Похожие презентации:
Securing Your Network
1. Ch 4: Securing Your Network
CompTIA Security+: GetCertified Get Ahead:
SY0-401 Study Guide
Darril Gibson
Updated 2-23-16
2. Understanding IDSs and IPSs
3. IDS v. IPS
IDS detects attacks but does not stopthem
– Detective technical control
– Passive IDS merely logs attacks, and/or
sends alerts
– Active IDS may send alerts and change
environment
IPS stops attacks in progress
– Preventive technical control
– Similar to Active IDS
4. HIDS v. NIDS
HIDS (Host-based IDS)– Installed on a server or workstation
NIDS (Network-based IDS)
– Installed on a network device, such as a
router or switch
5. Packet Sniffing
Wireshark and other tools show packetsone-by-one
Useful for debugging
Can steal passwords off the wire
– Especially if they are sent without encryption
6. Wall of Sheep
Displayspasswords
captured at
Defcon
7. Signatures v. Anomalies
Signature-based monitoring recognizesknown attack patterns
– Also called definition-based
Anomaly-based monitoring detects
abnormal behavior based on a baseline
– Also valled behavior-based or heuristicsbased
8. Active IDS v. IPS
Both react to an attack in some mannerIPS must be placed in line with the traffic
to prevent the attack
9. HIDS
Additional software on a workstation orserver
Can detect attacks on the local system
Can monitor changes to operating system
files
Protects only one host
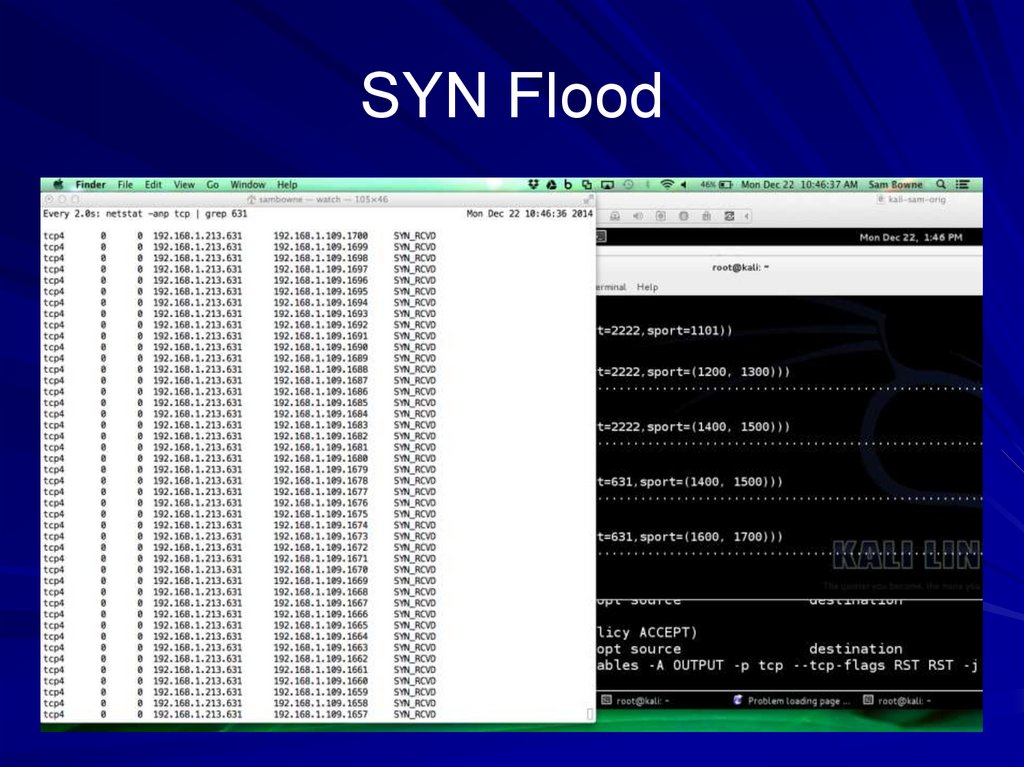
10. SYN Flood Demo Notes
On Mac OS X:– Preferences, click Sharing, turn on Printer
Sharing
– watch "netstat -anp tcp | grep 631"
On Kali Linux:
– iptables -A OUTPUT -p tcp --tcp-flags RST
RST -j DROP
– scapy
– send(IP(dst="192.168.1.213")/TCP(dport=631
, sport=(1000,1100))
11. SYN Flood
12. NIDS
Can only see network traffic, not OS filesUnable to decrypt encrypted traffic
– Unless your network performs a man-in-themiddle SSL attack
– Commonly done in modern corporations
13. NIDS Configuration
14. Detection Methods
Signature-based– Uses a database of predefined traffic patterns
– Database requires frequent updates
Anomaly-based
– Needs to measure a performance baseline
– Baseline must be updated if network is
changed
15. Data Sources and Trends
IDS collects data from various sources– Firewall logs
– System logs
– Application logs
– May monitor logs in real time
16. Reporting
Alarms– Also called Alerts
– Indicates that an interesting event was
detected
– Does not always indicate a real attack
Goal
– Set threshold low enough to detect all real
attacks, but
– High enough to avoid too may false positives
17. False Positives v. False Negatives
False positive– Alert on nonthreatening events
False negative
– Real attack, but no alert
18. IDS Threshold
Number of events required to cause analert
– Example: 50 incomplete TCP handshakes per
minute from the same IP
There are no established rules for
thresholds
– Must be "tuned" by administrators
Untuned security devices tend to produce
many false positives
19. IDS Responses
Passive (Alerts personnel)– Pop-up window
– Central monitor
– Page or text message
Active
– Alerts personnel
– Modify ACL on Firewall
– Divert attack to a honeypot or other safe environment
20. Honeypot
Appears to be a server worth hacking intoHas no valuable data
Often used to collect knowledge about
attackers
21.
Link Ch 4a22.
Link Ch 4b23.
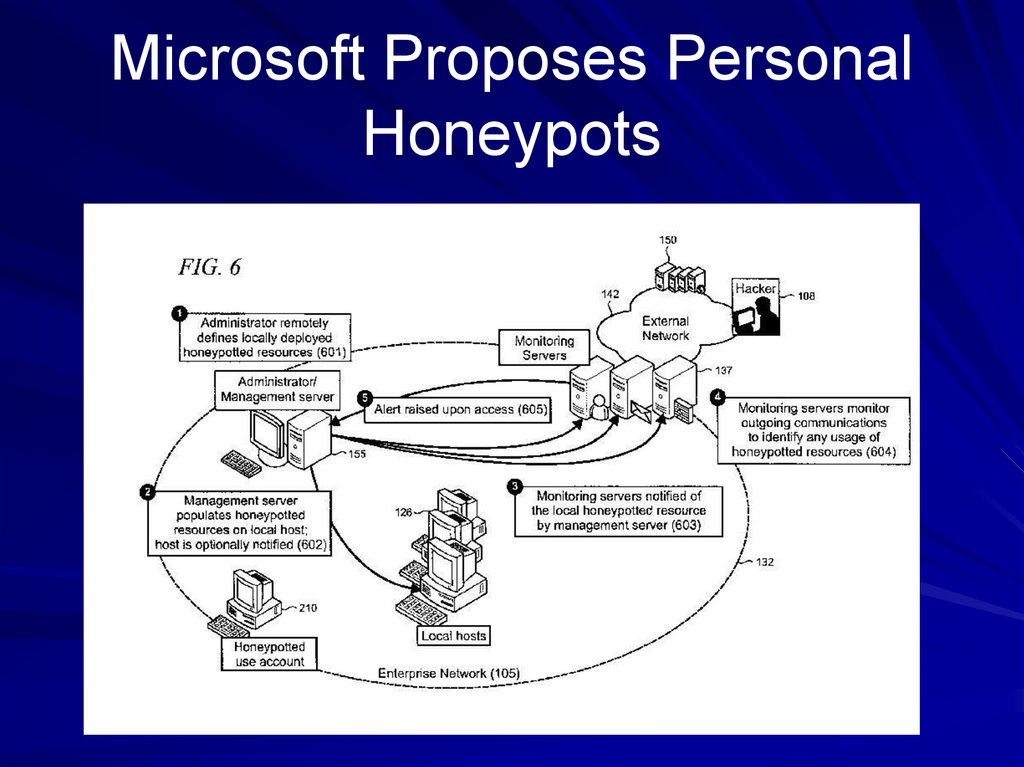
Link Ch 4c24. Microsoft Proposes Personal Honeypots
25. Honeynet
A group of virtual servers appearing to bea live network
26. Counterattacks
Some active IDS systems attack theattacker back
Legal problems
Likely that you are attacking another
innocent victim
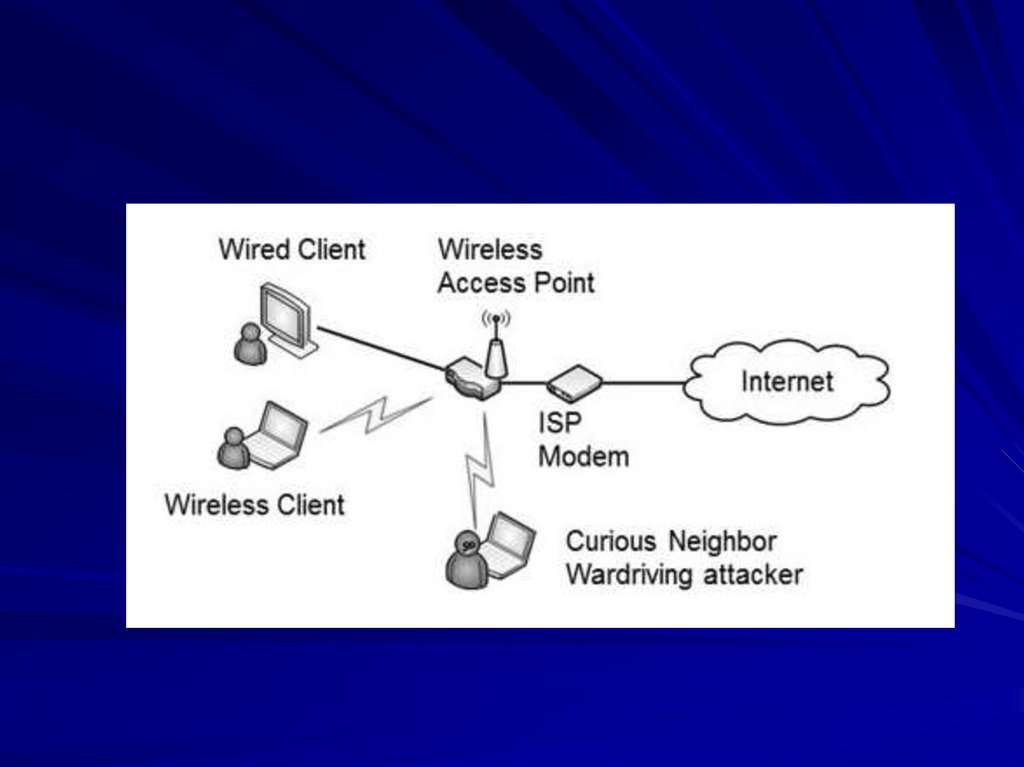
27. Securing Wireless Networks
28.
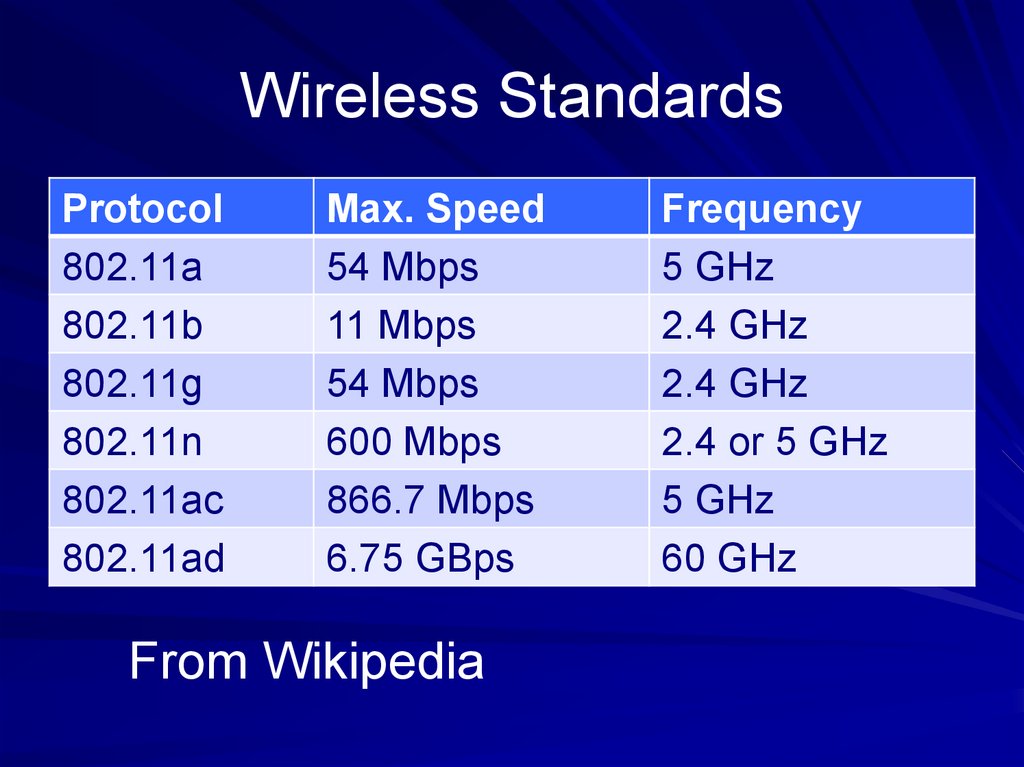
29. Wireless Standards
Protocol802.11a
802.11b
802.11g
802.11n
802.11ac
802.11ad
Max. Speed
54 Mbps
11 Mbps
54 Mbps
600 Mbps
866.7 Mbps
6.75 GBps
From Wikipedia
Frequency
5 GHz
2.4 GHz
2.4 GHz
2.4 or 5 GHz
5 GHz
60 GHz
30. Wireless Footprint
High power makes a large footprint– Easier for users to connect
– Easier for attackers to snoop on
Careful antenna placement
Metal in walls
Directional antennas such as a Yagi
increase range of reception
31. Site Surveys and Antenna Placement
Site Survey– Examine wireless environment to identify
potential problems
– Set up a WAP and measure signal strength
from various locations
– Also performed to detect
Rogue access points
Jamming
Evil twins
Interference
32. Security Protocols
WEP – Broken and unsafe to useWPA – Much safer, stronger with AES
than TKIP
WPA2 – Best security currently available,
especially in Enterprise mode with 802.1x
or RADIUS server
33. WEP (Wired Equivalent Privacy)
Mathematically insecureCan be broken with no knowledge of the
key 100% of the time
Attacker needs 50,000 packets or so
34. WPA (Wi-Fi Protected Access)
Designed to run on hardware designed forWEP with only a software upgrade
Weakest form of WPA uses TKIP
(Temporal Key Integrity Protocol) and RC4
encryption
Stronger form of WPA uses AES
encryption
35. WPA-2
Stronger cryptography than WEP or WPAUses CCMP mode of AES
36. Personal and Enterprise Modes
Both WPA and WPA-2 have Personal andEnterprise modes
Personal
– Pre-Shared Key (PSK) must be entered in
each device
– Key is the same for all users
37. Personal and Enterprise Modes
Enterprise mode– Each user has individual credentials
Username and password
Extensible protocols like LEAP and PEAP which
can use certificates
– Credentials stored on a RADIUS server
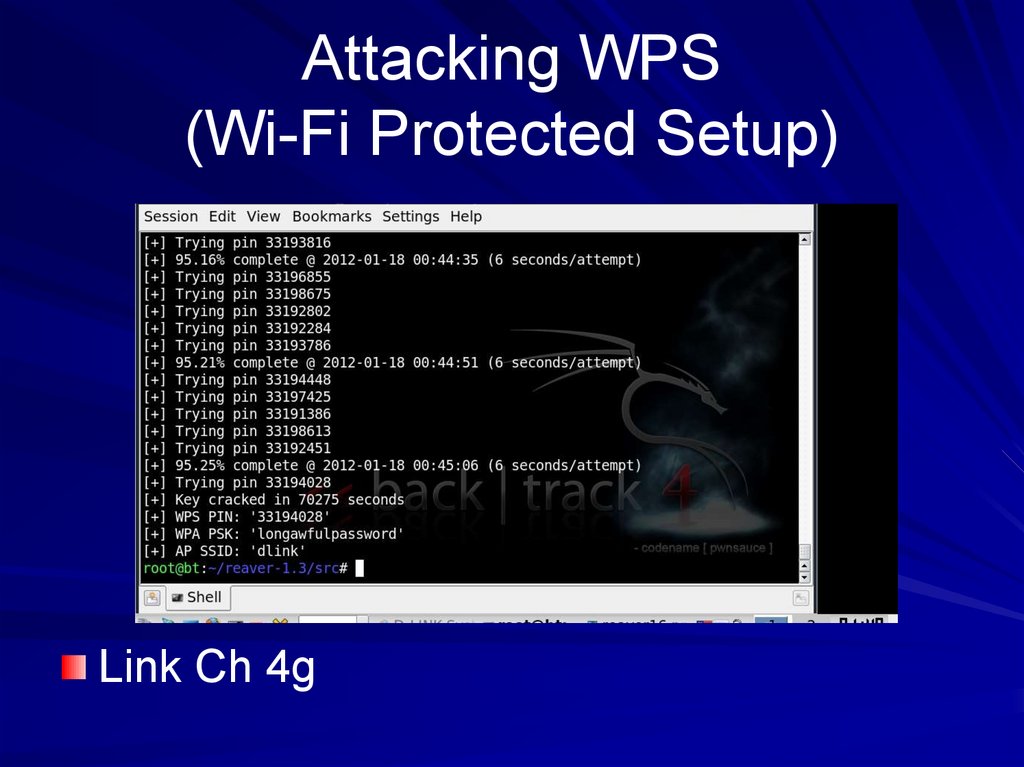
38. Attacking WPS (Wi-Fi Protected Setup)
Link Ch 4g39. EAP, PEAP, and LEAP
EAP (Extensible Authentication Protocol)– A framework that provides general guidance
for authentication
PEAP (Protected EAP)
– Encapsulates EAP conversation in a TLS
tunnel
– Requires a digital certificate for the server, but
not the clients
40. EAP-TTLS and EAP-TLS
EAP-Tunneled TLS (EAP-TTLS)– An extension of PEAP
– Allows some older authentication methods,
such as PAP within a TLS tunnel
– Requires a certificate on the 802.1x server but
not on the clients
EAP-TLS
– Most secure, widely implemented
– Requires a certificate on both the server and
the clients (link Ch 4o)
41. LEAP (Lightweight EAP
Cisco's attempt to improve WEPUses CHAP
Not secure, subject to offline dictionary
attack
Cisco recommends using PEAP instead
42. ASLEAP
Lightweight ExtensibleAuthentication Protocol
(LEAP)
– A Cisco product
– Vulnerable, but Cisco didn’t care
– Joshua Wright wrote the ASLEAP hacking
tool to crack LEAP, and forced Cisco to
develop a better protocol
See link Ch 4f
43. Reaction to ASLEAP
“Within months, some "helpful" person investedtheir time into generating a cracker tool.
Publicizing the threat was a service to everyone,
but I leave it as an exercise for readers to
determine what satisfaction is obtained by the
authors of tools that turn threat into reality and
lay waste to millions of dollars of investments.”
--"Real 802.11 Security", William Arbaugh and
Jon Edney, as quoted in link Ch 4f
44. WTLS and ECC
WTLS (Wireless Transport Layer Security)– Used by many smaller wireless devices
ECC (Elliptic Curve Cryptography)
– A more efficient cryptography method than
the RSA algorithm used on the Internet
– Used on small wireless devices to save power
45. Free SSL for Everyone
Cloudflare usesECC
This made
certificates so
cheap, they offer it
free to everyone
Link Ch 4p
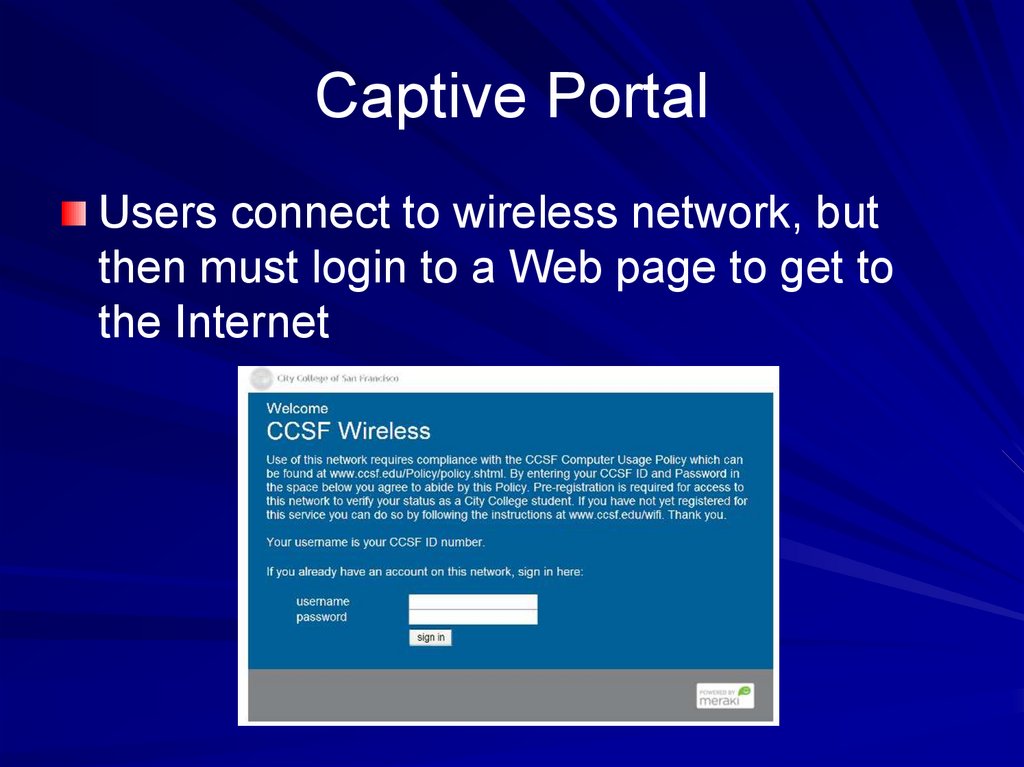
46. Captive Portal
Users connect to wireless network, butthen must login to a Web page to get to
the Internet
47. Common Captive Portals
Free Internet access– Users agree to Terms of Service
Paid Internet access
– Users must enter a credit card number or log
in to a prepaid account
Alternative to 802.1x
– Require users to authenticate
– Can be simpler than configuring 802.1x
48. Hot Spots and Isolation Mode
Each client is on a separate VLAN, ineffect
– Isolates clients better
– Protects clients from each other
– Done at Starbuck's
Does not protect against
– Evil twin
– Sniffing unencrypted wireless traffic directly in
Monitor mode
49. Other Security Concerns
Change default administrator passwordMAC filtering
– Allows only approved MAC addresses to
connect
– Easily sniffed & spoofed
50. CCSF Wardriving
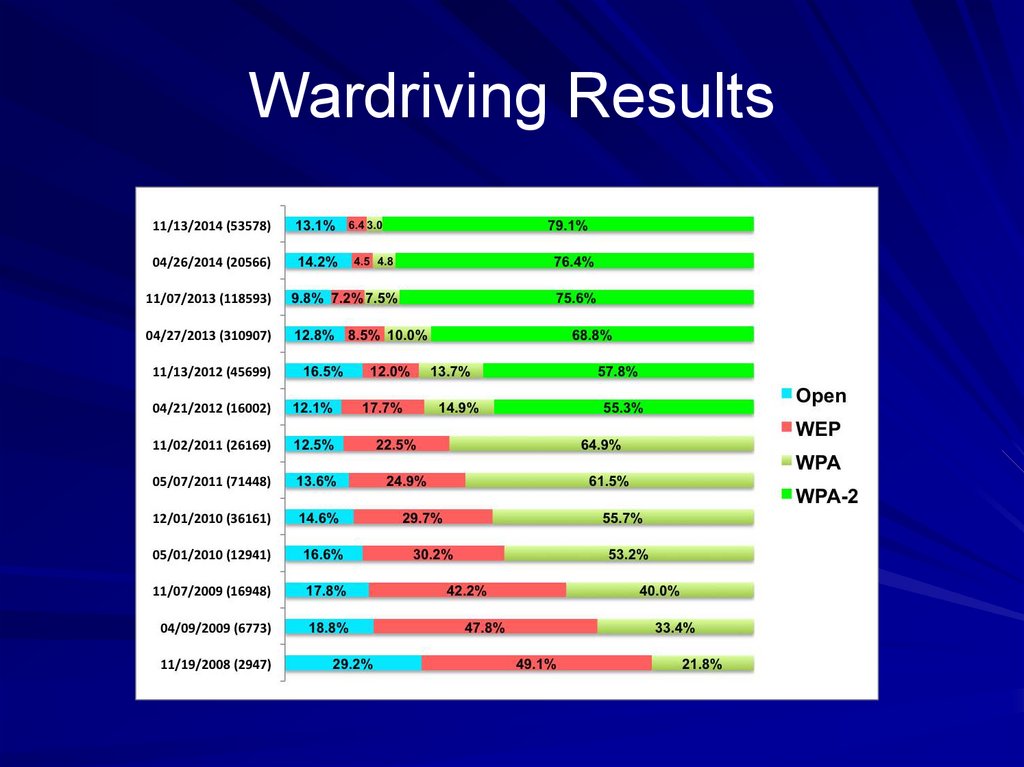
Sat., April 25, 2015, 9 am, SCIE 20051. Wardriving Results
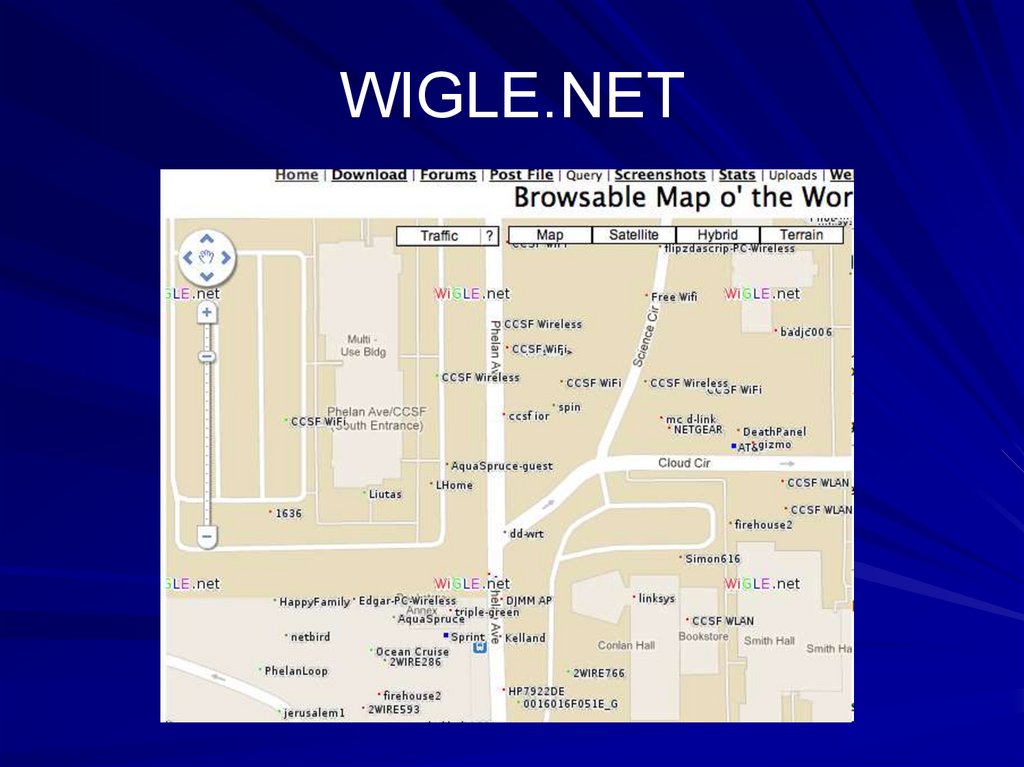
52. WIGLE.NET
53. Wardriving
Part of a wireless auditFinds "Rogue" access points
– Unauthorized routers added to network
Finds "Evil Twins"
– Access points spoofing the authorized ones to
perform MITM attacks
54. Change Default SSID
Conceals the real model of your routerMakes attackers work harder
55. Disabling SSID (Service Set Identifier) Broadcasts
SSID is the name that identifies your network,such as "Linksys" or "CCSF Wifi"
Disabling it only stops sloppy attackers who use
NetStumbler
SSID is in every packet sent anyway
56. Rogue Access Points
Unauthorized devices attached to networkCan exfiltrate data to attacker
Can allow attacker easier access to
network
57. Evil Twins
A rogue access point with the same SSIDas the real company WLAN
– Such as "CCSF Wireless"
Users will automatically connect to the evil
twin if it has a stronger signal
58. WiFi Pineapple
Automates eviltwin and other
wireless attacks
Link Ch 4q
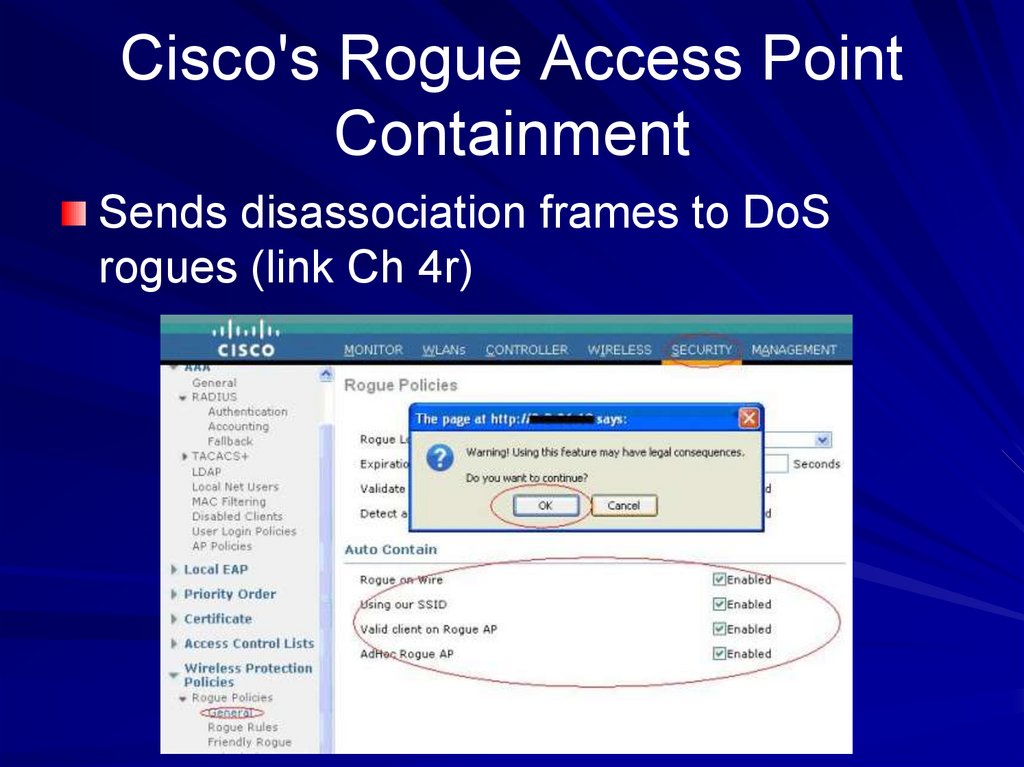
59. Cisco's Rogue Access Point Containment
Sends disassociation frames to DoSrogues (link Ch 4r)
60. Jamming and Interference
Attackers can use radio transmissions tointerfere with Wi-Fi
Changing channel or power levels may
help to resist the attack
Disassociation Frames are the most
effective DoS attack
61. Near Field Communications (NFC)
NFC is used to exchangeinformation over short
distances
Smartphones use it to
exchange information
Credit cards and Bart tickets
contain NFC chips
Google Wallet
62. Bluetooth Wireless
Short-range connectionsIn 'Discovery Mode", a
Bluetooth device broadcasts
its MAC address, to allow
"pairing"
– PINs are often set to 0000
– Turn off Discovery mode to
prevent the attacks on the next
slide
63. Bluesnarfing and Bluejacking
Bluejacking– Unauthorized sending of text messages from
a Bluetooth device
Bluesnarfing
– Access to or theft of data from a Bluetooth
connection
Bluebugging
– Take over a mobile phone
– Listen to calls, send messages, and more
64. Exploring Remote Access
65. Remote Access
Allows users who are travelling to connectto internal network services
Remote Access Service
– Through dial-up or VPN (Virtual Private
Network)
66. Components
Access Method– Dial-up or VPN
Authentication
– Require secure authentication because users
may use insecure lines
Access Control
– User authorization
– Client health
67. Telephony and Dial-Up RAS
Client and sever need phone lines andmodems
Requires POTS line (Plain Old Telephone
Service)
Requires a long-distance phone call
Uses PPP (Point-to-Point Protocol)
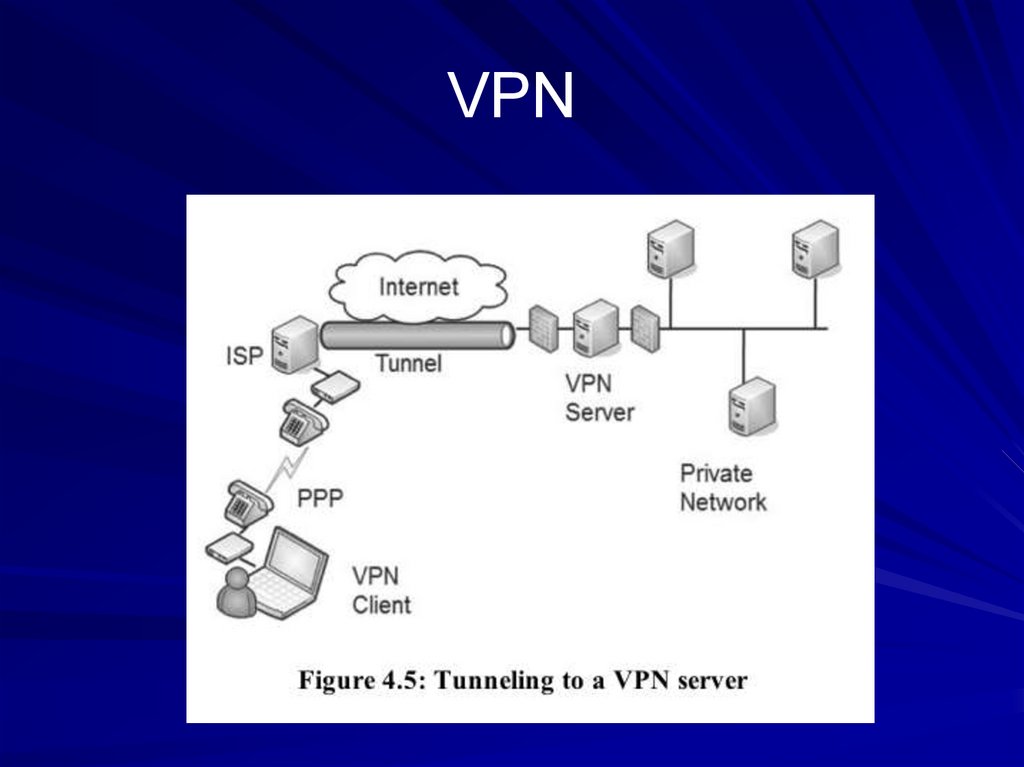
68. VPN
Uses the InternetFaster and cheaper than Dial-up
Uses tunneling to move LAN packets over
the Internet
69. VPN
70. VPN Concentrator
Used at large companiesIncludes
– Strong encryption and authentication
– Handles many clients
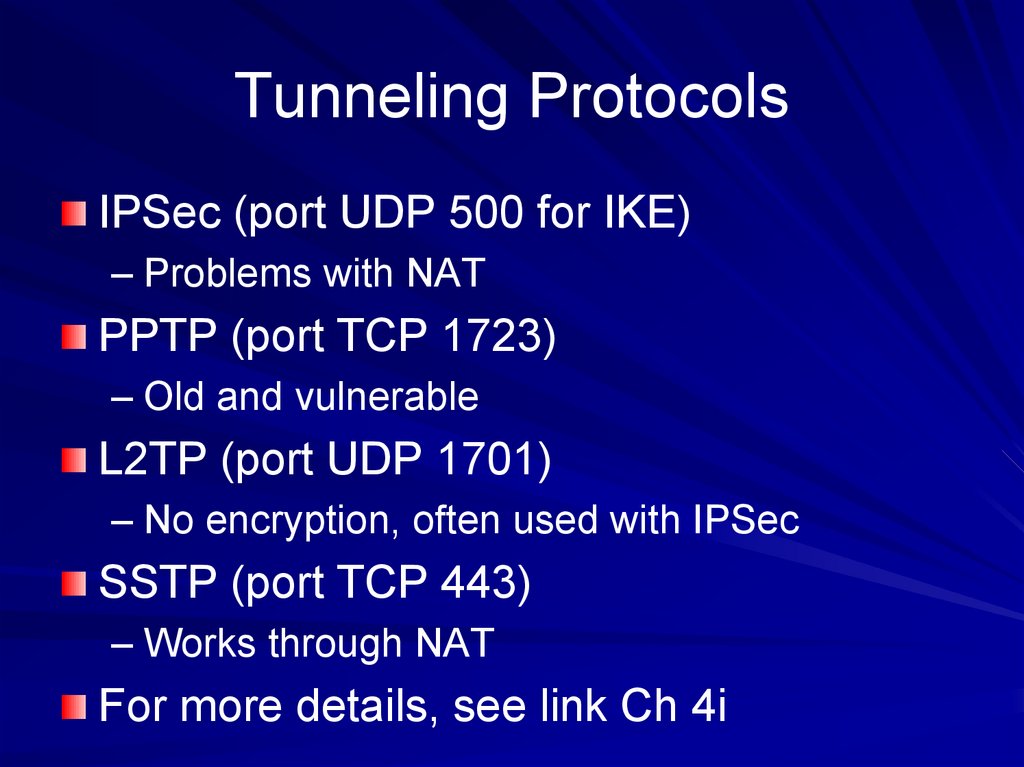
71. Tunneling Protocols
IPSec (port UDP 500 for IKE)– Problems with NAT
PPTP (port TCP 1723)
– Old and vulnerable
L2TP (port UDP 1701)
– No encryption, often used with IPSec
SSTP (port TCP 443)
– Works through NAT
For more details, see link Ch 4i
72. IPsec as a Tunneling Protocol
IPsec has two modes– Transport Mode
Only the payload is encrypted
– Tunnel Mode
The entire IP packet is encrypted
Uses IKE over UDP port 500 to
authenticate clients
Creates Security Associations (SAs) for
the VPN
73. AH and ESP
IPsec can use– AH (Authentication Header) alone
for Authentication and Integrity
no encryption
Protocol 51
– or ESP (Encapsulating Security Payload)
to encrypt the data
providing Confidentiality, Integrity, and
Authentication
Protocol 50
Link Ch 4j
74. L2TP and IPsec
L2TP creates a tunnel, but withoutencryption
– No confidentiality
L2TP/IPsec used together provide
– Authentication
from Authentication Header
on Protocol 51
– Encryption
from Encapsulating Security Payload (ESP)
on Protocol 50
75. NAT and IPsec
NAT changes the IP addresses of packetsIPsec detects this change as packet
damage and discards it
To use IPsec through NAT, use
– NAT-T (NAT Traversal) (link Ch 4k), or
– Another tunneling protocol such as SSTP
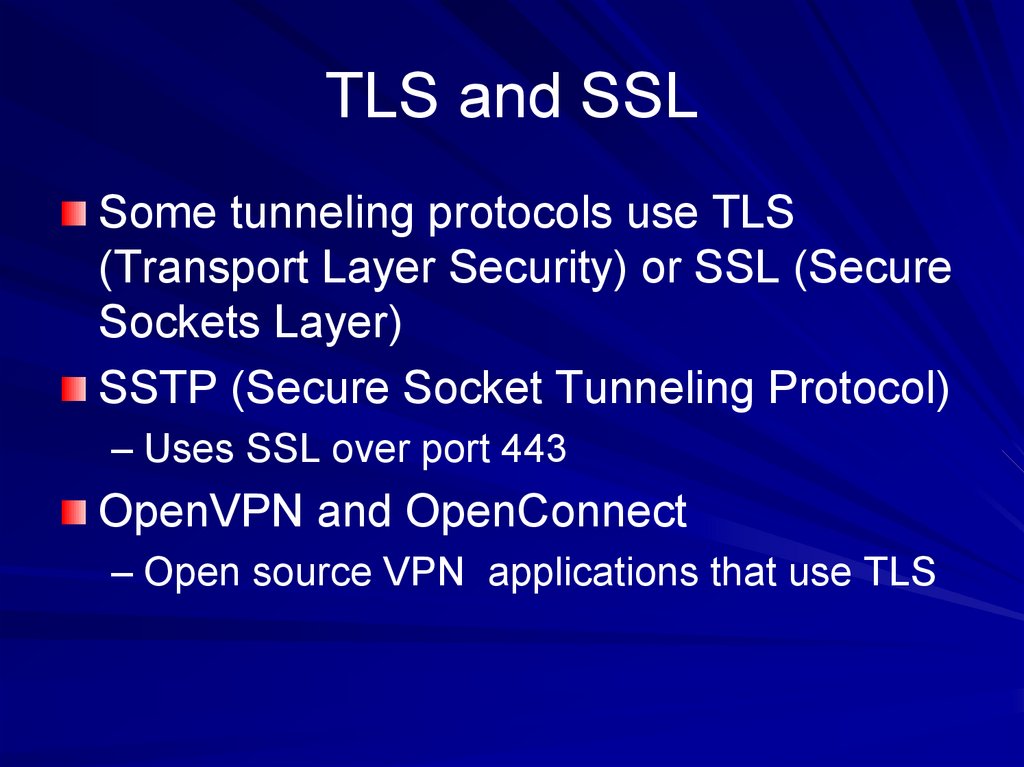
76. TLS and SSL
Some tunneling protocols use TLS(Transport Layer Security) or SSL (Secure
Sockets Layer)
SSTP (Secure Socket Tunneling Protocol)
– Uses SSL over port 443
OpenVPN and OpenConnect
– Open source VPN applications that use TLS
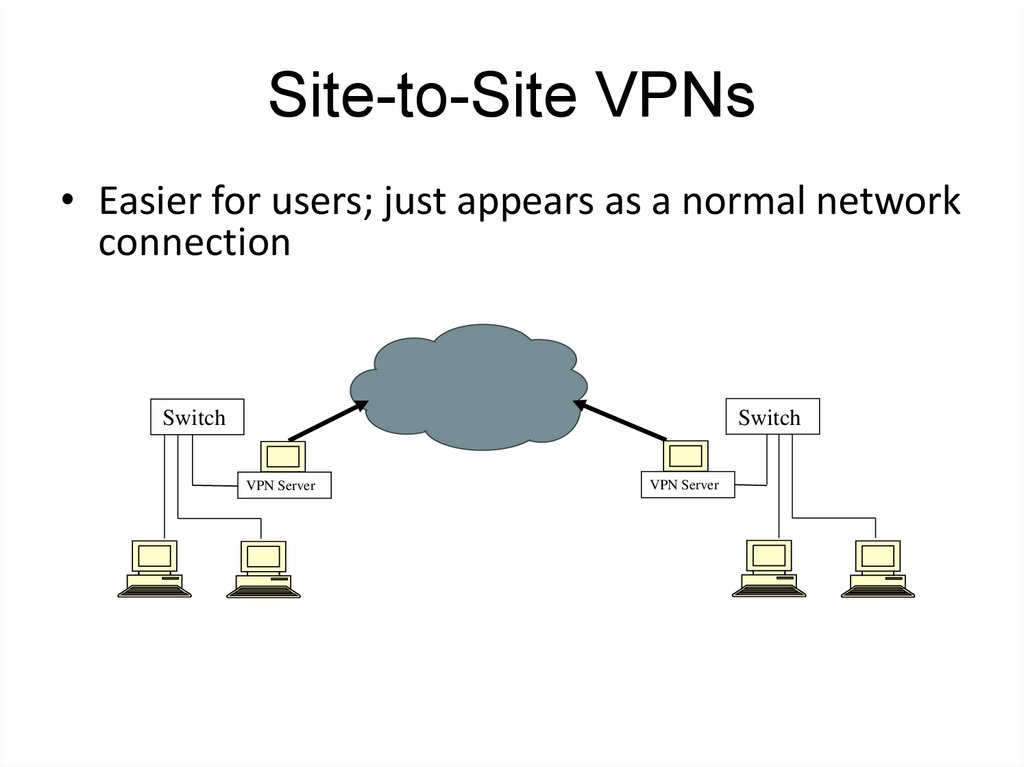
77. Site-to-Site VPNs
• Easier for users; just appears as a normal networkconnection
Switch
Switch
VPN Server
VPN Server
78. VPN Over Open Wireless
Public wireless hot spots often have littleor no security
Using a VPN protects you by adding a
layer of encryption
79. Free VPN
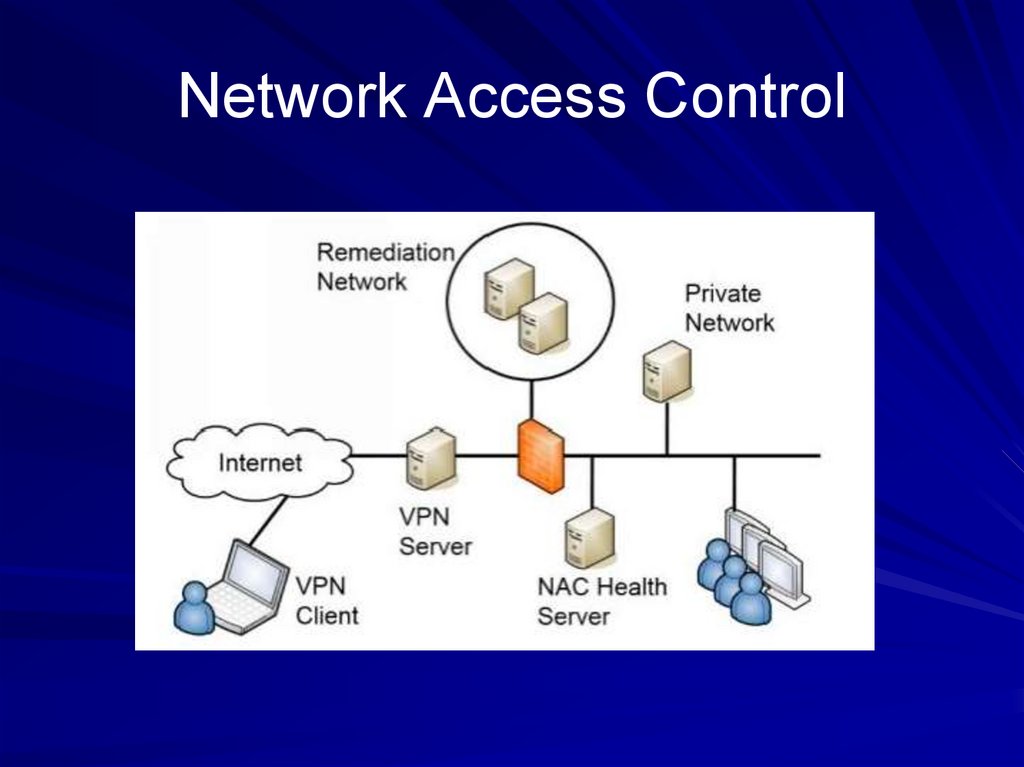
Link Ch 4s80. Network Access Control
Checks health of client before allowing it toconnect to the company LAN
– Up-to-date patches and antivirus, firewall on
– Health agent runs on client
Authentication
– NAC can deny access if clients don't provide
valid credentials






















































 Интернет
Интернет








