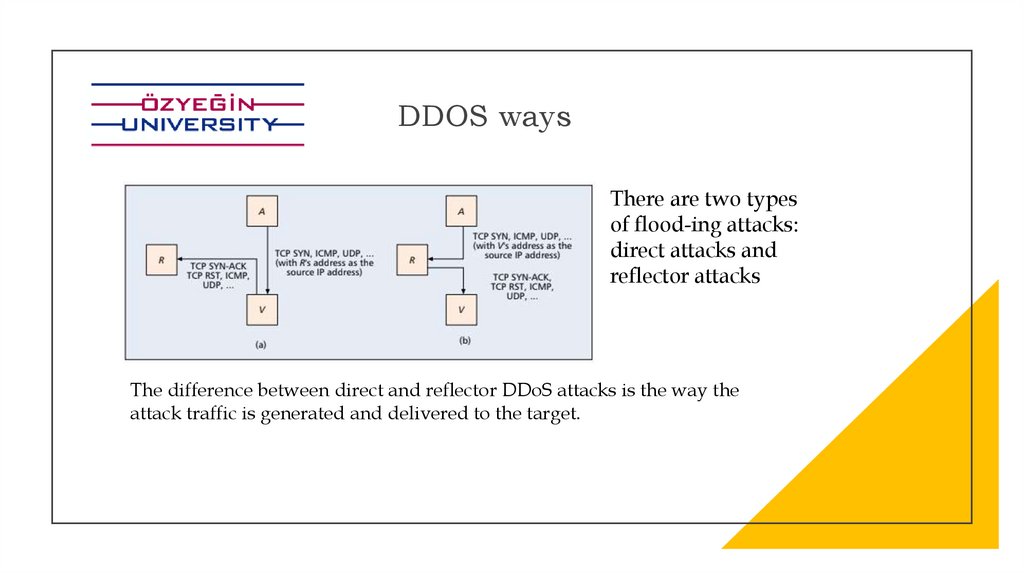
DDOS waysThere are two types
of flood-ing attacks:
direct attacks and
reflector attacks
The difference between direct and reflector DDoS attacks is the way the
attack traffic is generated and delivered to the target.
10.
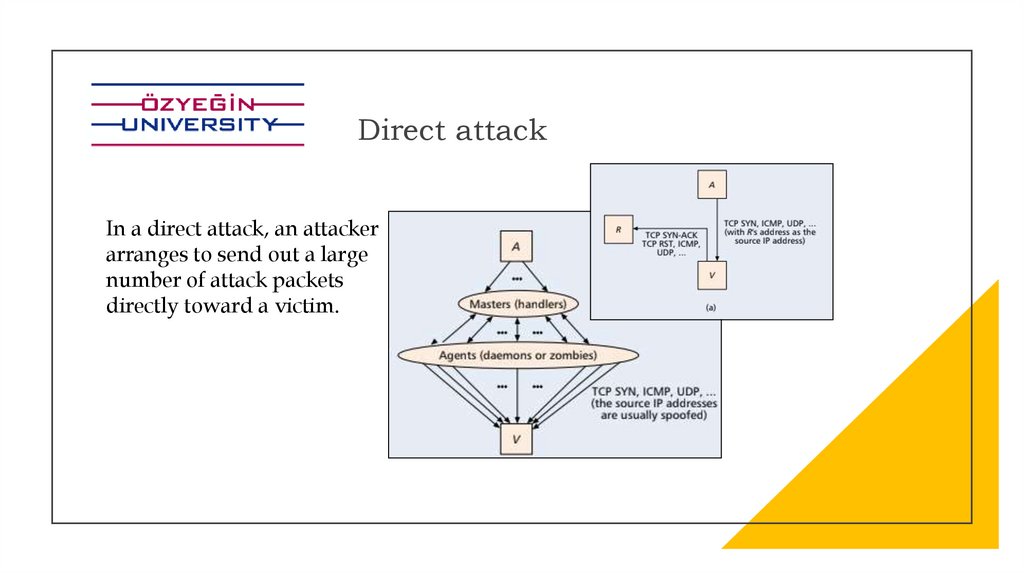
Direct attackIn a direct attack, an attacker
arranges to send out a large
number of attack packets
directly toward a victim.
11.
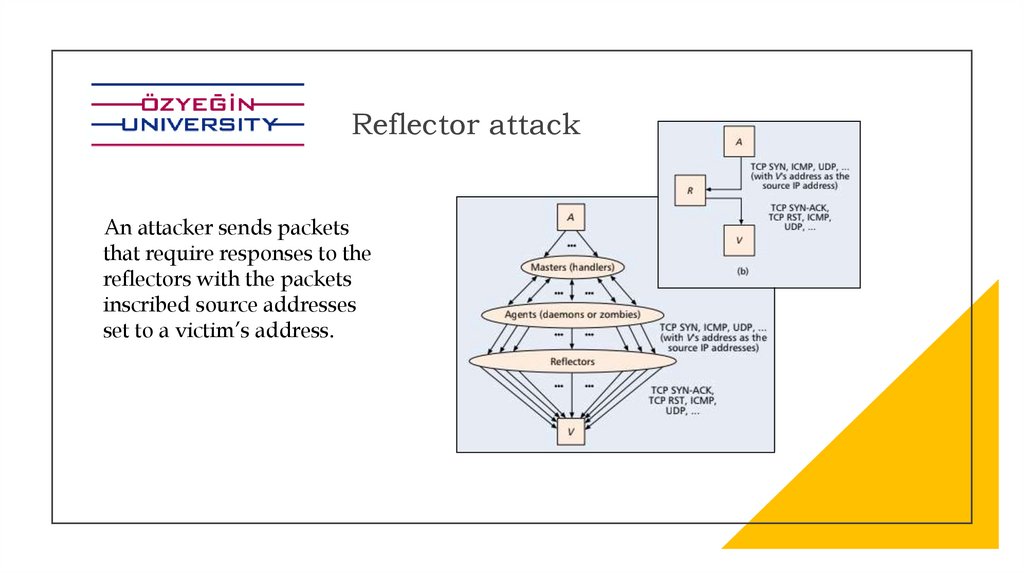
Reflector attackAn attacker sends packets
that require responses to the
reflectors with the packets
inscribed source addresses
set to a victim’s address.
12.
Possible solutionsDo you know any kind of DDOS attack
solutions?
13.
Attack prevention andpreemption
• hosts may be securely protected from master and agent implants
• cyber-informants and cyber-spies can be employed to intercept
attack plans
14.
Source traceback andidentification
There are generally two approaches to the IP traceback
problem:
• for routers to record information about packets
• for routers to send additional information about the
packets
15.
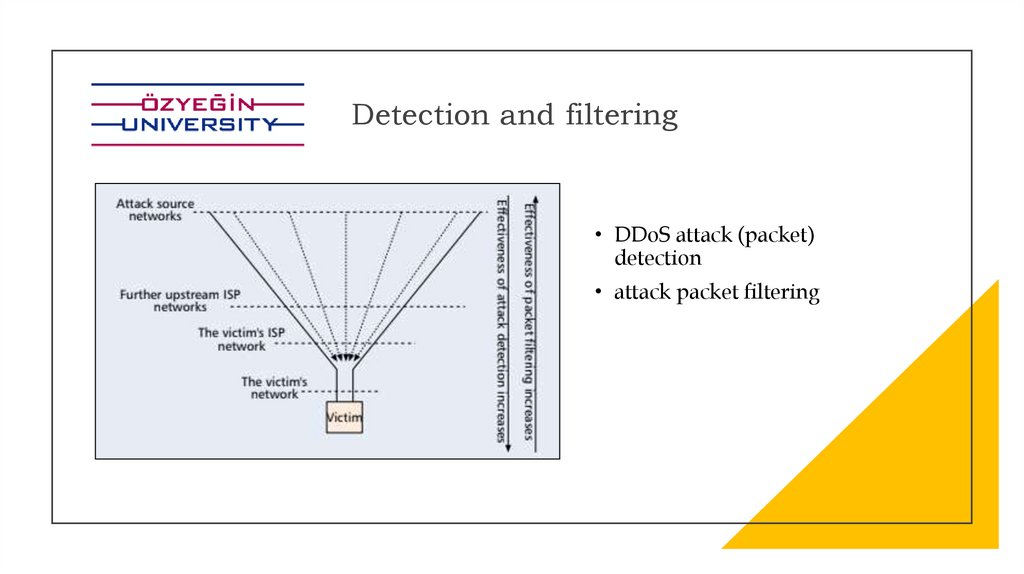
Detection and filtering• DDoS attack (packet)
detection
• attack packet filtering
16.
Packet filteringMost commons filtering ways are:
• The route-based packet filtering
(RPF) approach
• distributed attack detection (DAD)
17.
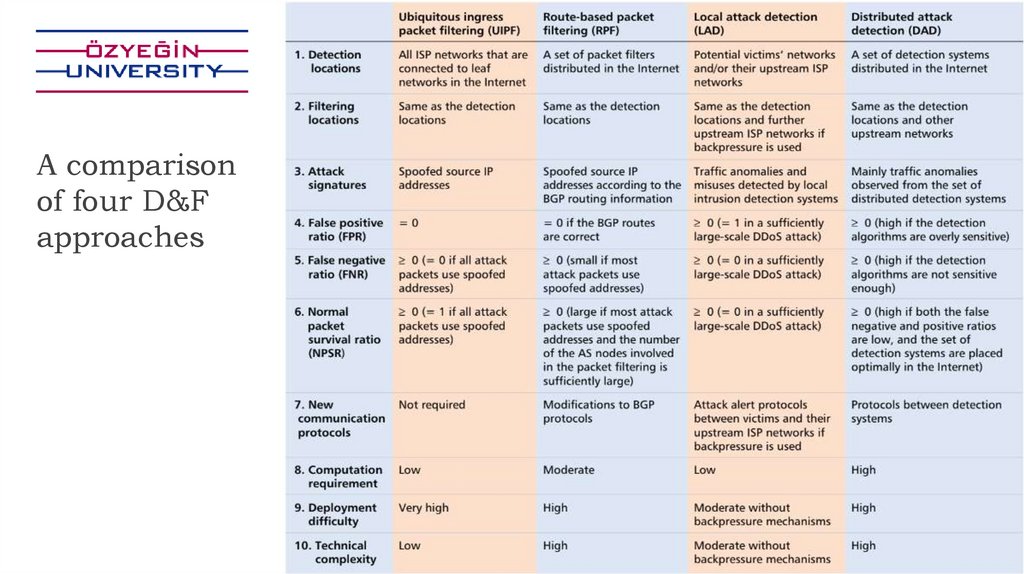
A comparisonof four D&F
approaches
18.
Conclusion• More nodes in the Internet should be involved in preventing,
detecting, and responding to DDoS flooding attacks
• collaboration and cooperation among the key defensive points
within and between service providers on the Internet
• More reliable mechanisms are required to authenticate the
sources of the Internet traffic
19.
Thank you for your attention20.
ReferencesDefending against Flooding-Based Distributed Denial-of-Service Attacks: A
Tutorial
Rocky K. C. Chang, The Hong Kong Polytechnic University October 2002
A Survey of Defense Mechanisms Against Distributed Denial of Service
(DDoS) Flooding Attacks
Saman Taghavi Zargar, Member, IEEE, James Joshi, Member, IEEE, and David Tipper, Senior Member,
IEEE, 2013E







 Интернет
Интернет








