Похожие презентации:
Chapter 6
1. Introduction to Cryptography
CSSY2201Chapter 6
2. Chapter 6:
1. Message Authentication2. Hash Functions
3. Message Authentication Code (MAC)
4. Key Management
5. Digital Certificates
3. Message Authentication
1.Message Authentication4. Story 1:
Sarah sends an urgent invoice to her client Ahmed viaemail , but a hacker intercepts the email, modified the number
of the bank account, and forwards it on.
Ahmed unknowingly sends the payment to the account number
as what was written on Sarah’s email. By the time they discover
the fraud, the money is gone.
• How could Ahmed ensure that the message is not modified ?
5. Story 2
• Ali gets an email that seems to be from his boss, urgentlyasking for the password to a shared file. Believing the message
is real, Ali sends the password. Later, in a brief conversation,
his boss mentions he never sent such an email—making Ali
realize that a hacker had impersonated his boss to steal the
password.
• How could Ali ensure that the message is coming from a person
who claim to be ?
6. Story 3
Fatma receives an email from her teammate Omar approving abudget increase for their project. She proceeds with the purchase
based on his message. Later, when questioned by management, Omar
insists he never sent the approval and claims someone must have
used his account. With no reliable way to prove whether Omar
actually sent the email or not, Fatma is left responsible for the
unauthorized expense.
How to stop the sender from denying that he has sent the message?
7. Message Authentication requirement
In the context of communications across a network, thefollowing attacks can be identified.
1. Disclosure
2. Traffic Analysis
3. Message Modification.
4. Masquerade
5. Source Repudiation
6. Destination Repudiation
8. Message Authentication
• Message authentication is a mechanism or service used toverify the integrity of a message. Message authentication
assures that data received are exactly as sent (i.e., there is no
modification, insertion, deletion, or replay).
9. Message Authentication
Message authentication is mechanism or services to verify themessage integrity . It is securing the message by :
1. Protecting the integrity of a message
2. Validating identity of originator
3. Provide Non-repudiation of origin
Three functions could be used to provide message authentication :
1. Hash function
2. Message encryption
3. Message authentication code (MAC)
10. 2. Hash function
11. Hash Function
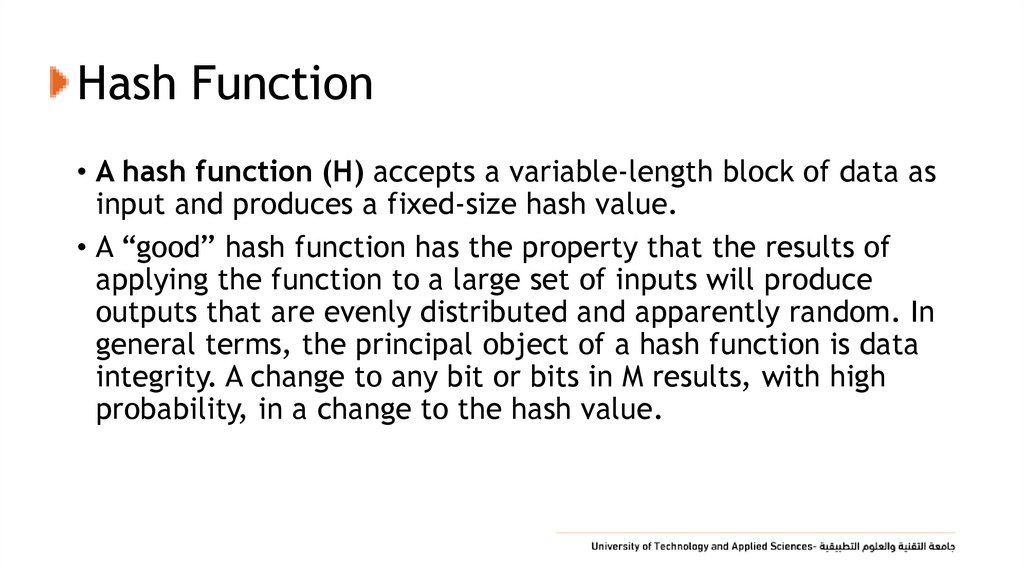
• A hash function (H) accepts a variable-length block of data asinput and produces a fixed-size hash value.
• A “good” hash function has the property that the results of
applying the function to a large set of inputs will produce
outputs that are evenly distributed and apparently random. In
general terms, the principal object of a hash function is data
integrity. A change to any bit or bits in M results, with high
probability, in a change to the hash value.
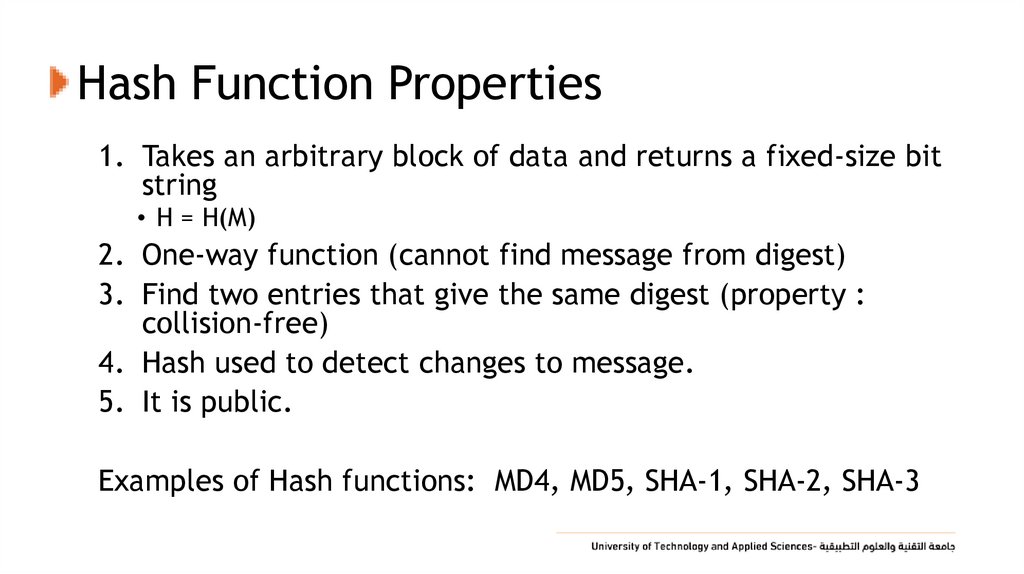
12. Hash Function Properties
1. Takes an arbitrary block of data and returns a fixed-size bitstring
• H = H(M)
2. One-way function (cannot find message from digest)
3. Find two entries that give the same digest (property :
collision-free)
4. Hash used to detect changes to message.
5. It is public.
Examples of Hash functions: MD4, MD5, SHA-1, SHA-2, SHA-3
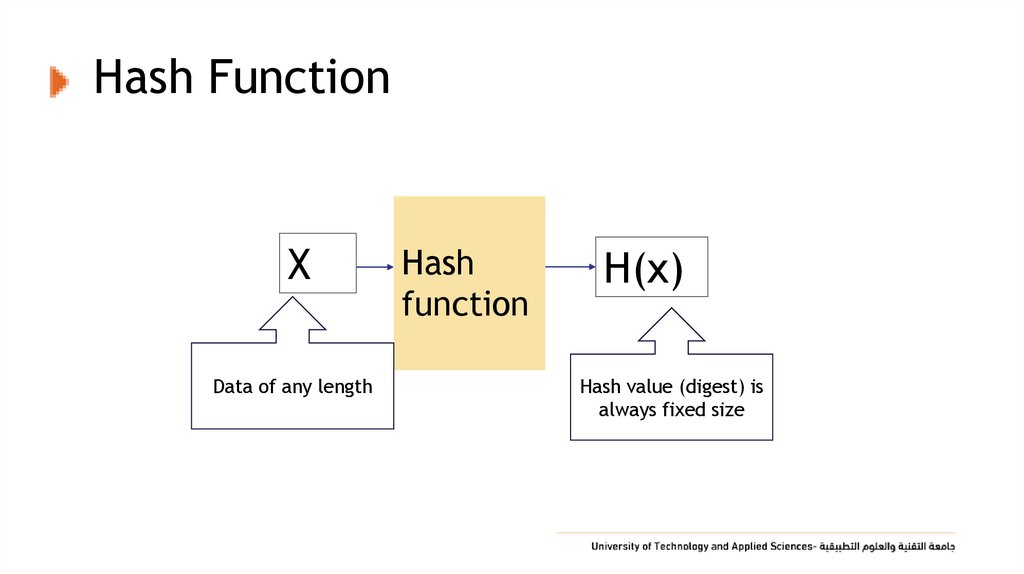
13. Hash Function
XData of any length
Hash
function
H(x)
Hash value (digest) is
always fixed size
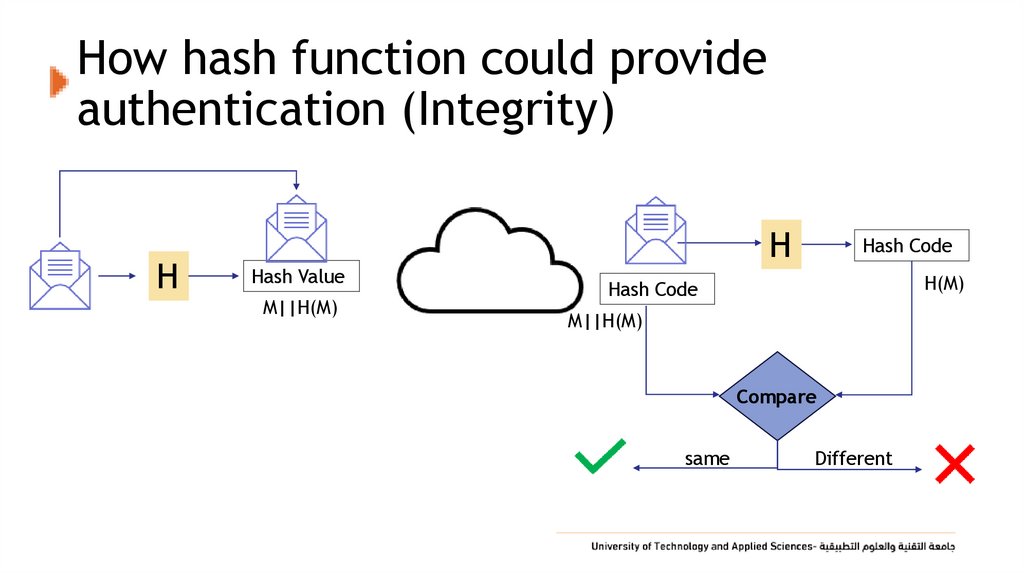
14. How hash function could provide authentication (Integrity)
HH
Hash Value
M||H(M)
Hash Code
H(M)
Hash Code
M||H(M)
Compare
same
Different
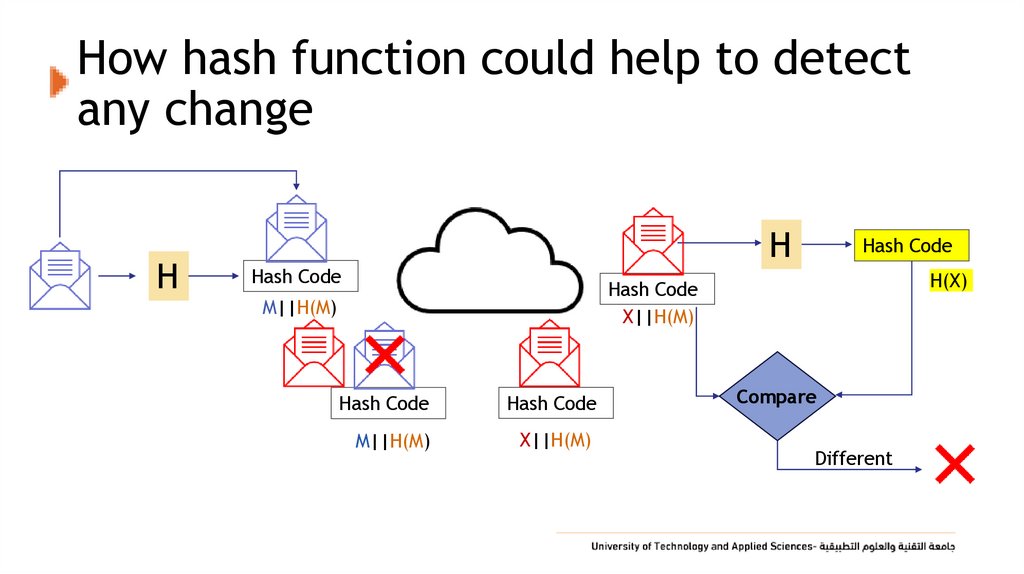
15. How hash function could help to detect any change
HH
Hash Code
Hash Code
H(X)
Hash Code
X||H(M)
M||H(M)
Hash Code
Hash Code
M||H(M)
X||H(M)
Compare
Different
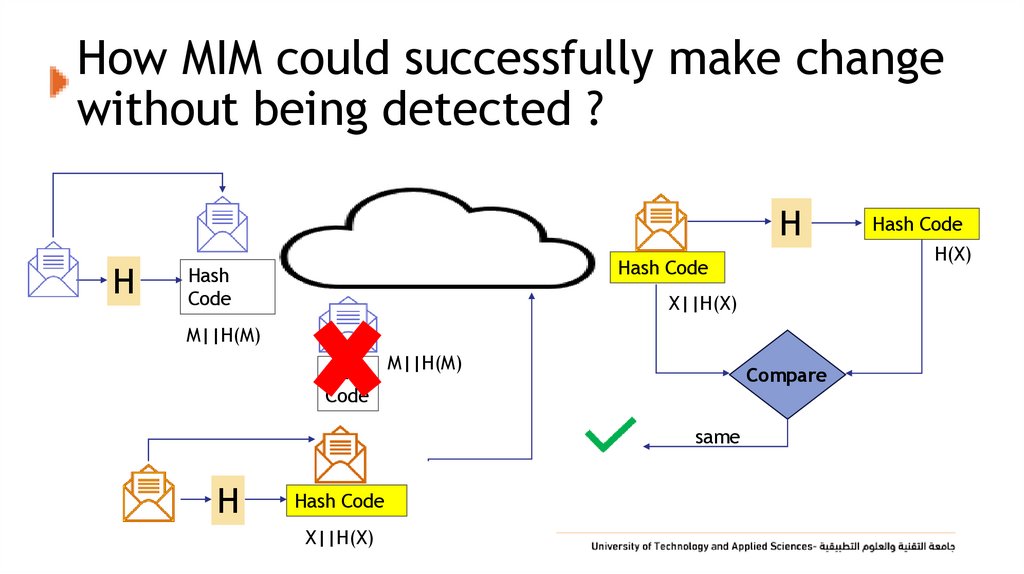
16. How MIM could successfully make change without being detected ?
HH
H(X)
Hash Code
Hash
Code
X||H(X)
M||H(M)
Hash M||H(M)
Code
Compare
same
H
Hash Code
X||H(X)
Hash Code
17. Message Authentication
We want to send a message with the following condition :1. Message is not modified (sent = received )
2. Sender identity is valid
3. Against MIM attack
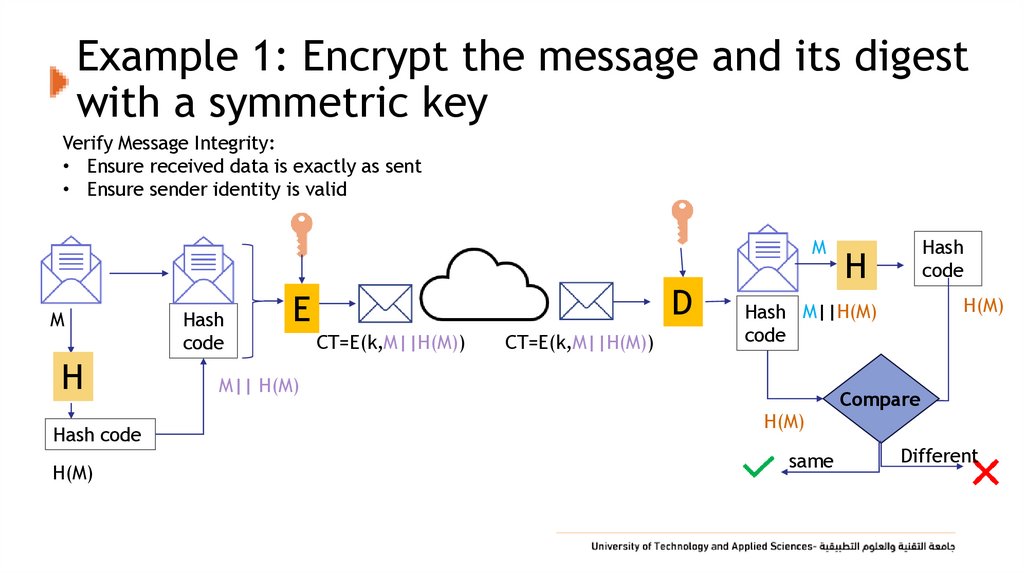
18. Example 1: Encrypt the message and its digest with a symmetric key
Verify Message Integrity:• Ensure received data is exactly as sent
• Ensure sender identity is valid
M
M
H
Hash code
H(M)
Hash
code
D
E
CT=E(k,M||H(M))
CT=E(k,M||H(M))
Hash
code
H
H(M)
Hash M||H(M)
code
M|| H(M)
Compare
H(M)
same
Different
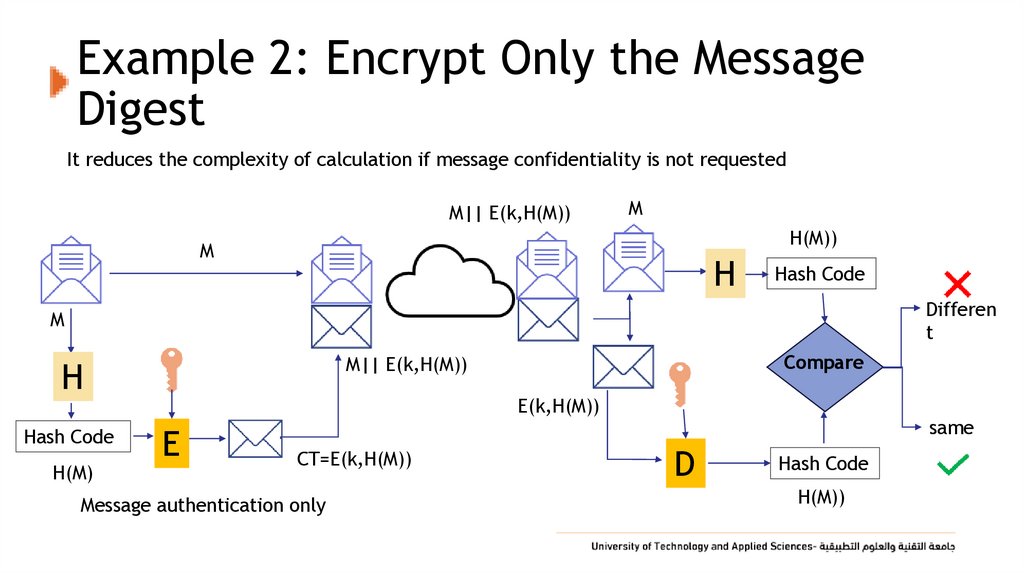
19. Example 2: Encrypt Only the Message Digest
It reduces the complexity of calculation if message confidentiality is not requestedM|| E(k,H(M))
M
H(M))
M
H
Hash Code
Differen
t
M
H
Hash Code
H(M)
Compare
M|| E(k,H(M))
E(k,H(M))
E
CT=E(k,H(M))
Message authentication only
same
D
Hash Code
H(M))
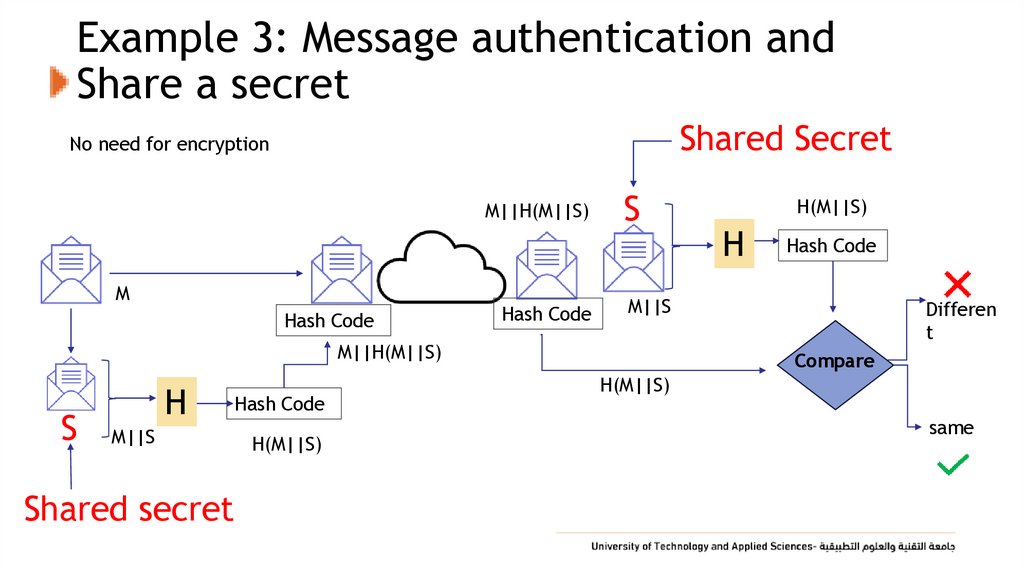
20. Example 3: Message authentication and Share a secret
Shared SecretNo need for encryption
M||H(M||S)
M
Hash Code
Hash Code
S
S
M||S
Shared secret
Hash Code
H(M||S)
H
Hash Code
M||S
M||H(M||S)
H
H(M||S)
Differen
t
Compare
H(M||S)
same
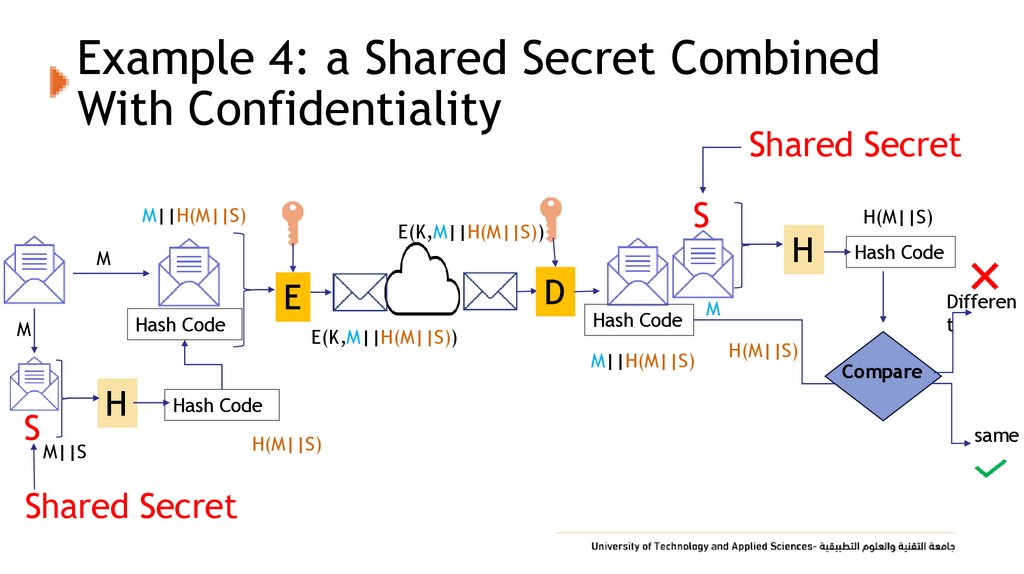
21. Example 4: a Shared Secret Combined With Confidentiality
Shared SecretM||H(M||S)
S
E(K,M||H(M||S))
M
Hash Code
M
D
E
E(K,M||H(M||S))
Hash Code
M||H(M||S)
S
H
H(M||S)
H
Hash Code
Differen
t
M
H(M||S)
Compare
Hash Code
M||S
Shared Secret
H(M||S)
same
22. Other Uses of Hash Functions
1. Used To Create Password Files: When a User Types a Password, theHash of the Password Is Compared to the Saved Hash for Verification
This Approach Is Used by the Majority of Operating Systems.
2. Used To Detect Intrusions and Viruses: Save the H(F) of Each File To
Disk the Antivirus Can Later Check if the File Has Been Altered or Not
by Recalculating its Digest H(F) an Intruder Will Try To Change F
Without Changing H(F) : Very Difficult !
3. Can Be Used To Build PRNG Pseudo-Random Sequence Generators:
Generate Keystreams, Secret Keys
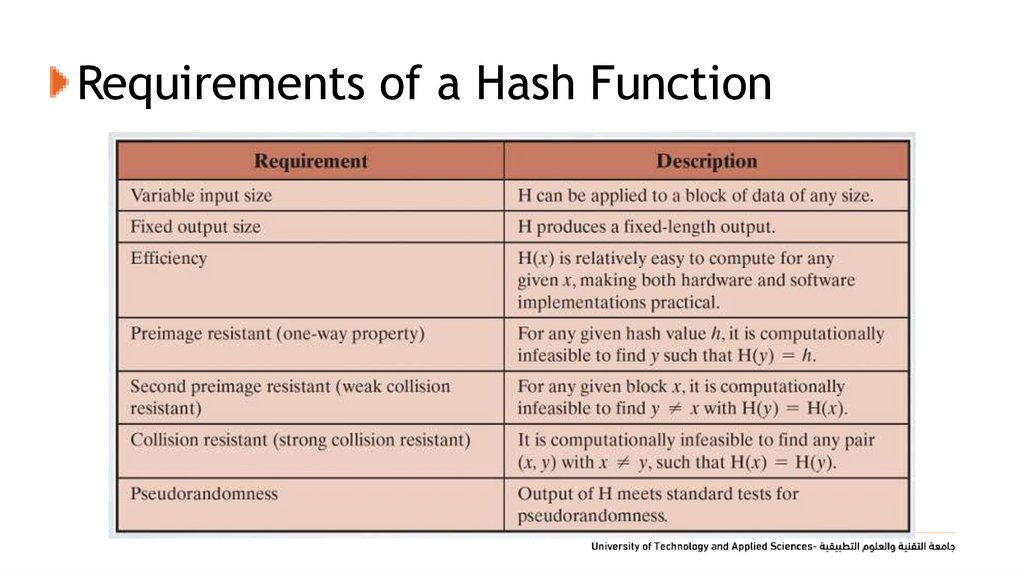
23. Requirements of a Hash Function
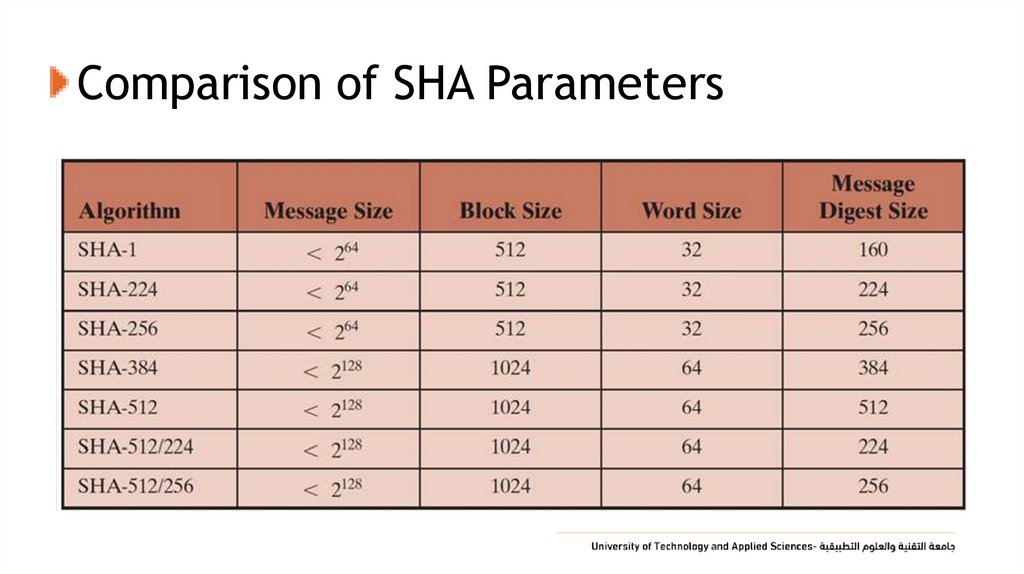
24. Comparison of SHA Parameters
25. SHA-3
• Stands for secure hash algorithm 3.• Developed through a public competition held by NIST. The winning
algorithm, keccak, was chosen in 2012 and standardized as SHA-3 in
2015.
• Designed to be a more secure alternative to previous SHA-2.
• Can be used for data integrity checks, password storage, digital
signatures, and more.
• Developed in response to potential vulnerabilities in the SHA-2 algorithm.
• SHA-2 provides better security against length extension attacks.
• Offers a high level of security and is currently considered secure
for most practical purposes
26. SHA-3
• SHA-512, part of SHA-2, is more widely used due to its longer history, butthis is expected to change over time.
• It can produce hash outputs (digests) of various lengths.
• The standard defines SHA-3-224, SHA-3-256, SHA-3-384, SHA-3-512,
shake128, and shake256.
• The numbers following "SHA-3" and "shake" represent the output length
in bits.
• For example, SHA-3-224 produces a hash output of 224 bits, while SHA-3-512
produces a hash output of 512 bits.
• The shake variants are extendable-output functions (XOFS) that can produce output
of any length.
• The ability to produce different output lengths gives SHA-3 a flexibility
that can be advantageous in different cryptographic applications.
27. Activity 1
1. Create a diagram showing how to use hash function to detect the messagemodification.
2. Create a diagram showing how MIM can attack the message with a hash function
without getting detected by the receiver.
3. Create a diagram showing how to send a message with hash function and
confidentiality? Your solution should prevent the MIM
4. Create a diagram showing how to send encrypted hash without confidentiality?
Your solution should prevent the MIM
5. Create a diagram showing how to verify the shared secret with hash without
confidentiality? Your solution should prevent the MIM
6. Create a diagram showing how to verify the shared secret with hash with
confidentiality? Your solution should prevent the MIM
28. 3. Message Authentication Code(MAC)
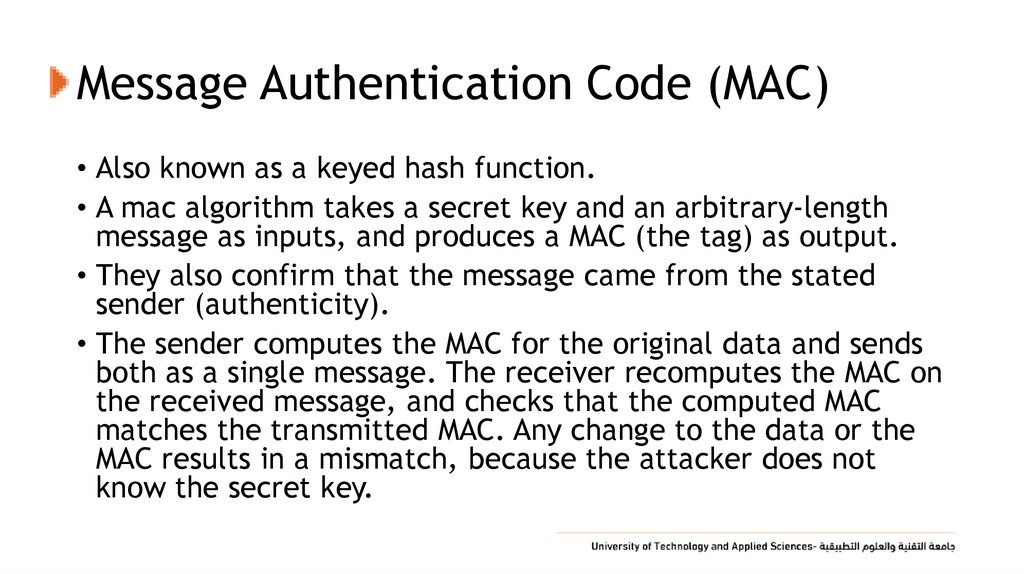
29. Message Authentication Code (MAC)
• Also known as a keyed hash function.• A mac algorithm takes a secret key and an arbitrary-length
message as inputs, and produces a MAC (the tag) as output.
• They also confirm that the message came from the stated
sender (authenticity).
• The sender computes the MAC for the original data and sends
both as a single message. The receiver recomputes the MAC on
the received message, and checks that the computed MAC
matches the transmitted MAC. Any change to the data or the
MAC results in a mismatch, because the attacker does not
know the secret key.
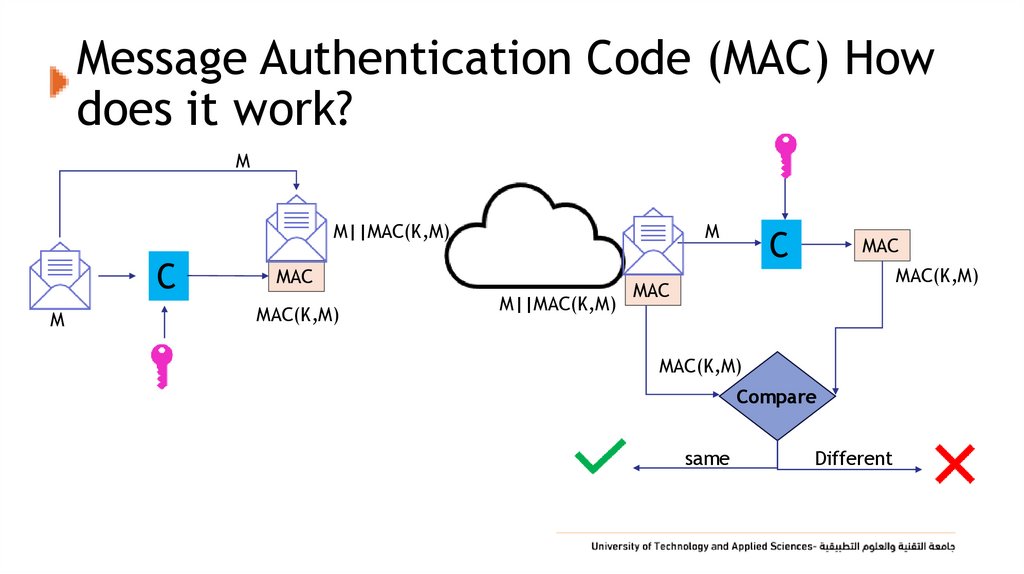
30. Message Authentication Code (MAC) How does it work?
MM||MAC(K,M)
C
M
M
MAC
MAC(K,M)
M||MAC(K,M)
C
MAC
MAC(K,M)
MAC
MAC(K,M)
Compare
same
Different
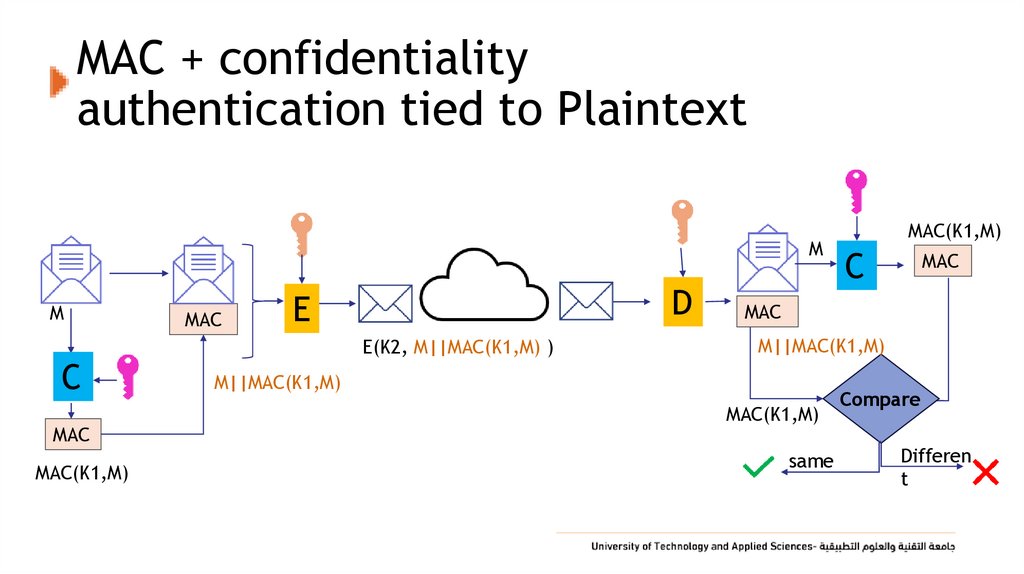
31. MAC + confidentiality authentication tied to Plaintext
MM
C
MAC
MAC(K1,M)
MAC
D
E
E(K2, M||MAC(K1,M) )
MAC(K1,M)
C
MAC
MAC
M||MAC(K1,M)
M||MAC(K1,M)
MAC(K1,M)
same
Compare
Differen
t
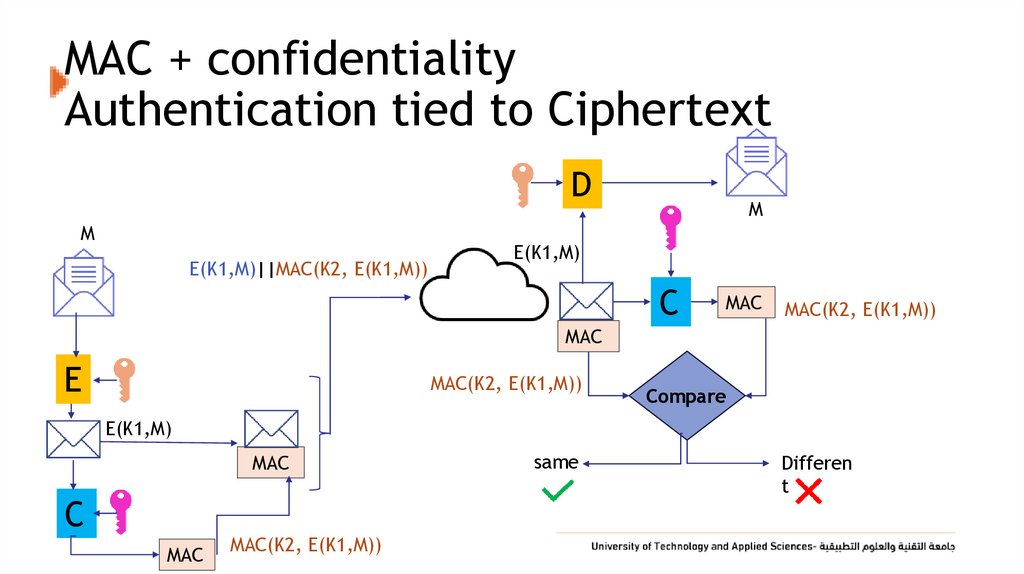
32. MAC + confidentiality Authentication tied to Ciphertext
DM
E(K1,M)||MAC(K2, E(K1,M))
M
E(K1,M)
C
MAC
MAC(K2, E(K1,M))
MAC
E
MAC(K2, E(K1,M))
Compare
E(K1,M)
MAC
C
MAC
MAC(K2, E(K1,M))
same
Differen
t
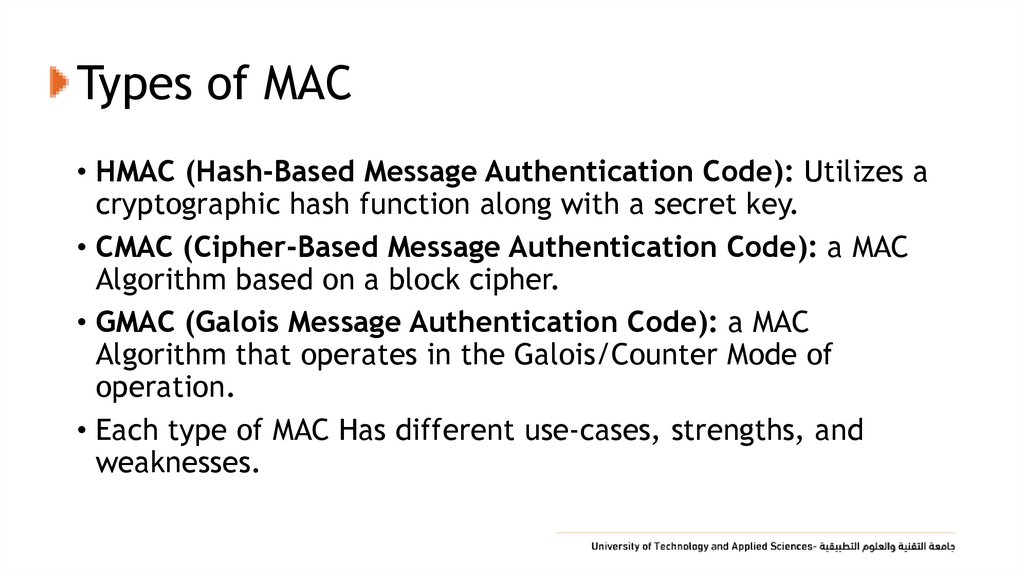
33. Types of MAC
• HMAC (Hash-Based Message Authentication Code): Utilizes acryptographic hash function along with a secret key.
• CMAC (Cipher-Based Message Authentication Code): a MAC
Algorithm based on a block cipher.
• GMAC (Galois Message Authentication Code): a MAC
Algorithm that operates in the Galois/Counter Mode of
operation.
• Each type of MAC Has different use-cases, strengths, and
weaknesses.
34. Security Considerations of MAC :
• The Security of a MAC Depends on the Secrecy of the Key; ifthe Key Is Compromised, the MAC Can Be Forged.
• MACs Do Not Provide Protection Against Replay Attacks, Where
an Attacker Re-Sends a Previously Sent Message.
• MACs Also Do Not Provide Non-Repudiation, as the Same Key Is
Usually Available to Both Parties in the Communication.
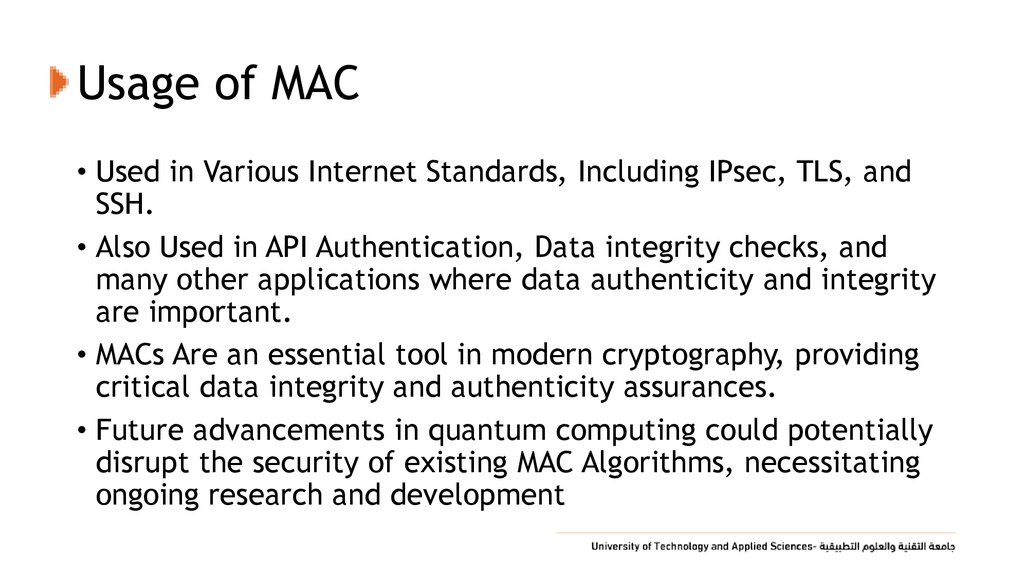
35. Usage of MAC
• Used in Various Internet Standards, Including IPsec, TLS, andSSH.
• Also Used in API Authentication, Data integrity checks, and
many other applications where data authenticity and integrity
are important.
• MACs Are an essential tool in modern cryptography, providing
critical data integrity and authenticity assurances.
• Future advancements in quantum computing could potentially
disrupt the security of existing MAC Algorithms, necessitating
ongoing research and development
36. Activity 2
1. Create a diagram showing how to use MAC to detect the message modification.2. Create a diagram showing how to send a message with message authentication and confidentiality?
The confidentiality should be tied to plaintext
3. Create a diagram showing how to send a message with message authentication and confidentiality?
The confidentiality should be tied to ciphertext
37. 4. Key Management
38. Problems solved
1. How to ensure that the message is not modified ? MAC2. How to ensure that the message is coming from a valid
sender ? MAC
3. How to stop the sender from denying that he has sent the
message? Digital Signature
39. Distribution of Public Keys
1. Public Announcement .2. Public Available Directory.
3. Public-Key Authority .
4. Public-Key Certificates
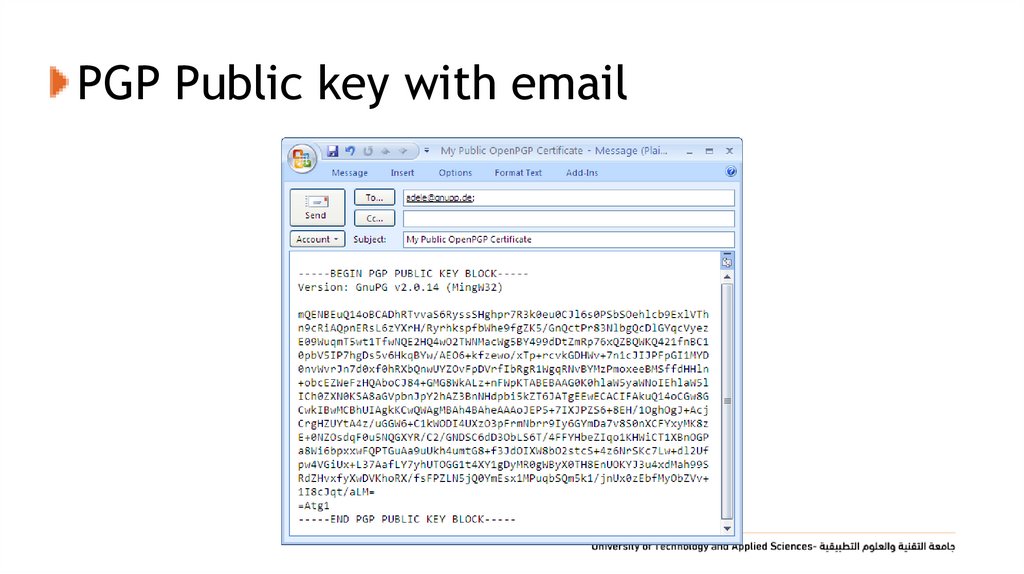
40. Public Announcement
• Users distribute public keys to recipients or broadcast tocommunity at large.
• Eg. Append PGP keys to email messages or post to news groups
or email list.
• Major weakness is forgery.
• Anyone can create a key claiming to be someone else and
broadcast it .
• Until forgery is discovered can masquerade as claimed user.
41. PGP Public key with email
42. Publicly Available Directory
• Obtain greater security by registering keys with a publicdirectory.
• Directory must be trusted with properties:
1. Contains {name,public-key} entries
2. Participants register securely with directory
3. Participants can replace key at any time
4. Directory is periodically published
5. Directory can be accessed electronically
• Still vulnerable to tampering or forgery
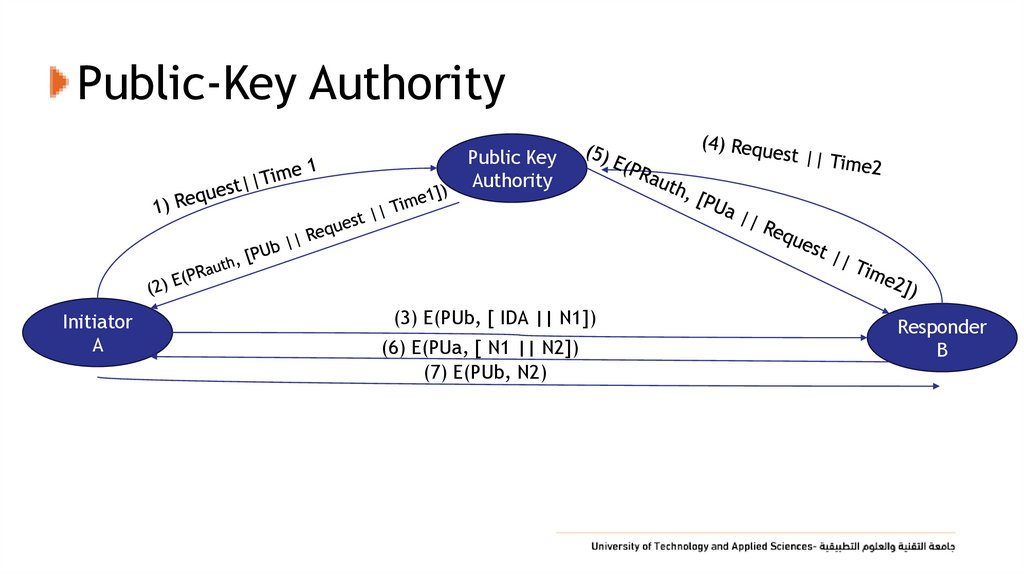
43. Public-Key Authority
• Improve security by tightening control over distribution of keysfrom directory
• Has properties of directory
• And requires users to know public key for the directory
• Then users interact with directory to obtain any desired public
key securely
• Does require real-time access to directory when keys are
needed
• May be vulnerable to tampering
44. Public-Key Authority
Public KeyAuthority
Initiator
A
(3) E(PUb, [ IDA || N1])
(6) E(PUa, [ N1 || N2])
(7) E(PUb, N2)
Responder
B
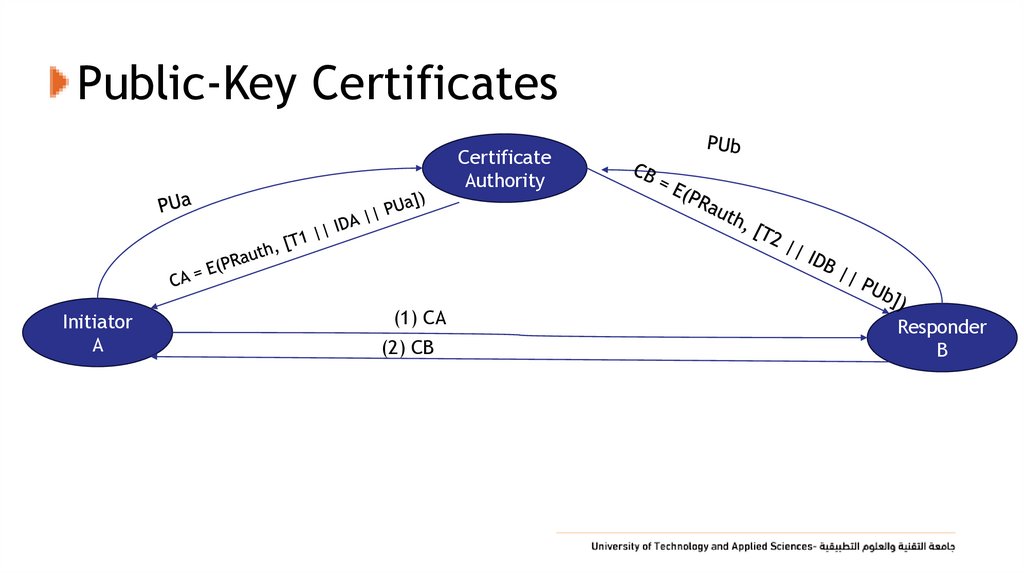
45. Public-Key Certificates
• Certificates Allow Key Exchange Without Real-Time Access toPublic-Key Authority
• A Certificate binds identity to public key
• Usually with other info such as period of validity, rights of use
etc
• With all contents signed by a trusted Public-Key or Certificate
Authority (CA)
• Can be verified by anyone who knows the Public-Key
Authorities Public key
46. Public-Key Certificates
CertificateAuthority
Initiator
A
(1) CA
(2) CB
Responder
B
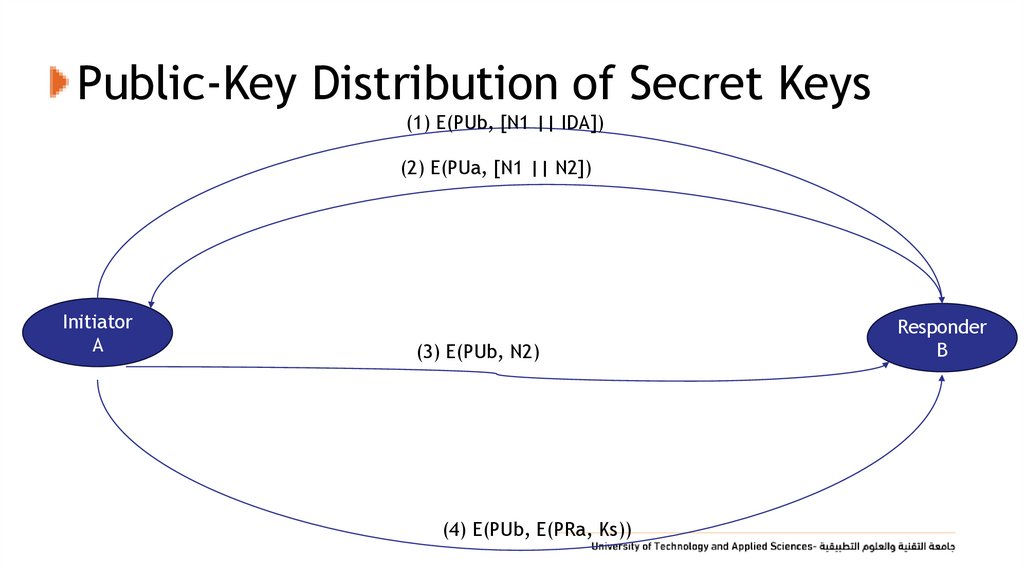
47. Public-Key Distribution of Secret Keys
(1) E(PUb, [N1 || IDA])(2) E(PUa, [N1 || N2])
Initiator
A
(3) E(PUb, N2)
(4) E(PUb, E(PRa, Ks))
Responder
B
48. 4. Digital Certificate
49. Digital Certificate
• An Electronic Document That Uses a Digital Signature To Bind aPublic Key With an Identity
• Such as the Name of a Person or an Organization, the Address,
and the Email Address.
• Can Be Used To Verify That a Public Key Belongs to an
Individual.
50. Why Digital Certificate ?
• Identification / Authentication• Confidentiality
• Integrity
• Non-Repudiation
• Access Control
51. Public-Key Infrastructure (PKI)
• Set of Hardware, Software, People, Policies, and ProceduresNeeded To Create, Manage, Distribute, Use, Store, and Revoke
Digital Certificates.
52. Certificate Authority
• Certificate Authority or Certification Authority (CA), Is anentity that issues digital certificates.
• CA Is a trusted third party that is trusted by both the subject
(Owner) Of the certificate and the party relying upon the
certificate.
53. Process of Obtaining a Certificate
• Subscriber (sender) generates a public\private key pair. Then,applies to CA for digital certificate with the public key.
• CA verifies subscriber's identity and issues digital certificate
containing the public key.
• CA publishes certificate to public, on-line repository.
• Subscriber signs message with private key and sends message to
second party.
• Receiving party verifies digital signature with sender's public key
and requests verification of sender's digital
• Certificate from ca's public repository.
• Repository reports status of subscriber's certificate.
54. Four Types Of Digital Certificates
1. Server certificates :allows visitors to exchange personalinformation.
2. Personal certificates: restrict access to specified content to
particular visitors.
3. Organization certificates :identify employees for secure email and web-based transaction.
4. Developer certificates : prove authorship and retain
integrity of distributed software programs
55. X.509 Certificate
• Standard formats for public key certificates• Used in most network security applications, including IP
security, secure sockets layer (SSL), secure electronic
transactions (SET), and S/MIME
56. X.509 Certificate
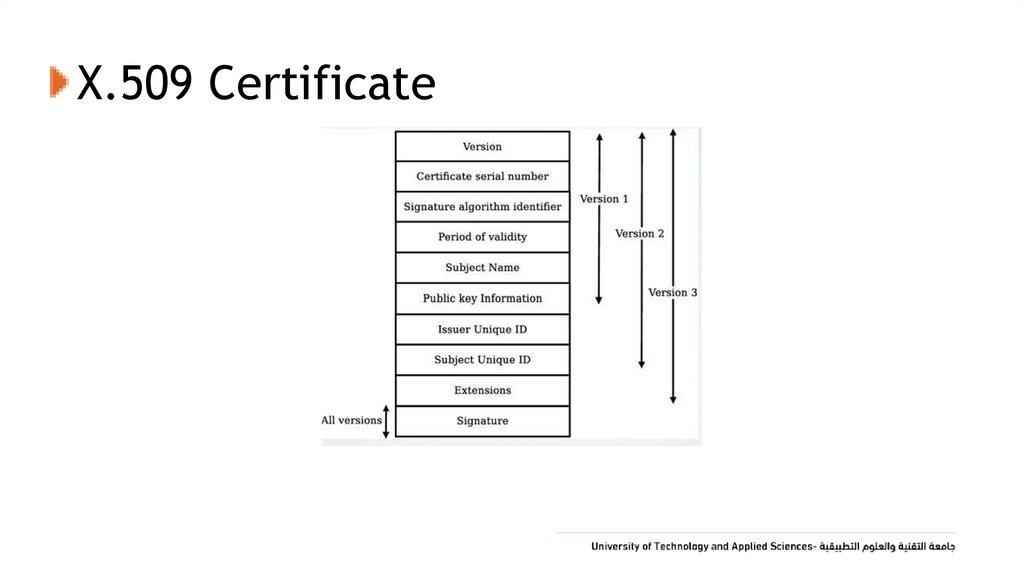
57. X.509 Certificate
• Version: (1, 2, Or 3)• Serial Number : ( an Integer Value, Unique Within CA) Identifying Certificate.
• Signature Algorithm Identifier : the Algorithm Used To Sign the Certificate.
• Issuer X.500 Name: Name of the CA.
• Period of Validity: the First and Last Dates on Which the Certificate Is Valid.
• Subject X.500 Name: Name of Owner
• Subject Public-Key Information: Algorithm, Parameters, Key
• Issuer Unique Identifier: an Optional Bit String Field To Identify the Issuing CA.
• Subject Unique Identifier: an Optional Bit String Field To Identify the Subject.
• Extension Fields: Extension Fields for Version3.
• Signature: Contains the Hash Code of all Fields in Certificate
58. Digital Signature
• Mathematical Scheme for Demonstrating the Authenticity of aDigital Message or Document.
• Digital Signatures Are Commonly Used for Software
Distribution, Financial Transactions, and in Other Cases Where
It Is Important To Detect Forgery or Tampering.
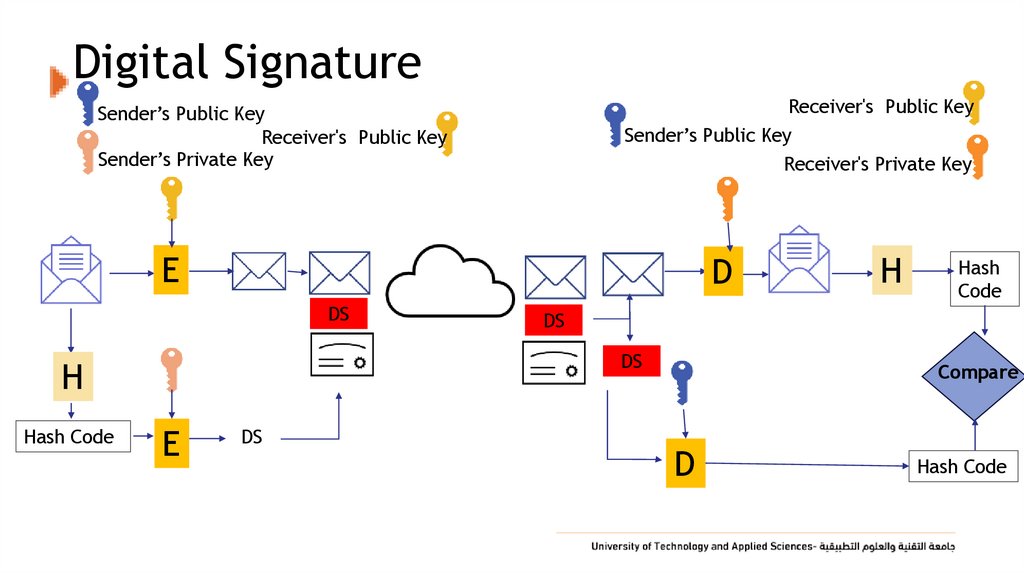
59. Digital Signature
Receiver's Public KeySender’s Public Key
Sender’s Public Key
Receiver's Public Key
Sender’s Private Key
Receiver's Private Key
E
D
DS
Hash Code
E
DS
Hash
Code
DS
DS
H
H
Compare
D
Hash Code