Похожие презентации:
Information security
1. Information security
2. Information
is a sequence of symbols thatcan be interpreted as a message.
Information is data, regardless of their form
of presentation.
2
3. What information to protect?
Confidential data means data which issensitive (конфиденциальная),
restricted (секретная)
top secret (сверхсекретная).
3
4. What information to protect?
Personal data means any data relatingdirectly or indirectly to a living individual
Example: name + address, date, telephone
number, etc
4
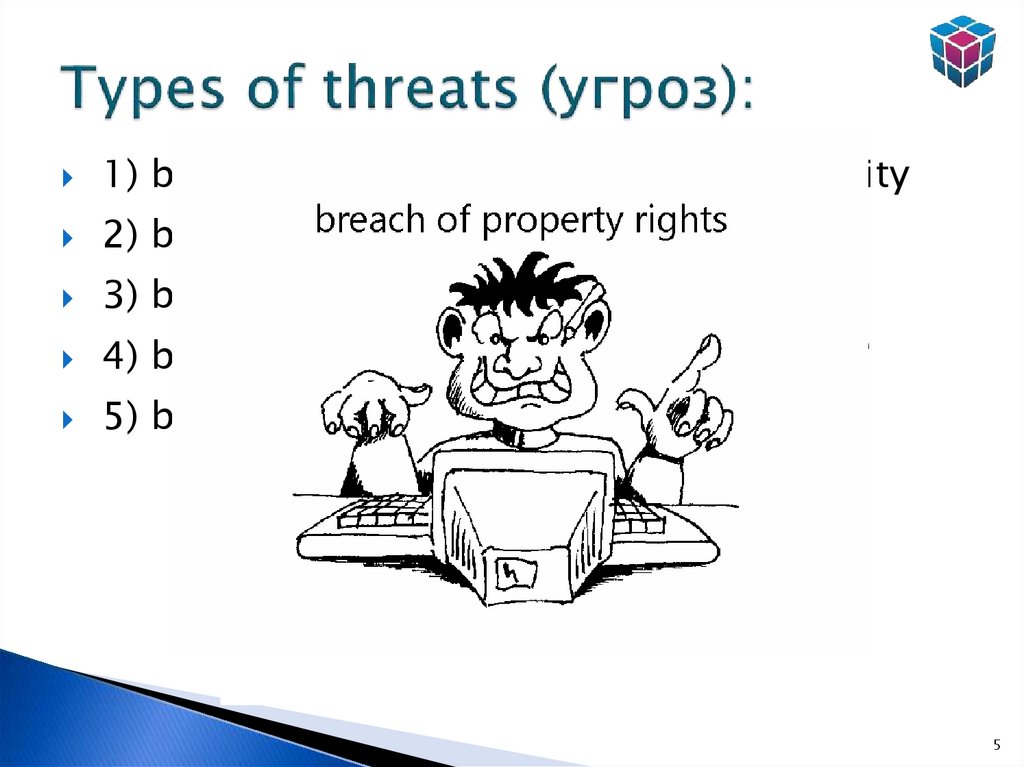
5. Types of threats (угроз):
1) breach (нарушение) of physical integrity2) breach of the logical structure
3) breach of contents
4) breach of confidentiality
5) breach of property rights
5
6. How do we handle (обрабатываем) electronic information?
67. How information leaks?
Informationleakage
(утечка)
happens
whenever a system that is designed to be
closed to an eavesdropper (перехватчик)
reveals some information to unauthorized
parties.
7
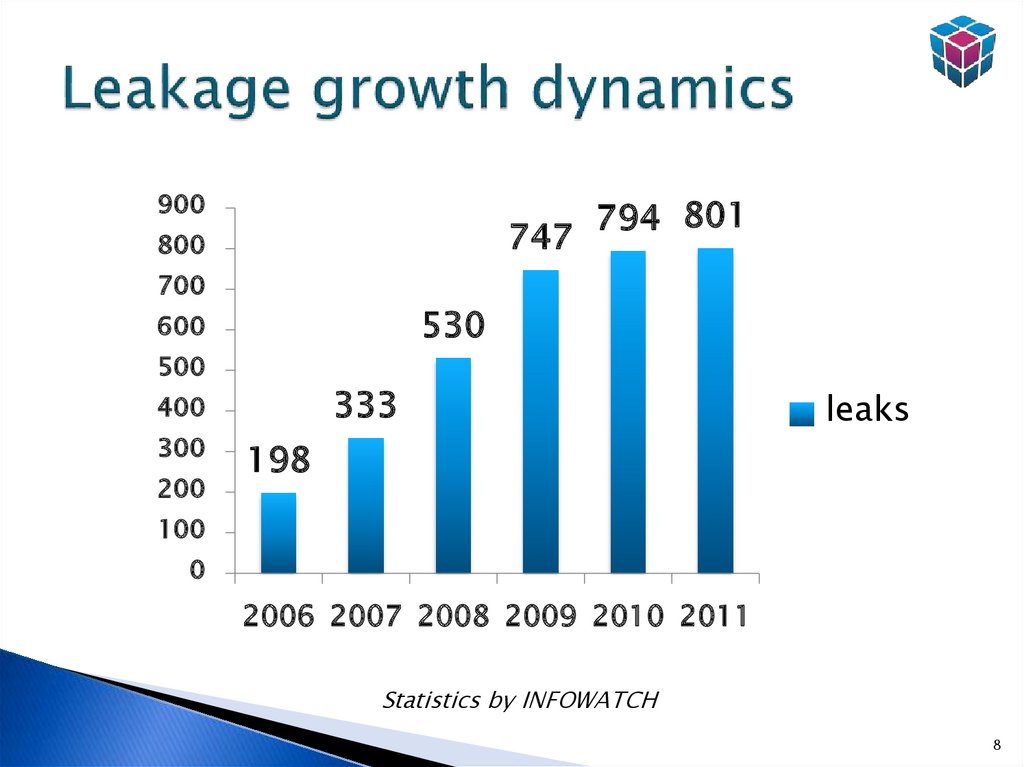
8. Leakage growth dynamics
900747
800
700
530
600
500
333
400
300
200
794 801
leaks
198
100
0
2006 2007 2008 2009 2010 2011
Statistics by INFOWATCH
8
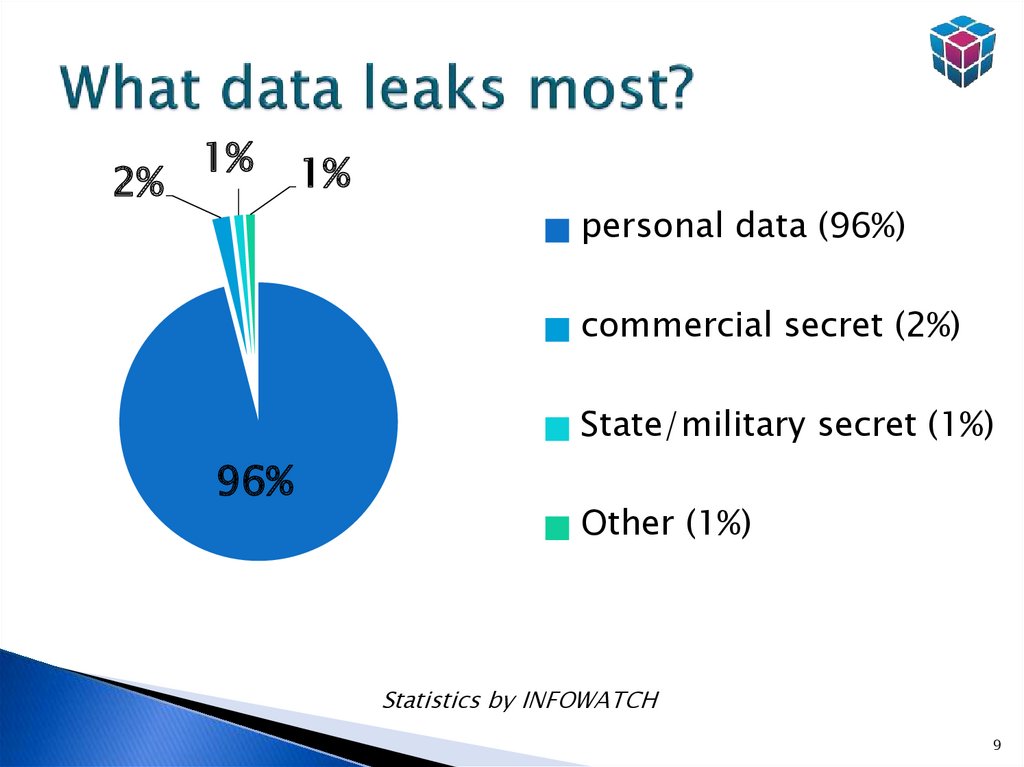
9. What data leaks most?
2%1%
1%
personal data (96%)
commercial secret (2%)
State/military secret (1%)
96%
Other (1%)
Statistics by INFOWATCH
9
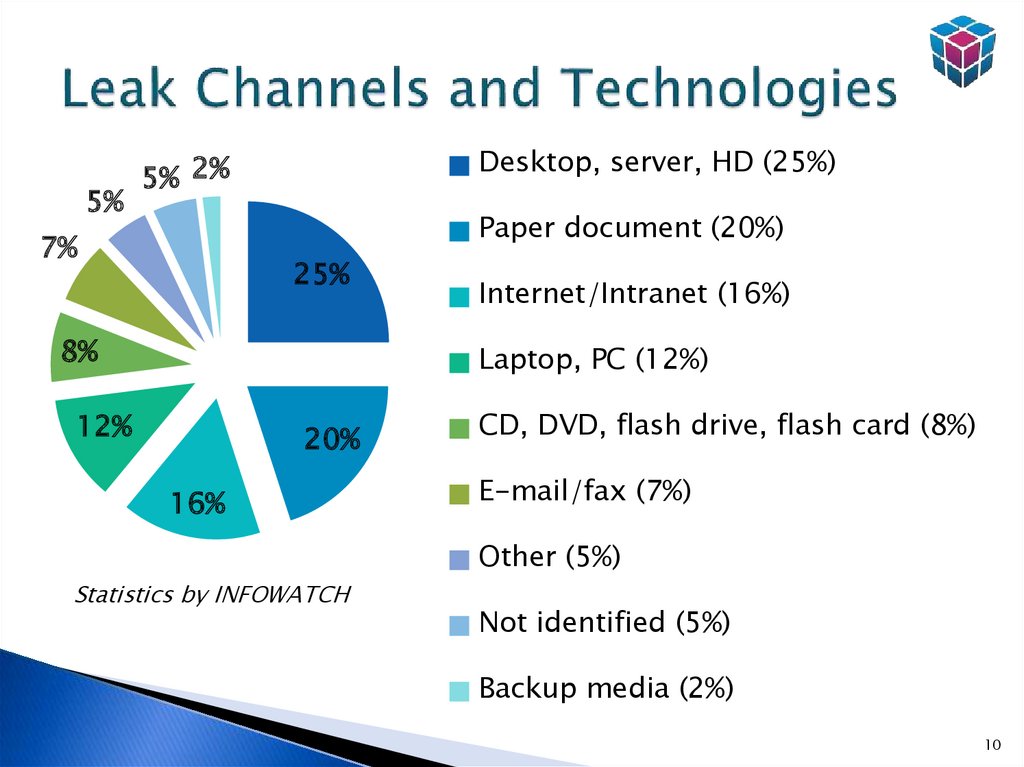
10. Leak Channels and Technologies
5%Desktop, server, HD (25%)
5% 2%
Paper document (20%)
7%
25%
8%
Internet/Intranet (16%)
Laptop, PC (12%)
12%
20%
16%
CD, DVD, flash drive, flash card (8%)
E-mail/fax (7%)
Other (5%)
Statistics by INFOWATCH
Not identified (5%)
Backup media (2%)
10
11. Tips in preventing (предотвращение) information leakage
Your awareness1. Access control (контроль доступа)
2. Strong password (надежный пароль)
a) At least eight characters composed of random
letters, digits and symbols;
b) Use different sets of password in different
systems
c) Never use dictionary words and personal
related information such as name, date,
telephone number etc.
11
12. Tips in preventing information leakage
3. Third-party management (сторонн)a) sign confidentiality agreement
4. Proper disposal (правильная утилизация)
a) Degaussing (размагничивание) the devices
b) physically destroying them, or by using
data cleaner to erase data inside
5. Media maintenance (медиа-обслуживание)
a) buy device which supports hardware data
encryption (шифрование)
b) remove hard disk before repairing
c) clean up hard disk
12
13.
Здесь будет видео13
14. Сonclusions
Nowadays information is very important. Themain aim of researches is information security
and how to prevent information leakage.
14
15.
Thanks for watching !!!15










 Интернет
Интернет








