Похожие презентации:
Lecture 4. Term 6. Network Etiquette (Netiquette)
1.
Lecture 4. Term 6.Network Etiquette
(Netiquette)
2.
Plan:1. Notion of netiquette.
2. Recommendations and core rules of
netiquette.
3. Netiquette for discussion groups.
4. Netiquette for information retrieval.
Copyright in cyberspace.
5. E-mail etiquette.
6. Violations of netiquette.
3.
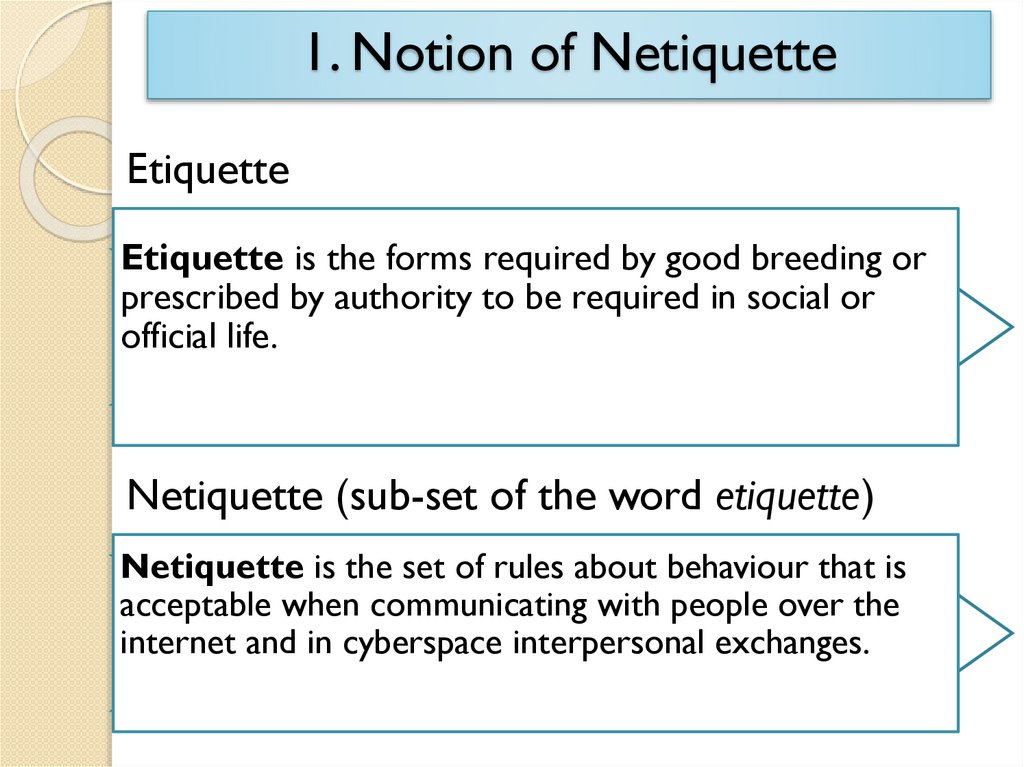
1. Notion of NetiquetteEtiquette
Etiquette is the forms required by good breeding or
prescribed by authority to be required in social or
official life.
Netiquette (sub-set of the word etiquette)
Netiquette is the set of rules about behaviour that is
acceptable when communicating with people over the
internet and in cyberspace interpersonal exchanges.
4.
1. Electronic forms ofmodern communication:
7. Electronic
advertising,
including
spam
6. Animation,
movies,
music, videos
created using
modern IT
- social networks
- virtual communities
- chats
- blogs
- forums
- sites
2.Virtual
museums,
galleries,
exhibition halls,
etc.
Phenomena
of digital
cultures:
5. Electronic
media (on-line
magazines,
newspapers)
3. Education
(distance,
electronic)
4. Electronic archives,
reference systems,
encyclopedias,
dictionaries, libraries
5.
2. Recommendations and Core Rules of Netiquette1.
Psychological,
emotional
Netiquette
Recommendations
:
2.Technical,
design
3.
Administrative
- use of lines of a certain
length,
- restrictions on the size
of a message,
- formatting (bold, italic,
color, background, etc.),
- the admissibility of
writing messages in
UPPERCASE
- naming rules (titles)
for topics,
- quoting rules,
- advertising
admissibility,
- flame admissibility,
- the need to adhere
to community topics,
etc.
:
- addressing,
- using
emoticons,
- supporting
newcomers or
ignoring their
questions, etc.
6.
Rule 1: Remember the HumanRemember to treat others the way
they want to be treated.
Respond to others courteously.
Try not to hurt others’ feelings or
cause offense.
7.
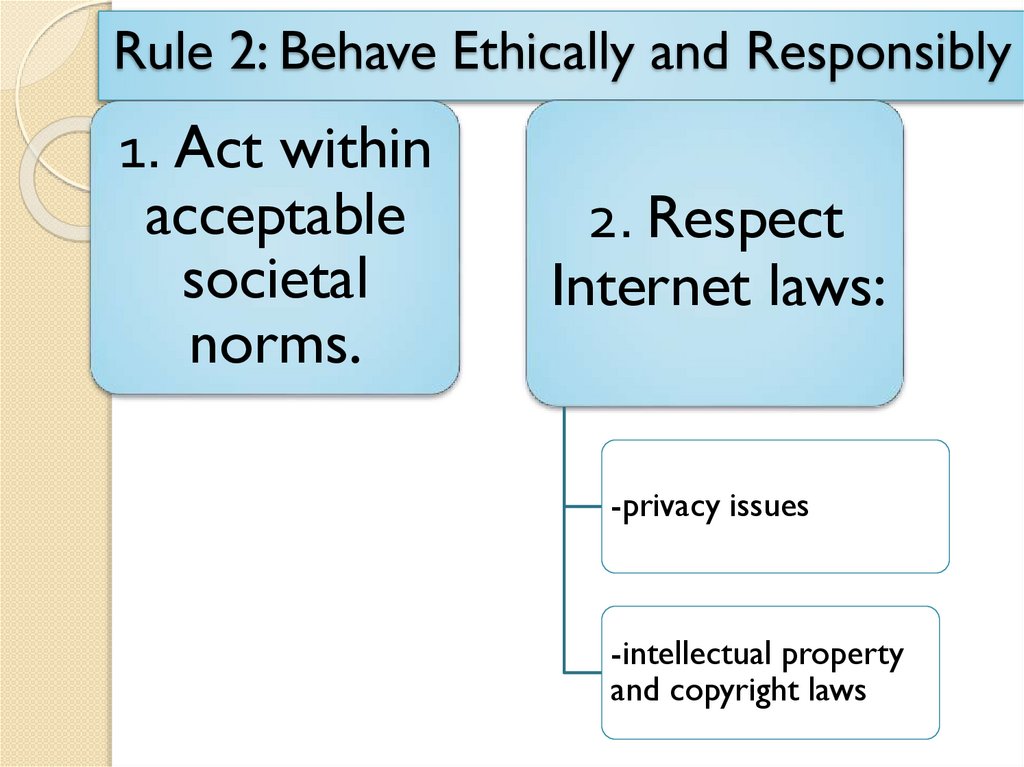
Rule 2: Behave Ethically and Responsibly1. Act within
acceptable
societal
norms.
2. Respect
Internet laws:
-privacy issues
-intellectual property
and copyright laws
8.
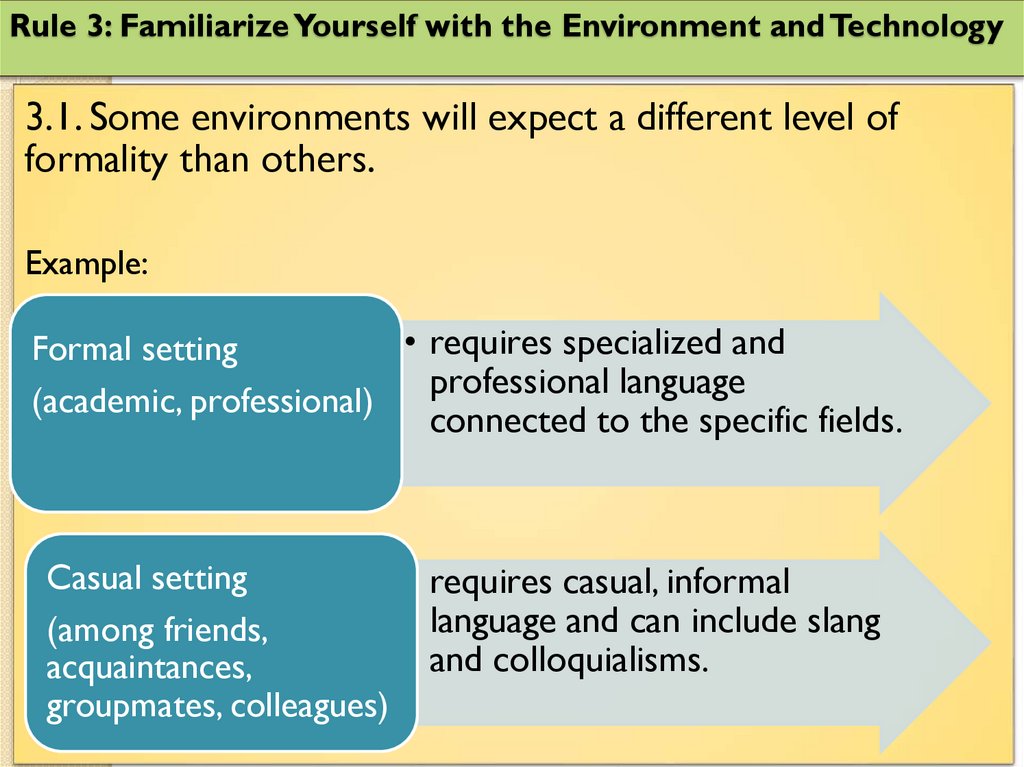
Rule 3: Familiarize Yourself with the Environment and Technology3.1. Some environments will expect a different level of
formality than others.
Example:
• requires specialized and
Formal setting
professional language
(academic, professional)
connected to the specific fields.
Casual setting
• requires casual, informal
language and can include slang
(among friends,
and colloquialisms.
acquaintances,
groupmates, colleagues)
9.
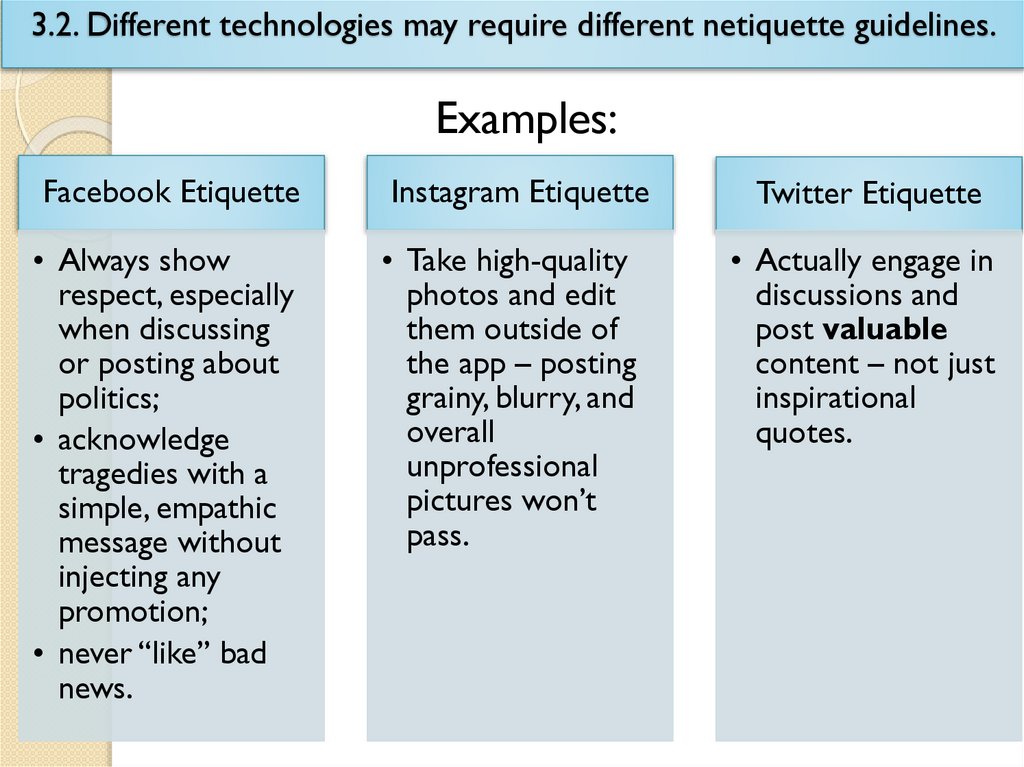
3.2. Different technologies may require different netiquette guidelines.Examples:
Facebook Etiquette
Instagram Etiquette
Twitter Etiquette
• Always show
respect, especially
when discussing
or posting about
politics;
• acknowledge
tragedies with a
simple, empathic
message without
injecting any
promotion;
• never “like” bad
news.
• Take high-quality
photos and edit
them outside of
the app – posting
grainy, blurry, and
overall
unprofessional
pictures won’t
pass.
• Actually engage in
discussions and
post valuable
content – not just
inspirational
quotes.
10.
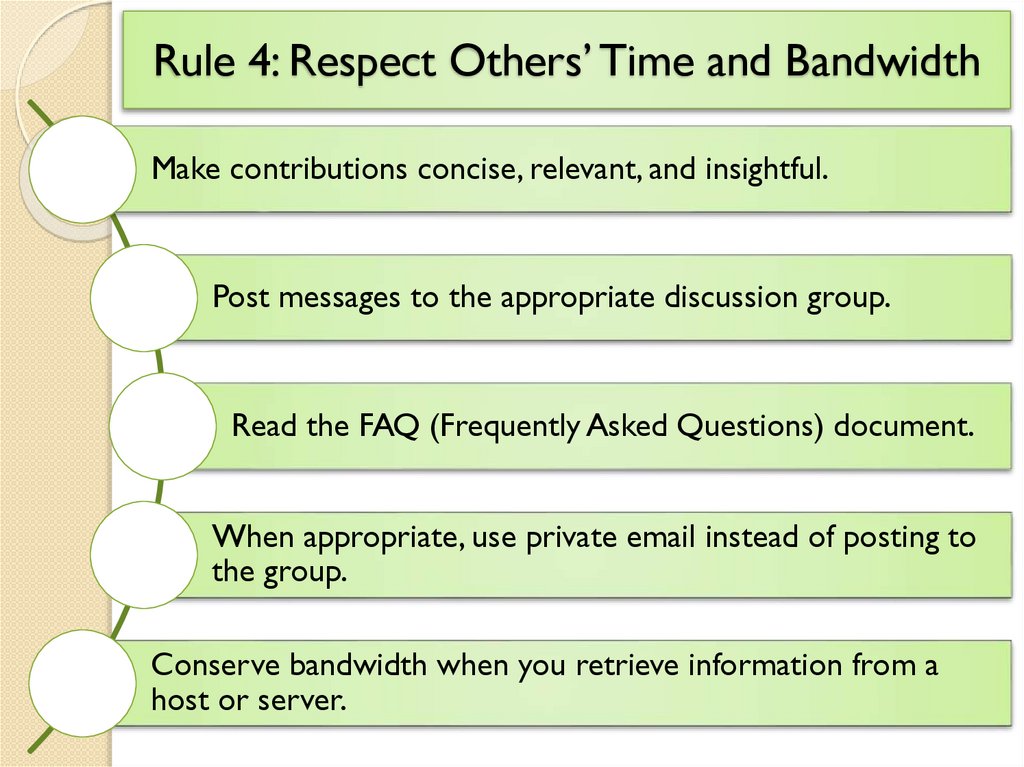
Rule 4: Respect Others’ Time and BandwidthMake contributions concise, relevant, and insightful.
Post messages to the appropriate discussion group.
Read the FAQ (Frequently Asked Questions) document.
When appropriate, use private email instead of posting to
the group.
Conserve bandwidth when you retrieve information from a
host or server.
11.
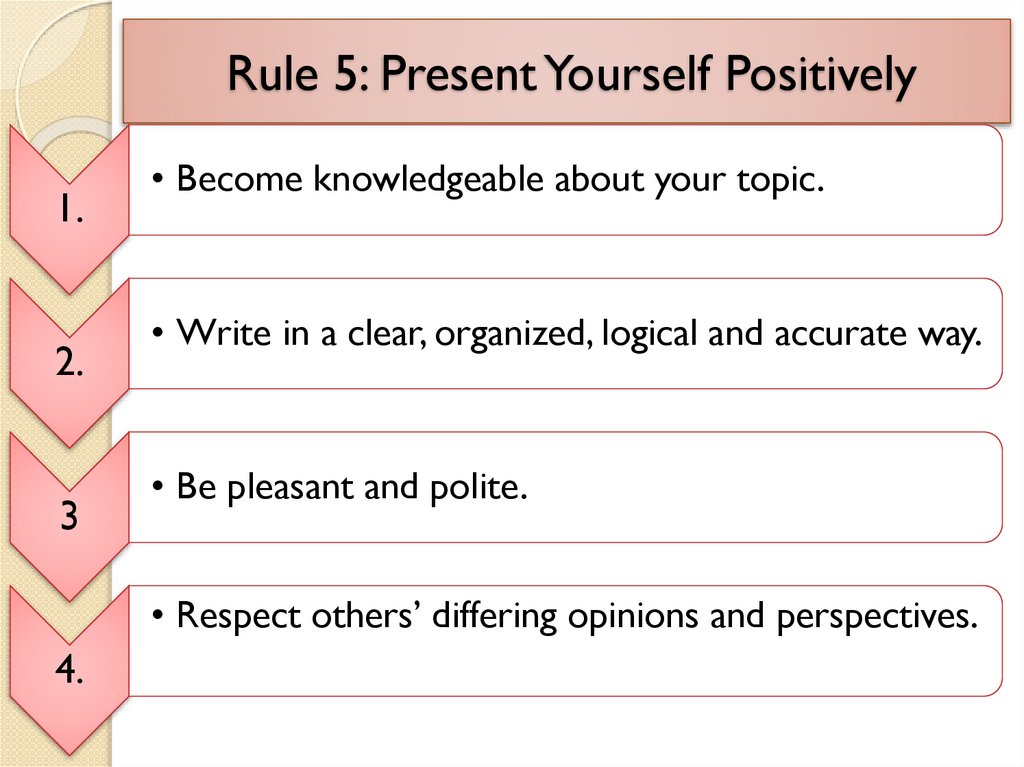
Rule 5: Present Yourself Positively1.
2.
3
• Become knowledgeable about your topic.
• Write in a clear, organized, logical and accurate way.
• Be pleasant and polite.
• Respect others’ differing opinions and perspectives.
4.
12.
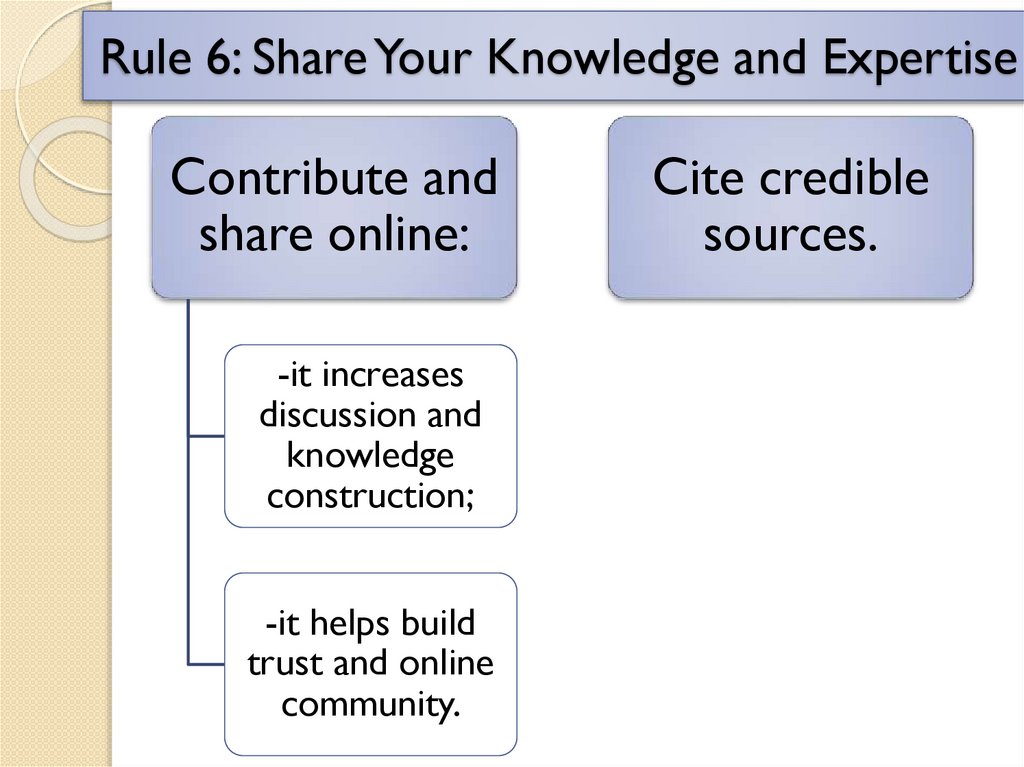
Rule 6: Share Your Knowledge and ExpertiseContribute and
share online:
-it increases
discussion and
knowledge
construction;
-it helps build
trust and online
community.
Cite credible
sources.
13.
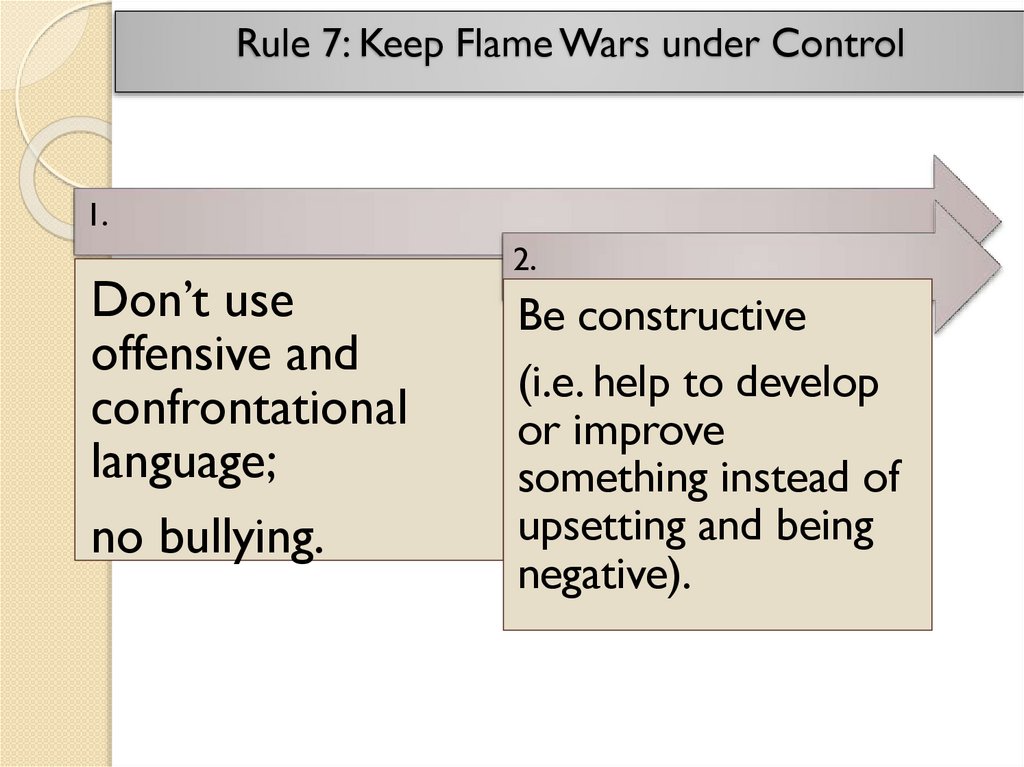
Rule 7: Keep Flame Wars under Control1.
Don’t use
offensive and
confrontational
language;
no bullying.
2.
Be constructive
(i.e. help to develop
or improve
something instead of
upsetting and being
negative).
14.
3.Netiquette for Discussion Groups
Discussion groups
are areas where notes
on a topic of common
interest are posted
and stored for anyone
to read.
Discussion groups are
also known as
-newsgroups,
-message boards,
-bulletin boards,
-forums.
15.
Netiquette for Discussion Groups Rules:1. If you're getting started with newsgroups,
check out the many useful articles in these
newsgroups. Do this before you post anything
anywhere.
2. Lurk for a while before you post. "Lurking" is
reading the discussion group correspondence
without actually participating.
3. Get and read a copy of the FAQ (Frequently
Asked Questions) document for the group, if it
has one.
16.
4. When you start posting, post appropriatecomments and questions.
5.Try to fit in with the tone and style of the
discussion group.
6. Phrase your postings politely.
7. Make sure your postings are correct.
8. Post messages to the appropriate discussion
group.
17.
4.1.Netiquette for Information Retrieval (Rules):
1. Don't stay logged in when
you're not doing anything.
2. If possible, log in at off-peak
hours.
3. Download only files you actually
need.
18.
4.2. Copyright in CyberspaceCopyright is really a collection of rights that belong to the
creator of an original work in a "fixed and tangible" form, for
example, a book, an article, a painting, or a recording.
Among them are the rights to
- reproduce the work;
- produce derivative works;
- perform the work in public.
The purpose of copyright law is to ensure that the person
who creates an "original work" can benefit from it.
19.
Frequently asked questionsQ.1: Does that mean I can't write a research paper
without violating someone's copyright?
For writers, the doctrine of fair use generally permits
quotation of short excerpts of a work in a review or
criticism, in a scholarly or technical work.
A use is more likely to be considered "fair" if it's for
educational or nonprofit purposes and if the resulting
product doesn't compete with the original work.
20.
Q.2:What's the publicdomain?
Anything that's not under copyright is in the
public domain.
That means:
Anyone can freely copy and distribute it.
You can give copies away for free, or, if
anyone's willing to pay, you can charge them.
21.
Q.3: Can I use email a friend sent me to bolstermy position in an argument I'm pursuing in a
discussion group?
Don't do it without permission.
Posting private email to the net without
the author's OK is considered very poor
Netiquette.
22.
10. Rememberthat your tone
can't be heard in
e-mail.
9. Don't send chain
letters, virus
warnings, or junk
mail.
8. Agree on
acronyms to use
that quickly identify
actions.
7. Be careful with
group e-mail.
1.Be formal, not
sloppy.
5.E-mail use
professional
standards
6. Remember
that e-mail
isn't private.
2. Keep messages
brief and to the
point.
3. Use
sentence case.
4. Use the blind
copy and courtesy
copy
appropriately.
5. Don't use e-mail
as an excuse to
avoid personal
contact.
23.
1. Be formal, not sloppy.Follow standard writing
protocol.
Apply traditional spelling,
grammar and punctuation
rules.
24.
2. Keep messages brief and to the point.Don’t make your message long.
Concentrate on one subject
per message whenever
possible.
25.
3. Use sentence case (режим наборакаждого предложения с большой буквы)
1. USING ALL CAPITAL LETTERS LOOKS AS
IF YOU'RE SHOUTING.
2. Using all lowercase letters looks lazy.
3. For emphasis, use asterisks or bold
formatting to emphasize important words.
4. Do not, however, use a lot of colors or
graphics embedded in your message
26.
4. Use the blind copy and courtesycopy appropriately.
Blind carbon copy (BBC) (скрытая копия) -
a feature of e-mail programs that allows a user to
send a copy of an e-mail message to a recipient
without notifying other recipients that this was
done.
Courtesy copy (CC) ( персонально
адресованная электронная копия
сообщения с приложением списка рассылки)
- a copy of an electronic mail message which is sent
to another person in addition to the original
recipient.
27.
5. Don't use e-mail as an excuse toavoid personal contact.
1
• Don't forget the value of face-toface or even voice-to-voice
communication.
2
• E-mail communication isn't
appropriate when sending confusing
or emotional messages.
3
• Don't use e-mail to avoid an
uncomfortable situation or to
cover up a mistake
28.
6. Remember that e-mail in anorganization isn't private.
E-mail is considered
company property and can
be retrieved, examined, and
used in a court of law.
Unless you are using an
encryption device
(hardware or software),
you should assume that email over the Internet is
not secure.
29.
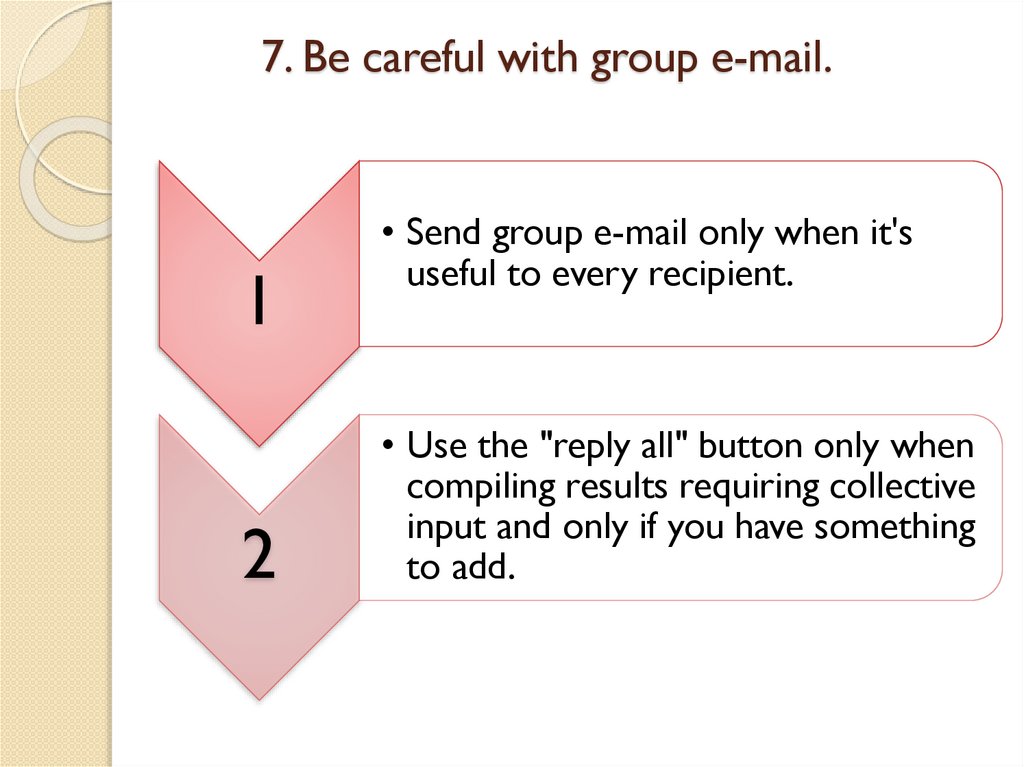
7. Be careful with group e-mail.1
2
• Send group e-mail only when it's
useful to every recipient.
• Use the "reply all" button only when
compiling results requiring collective
input and only if you have something
to add.
30.
8. Agree on acronyms to use that quicklyidentify actions.
For example, your team could use <AR> to
mean "Action Required" or <MSR> for the
Monthly Status Report.
It's also a good practice to include the word
"Long" in the subject field, if necessary, so
that the recipient knows that the message
will take time to read.
31.
9. Don't send chain letters, viruswarnings, or junk mail.
10. Remember that your tone can't
be heard in e-mail.
In an attempt to infer tone of voice, some
people use emoticons, but use them
sparingly so that you don't appear
unprofessional.
32.
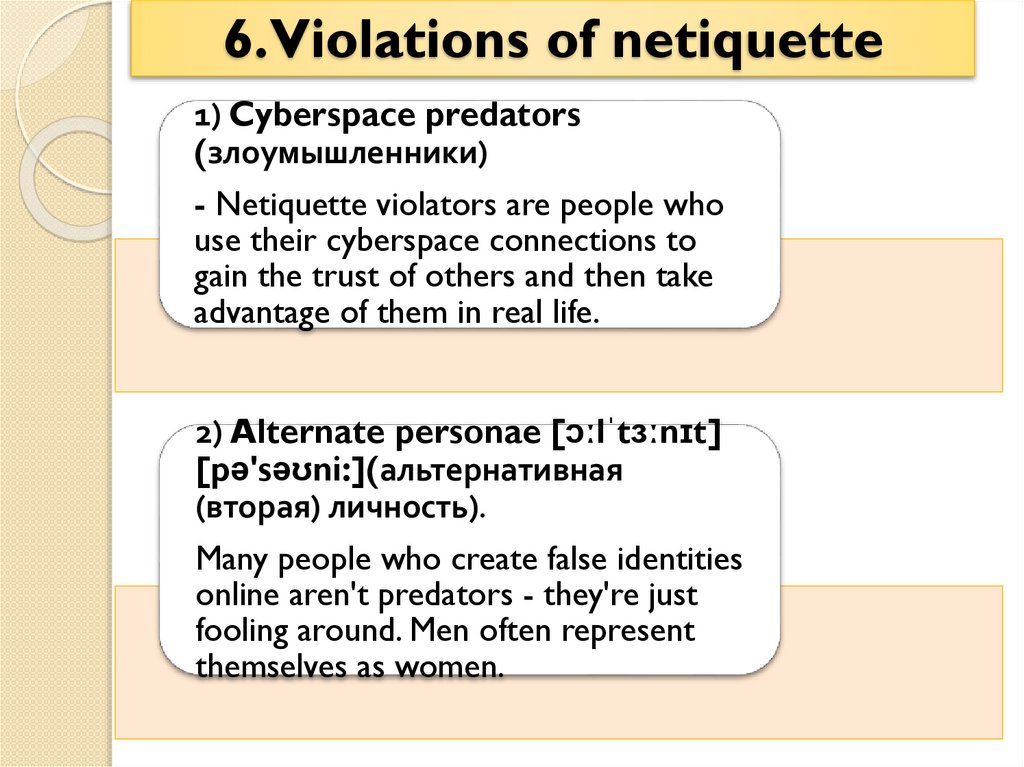
6.Violations of netiquette1) Cyberspace predators
(злоумышленники)
- Netiquette violators are people who
use their cyberspace connections to
gain the trust of others and then take
advantage of them in real life.
2) Alternate personae [ɔːlˈtɜːnɪt]
[pə'səʊni:](альтернативная
(вторая) личность).
Many people who create false identities
online aren't predators - they're just
fooling around. Men often represent
themselves as women.
33.
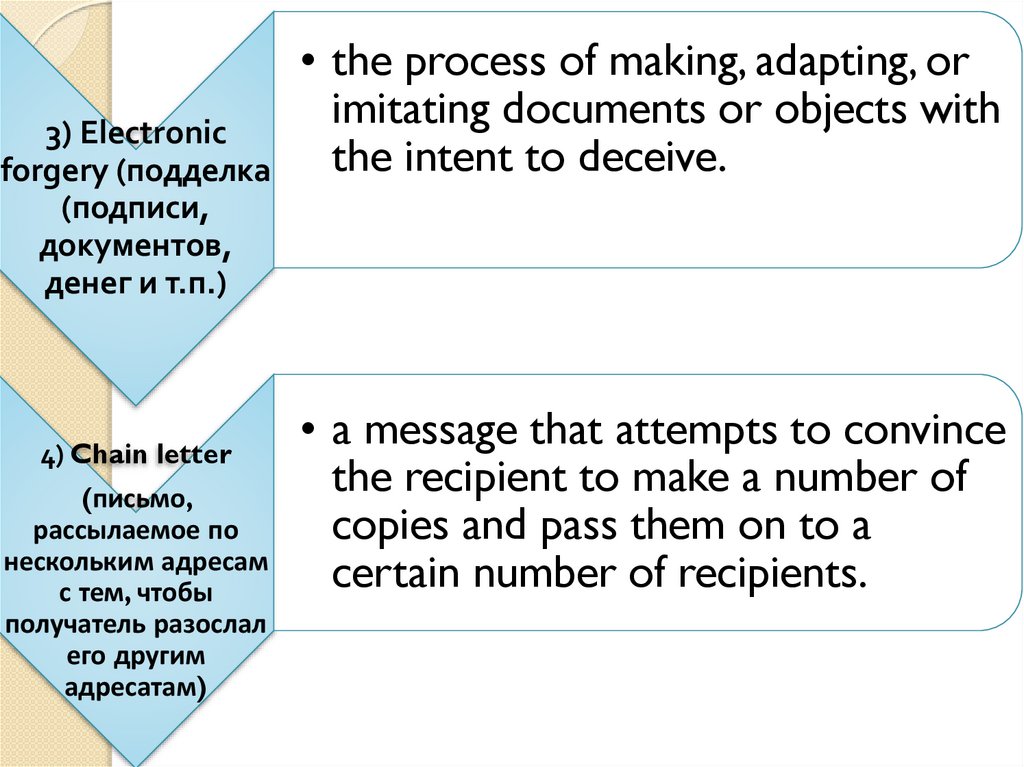
• the process of making, adapting, orimitating
documents
or
objects
with
3) Electronic
the intent to deceive.
forgery (подделка
(подписи,
документов,
денег и т.п.)
a
message
that
attempts
to
convince
4) Chain letter
the recipient to make a number of
(письмо,
copies and pass them on to a
рассылаемое по
нескольким адресам
certain number of recipients.
с тем, чтобы
получатель разослал
его другим
адресатам)
34.
5) Electronic hoaxes («утки», фейки, мистификации)the delivery of messages by provoking, lying news, fraud in
transactions, incorrect information, changing the
contents of information, and so forth that cause harm to
the public who know, read and see the information
conveyed.
Examples:
179 year old man in India
Tax for having pets
35.
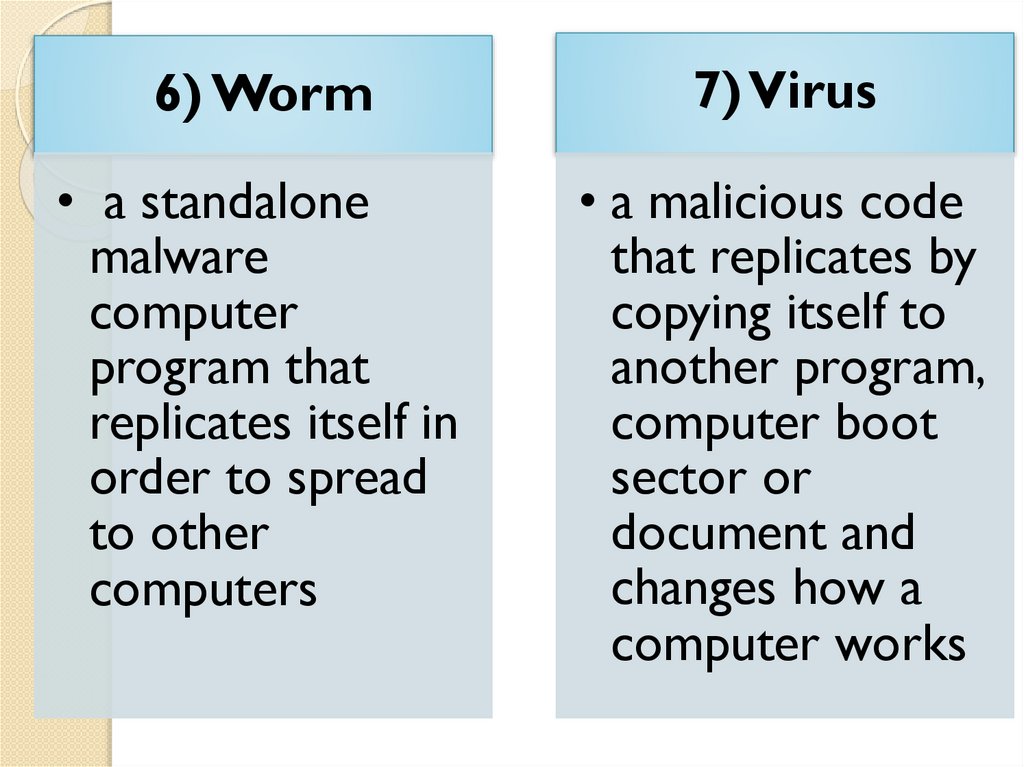
6) Worm7) Virus
• a standalone
malware
computer
program that
replicates itself in
order to spread
to other
computers
• a malicious code
that replicates by
copying itself to
another program,
computer boot
sector or
document and
changes how a
computer works
36.
Task. Watch the movie 10 Examples of Good Netiquette andwrite the guidelines of network etiquette expressed in it.























 Английский язык
Английский язык








