Похожие презентации:
Introduction to Computer Systems. Architecture of Computer Systems. Lecture №2
1.
Introduction to ComputerSystems. Architecture of
Computer Systems.
Lecture №2
2.
Lecture’s Outline• Computer architecture
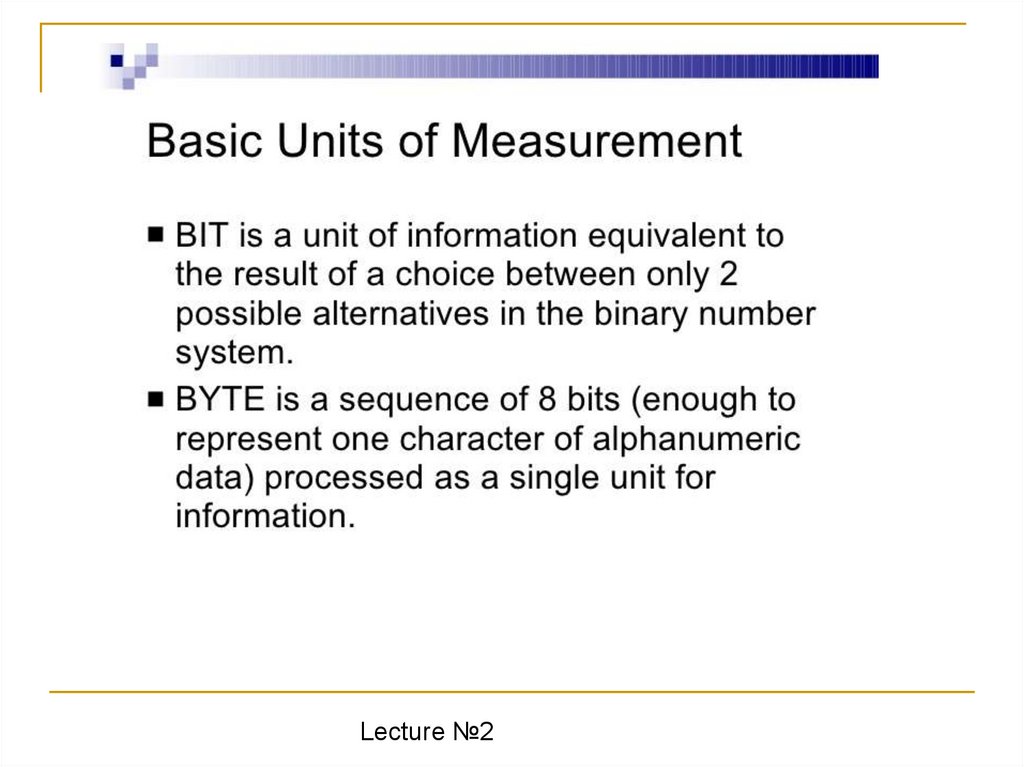
• Basic units of measurement
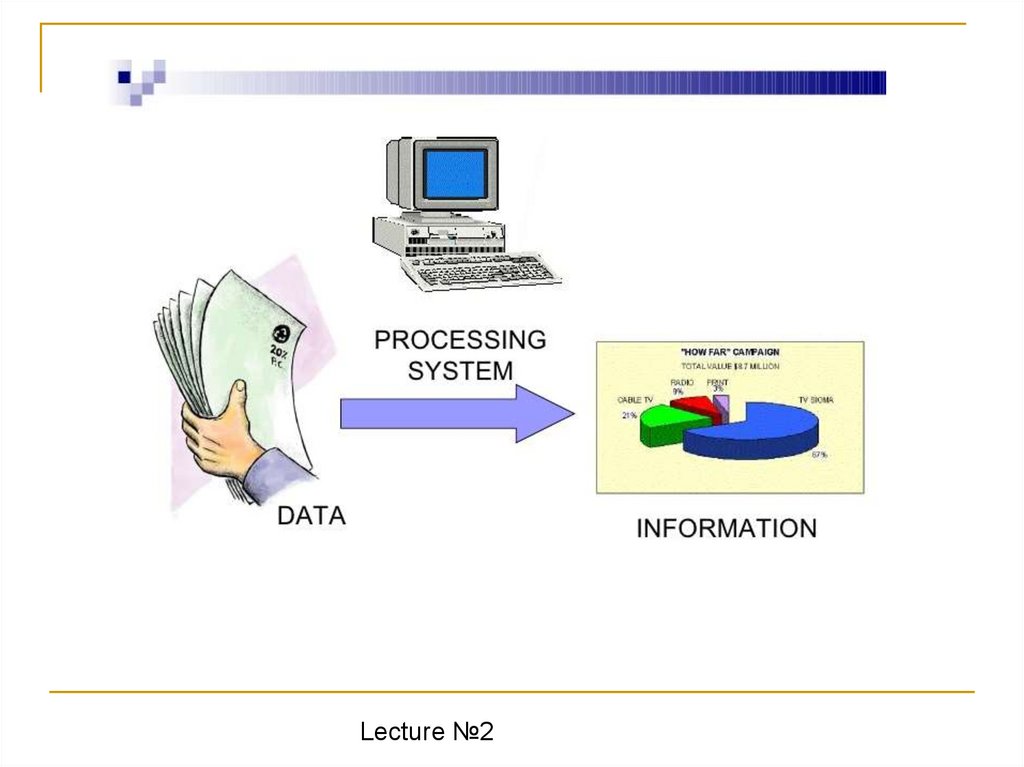
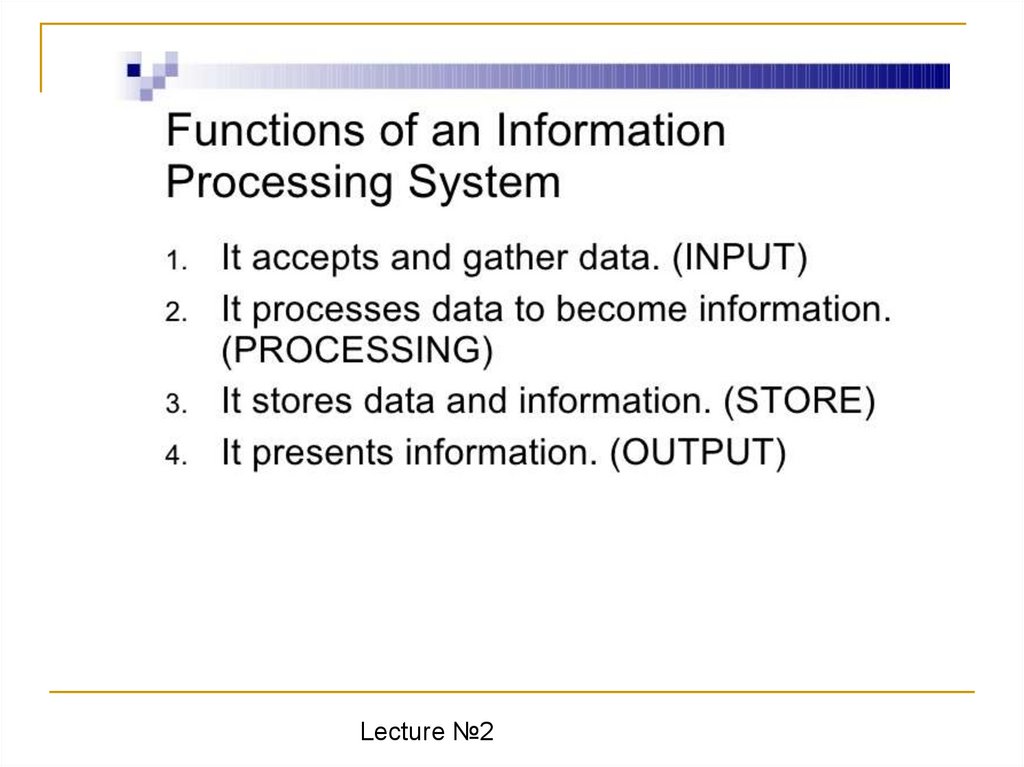
• The major components of an Information
processing systems
• Definition of Hardware
• CPU and Motherboard
• Types of storage devices
• Input devices
• Output devices
Lecture №2
3.
Lecture №24.
In computer engineering, computer architecture is a set of rules andmethods that describe the functionality, organization, and
implementation of computer systems.
Von-Neumann architecture
In a Von-Neumann architecture, the same memory and bus are used to
store both data and instructions that run the program. Since you cannot
access program memory and data memory simultaneously, the Von
Neumann architecture is susceptible to bottlenecks and system
performance is affected.
Lecture №2
5.
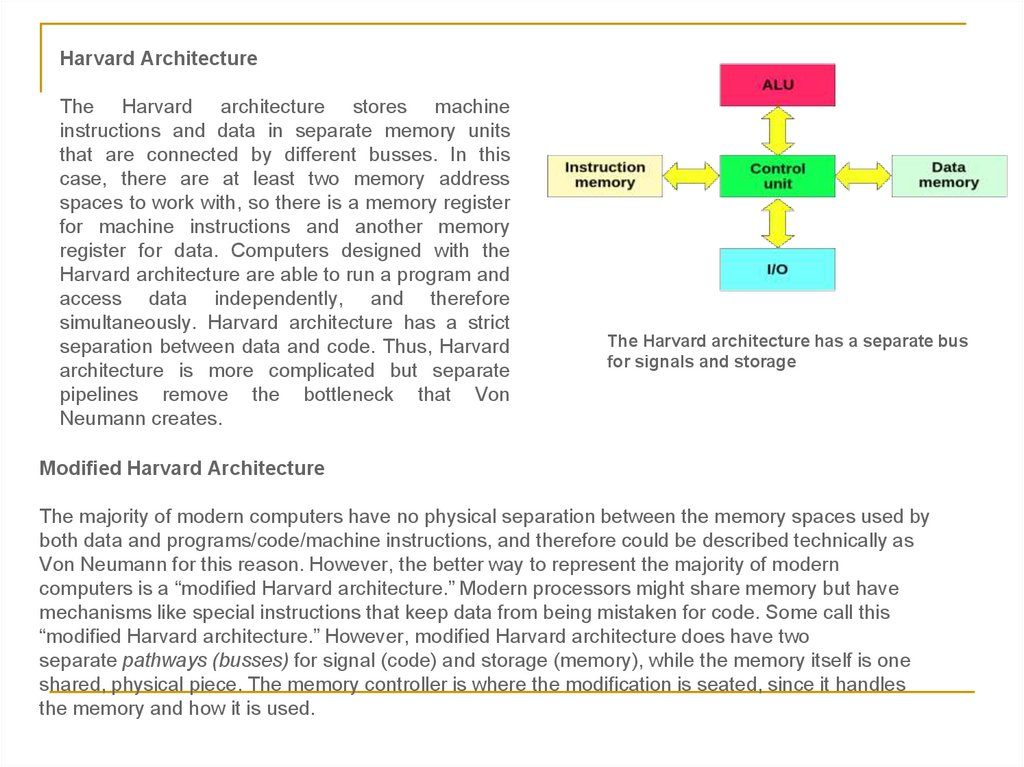
Harvard ArchitectureThe Harvard architecture stores machine
instructions and data in separate memory units
that are connected by different busses. In this
case, there are at least two memory address
spaces to work with, so there is a memory register
for machine instructions and another memory
register for data. Computers designed with the
Harvard architecture are able to run a program and
access data independently, and therefore
simultaneously. Harvard architecture has a strict
separation between data and code. Thus, Harvard
architecture is more complicated but separate
pipelines remove the bottleneck that Von
Neumann creates.
The Harvard architecture has a separate bus
for signals and storage
Modified Harvard Architecture
The majority of modern computers have no physical separation between the memory spaces used by
both data and programs/code/machine instructions, and therefore could be described technically as
Von Neumann for this reason. However, the better way to represent the majority of modern
computers is a “modified Harvard architecture.” Modern processors might share memory but have
mechanisms like special instructions that keep data from being mistaken for code. Some call this
“modified Harvard architecture.” However, modified Harvard architecture does have two
separate pathways (busses) for signal (code) and storage (memory), while the memory itself is one
shared, physical piece. The memory controller is where the modification is seated, since it handles
the memory and how it is used.
6.
The Von Neumann BottleneckIf a Von Neumann machine wants to perform an operation on some data in memory, it
has to move the data across the bus into the CPU. When the computation is done, it
needs to move outputs of the computation to memory across the same bus. The amount
of data the bus can transfer at one time (speed and bandwidth) plays a large part in how
fast the Von Neumann architecture can be. The throughput (bandwidth) of a computer is
related to how false the processors are as well as the rate of data transfer across the
bus. The processor can be idle (inactive) while waiting for a memory fetch (extract), or it
can perform something called speculative processing, based on what the processor
might next need to do after the current computation is finished (once data is fetched and
computations are performed).
The Von Neumann bottleneck occurs when data taken in or out of memory must wait
while the current memory operation is completed. That is, if the processor just
completed a computation and is ready to perform the next, it has to write the finished
computation into memory (which occupies the bus) before it can fetch new data out of
memory (which also uses the bus). The Von Neumann bottleneck has increased over
time because processors have improved in speed while memory has not progressed as
fast. Some techniques to reduce the impact of the bottleneck are to keep memory in
cache to minimize data movement, hardware acceleration, and speculative execution.
Lecture №2
7.
Lecture №28.
Lecture №29.
Lecture №210.
Lecture №211.
Lecture №212.
Lecture №213.
What is Hardware?Hardware is the physical parts of the
computer system – the parts that you
can touch and see.
A motherboard, a CPU, a keyboard and a
monitor are all items of hardware.
Lecture №2
14.
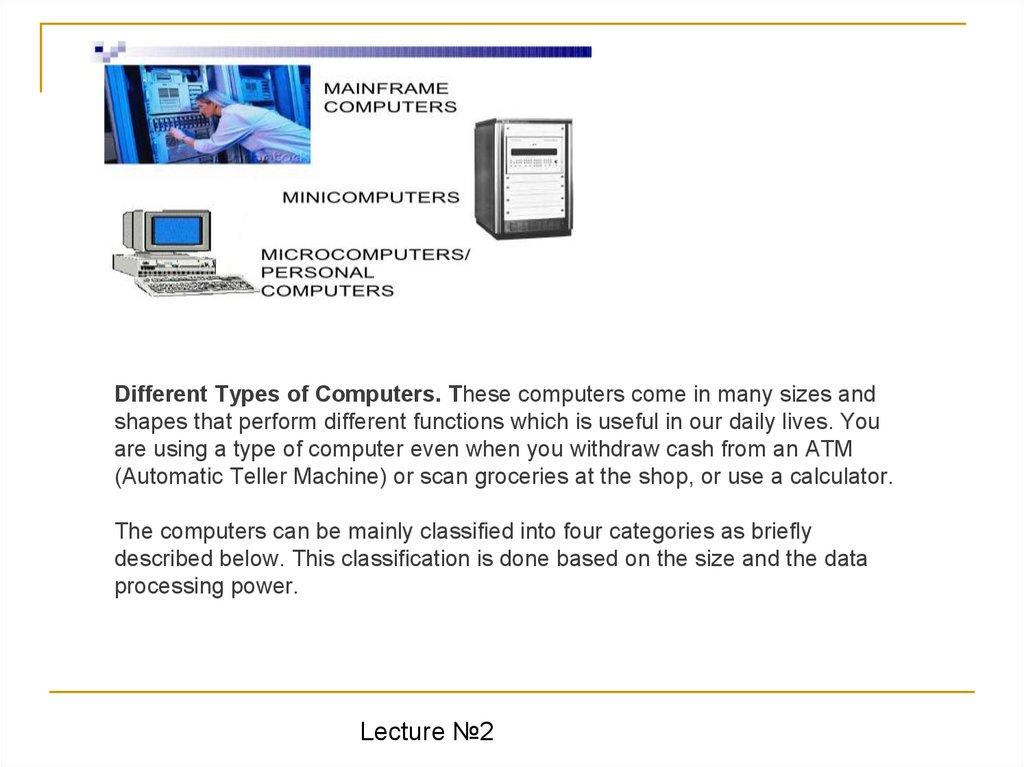
Different Types of Computers. Тhese computers come in many sizes andshapes that perform different functions which is useful in our daily lives. You
are using a type of computer even when you withdraw cash from an ATM
(Automatic Teller Machine) or scan groceries at the shop, or use a calculator.
The computers can be mainly classified into four categories as briefly
described below. This classification is done based on the size and the data
processing power.
Lecture №2
15.
• Microcomputers: most common type of computers in the society. Canbe used at your workplace, at university or on your study desk at home.
Used by single user at a time. Small in size. Also called Personal
Computers (PCs).
• Minicomputers: is a class of smaller general purpose computers that
developed in the mid-1960s and sold for much less than mainframe and
mid-size computers from IBM and its direct competitors. The class formed
a distinct group with its own software architectures and operating systems.
Minicomputers were designed for control, instrumentation, human
interaction, and communication switching as distinct from calculation and
record keeping.
• Mainframes:Largest in size. Capable of handling and processing very
large amounts of data quickly.
• Super computers: Used for performing complex scientific and numerical
computations such as weather forecasting, fluid dynamics, nuclear
simulations, theoretical astrophysics.
Lecture №2
16.
Lecture №217.
Lecture №218.
Lecture №219.
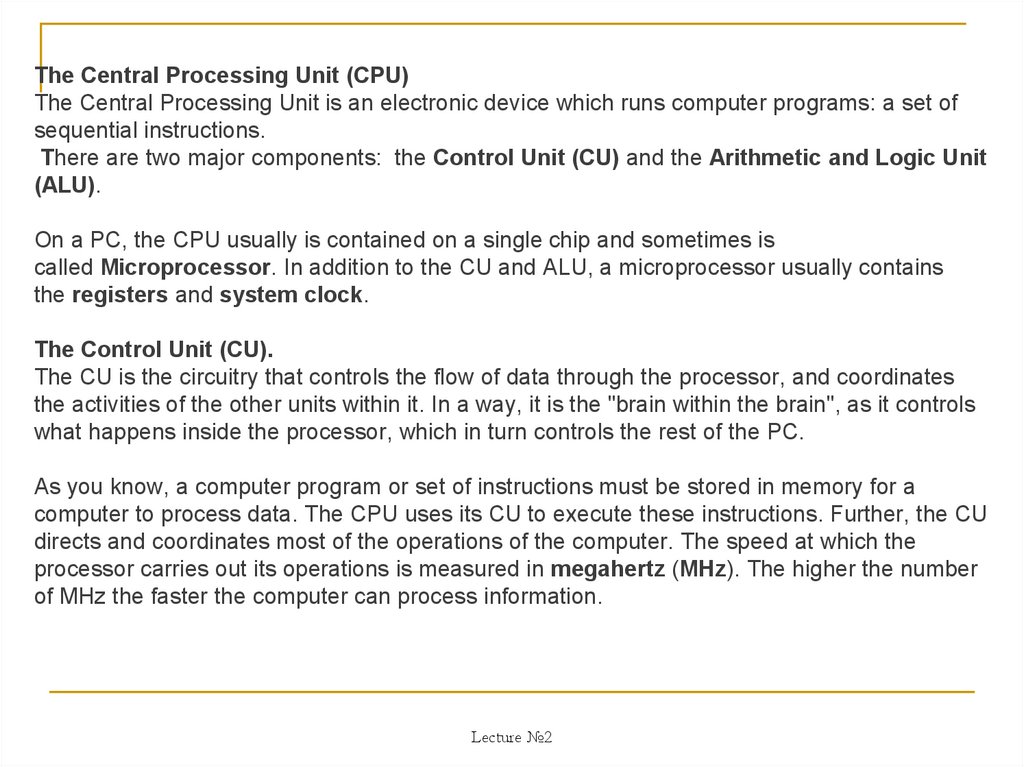
The Central Processing Unit (CPU)The Central Processing Unit is an electronic device which runs computer programs: a set of
sequential instructions.
Тhere are two major components: the Control Unit (CU) and the Arithmetic and Logic Unit
(ALU).
On a PC, the CPU usually is contained on a single chip and sometimes is
called Microprocessor. In addition to the CU and ALU, a microprocessor usually contains
the registers and system clock.
The Control Unit (CU).
The CU is the circuitry that controls the flow of data through the processor, and coordinates
the activities of the other units within it. In a way, it is the "brain within the brain", as it controls
what happens inside the processor, which in turn controls the rest of the PC.
As you know, a computer program or set of instructions must be stored in memory for a
computer to process data. The CPU uses its CU to execute these instructions. Further, the CU
directs and coordinates most of the operations of the computer. The speed at which the
processor carries out its operations is measured in megahertz (MHz). The higher the number
of MHz the faster the computer can process information.
Lecture №2
20.
The Arithmetic and Logic Unit (ALU).The ALU is a digital circuit that performs arithmetic and logical
operations. The ALU is a fundamental building block of the central
processing unit of a computer, and even the simplest
microprocessors contain one. The processors found inside
modern CPUs have very powerful and very complex ALUs; a
single component may contain a number of ALUs.
ALU performs the arithmetic, comparison, and logical operations.
Arithmetic operations include addition (+), subtraction (-),
multiplication (*) and division (/). Comparison operations include
comparing one data item to another to determine if the first item is
greater than (>), equal (=), or less than (<) to the second
item. Logical operations work with conditions such as AND, OR,
NOT.
Lecture №2
21.
CPU performanceThere are four key factors about CPU architecture that affect its performance:
•cores
•clock speed
•cache size
•processor type
Cores
A CPU can contain one or more processing units. Each unit is called a core. A core contains
an ALU, control unit and registers. It is common for computers to have two (dual), four (quad) or even
more cores. CPUs with multiple cores have more power to run multiple programs at the same time.
However, doubling the number of cores will not simply double a computer's speed. CPU cores have to
communicate with each other through channels and this uses up some of the extra speed.
Clock speed
The clock speed - also known as clock rate - indicates how fast the CPU can run. This is measured
in megahertz (MHz) or gigahertz (gHz) and corresponds with how many instruction cycles the CPU can
deal with in a second. A 2 gHz CPU performs two billion cycles a second. A faster CPU uses more energy and
creates more heat.
A computer will normally have a maximum clock speed set by default, but it is possible to change this speed in
the computer BIOS. Some people increase a CPU clock speed to try to make their computer run faster - this is
called overclocking.
There are limits to how fast a CPU can run and its circuitry cannot always keep up with an overclocked speed.
If the clock tells the CPU to execute instructions too quickly, the processing will not be completed before the
next instruction is carried out. If the CPU cannot keep up with the pace of the clock, the data is corrupted.
CPUs can also overheat if they are forced to work faster than they were designed to work.
Lecture №2
22.
CacheCache is a small amount of memory which is a part of the CPU - closer to the CPU
than RAM. It is used to temporarily hold instructions and data that the CPU is likely to reuse.
The CPU control unit automatically checks cache for instructions before requesting data
from RAM. This saves fetching the instructions and data repeatedly from RAM – a relatively
slow process which might otherwise keep the CPU waiting. Transfers to and from cache take
less time than transfers to and from RAM.
The more cache there is, the more data can be stored closer to the CPU.
Cache is graded as Level 1 (L1), Level 2 (L2) and Level 3 (L3):
•L1 is usually part of the CPU chip itself and is both the smallest and the fastest to access. Its
size is often restricted to between 8 KB and 64 KB.
•L2 and L3 caches are bigger than L1. They are extra caches built between the CPU and the
RAM. Sometimes L2 is built into the CPU with L1. L2 and L3 caches take slightly longer to
access than L1. The more L2 and L3 memory available, the faster a computer can run.
Not a lot of physical space is allocated for cache. There is more space for RAM, which is
usually larger and less expensive.
Each CPU core has its own L1 cache, but may share L2 and L3 caches.
Lecture №2
23.
Processor typeThere are two main types of CPU: CISC and RISC.
Most desktop or laptop computers use CISC (complex instruction set computing) architecture made by Intel
or AMD.
Smartphones and tablets use RISC (reduced instruction set computing) ARM architecture
(Advanced RISC Machine)
The key differences between the two CPUs are:
•Instructions - RISC has fewer instructions than CISC. CISC generally have hundreds of instructions
whereas RISC usually has a lot less. To do complex tasks, RISC CPUs must combine simple operations
from their reduced instruction set. The instruction cycle in CISC is more complex than RISC, so RISC can be
more efficient at performing simpler tasks.
•Physical size - in order to handle all those instructions CISC CPUs are larger and require more silicon to
make.
•Speed - RISC CPUs run at a lower clock speed than CISC CPUs. They can perform simpler tasks more
quickly than CISC, but more intensive tasks will be better on a CISC CPU. However, smartphones and
tablets are generally not used to do intensive tasks like playing the most hi-spec advanced games.
•Energy consumption - because CISC CPUs are larger, they use more electricity. RISC CPUs are
designed to use less power and they can go into 'sleep mode' when not actively processing a program.
•Design - smartphones and tablets combine their processing architecture into a system on a chip (SOC
System-on-a-Chip). As RISC CPUs are much smaller than CISC, more functions (including the memory and
other hardware) can be combined with the CPU in one chip. CISC CPUs are usually built into a system which
has a heat sink (radiator, heatsink) and fan to cool them down. Smartphones or tablets do not have space
for heat sinks or fans.
•Cost - RISC CPUs use less power and are cheaper to make.
Lecture №2
24.
The motherboard is a circuit board that connectsthe CPU to the memory and all the other hardware.
The CPU sits on the motherboard
Buses are circuits on the motherboard that connect the
CPU to other components. There are many buses on
the motherboard. A bus moves instructions and data
around the system. The speed of a bus is measured
in megahertz (MHz). The faster the bus, the faster data
is communicated. The speed of the motherboard is
defined by the bus speed.
Buses are limited by their width in bits. They are
usually 8, 16 or 32-bits wide. This tells us how many
bits can be sent by the bus at any one time, eg a 32-bit
bus can send 32 bits at once.
Lecture №2
25.
The bus that connects the CPU to the memory is calledthe front-side bus (FSB) or system bus.
CPU cores share Level 2 and Level 3 cache across
the FSB. They will usually connect to Level 2 cache
through the back-side bus (BSB). The BSB is much
faster than the FSB.
The FSB contains two types of bus:
•Address bus - this sends information about where
data needs to go by sending an address to the memory.
The address bus only sends data in one direction - from
the CPU to RAM.
•Data bus - this sends data to the memory or receives
data from the memory. Data can flow both ways along
the data bus.
Bridges
Bridges manage how data and instructions are
transferred between the CPU, memory and other
devices.
Many PC motherboards use a northbridge and
a southbridge to connect devices:
•The northbridge connects the
CPU, RAM and GPU through the FSB.
•The southbridge connects to the northbridge. All other
hardware, such as the hard drive, connects to the CPU
through the southbridge.
Lecture №2
26.
MemoryMemory is the area where the computer stores or remembers data. Memory
provides the CPU with its instructions. There are different types of memory, and
each one plays an important role in the running of a computer system. Memory is
sometimes called primary memory.
Memory is either volatile or non-volatile. Volatile memory only stores information
to run programs while the computer is on. It is reset and emptied once the
computer is turned off. Volatile memory requires electricity to store data
using transistors and capacitors(condenser).
There is a key difference between memory and storage. Programs are kept on a
storage device and copied into the computer's memory before they are executed.
Storage is also called secondary storage.
Storage and read only memory (ROM) use non-volatile memory to retain(hold)
data - even when the computer has been switched off. In older computers, paper,
punched tape and floppy disks have been used for non-volatile memory.
Lecture №2
27.
Lecture №228.
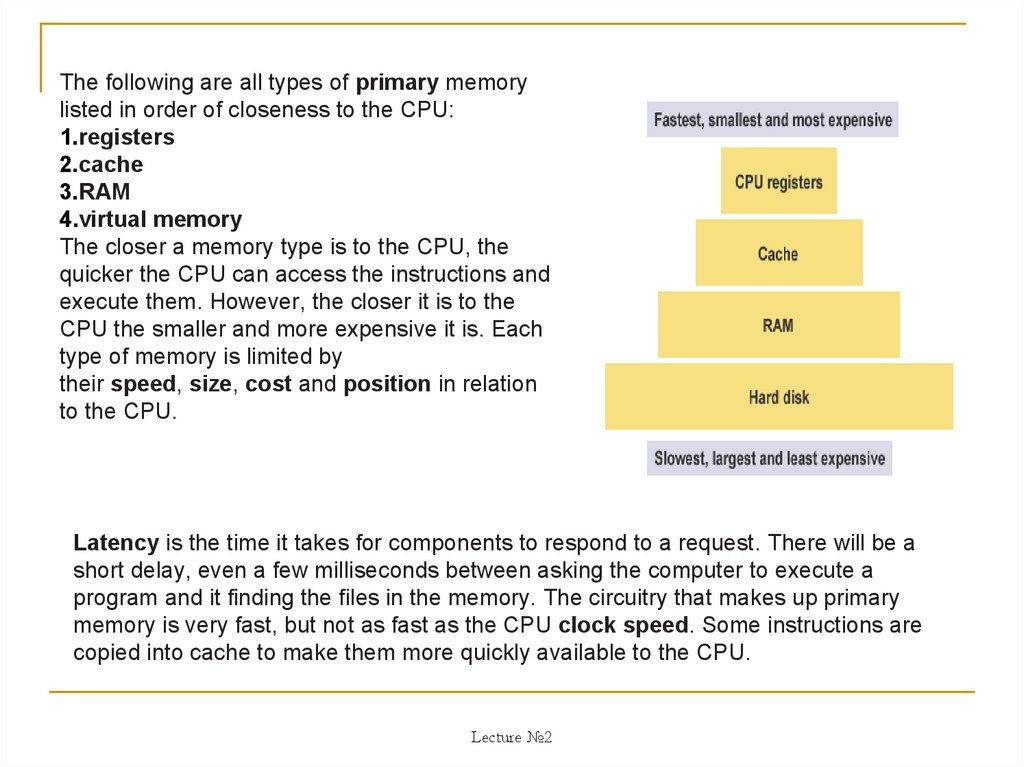
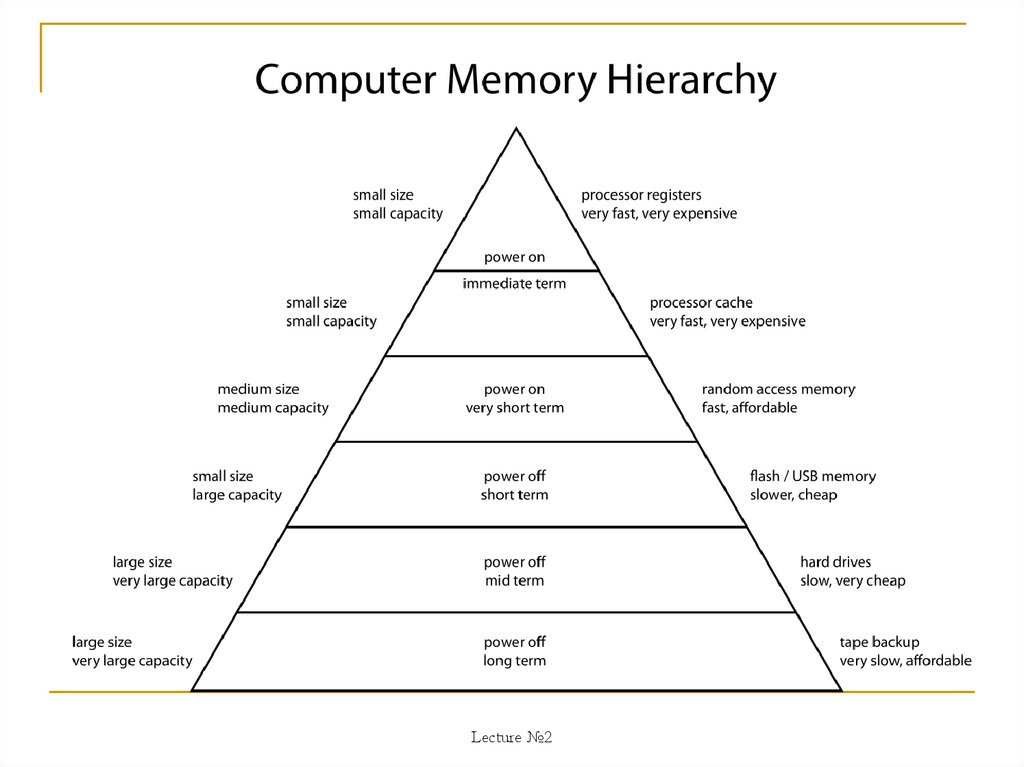
The following are all types of primary memorylisted in order of closeness to the CPU:
1.registers
2.cache
3.RAM
4.virtual memory
The closer a memory type is to the CPU, the
quicker the CPU can access the instructions and
execute them. However, the closer it is to the
CPU the smaller and more expensive it is. Each
type of memory is limited by
their speed, size, cost and position in relation
to the CPU.
Latency is the time it takes for components to respond to a request. There will be a
short delay, even a few milliseconds between asking the computer to execute a
program and it finding the files in the memory. The circuitry that makes up primary
memory is very fast, but not as fast as the CPU clock speed. Some instructions are
copied into cache to make them more quickly available to the CPU.
Lecture №2
29.
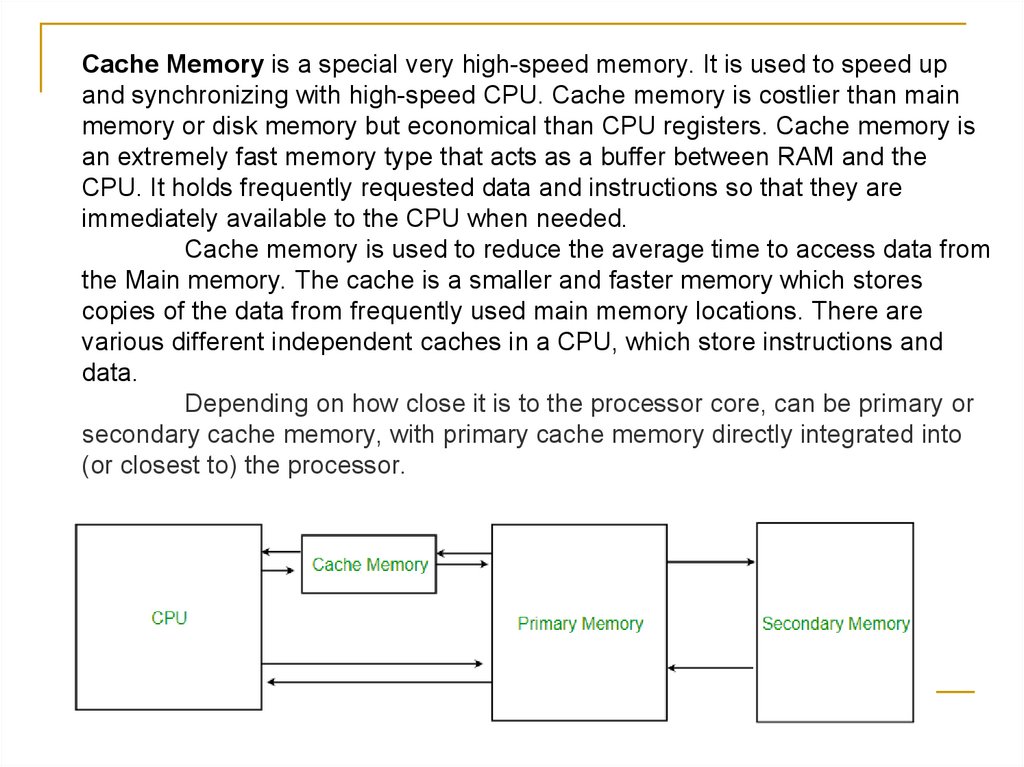
Cache Memory is a special very high-speed memory. It is used to speed upand synchronizing with high-speed CPU. Cache memory is costlier than main
memory or disk memory but economical than CPU registers. Cache memory is
an extremely fast memory type that acts as a buffer between RAM and the
CPU. It holds frequently requested data and instructions so that they are
immediately available to the CPU when needed.
Cache memory is used to reduce the average time to access data from
the Main memory. The cache is a smaller and faster memory which stores
copies of the data from frequently used main memory locations. There are
various different independent caches in a CPU, which store instructions and
data.
Depending on how close it is to the processor core, can be primary or
secondary cache memory, with primary cache memory directly integrated into
(or closest to) the processor.
Lecture №2
30.
Lecture №231.
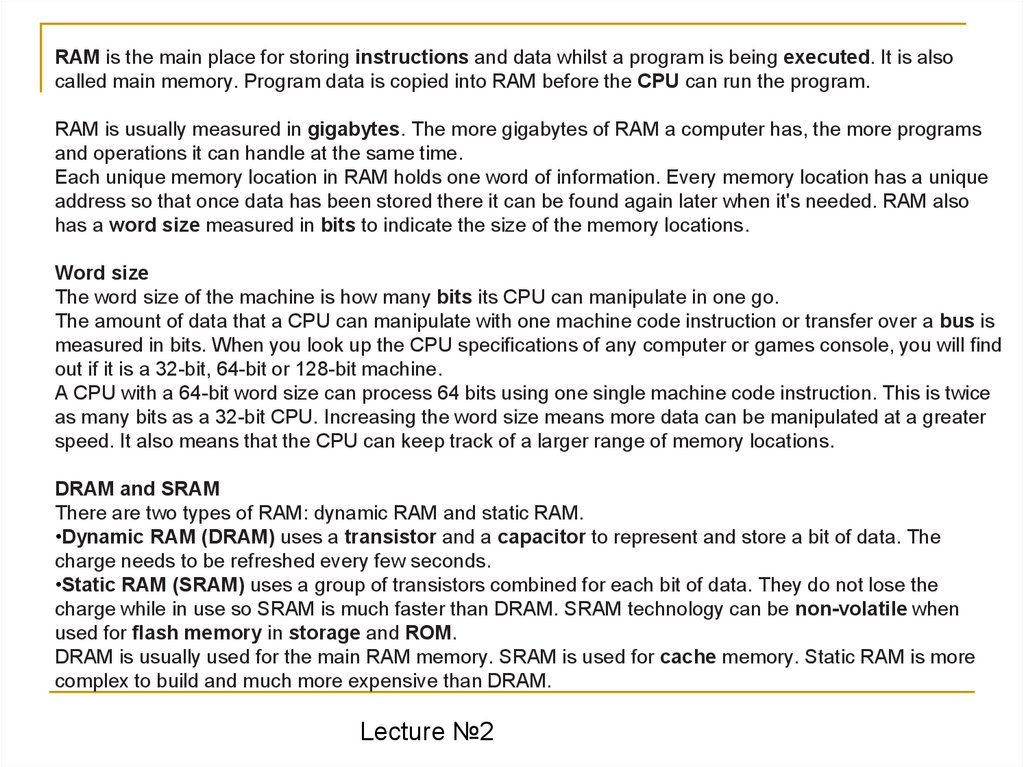
RAM is the main place for storing instructions and data whilst a program is being executed. It is alsocalled main memory. Program data is copied into RAM before the CPU can run the program.
RAM is usually measured in gigabytes. The more gigabytes of RAM a computer has, the more programs
and operations it can handle at the same time.
Each unique memory location in RAM holds one word of information. Every memory location has a unique
address so that once data has been stored there it can be found again later when it's needed. RAM also
has a word size measured in bits to indicate the size of the memory locations.
Word size
The word size of the machine is how many bits its CPU can manipulate in one go.
The amount of data that a CPU can manipulate with one machine code instruction or transfer over a bus is
measured in bits. When you look up the CPU specifications of any computer or games console, you will find
out if it is a 32-bit, 64-bit or 128-bit machine.
A CPU with a 64-bit word size can process 64 bits using one single machine code instruction. This is twice
as many bits as a 32-bit CPU. Increasing the word size means more data can be manipulated at a greater
speed. It also means that the CPU can keep track of a larger range of memory locations.
DRAM and SRAM
There are two types of RAM: dynamic RAM and static RAM.
•Dynamic RAM (DRAM) uses a transistor and a capacitor to represent and store a bit of data. The
charge needs to be refreshed every few seconds.
•Static RAM (SRAM) uses a group of transistors combined for each bit of data. They do not lose the
charge while in use so SRAM is much faster than DRAM. SRAM technology can be non-volatile when
used for flash memory in storage and ROM.
DRAM is usually used for the main RAM memory. SRAM is used for cache memory. Static RAM is more
complex to build and much more expensive than DRAM.
Lecture №2
32.
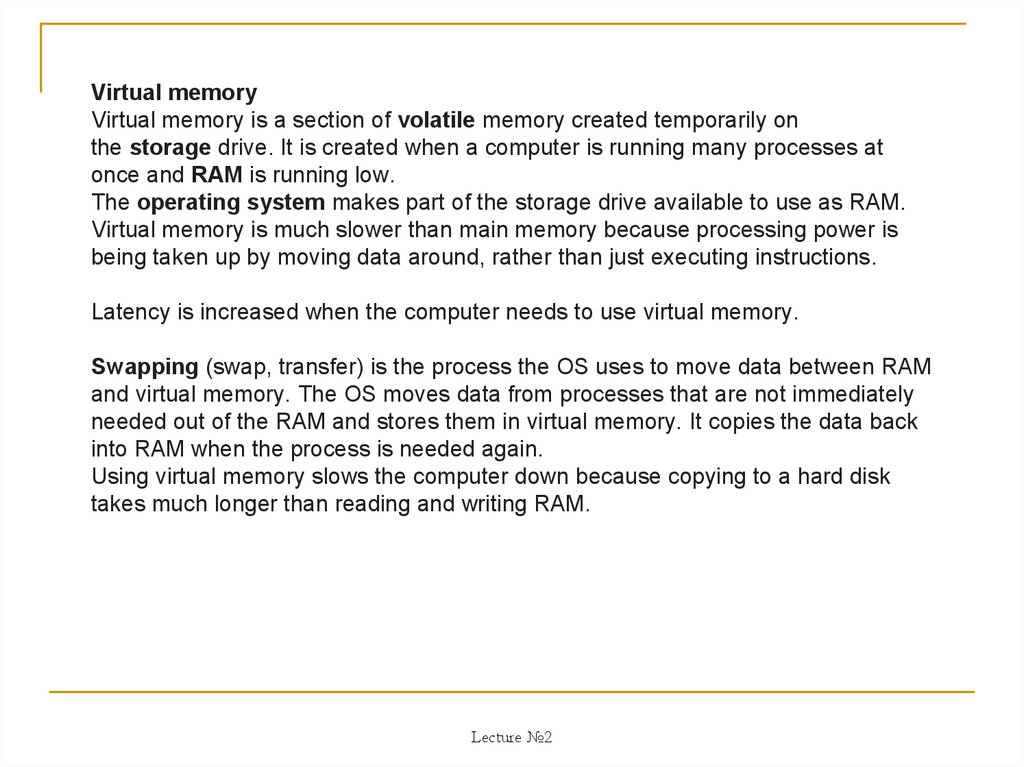
Virtual memoryVirtual memory is a section of volatile memory created temporarily on
the storage drive. It is created when a computer is running many processes at
once and RAM is running low.
The operating system makes part of the storage drive available to use as RAM.
Virtual memory is much slower than main memory because processing power is
being taken up by moving data around, rather than just executing instructions.
Latency is increased when the computer needs to use virtual memory.
Swapping (swap, transfer) is the process the OS uses to move data between RAM
and virtual memory. The OS moves data from processes that are not immediately
needed out of the RAM and stores them in virtual memory. It copies the data back
into RAM when the process is needed again.
Using virtual memory slows the computer down because copying to a hard disk
takes much longer than reading and writing RAM.
Lecture №2
33.
ROM (read only memory) is a flash memory chip that contains a small amount of non-volatilememory. Non-volatile means that its contents cannot be changed and it retains its memory
after the computer is turned off.
ROM contains the BIOS which is the firmware for the motherboard.
//Firmware is a software program or set of instructions programmed on a hardware device.
The BIOS contains the bootstrap (boot loading) – the program which takes the computer
through steps that lead up to the loading of the operating system (OS). It happens between
turning on the power and the computer beeping to say it is starting to load the OS. This
process is known as POST (power on self test) on a PC.
The boot sequence is the computer's initial start-up process. After the boot, the OS controls
the CPU and supplies the programs to run.
Types of ROM include:
•PROM (programmable read-only memory) - manufactured as blank ROM. PROM chips can
be bought cheaply and programmed directly by a programmer. They are not rewritable so they
can only be programmed once.
•EEPROM (electrically erasable programmable read-only memory) - popular in PCs
and smartphones as the firmware can be easily updated by the manufacturer. This is similar
to a rewritable CD in that the chip can be reprogrammed.
Lecture №2
34.
Secondary storage is non-volatile, long-term storage. Without secondary storage allprograms and data would be lost the moment the computer is switched off.
There are three main types of secondary storage in a computer system:
•solid state storage devices, such as USB memory sticks and SSD
•optical storage devices, such as CD, DVD and Blu-ray discs
•magnetic storage devices, such as hard disk drives
However, not all computers require secondary storage. Embedded computers, such as
those found in a washing machine or central heating system, do not need to store data
when the power is turned off. The instructions needed to run them are stored in read-only
memory (ROM) and any user data is held in RAM.
Lecture №2
35.
Solid stateSolid state storage is a special type of storage made from silicon microchips. It can be written to and
overwritten like RAM. However, unlike RAM, it is non-volatile, which means that when the computer's power
is switched off, solid state storage will retain its contents.
Solid state is also used as external secondary storage, for example in USB memory sticks and solid state
drives (SSD).
A solid-state drive (SSD) is a new generation of storage device used in computers. SSDs use flash-based
memory, which is much faster than a traditional mechanical hard disk. Upgrading to an SSD is one of the
best ways to speed up your computer.
One of the major benefits of solid state storage is that is has no moving parts. Because of this, it is more
portable, and produces less heat compared to traditional magnetic storage devices. Less heat means that
components last longer.
Solid state storage has no moving parts making it more portable and durable.
Solid state storage is also faster than traditional hard disk drives because the data is stored electrically in
silicon chips called cells. Within the cells, the binary data is stored by holding an electrical current in a
transistor with an on / off mode. Unlike RAM which uses a similar technique, solid state storage retains this
even when the power is switched off by using a technology known as flash memory.
Solid state is an ideal storage medium for many modern devices such as tablets, smartphones and digital
cameras.
Lecture №2
36.
Magnetic devicesMagnetic devices such as hard disk drives use
magnetic fields to magnetise tiny individual sections of
a metal spinning disk. Each tiny section represents
one bit. A magnetised section represents a binary '1'
and a demagnetised section represents a binary '0'.
These sections are so tiny that disks can
contain terabytes (TB) of data.
As the disk is spinning, a read/write head moves across
its surface. To write data, the head magnetises or
demagnetises a section of the disk that is spinning
under it. To read data, the head makes a note of
whether the section is magnetised or not.
Magnetic devices are fairly cheap, high in capacity and
durable. However, they are susceptible to damage if
dropped. They are also vulnerable to magnetic fields - a
strong magnet might possibly erase the data the device
holds.
Lecture №2
37.
Optical devicesOptical devices use a laser to scan the surface of a
spinning disc made from metal and plastic. The disc
surface is divided into tracks, with each track containing
many flat areas and hollows. The flat areas are known
as lands and the hollows as pits.
When the laser shines on the disc surface, lands reflect
the light back, whereas pits scatter the laser beam. A
sensor looks for the reflected light. Reflected light - land
- represents a binary '1', and no reflection - pits represents a binary '0'.
There are different types of optical media:
•ROM media have data pre-written on them. The data
cannot be overwritten. Music, films, software and
games are often distributed this way.
•Read (R) media are blank. An optical device writes
data to them by shining a laser onto the disc. The laser
burns pits to represent '0's. The media can only be
written to once, but read many times. Copies of data
are often made using these media.
•Read/write RW works in a similar way to R, except that
the disc can be written to more than once.
Lecture №2
38.
Introducing peripheralsPeripherals are devices that
are not the computer's core
architecture involved
in memory and processing.
Peripherals include input
hardware, output hardware and
storage devices.
A typical desktop computer could
include:
•inputs - mouse, keyboard,
webcam, games controller
•outputs - screen, printer,
speakers, headphones
•storage - hard drive
Connections
Peripherals connect to the processor hardware through the motherboard. External
devices will connect to the motherboard via USB, FireWire or through a wireless
connection such as Bluetooth.
Monitors normally connect through HDMI or VGA cables.
Lecture №2
39.
Input devices send signals into the computer that have to be interpreted bythe operating system using drivers. Some of the most common input devices include:
•Keyboard - used to enter characters and data into computers. A QWERTY keyboard uses
the standard layout for English-speaking countries. The Dvorak keyboard layout is an
alternative and was designed to avoid awkward key combinations. Keys on a keyboard
send binary information into the computer which is interpreted using
the ASCII or Unicode character sets.
•Mouse - used to control a pointer on the screen of a computer.
•Trackball - similar to a mouse, this is used where extreme
accuracy is needed - for example, in CAD, sound and video
editing, and some medical imaging applications (such
as MRI scans).
•Graphics tablet - a physical pad, similar in size to a mouse
mat, which can be touched with a stylus or fingertips to allow
highly-accurate movements on the screen. The graphics tablet is
very popular with graphic designers, who can use it in a similar
way to a drawing pad.
•Games controller - use a combination of buttons and mini
thumb-controlled joysticks.
•Digital camera/web cam - used to capture and create images.
•Scanners - used to copy physical printed materials into the
computer. Scanners are often incorporated into printers.
Lecture №2
40.
Wireless inputsSome hardware peripherals can be used to transfer data between devices
wirelessly. They can be a useful way of inputting information. Here are some
examples:
•RFID chips (radio frequency ID chips) - these are a basic type of wireless
communication. When passed through a special electrical field, they broadcast data
through a high-frequency radio wave. This non-contact method of one-way
communication is used in tracking and identification. The chips can be easily
implanted into animals, and are already used in supermarkets and department stores
to track purchased goods.
•NFC (near field communication) - this builds on RFID, with the main difference
that it allows for two-way communication. NFC technology can be embedded
in smartphones, increasing opportunities to integrate with contactless payment
systems. NFC is similar to Bluetooth. It is an effective method of communicating
between mobile devices.
•Magnetic strip - different types of cards use magnetic bands to store information,
eg credit and debit cards and security access cards.
•Barcode reader - barcodes are scanned by a reader and the numbers in the code
correspond to records in a database. They are used to identify goods and products.
Lecture №2
41.
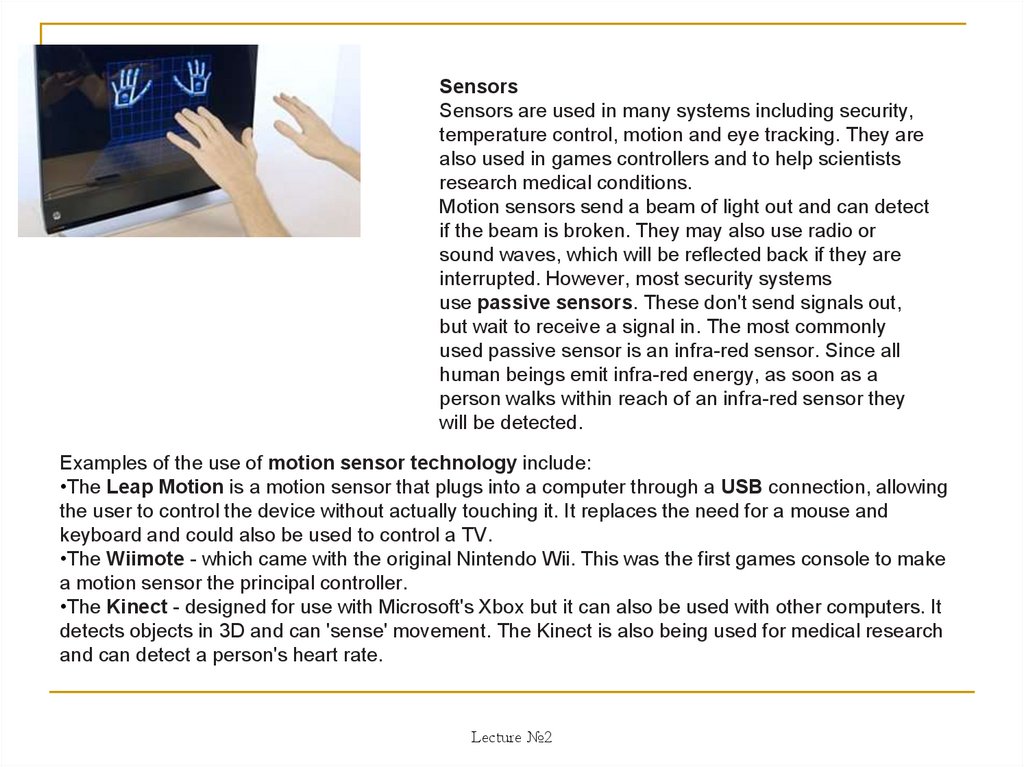
SensorsSensors are used in many systems including security,
temperature control, motion and eye tracking. They are
also used in games controllers and to help scientists
research medical conditions.
Motion sensors send a beam of light out and can detect
if the beam is broken. They may also use radio or
sound waves, which will be reflected back if they are
interrupted. However, most security systems
use passive sensors. These don't send signals out,
but wait to receive a signal in. The most commonly
used passive sensor is an infra-red sensor. Since all
human beings emit infra-red energy, as soon as a
person walks within reach of an infra-red sensor they
will be detected.
Examples of the use of motion sensor technology include:
•The Leap Motion is a motion sensor that plugs into a computer through a USB connection, allowing
the user to control the device without actually touching it. It replaces the need for a mouse and
keyboard and could also be used to control a TV.
•The Wiimote - which came with the original Nintendo Wii. This was the first games console to make
a motion sensor the principal controller.
•The Kinect - designed for use with Microsoft's Xbox but it can also be used with other computers. It
detects objects in 3D and can 'sense' movement. The Kinect is also being used for medical research
and can detect a person's heart rate.
Lecture №2
42.
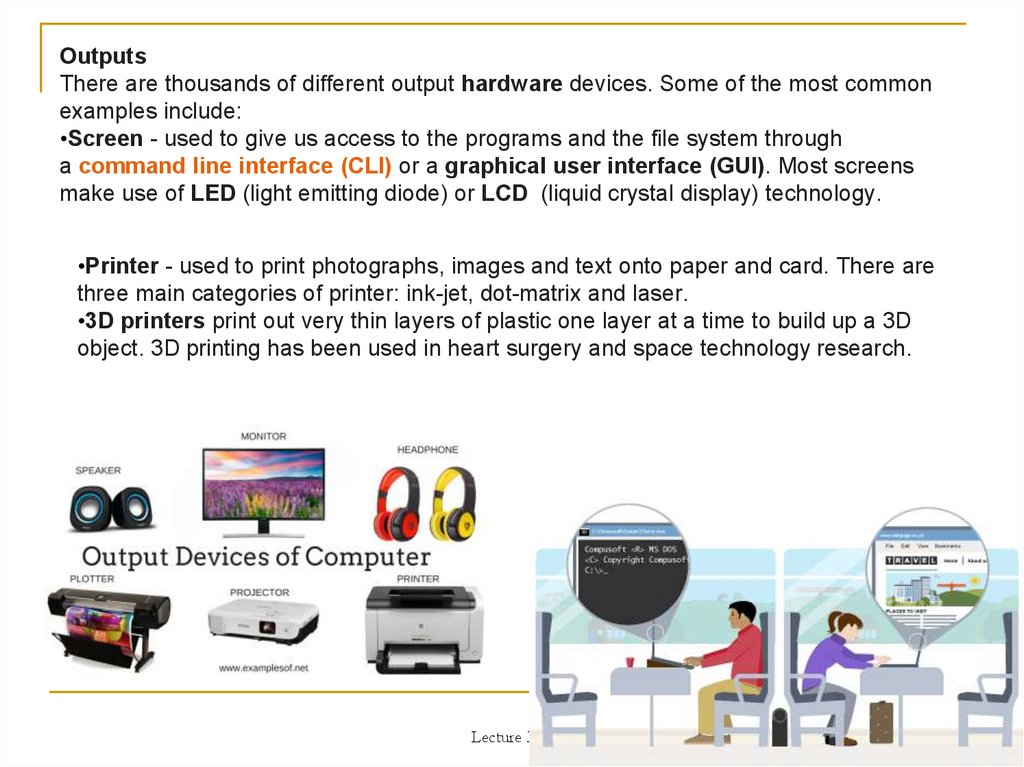
OutputsThere are thousands of different output hardware devices. Some of the most common
examples include:
•Screen - used to give us access to the programs and the file system through
a command line interface (CLI) or a graphical user interface (GUI). Most screens
make use of LED (light emitting diode) or LCD (liquid crystal display) technology.
•Printer - used to print photographs, images and text onto paper and card. There are
three main categories of printer: ink-jet, dot-matrix and laser.
•3D printers print out very thin layers of plastic one layer at a time to build up a 3D
object. 3D printing has been used in heart surgery and space technology research.
Lecture №2
43.
Inputs and outputs combinedSome peripherals operate as both inputs and outputs.
•Soundcard - used to receive and give out any sound more complicated than a basic beep. A
soundcard is usually inside the computer connected to the motherboard. Hi-spec soundcards can
be external and connected by FireWire or USB. Powerful external soundcards are used in music
recording studios to process live music recordings.
•//FireWire is a high-speed computer data-transfer interface that was used to connect personal
computers, audio and video devices, and other professional and consumer electronics.
•Microphone - used to record sounds and communicate over the internet. Microphones
convert analogue sound into digital sound. Voice activation devices allow us to give voice
commands to a computer. Therefore, voice control can be used instead of a mouse or
keyboard to interact with a screen reader.
Lecture №2
44.
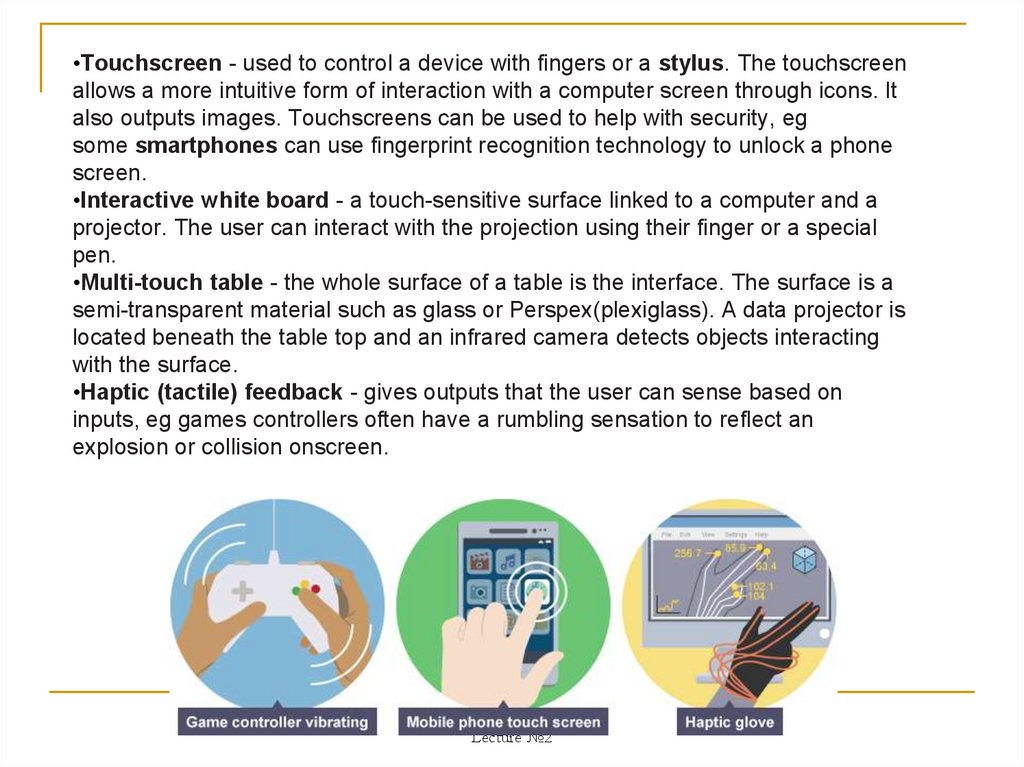
•Touchscreen - used to control a device with fingers or a stylus. The touchscreenallows a more intuitive form of interaction with a computer screen through icons. It
also outputs images. Touchscreens can be used to help with security, eg
some smartphones can use fingerprint recognition technology to unlock a phone
screen.
•Interactive white board - a touch-sensitive surface linked to a computer and a
projector. The user can interact with the projection using their finger or a special
pen.
•Multi-touch table - the whole surface of a table is the interface. The surface is a
semi-transparent material such as glass or Perspex(plexiglass). A data projector is
located beneath the table top and an infrared camera detects objects interacting
with the surface.
•Haptic (tactile) feedback - gives outputs that the user can sense based on
inputs, eg games controllers often have a rumbling sensation to reflect an
explosion or collision onscreen.
Lecture №2































 Информатика
Информатика








